CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Hackers Target Unpatched Citrix with Ransomware Attacks
All these attacks are taking place, hackers are scanning the internet for Citrix appliances which were unpatched for the CVE-2019-19781 [1] vulnerability. Vulnerable devices include the Citrix Application Delivery Controller (ADC), Citrix Gateway, and two older versions of Citrix SD-WAN WANOP. The vulnerability was disclosed in mid-December; however, internet-wide attacks began after January 11, when proof-of-concept exploit code was published online and became broadly available to anyone.
Citrix released the final permanent fix for the actively exploited CVE-2019-19781 vulnerability, needed to secure all vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
The CyberSecOp team has identified attacks scanning multiple client Citrix gateway to take advantage of vulnerabilities in Citrix gateway applications.
Timeline
On January 19, 2020, Citrix released firmware updates for Citrix Application Delivery Controller (ADC) and Citrix Gateway versions 11.1 and 12.0.
On January 22, 2020, Citrix released security updates for vulnerable SD-WAN WANOP appliances.
On January 23, 2020, Citrix released firmware updates for Citrix ADC and Gateway versions 12.1 and 13.0.
On January 24, 2020, Citrix released firmware updates for Citrix ADC and Gateway version 10.5.
A remote, unauthenticated attacker could exploit CVE-2019-19781 to perform arbitrary code execution.[2] This vulnerability has been detected in exploits in the wild.[3]
The Cybersecurity and Infrastructure Agency (CISA) strongly recommends that all users and administrators upgrade their vulnerable appliances as soon as possible.
Timeline of Specific Events
December 17, 2019 – Citrix released Security Bulletin CTX267027 with mitigations steps.
January 8, 2020 – The CERT Coordination Center (CERT/CC) released Vulnerability Note VU#619785: Citrix Application Delivery Controller and Citrix Gateway Web Server Vulnerability, and CISA releases a Current Activity entry.
January 10, 2020 – The National Security Agency (NSA) released a Cybersecurity Advisory on CVE-2019-19781.
January 11, 2020 – Citrix released blog post on CVE-2019-19781 with timeline for fixes.
January 13, 2020 – CISA released a Current Activity entry describing their utility that enables users and administrators to test whether their Citrix ADC and Citrix Gateway firmware is susceptible to the CVE-2019-19781 vulnerability.
January 16, 2020 – Citrix announced that Citrix SD-WAN WANOP appliance is also vulnerable to CVE-2019-19781.
January 19, 2020 – Citrix released firmware updates for Citrix ADC and Citrix Gateway versions 11.1 and 12.0 and blog post on accelerated schedule for fixes.
January 22, 2020 – Citrix released security updates for Citrix SD-WAN WANOP release 10.2.6 and 11.0.3.]
January 22, 2020 – Citrix and FireEye Mandiant released an indicator of compromise (IOC) scanning tool for CVE-2019-19781.
January 23, 2020 – Citrix released firmware updates for Citrix ADC and Citrix Gateway versions 12.1 and 13.0.
January 24, 2020 – Citrix released firmware updates for Citrix ADC and Citrix Gateway version 10.5.
Technical Details
Impact
On December 17, 2019, Citrix reported vulnerability CVE-2019-19781. A remote, unauthenticated attacker could exploit this vulnerability to perform arbitrary code execution. This vulnerability has been detected in exploits in the wild.
The vulnerability affects the following appliances:
Citrix NetScaler ADC and NetScaler Gateway version 10.5 – all supported builds
Citrix ADC and NetScaler Gateway version 11.1 – all supported builds before 11.1.63.15
Citrix ADC and NetScaler Gateway version 12.0 – all supported builds before 12.0.63.13
Citrix ADC and NetScaler Gateway version 12.1 – all supported builds before 12.1.55.18
Citrix ADC and Citrix Gateway version 13.0 – all supported builds before 13.0.47.24
Citrix SD-WAN WANOP appliance models 4000-WO, 4100-WO, 5000-WO, and 5100-WO – all supported software release builds before 10.2.6b and 11.0.3b. (Citrix SD-WAN WANOP is vulnerable because it packages Citrix ADC as a load balancer).
What Customers Should Do
Exploits of this issue on unmitigated appliances have been observed in the wild. Citrix strongly urges affected customers to immediately upgrade to a fixed build OR apply the provided mitigation which applies equally to Citrix ADC, Citrix Gateway and Citrix SD-WAN WANOP deployments. Customers who have chosen to immediately apply the mitigation should then upgrade all of their vulnerable appliances to a fixed build of the appliance at their earliest schedule. Subscribe to bulletin alerts at https://support.citrix.com/user/alerts to be notified when the new fixes are available.
The following knowledge base article contains the steps to deploy a responder policy to mitigate the issue in the interim until the system has been updated to a fixed build: CTX267679 - Mitigation steps for CVE-2019-19781
Upon application of the mitigation steps, customers may then verify correctness using the tool published here: CTX269180 - CVE-2019-19781 – Verification Tool
Fixed builds have been released across all supported versions of Citrix ADC and Citrix Gateway. Fixed builds have also been released for Citrix SD-WAN WANOP for the applicable appliance models. Citrix strongly recommends that customers install these updates at their earliest schedule. The fixed builds can be downloaded from https://www.citrix.com/downloads/citrix-adc/ and https://www.citrix.com/downloads/citrix-gateway/ and https://www.citrix.com/downloads/citrix-sd-wan/
If you would like to learn more about CVE-2019-19781 vulnerability & risk mitigation, please contact CyberSecOp at the following support@cybersecop.com
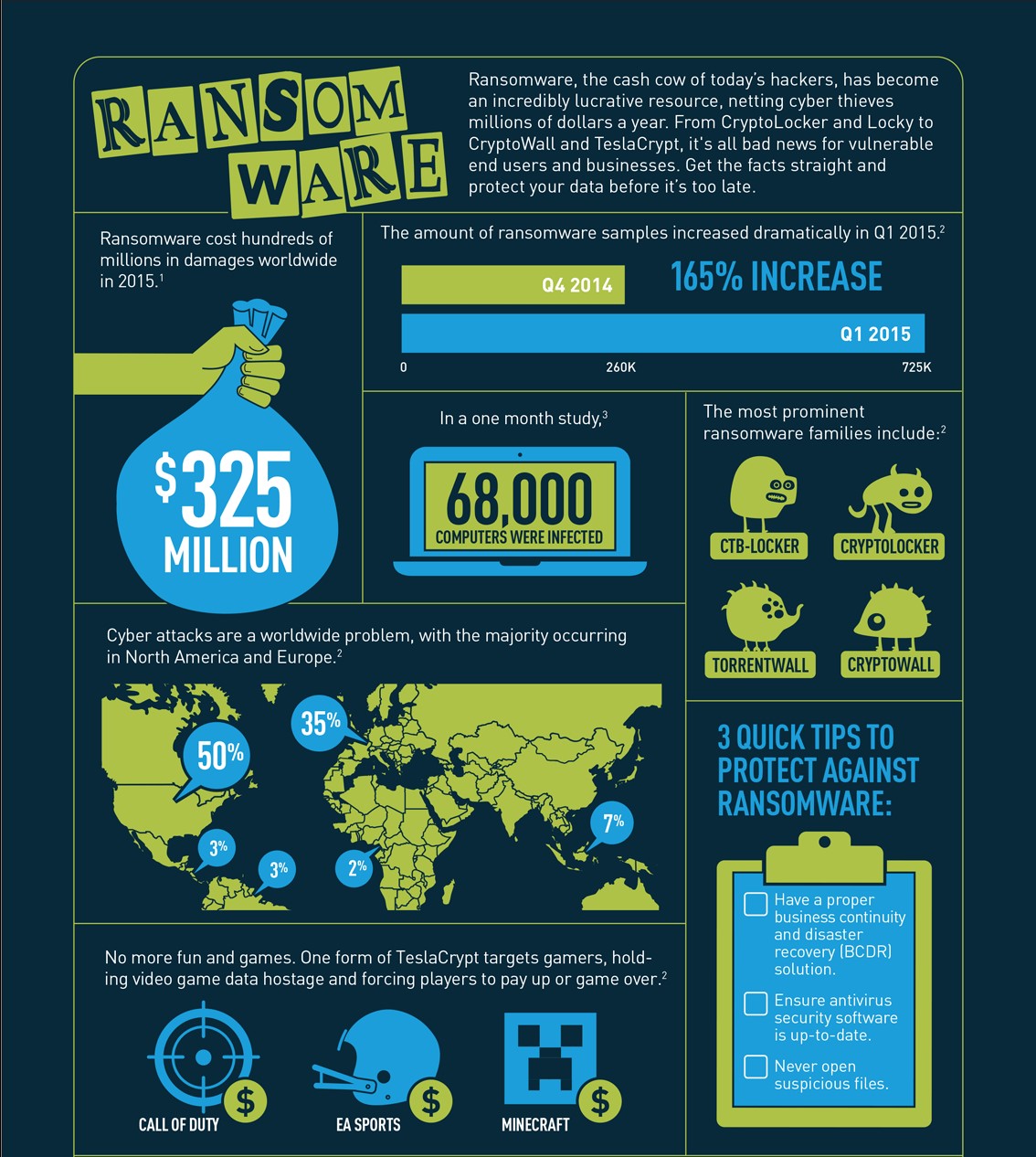
Ransomware - SMEs Faces Greatest Risk - Attacks Grown 235%
Enterprises, beware. Threat actors are continuing to eye businesses for high returns on investment in Q1 2019, breaching infrastructure, exfiltrating or holding data hostage, and abusing weak credentials for continued, targeted monitoring. From a steadfast increase of pervasive Trojans, such as Emotet, to a resurgence of ransomware lodged against corporate targets, cybercriminals are going after organizations with a vengeance.
Ransomware attacks on business targets have seen a substantial increase in the first quarter of 2019, up by 195 percent since the fourth quarter of 2018, according to a recent Malwarebytes report.
Malwarebytes researchers analyzed the combined statistics and intel collected from its intelligence, research, and data science teams between January 1 and March 31, 2019. They also leveraged telemetry from both consumer and business products on PC, Mac, and mobile devices.
Overall, they found that business detection of ransomware attacks increased by more than 500 percent from the same time frame in 2018 with 336,634 detections.
SMEs face the greatest risk from attacks as overall business detections have grown 235%
“Zero day attacks are on the rise and estimated to be a daily occurrence by 2021. This is largely down to digitisation within organisations and there’s more pressure on developers to deliver software faster – leaving systems vulnerable. This problem is exacerbated by hackers becoming more sophisticated, enabling them to bypass defences more easily.
“IT teams often prioritise stopping a breach occurring at all, but in today’s cyber climate a successful breach is inevitable. The most important aspect of cyber security is that businesses prepare for the worst and have effective data recovery and backup systems in place. Zero day recovery makes sure critical systems are down for as little time as possible. It’s often true that real damage from these breaches doesn’t come from the attack itself, but the resultant downtime after a breach – the time taken to become fully operational dictates the financial and operational fallout on a business.”
Key takeaways
cryptomining seems to have gone the way of the dodo. Detections of consumer-focused Bitcoin miners have dropped significantly over the last year and even from last quarter, while business-focused miners have increased from the previous quarter, especially in the APAC region.
Adware in Macs and mobile devices was problematic.
While all Mac malware saw a more than 60 percent increase from Q4 2018 to Q1 2019, adware was particularly pervasive, clocking in at over 200 percent from the previous quarter. Mobile adware detections also trended upward, as supply chain attacks delivered malware pre-installed on mobile devices. However, overall adware detections were fewer in Q1 2019 than they were during the same time period last year.
Exploit authors developed some attention-grabbing techniques. A new Flash Player zero-day was discovered in Q1 and quickly implemented into popular exploit kits, including Underminer and Fallout EK, as well as a new exploit kit called Spelevor. In addition, a Chrome zeroday required users to take action, fully shutting down and restarting their browser in order to patch the vulnerability. Finally, the popular software WinRAR was being used to deliver payloads to users.
As attacks against businesses ramped up, user trust in businesses to protect their data reached a new low.
In a survey conducted by Malwarebytes in Q1 2019 of nearly 4,000 respondents, users expressed deep concerns about abuse, misuse, and theft of PII, especially from social media and search engine companies. In a new section of our Cybercrime Tactics and Techniques report, we examine how cybercriminals found success by exploiting infrastructure weaknesses, gaps in policy and regulation, and even corporate negligence to not only walk away with valuable data, but establish persistence within the network.
Businesses are still the prime target. Overall detections of threats to businesses have steadily risen, while consumer threats have dropped off. Business detections increased by about 7 percent from the previous quarter, while consumer detections declined by nearly 40 percent, resulting in an overall dip in malware volume of 35 percent quarter over quarter. Compared to Q1 2018, business detections have skyrocketed 235 percent, with consumer detections dropping 24 percent year over year. This reinforces the observed trend of cybercriminals focusing more on business targets today.
Emotet shows no signs of stopping. Emotet, the most fearsome and dangerous threat to businesses today, has made a total shift away from consumers, reinforcing the intent of its creators to focus on enterprise targets, except for a few outlier spikes. Detections of Trojans (Emotet’s parent category) on business endpoints increased more than 200 percent from the previous quarter, and almost 650 percent from the same time last year.
Ransomware is back to business.
Ransomware has made a tremendous comeback against business targets in Q1 2019, with an increase of 195 percent in detections from Q4 2018 to Q1 2019. In comparison to the same time last year, business detections of ransomware have seen an uptick of over 500 percent, thanks in large part to a massive attack by the Troldesh ransomware against US organizations in early Q1.
Consumer detections of ransomware died down. Meanwhile, ransomware consumer detections have continued to drop, despite activity by families such as GandCrab, which primarily targeted consumers over the last quarter as it switched to a ransomware-asa-service and began brute-forcing RDP to infiltrate systems. Consumer detections of ransomware decreased by 10 percent quarter over quarter, and by 33 percent year over year.
Ransomware Breach and Ransomware Prevention
Cyber-criminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, TeslaCrypt., RyUK and others. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks. CyberSecOp use AI to help organization protect their data, and provide ransomware Incident response and remediation services.
HOW DO I RESPOND TO RANSOMWARE?
Implement your security incident response and business continuity plan. It may take time for your organization’s IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your organization’s essential functions according to your business continuity plan. Organizations should maintain and regularly test backup plans, disaster recovery plans, and business continuity procedures.
Contact law enforcement immediately. We encourage you to contact a local FBI or USSS field office immediately to report a ransomware event and request assistance. Contact CyberSecOp Security Consulting Firm for ransomware incident response & digital forensic services.
There are serious risks to consider before paying the ransom. We do not encourage paying a ransom. We understand that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. As you contemplate this choice, consider the following risks:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.
• Some victims who paid the demand have reported being targeted again by cyber actors.
• After paying the originally demanded ransom, some victims have been asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
Ransomware Incident Response from CyberSecOp, the firm that provide ransomware protection, and ransomware ransom payment.
WHAT IS RANSOMWARE?
Ransomware is a type of malicious software cyber actors use to deny access to systems or data. The malicious cyber actor holds systems or data hostage until the ransom is paid. After the initial infection, the ransomware attempts to spread to shared storage drives and other accessible systems. If the demands are not met, the system or encrypted data remains unavailable, or data may be deleted.
HOW DO I PROTECT MY NETWORKS?
A commitment to cyber hygiene and best practices is critical to protecting your networks. Here are some questions you may want to ask of your organization to help prevent ransomware attacks:
1. Backups: Do we backup all critical information? Are the backups stored offline? Have we tested our ability to revert to backups during an incident?
2. Risk Analysis: Have we conducted a cybersecurity risk analysis of the organization?
3. Staff Training: Have we trained staff on cybersecurity best practices?
4. Vulnerability Patching: Have we implemented appropriate patching of known system vulnerabilities?
5. Application Whitelisting: Do we allow only approved programs to run on our networks?
6. Incident Response: Do we have an incident response plan and have we exercised it?
7. Business Continuity: Are we able to sustain business operations without access to certain systems? For how long? Have we tested this?
8. Penetration Testing: Have we attempted to hack into our own systems to test the security of our systems and our ability to defend against attacks?
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
Ransomware?
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment.
Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails.
You will need and experience security consulting firm to guide you remediate the ransomware.
Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and contact CyberSecOp to request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. CyberSecOp does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key. CyberSecOp can negotiate the ransom for you, we have a 60% t rate of reducing the ransom.
• Paying could inadvertently encourage this criminal business model.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising.
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
Ransomware Attack: Threats, and Countermeasures
When you combine cryptography with malware, you get a very dangerous mix of problems. This is a type of computer virus that goes by another name, “ransomware”. This type of virus is part of a field of study called “cryptovirology”. Through the use of techniques called phishing, a threat actor sends the ransomware file to an unknowing victim. If the file is opened it will execute the virus payload, which is malicious code. The ransomware runs the code that encrypts user data on the infected computer or host. The data are user files like documents, spreadsheets, photos, multimedia files and even confidential records. The ransomware targets your personal computer files and applies an encryption algorithm like RSA which makes the file inaccessible. The only way to access them is if the user pays a ransom to the threat actor by following instructions which appear encoded into the encrypted files. Thus it is called ransomware, because a form of payment is demanded in order to fix the problem.
Once they have all publicly available email addresses, the fun starts. The more of your email addresses that are floating out there, the bigger your attack footprint is, and the higher the risk is. It’s often a surprise how many addresses are actually out there. Now they can send all employees an email supposedly coming from Accounting, Human Resources, the CEO or perhaps the mail room, and social engineer your users to click on a link. almost 90 percent of attack are done via the internet, based on the new software model, and yes the bad guys are also moving to the cloud. Software is shifting away from locally-installed apps to Software as a Service web applications that run in the cloud. Criminals are cashing in on this trend, which has led to the creation of Ransomware as a Service (RaaS), a growing threat to business.
RaaS refers to various online malware exploits that bad actors can use to attack the IT assets of businesses and individuals. These attack programs are created by criminal entrepreneurs who sell their services to other criminals. The people who buy these programs then extort or blackmail their victims by holding computer systems to ransom.
How does Ransomware spread?
Ransomware is typically spread through phishing emails that contain malicious attachments. These emails appear to come from a legitimate source and give a compelling reason that the document is important. Malicious attachments are often PDF, ZIP, DOC, XLS, PPT files that appear as invoices, legitimate business documents, or other work-related files. In some cases, Ransonware may end up on your computer by visiting infected web sites. To avoid malicious drive-by downloads, ensure that antivirus and all installed software is up-to-date.
How to Mitigate the Risk of Ransomware Infections
These recommendations are not comprehensive but provide general best practices.
Securing Networks and Systems
Have an incident response plan that includes what to do during a ransomware event.
Backups are critical. Use a backup system that allows multiple iterations of the backups to be saved, in case a copy of the backups includes encrypted or infected files. Routinely test backups for data integrity and to ensure it is operational.
Use antivirus and anti-spam solutions. Enable regular system and network scans with antivirus programs enabled to automatically update signatures. Implement an anti-spam solution to stop phishing emails from reaching the network. Consider adding a warning banner to all emails from external sources that reminds users of the dangers of clicking on links and opening attachments.
Disable macros scripts. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full office suite applications.
Keep all systems patched, including all hardware, including mobile devices, operating systems, software, and applications, including cloud locations and content management systems (CMS), patched and up-to-date. Use a centralized patch management system if possible. Implement application white-listing and software restriction policies (SRP) to prevent the execution of programs in common ransomware locations, such as temporary folders.
Restrict Internet access. Use a proxy server for Internet access and consider ad-blocking software. Restrict access to common ransomware entry points, such as personal email accounts and social networking websites.
Apply the principles of least privilege and network segmentation. Categorize and separate data based on organizational value and where possible, implement virtual environments and the physical and logical separation of networks and data. Apply the principle of least privilege.
Vet and monitor third parties that have remote access to the organization’s network and/or your connections to third parties, to ensure they are diligent with cybersecurity best practices.
Participate in cybersecurity information sharing programs and organizations, such as MS-ISAC and InfraGard.
Securing the End User
Provide social engineering and phishing training to employees. Urge them not to open suspicious emails, not to click on links or open attachments contained in such emails, and to be cautious before visiting unknown websites.
Remind users to close their browser when not in use.
Have a reporting plan that ensures staff knows where and how to report suspicious activity.
Responding to a Compromise/Attack
Immediately disconnect the infected system from the network to prevent infection propagation.
Call CyberSecOp.com Ransomware Response Team: They provide remediation and bitcoin payment services.
Determine the affected data as some sensitive data, such as electronic protected health information (ePHI) may require additional reporting and/or mitigation measures.
Determine if a decryptor is available. Online resources such as No More Ransom! can help.
Restore files from regularly maintained backups.
Report the infection. It is highly recommended that SLTT government agencies report ransomware incidents to MS-ISAC. Other sectors and home users may report to infections to local Federal Bureau of Investigation (FBI) field offices or to the Internet Crime Complaint Center (IC3).
Ransomware Checker & Removal Tools
Addressing Cyber Threats and Enabling Security in your Enterprise
Cybersecurity threats from hacktivists, criminals, and hostile nation states are enough to keep government officials, businesses, and consumers up at night. These attacks are growing in sophistication and frequency and pose serious threats to our national and economic security.
Everyone impacted by these vicious and dangerous acts must work together to help prevent, protect against, and effectively respond to them.
What are the biggest cyber threats CISOs are worried about in 2019? In today's age of breaches, staying ahead of cyber threats is becoming more critical than ever. Dive into how organizations are addressing the threat of cyber attacks, how they are measuring risk, and what they are doing about improving security from some of the top experts in the field.
Ransomware is still a large risk, affecting a large number of businesses
Data Loss and Data Breach based on information available on dark web, proves that organization can’t protect customers data.
Small business with no security program are at risk more than large organization.
All industry need to have some type of cyber regulations based on secure standards such as NIST or ISO.
What can business do, to enable a stronger security posture in their enterprise
Businesses adopt standalone cyber insurance policies as boards and executives wake up to cyber liability. As boards and executives experience and witness the impact of cyber attacks, including reduced earnings, operational disruption, and claims brought against directors and officers, businesses will turn to tailored enterprise cyber insurance policies, rather than relying on “silent” components in other policies. Adoption will spread beyond traditional buyers of cyber insurance, such as retail, financial, and healthcare sectors, to others vulnerable to cyber-related business disruption, including manufacturing, transportation, utility, and oil and gas.
As the physical and cyber worlds collide, chief risk officers take center stage to manage cyber as an enterprise risk. As sophisticated cyber attacks generate real-world consequences that impact business operations at increasing scale, C-suites will wake up to the enterprise nature of cyber risk. In 2018, expect CROs to have a seat at the cyber table, working closely with chief information security officers (CISOs) to help organizations understand the holistic impact of cyber risk on the business.
Regulatory spotlight widens and becomes more complex, provoking calls for harmonization. EU holds global companies to account over General Data Protection Regulation (GDPR) violation; big data aggregators come under scrutiny in the U.S. In 2018, regulators at the international, national and local levels will more strictly enforce existing cybersecurity regulations and introduce new regulations. Expect to see EU regulators holding major U.S. and global companies to account for GDPR violations. Across the Atlantic, big data organizations (aggregators and resellers) will come under scrutiny on how they are collecting, using, and securing data. Industry organizations will push back on regulators, calling for alignment of cyber regulations.
Criminals look to attack businesses embracing the Internet of Things, in particular targeting small to mid-sized businesses providing services to global organizations. In 2018, global organizations will need to consider the increased complexities when it comes to how businesses are using the IoT in relation to third-party risk management. The report predicts large companies will be brought down by an attack on a small vendor or contractor that targets the IoT, using it as a way into their network. This will serve as a wake-up call for large organizations to update their third-party risk management, and for small and mid-sized businesses to implement better security measures or risk losing business.
As passwords continue to be hacked, and attackers circumvent physical biometrics, multi-factor authentication becomes more important than ever before. Beyond passwords, companies are implementing new methods of authentication – from facial recognition to fingerprints. However, these technologies are still vulnerable and as such, the report anticipates that a new wave of companies will embrace multi-factor authentication to combat the assault on passwords and attacks targeting biometrics. This will require individuals to present several pieces of evidence to an authentication instrument. With the new need for multi-factor authentication, and consumer demand for unobtrusive layers of security, expect to see the implementation of behavioral biometrics.
Criminals will target transactions that use reward points as currency, spurring mainstream adoption of bug bounty programs: Companies beyond the technology, government, automotive and financial services sectors will introduce bug bounty platforms into their security programs. As criminals target transactions that use points as currency, businesses with loyalty, gift and rewards programs –such as airlines, retailers, and hospitality providers– will be the next wave of companies implementing bug bounty programs. As more organizations adopt the programs, they will require support from external experts to avoid introducing new risks with improperly configured programs.
Ransomware attackers get targeted; crypto currencies help ransomware industry flourish. In 2018, ransomware criminals will evolve their tactics. The reports predicts that attackers utilizing forms of benign malware—such as software designed to cause DDoS attacks or launch display ads on thousands of systems— will launch huge outbreaks of ransomware. While attackers will continue to launch scatter-gun-style attacks to disrupt as many systems as possible, the report predicts an increase in instances of attacks targeting specific companies and demanding ransomware payments proportional to the value of the encrypted assets. Crypto currencies will continue to support the flourishing ransomware industry overall, despite law enforcement becoming more advanced in their ability to trace attacks, for example through bitcoin wallets.
Insider risks plague organizations as they underestimate their severe vulnerability and liability while major attacks fly under the radar. In 2017, businesses under invested in proactive insider risk mitigation strategies, and 2018 will be no different. According to the report, a continued lack of security training and technical controls, coupled with the changing dynamics of the modern workforce, the full extent of cyber attacks and incidents caused by insiders will not become fully public. Many companies will continue to reactively responding to incidents behind closed doors and remain unaware of the true cost and impact of insider risk on the organization.
What is Cybersecurity Risk Management
Cyber Risk Management is the next evolution in enterprise technology risk and security for organizations that increasingly rely on digital processes to run their business. Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such doors and locks to protect homes and autos, vaults to protect money and precious jewels, and police, fire and security to protect against other physical risks.
What is cybersecurity risk management?
Rather than doors, locks and vaults, IT departments rely on a combination of strategies, technologies and user education to protect an enterprise against cybersecurity attacks that can compromise systems, steal data and other valuable company information, and damage an enterprise’s reputation. As the volume and severity of cyber attacks grow, the need for cybersecurity risk management grows with it.
Cybersecurity risk management takes the idea of real world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.
Setting up your risk management system
Before setting up a cybersecurity risk management system, the enterprise needs to determine what assets it needs to protect and place a priority on. As the National Institute of Standards and Technology (NIST) points out in its Framework for Improving Critical Infrastructure Cybersecurity, there is no one-size-fits all solution. Different organizations have different technology infrastructures and different potential risks. Some organizations such as financial services firms and healthcare organizations, have regulatory concerns in addition to business concerns that need to be addressed in a cybersecurity risk management system. Cybersecurity should follow a layered approach, with additional protections for the most important assets, such as corporate and customer data. Remember that reputational harm from a breach can do more damage than the breach itself.
Risk management with CyberSecOp
Identity Services
Identity services help companies manage the explosion of digital identities and access to critical resources, both internal and cloud-based. In this age of digital transformation, the spheres of the individual’s life―as a professional, consumer, and private citizen―are interlinked in a complex digital structure, like a piece of fabric. The growing ability to piece together a digital picture of a person’s life and identity carries both risk and opportunity.
Wherever an organization is on its journey, we can help them achieve efficiencies, reduce risk, and evolve to support the changing needs of the digital business. With 20 years of identity management experience across the major industries, we offer field-tested accelerators and methods that are scalable and adaptive to each client’s specific set of business requirements.
Data Protection
Data Protection services help implement capabilities and technologies to protect sensitive data. As infrastructure and applications become more virtualized and adaptive, new cybersecurity gaps can be created as fast as old ones have been addressed, making the prevention of data breaches more difficult than ever. By prioritizing preventative and detective defenses around highly sensitive data, security teams can help reduce data loss and risk when attackers get past network, application, and infrastructure controls.
Leveraging these principles and an understanding of each client’s risk profile, CyberSecOp helps organizations design, implement, and manage capabilities to help better protect sensitive information across the end-to-end data lifecycle, and at an organization’s last line of defense.Application Security
In the era of digital transformation, application portfolios are becoming exponentially more diverse—and support a growing community of users. As the application “surface area” expands, so does cyber risk. Amid the change, one thing remains constant: applications are the lifeline of the business—and need to be a front line of cyber defense. It’s an important time for organizations to reexamine their approaches to application security.
Improving application security requires technical attention to individual applications, but also a broad framework across the application portfolio—from custom-developed to commercial off-the-shelf (COTS) applications and whether managed on-premise, on a mobile platform, in the cloud, or in a hybrid environment. It also requires the flexibility to support varying and often coexisting system methodology processes from waterfall, to agile, to DevOps in order to address application-related cyber risk at the pace of the organization’s digital evolution.
CyberSecOp’s application security services help organizations to design and implement security mechanisms across the system development methodology that can flex to your operational requirements to drive value through IT while also protecting your application portfolio against the changing cyber threat landscape.Infrastructure Security
Infrastructure Security services focus on developing advanced protection of core systems and devices. Today’s critical business drivers—the need to digitally transform, modernize the supply chain, enhance customer experience, increase agility, reduce costs, etc.—are driving a major shift in technology priorities. This shift includes increasing focus on cloud adoption, the Internet of Things (IoT), hybrid computing, software-defined networks (SDN), robotic process automation (RPA), blockchain, artificial intelligence, and more. The infrastructure supporting it has become highly virtualized and automated—and the traditional means of securing infrastructure fall short.
CyberSecOp helps organizations move toward a modernized, risk-focused agile defense approach. While the basic infrastructure domains—physical facilities, networks, systems and storage, and endpoints—that need to be protected remain the same, the means to secure them must evolve. By providing assessment, strategy, architecture, implementation, and operational management assistance across the four infrastructure domains, we help clients face our brave new world with a transformed, agile defense capability.
Data Protection Solutions & Data Security
Protect and secure data and data privacy is critical since most companies hold clients/costumers sensitive data, and protect that data is not only critical to its clients/costumes. Data protection is also critical for companies intellectual properties and reputation.
Data Protection Services
As more organizations move to hybrid or multi-cloud IT strategy, managing data protection services has become increasingly more complex. Various systems, technologies and environments require different tools for data protection management, and many IT teams find they must use a variety of tools to perform backup operations. In addition to greater inefficiency and rising costs, this intensive focus on data protection services diverts IT teams from higher value tasks and other strategic priorities.
Data Protection Simplified by CyberSecOp LocVault services
To simplify data protection services, CyberSecOp offers a Managed Data Protection solution that can protect digital assets across all your environments. Powered by Locvault's best-in-class data backup and recovery software, CyberSecOps Managed Data protection services help simplify data protection by enabling IT teams to use a single tool for backup and restore processes.
Efficiently Protect, Manage and Recover Your Data
Protect, manage and access the information you need with a heterogeneous data protection solution
A single interface manages data at a fraction of the time, effort and cost required by separate point products
Simplify data management in complex networked storage environments with a consistent way to locate and manage data and applications
With Privacy and Data Protection, CyberSecOp LocVault will help you protect your sensitive business data and help you meet compliance requirements related to data storage and protection.
We’ll also help you assess your risk, create custom policies to encrypt and restrict access to sensitive data, and report on data access — helping to ensure that your important data remains protected. Speak with an expert
Are Users Your Weakest Link - To Your Cybersecurity Posture
Humans remain the weak link in corporate data protection
Humans remain the weak link in corporate data protection, but you might be surprised that it isn't only rank-and-file employees duped by phishing scams who pose risks. Some companies are lulled into a false sense of cybersecurity by vendors. You read that right, Some enterprises believe the shiny new technologies they've acquired will protect them from anything.
As we continue to build defense in depth and deploy security appliances utilizing AI and other emerging technologies, attackers will continue to pivot to the perennial weak spot: the users. Recently I hosted the Social Engineering Capture The Flag competition at Hackfest in Quebec, and similar to last year, the results were sobering. Every single targeted company had employees that gave detailed information over the phone on their OS and service pack level, and 88 percent gave detailed information on the browser they were using. Three quarters went to a URL that they were given over the phone. The information that the companies bled was disheartening but not shocking. Until we train employees to trust their instincts and tell them it's okay to say no to a customer, things won't change. In the current environment where companies ask their customers to leave a positive review online, employees increasingly feel less empowered to terminate a call they feel is suspicious. Your friendly neighborhood hacker is happy to exploit this weakness.
Billions being send on security tools
The threat of cyber crime has created a significant increase in interest on the topic of cyber security, with organizations spending billions of dollars to protect themselves against a fast evolving array of current and potential future threats. Many spend heavily on monitoring, surveillance and software; however, they often neglect the risk exposure created by their own people – and, in this digital age, by their customers.
Businesses are losing the fight, pay ransom, or lose their lively hood
Businesses are forced to make exceedingly difficult decisions. On one hand, it feels wrong to negotiate with the cybercriminals and give them what they want. On the other hand, the looming financial hit and business interruption is typically far more detrimental than the payoff amount. If business owners don’t engage with the ransomers, they face the prospect that they, and their employees, may lose their livelihood. I see ransomware as a continuing cyber threat in 2019 and beyond. It’s up to business owners to implement the best security practices and ensure that their employees are properly trained to identify and avoid potential threats.
Choosing A Managed Detection & Response Provider
Why Managed Detection & Response Provider may be the right move
Companies outsourcing security need Managed Detection & Response providers (MDR) more than ever to improve cyber resilience. With the security landscape growing more complex, and the costs of maintaining adequate in-house security teams high, it makes sense for many companies to outsource the tasks of threat hunting and response to ensure that they can promptly identify potential threats and react swiftly to mitigate damages. Managed Detection & Response providers often integrate tools such as Endpoint Detection & Response and other solutions to detect threats, analyze risk, and correlate threat data to pinpoint patterns that could indicate a larger attack.
How to choose the right Manged Detection & Response Provider
Smart moves: you’re making them. How do we know? For one, you’re investigating ways to close the gaps in your threat detection and incident response. Which makes sense, given that assembling the talent and tech to thoroughly thwart attackers requires more than most organizations can commit to. Even smarter, you’re checking out Managed Detection and Response (MDR) Services, an increasingly popular solution which combines expertise and tools to provide monitoring and alerting, as well as remote incident investigation and response that can help you detect and remediate threats.
9 things to look our for when choosing a Managed Detection & Response Provider
Your Managed Detection & Response Provider should combine numerous data inputs from security detection tools, threat intel feeds, third party data sources, and the IT asset database to identify not only where there is a threat but its risk compared to others in the queue.
Assess your company's present and future technology needs and initiatives. Qualify, quantify and communicate those needs throughout your company. Is the Managed Detection & Response Provider able to address your range of needs?
Technology strategies should encompass people and processes as part of the organization's mission and strategies. Do they offer ongoing employee training as part of their service?
Does the Managed Detection & Response Provider continuously assess your organization's performance for meeting objectives? You want a partner that focuses on continuous evaluation and improvement of your objectives.
Review your company's goals and mission. Ensure they are clear and concise and can be communicated to all organizational stakeholders as well as your new IT partner.
Perform annual policy and process reviews to assess organization's readiness for external reviews and incident response.
Identify and create teams within your organization to define current challenges and align initiatives to those challenges.
Through playbooks and pre-defined workflows, you can quickly assess and begin to remediate security incidents based on best practices. Ask a Managed Detection & Response Provider if they include such materials as part of their package.
CIOs/CISOs should have unprecedented transparency to all aspects of the security environment. Through dashboards and visualization techniques, CIOs/CISOs will be more easily able to communicate with Managed Detection & Response Providers which vulnerabilities and threats exist and the risks of inaction.
WHAT DO SECURITY CONSULTANTS DO?
WHAT DO SECURITY CONSULTANTS DO?
Security consults deal with various threats to physical and computer security. Security threats come in many forms such as computer hackers, terrorists, and attacks on physical assets. There are specializations for security consultants of building security, natural and man-made disaster prevention, or with computer security issues.
Some of the roles security consultants may do for companies or private individuals are installing physical protections of video surveillance and alarm systems. Physical security risks are issues for many companies and security consultants may determine physical security risks such as threats of violence in the workplace, the stability of a building during tornadoes, earthquakes, fires, or other natural disasters, and development of evacuation plans for personnel during emergencies. Security consultants also may advise on building maintenance issues.
What services does a security consultants provide?
Security consultants can also help to incorporate security changes at all levels of the company. Based upon the security audit that’s conducted, a security consultant, if allowed to, can implement various new security measures and procedures throughout the company, which can include security related to:
Analyzing areas that are currently exposed and if they have had their security compromised in the past;
Performing a gap analysis in order to determine if any areas of a company’s current security does not meet accepted industry standards;
Gauging the work environment through performing interviews with important personnel and company employees;
Providing a list of recommendations based upon found security vulnerabilities, which includes security measures that should be incorporated.
Policies and procedures;
Electronic surveillance and alarm systems;
Security personnel.
A security consultant will work closely with management for the purposes of transparent communication and to make sure that any security changes that are implemented are done so within the allotted budget. The degree to which a security consultant can incorporate security changes depends largely upon this, in addition to the management’s instructions.
CyberSecOp Security Services has been providing expert security consulting services for decades. Make sure to contact us today to ask about our advanced security consulting services, which will be personalized to your company’s particular needs.
Cyber Security Do's and Don'ts
Information and Cyber Security Consulting Services: Cyber security systems and principles are designed to safeguard company data, websites and web applications from attackers seeking to disrupt, delay, alter or redirect the flow of data. These attackers vary in target, motive, levels of organization, and technical capabilities, requiring public and private organizations to adopt ever-increasing measures to prevent cyber attacks. CyberSecOp is an award winning US based to Cyber Security Consulting Company.
The following are some important do’s and don’ts for advisers to keep in mind when executing on the action steps in your cybersecurity plan:
Make use of all tools available from your broker-dealer or custodian. The securities industry is investing tens of millions of dollars in cybersecurity, making tools and resources available to advisers and their teams. Actively seek out those tools and become known at your firm for your interest in and commitment to cybersecurity.
Eliminate weak links in your system. Hackers will be turned away from your systems that use strong passwords and encryption. Don’t let users share passwords. In addition to PCs, encrypt
all thumb drives, cell phones and tablets. And set untended computers to lock automatically after a set number of minutes.
Take preparation, training and review seriously. Put effort into your plan, review it seriously on a regular basis, document that review, and make sure that all staff – including even those who don’t usually deal with clients or their information – are regularly trained and updated on cybersecurity policies and procedures. Since staff carelessness or inattention can be the weakest link
in the defense chain, make sure that you and your staff never download an attachment or accept a request if it can’t be verified.
Be alert to things that don’t feel right. Suppose, for example, that a staff member receives a phone call from someone saying he’s from Microsoft tech support and has noticed a computer virus on your system. Even if the employee isn’t aware that reputable tech support operations don’t work that way, he or she should immediately sense that the call is out of the ordinary and somehow amiss. Given that feeling, the employee should hang up immediately and not let the unidentified caller connect to the firm’s system. Similarly, if you or staff receive an e-mail from a client saying they’ve been mugged on vacation or have lost their wallet or passport, most likely their e-mail has been hacked. Contact that person via landline or cell phone and confirm the story.
Educate your users and clients in how to communicate safely. Advisers should require multifactor authentication (use of a token or other identifier beyond password or ID) for client communication through Gmail, Yahoo! and other major providers. This will protect them, and you, from hackers.
Don’t keep cybersecurity a secret. The financial advice business is competitive, but there is one area where cooperation, not competition, is paramount: cybersecurity. Discuss the issue frequently with peers and share any ideas you have.
Don’t lull yourself into thinking cybersecurity is someone else’s problem. Be alert to news and developments in cybercrime and cybersecurity and seek more information and update plans and programs accordingly. Start by identifying your three biggest potential threats and get to work addressing them.
MSSP Cybersecurity & Managed Detection and Response
MSSP Cybersecurity & Managed Detection and Response
Managed detection and response enables a proactive approach to security with its ability to detect and fully analyze threats and promptly respond to incidents. CyberSecOp Threat intelligence is one of the key aspects our security consultants used to help organizations make decisions on how to combat threats. Through managed detection and response, organizations can take advantage of the threat intelligence capabilities of security experts.
How Managed Detection and Response Provides Effective Threat Intelligence
Capture full visibility across your entire IT environment
Detect the most advanced threats (known and unknown) designed to bypass your traditional perimeter security controls, even when no malware is used
Expose threat actors currently hiding in your environment
Gain 24x7 monitoring by an advanced team of security experts that are specially trained to analyze advanced threats, determine the severity of any incidents and provide actionable guidance to remediate
Quickly elevate the alerts that matter most so you can focus limited resources where it matters most
Managed Detection and Response Service
Managed Detection and Response (MDR) is an all-encompassing cybersecurity service used to detect and respond to cyber-attacks. Using the best of signature, behavioral and anomaly detection capabilities, along with forensic investigation tools and threat intelligence, human analysts hunt, investigate and respond to known and unknown cyber threats in real time 24x7x365. Get Managed Detection and Response Services for your business www.cybersecop.com.
Ransomware Cyberattack - 92% of MSSPs Expect Ongoing Attacks
Ransomware is the leading cyberattack experienced by small and medium-sized businesses (SMBs), according to a survey of more than 2,400 managed service providers (MSSPs) conducted by data protection company Datto.
Datto’s State of the Channel Ransomware Report provides unique visibility into the ransomware epidemic from the perspective of the IT Channel and the SMB clients who are dealing with these infections on a daily basis. The report provides a wealth of detail on ransomware, including year-over-year trends, frequency, targets, impact, and recommendations for ensuring recovery and continuity in the face of the growing threat.
Key findings from Datto’s “State of the Channel Ransomware Report” included:
79 percent of MSSPs reported ransomware attacks against customers.
85 percent indicated that victims had antivirus software installed, 65 percent reported victims had email/spam filters installed and 29 percent reported victims used pop-up blockers.
89 percent are “highly concerned” about ransomware attacks.
92 percent predict the number of ransomware attacks will continue at current, or worse, rates.
MSPs ranked phishing emails as the top ransomware delivery method, followed by malicious websites, web ads and clickbait.
The average requested ransom for SMBs is roughly $4,300, while the average cost of downtime related to such an attack is approximately $46,800.
The number of MSPs reporting OS/iOS attacks increased by nearly 500 percent year over year in the first six months of 2018.
No single solution is guaranteed to prevent such attacks, Datto indicated. Conversely, SMBs require a multilayered approach to identify and stop ransomware attacks before they cause brand reputation damage, revenue loss and other problems.
How Can SMBs Address Ransomware Attacks?
CyberSecop offered the following recommendations to help SMBs safeguard their data and assets against such attacks:
Leverage business continuity and disaster recovery (BCDR) technology. BCDR technology won’t stop ransomware attacks; instead, it helps an SMB determine how to limit downtime and maintain operations despite a ransomware attack.
Provide cybersecurity training. By offering regular and mandatory cybersecurity training, an SMB can ensure all of its employees can identify and avoid potential phishing scams that otherwise lead to such an attack.
Employ a dedicated cybersecurity professional. It may be difficult for an SMB to hire a full-time cybersecurity professional. Fortunately, working with an MSSP allows an SMB to receive cybersecurity monitoring and other security services.
Data Breaches Ransomware and Cyber Attacks
Data Breaches Ransomware and Cyber Attacks
It’s unrealistic to think that you can completely avoid cyberattacks and data breaches, so it’s vital to have a proper data recovery plan in place. You can also tighten your defenses significantly by ensuring all of your network devices are properly configured, and by putting some thought into all of your potential network borders.
Data Recovery Capability
Do you have a proper backup plan in place? Have you ever tested it to see that it works? Disaster recovery is absolutely vital, but an alarming number of companies do not have an adequate system in place. A survey of 400 IT executives by IDG Research revealed that 40% rate their organizations’ ability to recover their operations in the event of disaster or disruption as “fair or poor.” Three out of four companies fail from a disaster recovery standpoint, according to the Disaster Recovery Preparedness Benchmark.
A successful malware attack can lead to altered data on all compromised machines and the full effects are often very difficult to determine. The option to roll back to a backup that predates the infection is vital. Backed up data must be encrypted and physically protected. It’s also important that a test team routinely checks a random sampling of system backups by restoring them and verifying data integrity.
Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
The default configurations for network devices like firewalls, routers, and switches are all about ease of use and deployment. They aren’t designed with security in mind and they can be exploited by determined attackers. There’s also a risk that companies will create exceptions for business reasons and then fail to properly analyze the potential impact.
The 2015 Information Security Breaches Survey found that failure to keep technical configuration up to date was a factor in 19% of incidents. Attackers are skilled at seeking out vulnerable default settings and exploiting them. Organizations should have standardized secure configuration guidelines applied across devices. Security updates must be applied in a timely fashion.
You need to employ two-factor authentication and encrypted sessions when managing network devices, and engineers should use an isolated, dedicated machine without Internet access. It’s also important to use automated tools to monitor the network and track device configurations. Changes should be flagged and rule sets analyzed to ensure consistency.
Boundary Defense
When the French built the Maginot Line in World War II, a series of impregnable fortifications that extended along the border with Germany and beyond, it failed to protect them because the Germans invaded around the North end through neutral Belgium. There’s an important lesson there for security professionals: Attackers will often find weaknesses in perimeter systems and then pivot to get deeper into your territory.
They may gain access through a trusted partner, or possibly an extranet, while your defensive eye is focused on the Internet. Effective defenses are multi-layered systems of firewalls, proxies, and DMZ perimeter networks. You need to filter inbound and outbound traffic and take caution not to blur the boundaries between internal and external networks. Consider network-based IDS sensors and IPS devices to detect attacks and block bad traffic.
Segment your network and protect each sector with a proxy and firewall to limit access as far as possible. If you don’t have internal network protection, then intruders can get their hands on the keys to the kingdom by successfully breaching the outer defenses.
The real cost
A lot of businesses argue that they can’t afford a comprehensive disaster recovery plan, but they should really consider whether they can afford to lose all their data or be uncertain about its integrity. They may lack the expertise to ensure that network devices are securely configured, but attackers don’t lack the skills to exploit that. It’s understandably common to focus on the outer boundary of your network and forget about threats that come from unexpected directions or multiply internally, but it could prove costly indeed.
Compared to the cost of a data breach, all of these things are cheap and easy to set up
Cyber Insurance - Is a must have - you will need it
Cyber Insurance - Is a must have - you will need it.
It’s every healthcare organization’s nightmare to get the call that their data has been breached or hacked. As a result, many have turned to cyber insurance to protect assets and business operations.
As cyber policies and carriers lack a universal policy, there’s an even greater worst case scenario: An organization is breached, and the policy doesn’t cover what the leaders thought it did. Now, not only is the healthcare provider strapped with the burden of the breach, it wasted money on a useless cyber insurance policy.
To get a better grasp on how to choose the right policy, Healthcare IT News asked attorney Matthew Fisher, partner with Mirick O’Connell, and Jane Harper, Henry Ford Health System’s director of privacy and security risk management, to outline the biggest policy mistakes -- and how to avoid them.
Mistake #1: Rushing the process
When buying a policy, a carrier will provide a questionnaire that will evaluate your organization’s security posture, program, tools and policies. The biggest mistake is to rush the pre-policy process to see the rates and what the carrier will cover, explained Fisher.
Organizations need to be conservative with how they answer the questions, as “it could be a ground for denial, if you don’t have the policies you said you have in place,” said Fisher. “You have to make sure you’re not unintentionally misleading the insurance company when it comes to coverage.”
Often these questionnaires attempt to create a black and white policy and “it can be tough to answer correctly,” explained Fisher.
“Your ability to be as transparent and truthful upfront is critical to the nonpayment discussion,” said Harper. “If you tell the insurance company that you have everything in place and are compliant, if you tell them that and then you have an issue, and you weren’t truthful, it ends up being a legal battle.”
“When you submit your checklist that they have you fill out, meet with the underwriter to make sure you understand what you’ve documented,” she added. “You also need the copy that was provided to the insurance company because it will come back into play when you submit the final documents.”
For example, if you say you have a specific control in place, and you actually don’t, Harper explained that can create a situation where “they thought they had an understanding of something, but they didn’t.”
“Be honest, transparent and accurate -- because they can deny your policy if you were inaccurate or misleading in your responses,” she said.
Mistake #2: Lax, incomplete risk assessment
It’s easier to prevent a misleading or false statement to an underwriter, when an organization has a strong assessment and inventory of the processes and tools on the system. But far too often, hospitals “don’t know everything about the control environment,” explained Harper.
“When you talk about protecting an system and preventing a cyber incident, you have to have a good understanding of the organization’s overall control environment,” Harper said. “It’s key, as the longer it takes you to identify that you’ve had an incident, it leads to more exposure and the longer it takes to recover.”
But it’s also important to remember to update this inventory or assessment when buying new tools, merging with other organizations, hiring new staff and the like, Harper explained.
“Think about all of the activities and operations that happen,” she said. “And every three years, you’re updating a cybersecurity checklist -- that may not be frequent enough.”
For example, Harper explained that an organization filling out the policy questionnaire may have all of the right elements in place. But if another tool was purchased and the controls weren’t updated or the control was removed and the underwriter was not notified, there could be a problem.
“If those controls played into how the underwriter rated you: that can be key,” said Harper. “Think about your own home: you get additional discounts when you have a burglar alarm. So if you get one, and let them know, you may get a lower rate… But if you no longer have that control, you have to tell the carrier.”
“It’s the same kind of practice that we want to get into when we get into cyber insurance for our organization,” she added.
Mistake #3: Failing to involve the right people
Many organizations understand that security needs to exist outside of the IT team. In the same vein, it’s crucial when buying a cyber insurance policy that the same mentality is applied to make sure all of your bases are covered.
“Make sure you are talking to the right individuals,” Harper said. “The appropriate key stakeholders are not only involved with the evaluation process - how many patients, how much data, etc. -- but also the responses to the questions the policy is going to ask.”
“Risk folks typically talk about it as it relates to patients,” she continued. “Those folks are key, but in addition, you need your privacy and security risk professionals, security officers, IT leader, your key business leaders/owners and those driving the data. It’s key.”
Also crucial? Making sure the facilities team is involved, as there can sometimes be a cyber incident based on a physical issue. Harper explained that “often people tend to focus on things like electronic PHI, but there’s physical PHI. If there’s a break in at a warehouse and data is stolen, OCR considers that a breach.”
Mistake #4: Failing to understand coverage
Far too often organizations make large assumptions as to just what cyber insurance will cover. Fisher explained that these leaders are often shocked to learn that they did not receive the full spectrum of coverage they wanted.
“Relying on blind faith on those terms, or what the broker or agent is telling you is a major mistake,” said Fisher. “It’s always up to up to you to go into something with eyes fully wide open to make sure you know what you’re actually buying.”
Harper took it a step further and laid to rest a common misconception when it comes to coverage: “Insurance will not cover fines and penalties associated with noncompliance. If you’re not complaint, and you didn’t do risk assessments, cyber insurance won’t protect you from that, so don’t expect it.”
Ransomware Business Impacts, Ransomware Business Cost
Projecting the overall cost of a ransomware attack can be tricky for security executives considering the many factors that can come into play when responding to and recovering from one. Information from numerous previous incidents show the costs go well beyond any demanded ransom amount and the costs associated with cleaning infected systems.
Ransomware is defined as a form of malicious software that is designed to restrict users from accessing their computers or files stored on computers till they pay a ransom to cybercriminals. Ransomware typically operates via the crypto virology mechanism, using symmetric as well as asymmetric encryption to prevent users from performing managed file transfer or accessing particular files or directories. Cybercriminals use ransomware to lock files from being used assuming that those files have extremely crucial information stored in them and the users are compelled to pay the ransom in order to regain access.
Ransomware History
It’s been said that Ransomware was introduced as an AIDS Trojan in 1989 when Harvard-educated biologist Joseph L. Popp sent 20,000 compromised diskettes named “AIDS Information – Introductory Diskettes” to attendees of the internal AIDS conference organized by the World Health Organization. The Trojan worked by encrypting the file names on the customers’ computer and hiding directories. The victims were asked to pay $189 to PC Cyborg Corp. at a mailbox in Panama.
From 2006 and on, cybercriminals have become more active and started using asymmetric RSA encryption. They launched the Archiveus Trojan that encrypted the files of the My Documents directory. Victims were promised access to the 30-digit password only if they decided to purchase from an online pharmacy.
After 2012, ransomware started spreading worldwide, infecting systems and transforming into more sophisticated forms to promote easier attack delivery as the years rolled by. In Q3, about 60,000 new ransomware was discovered, which doubled to over 200,000 in Q3 of 2012.
The first version of CryptoLocker appeared in September 2013 and the first copycat software called Locker was introduced in December of that year.
Ransomware has been creatively defined by the U.S. Department of Justice as a new model of cybercrime with a potential to cause impacts on a global scale. Stats indicate that the use of ransomware is on a steady rise and according to Veeam, businesses had to pay $11.7 on average in 2017 due to ransomware attacks. Alarmingly, the annual ransomware-induced costs, including the ransom and the damages caused by ransomware attacks, are most likely to shoot beyond $11.5 billion by 2019.
Ransomware Business Impacts Can Be Worrisome
Ransomware can cause tremendous impacts that can disrupt business operations and lead to data loss. The impacts of ransomware attacks include:
Loss or destruction of crucial information
Business downtime
Productivity loss
Business disruption in the post-attack period
Damage of hostage systems, data, and files
Loss of reputation of the victimized company
You will be surprised to know that apart from the ransom, the cost of downtime due to restricted system access can bring major consequences. As a matter of fact, losses due to downtime may cost tens of thousands of dollars daily.
As ransomware continues to become more and more widespread, companies will need to revise their annual cybersecurity goals and focus on the appropriate implementation of ransomware resilience and recovery plans and commit adequate funds for cybersecurity resources in their IT budgets.
Consider the following examples. The Erie County Medical Center (ECMC) in Buffalo, NY, last July estimated it spent $10 million responding to an attack involving a $30,000 ransom demand. About half the amount went toward IT services, software, and other recovery-related costs. The other half stemmed from staff overtime, costs related to lost revenues, and other indirect costs. ECMC officials estimated the medical center would need to spend hundreds of thousands of dollars more on upgrading technology and employee awareness training.
Public records show that the City of Atlanta spent almost $5 million just in procuring emergency IT services following a March 2018 ransomware attack that crippled essential city services for days. The costs included those associated with third-party incident response services, crisis communication, augmenting support staff and subject matter expert consulting services.
In Colorado, Gov. John Hickenlooper had to set aside $2 million from the state disaster emergency fund after ransomware infected some 2,000 Windows systems at CDOT, the state department of transportation, this February. In less than eight weeks, CDOT officials spent more than half that amount just returning systems to normal from the attack.
Not surprisingly, industry estimates relating to ransomware damages have soared recently. Cybersecurity Ventures, which pegged ransomware costs at $325 million in 2015, last year estimated damages at $5 billion in 2017 and predicted it would exceed $11.5 billion in 2019.
For security executives trying to prepare a total ransomware cost estimate, the key is not to get fixated on the ransom amount itself. Even if you end up paying it to recover your data—something that most security analysts advocate against—the actual costs of the attack in most cases will end up being greater.
FBI: Protecting Your Networks from Ransomware
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
What is Ransomware”
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment. Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails. For additional information on Avoiding Social Engineering and Phishing Attacks.
Ransomware Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Ransomware Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. USG does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
How Law Enforcement Can Help
Any entity infected with ransomware should contact law enforcement immediately. Law enforcement may be able to use legal authorities and tools that are unavailable to most organizations. Law enforcement can enlist the assistance of international law enforcement partners to locate the stolen or encrypted data or identify the perpetrator. These tools and relationships can greatly increase the odds of successfully apprehending the criminal, thereby preventing future losses.
Federal law enforcement places a priority on conducting cyber investigations in a manner that causes minor disruption to a victim entity’s normal operations and seeks to work cooperatively and discreetly with that entity. Federal law enforcement uses investigative measures that avoid unnecessary downtime or displacement of a company’s employees. Federal law enforcement closely coordinates its activities with the affected organization to avoid unwarranted disclosure of information.
As an affected entity recovers from a cybersecurity incident, the entity should initiate measures to prevent similar incidents. Law enforcement agencies and the Department of Homeland Security’s National Cybersecurity and Communications Integration Center can assist organizations in implementing countermeasures and provide information and best practices for avoiding similar incidents in the future. Additionally, the affected organization should conduct a post-incident review of their response to the incident and assess the strengths and weaknesses of its incident response plan.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor ” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising .
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
HOW DOES RANSOMWARE WORK?
HOW DOES RANSOMWARE WORK?
Ransomware infections occur when a user opens a malicious email attachment, clicks on a malicious link, or visits a website infected with malicious code, known as a drive-by download.
Once a system is infected, the ransomware contacts a command and control (C2) server to generate an encryption key and begins encrypting files on the victim’s machine.
The ransomware runs quietly in the background performing in-depth searches of all disk folders, including removable drives and network shares, and encrypts as many files as it can.
Ransomware may also delete Shadow Volume Copies, destroy restore points, and overwrite free disk space to prevent victims from recovering their files and systems without paying the ransom.
If a system is powered off as files are being encrypted, some ransomware variants resume where they left off when the system or device is powered on again.
After files are encrypted, a ransom note is displayed on the screen with instructions on how and where to pay the ransom and the length of time before the hacker or software destroys the decryption key.
Some recent variants offer victims a ‘second chance’ to pay after the initial timer expires; however, the ‘second chance’ is often at least double the original ransom amount.
If the victim pays the ransom, the malware is supposed to contact the C2 server for the decryption key and begin decrypting the victim’s files; however, in many cases, the files are never decrypted.
Some ransomware files can delete themselves in order to avoid detection and analysis by security researchers or law enforcement.
CyberSecOP: Ransomware Remediation and Prevention Service
RANSOMWARE MITIGATION STRATEGIES
For many organizations, preventing ransomware entirely is nearly impossible, however, the impact of a successful infection can be greatly reduced if a robust data backup process is in place. Comprehensive data backups should be scheduled as often as possible and must be kept offline in a separate and secure location. The most effective method to prevent ransomware infections is to conduct regular training and awareness exercises with all employees to ensure users are proficient in safe Internet-browsing techniques and the ability to identify phishing emails. For specific recommendations for data protection, systems management, network management, mobile device management, and post-infection remediation.
5 steps for preventing ransomware
5 steps for preventing ransomware
Hardening Your Environment Against Ransomware
To avoid ransomware infection, follow these steps:
1. Back up your computers and servers regularly.
Regularly back up the files on both the client computers and servers. Either back up the files when the computers are offline or use a system that networked computers and servers cannot write to. If you do not have dedicated backup software, you can also copy the important files to removable media. Then eject and unplug the removable media; do not leave the removable media plugged in.
2. Lock down mapped network drives by securing them with a password and access control restrictions.
Use read-only access for files on network drives, unless it is absolutely necessary to have write access for these files. Restricting user permissions limits which files the threats can encrypt.
3. Deploy and enable the following Endpoint Protection:
Implement and managed endpoint antivirus on all endpoint to prevent ransomware, most ransomware can be detected by popular antivirus.
4. IPS/IDS
IPS blocks some threats that traditional virus definitions alone cannot stop. IPS is the best defense against drive-by downloads, which occurs when software is unintentionally downloaded from the Internet. Attackers often use exploit kits to deliver a web-based attack like CryptoLocker through a drive-by download.
See Enabling network intrusion prevention or browser intrusion prevention.
5. Download the latest patches for web application frameworks, web browsers, and web browser plug-ins.
Attacking exploit kits cannot deliver drive-by downloads unless there is an old version of a plug-in to exploit, such as Flash. Historically, attacks were delivered through phishing and web browsers. Recently, more attacks are delivered through vulnerable web applications, such as JBOSS, WordPress, and Joomla.
6. Use an email security product to handle email safely.
CryptoLocker is often spread through spam emails that contain malicious attachments. Scanning inbound emails for threats with a dedicated mail security product or service is critical to keep ransomware and other malware out of your organization. For important advice and recommendations, see:
How to remove ransomware
There is no ransomware removal tool or CryptoLocker removal tool. Instead, if your client computers do get infected with ransomware and your data is encrypted, follow these steps:
1. Do not pay the ransom.
If you pay the ransom:
· There is no guarantee that the attacker will supply a method to unlock your computer or decrypt your files.
· The attacker uses the ransom money to fund additional attacks against other users.
2. Isolate the infected computer before the ransomware can attack network drives to which it has access.
3. Update the virus definitions and scan the client computers.
New definitions are likely to detect and remediate the ransomware. Configure Endpoint Protection to automatically downloads virus definitions to the client, as long as the client is managed and connected to the Symantec Endpoint Protection Manager.
4. Restore damaged files from a known good backup.
No security Endpoint Protection cannot decrypt the files that ransom lockers have sabotaged.
Submit the malware to antivirus provider.
If you can identify the malicious email or executable, submit it to antivirus provider.