CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
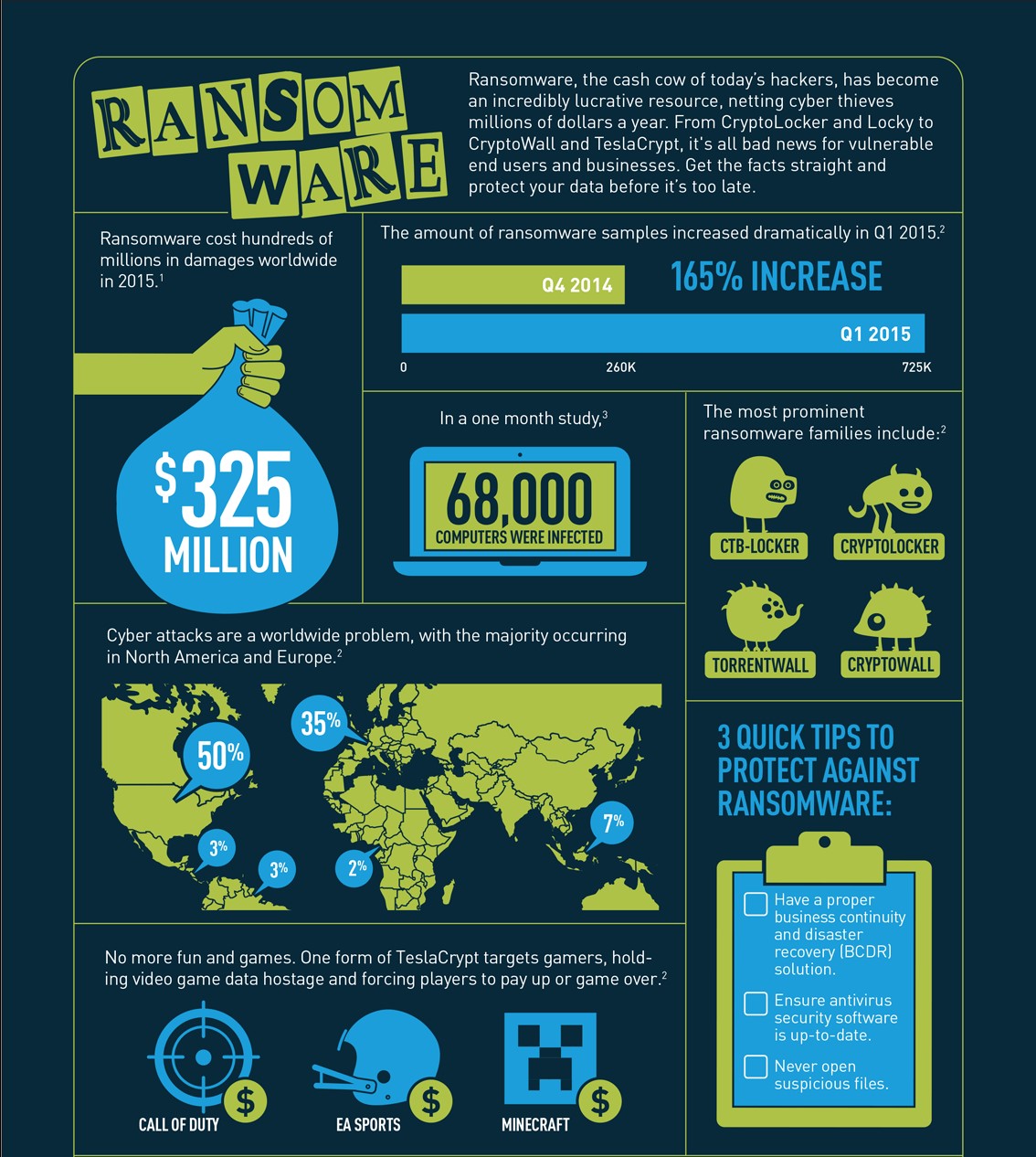
Popular Ransomware & Largest Data Breaches
Our data breach incident response team works with clients to build a timely, comprehensive & compliant response plan to mitigate data loss. They have done some research and came up with the following. The Incident response team assist clients with data breach response plan, which provides a roadmap your organization can follow in the event a data breach is discovered.
Largest data breaches?
LinkedIn | 117 million
Cybercriminals absconded with email addresses and encrypted passwords for 117 million LinkedIn users in this 2012 data breach. The passwords were encrypted, right? No big deal. Unfortunately, LinkedIn used that darn SHA1 encryption we talked about earlier. And if you have any doubts that your stolen passwords are being decrypted, CyberSecOp News reported on hacked LinkedIn accounts being used in an InMail phishing campaign. These InMail messages contained malicious URLs that linked to a website spoofed to look like a Google Docs login page by which cybercriminals harvested Google usernames and passwords. Still better than that temp-to-perm ditch-digging job recruiters keep sending you.
eBay | 145 million
In early 2014, cybercriminals clicked “Steal It Now” when they broke into the network of the popular online auction site and pinched the passwords, email addresses, birth dates, and physical addresses for 145 million users. One positive takeaway, financial information from sister site PayPal was stored separately from user information in a practice known as network segmentation (more on that later). This had the effect of limiting the attack and prevent criminals from getting to the really sensitive payment info.
Equifax | 145.5 million
The credit reporting company Equifax took a hard hit to their own “credit” score, at least in the eyes of American consumers, when the company announced they had experienced a data breach back in 2017. All of this could have been avoided if Equifax just kept their software up-to-date. Instead, hackers were able to take advantage of a well-known software bug and hack into the underlying software supporting the Equifax website. What makes the Equifax data breach so awful is not the size, though considerable; rather, it’s the value of the information stolen. The perpetrators made off with the names, birthdates, Social Security numbers, addresses, and drivers license numbers for 145.5 million Americans. Add to that approximately 200,000 credit card numbers and you get one of the worst data breaches in terms of sensitivity of the compromised data.
Under Armour | 150 million
Sports apparel company Under Armour’s slogan is “Protect This House.” Apparently, they didn’t take their own advice when their diet and exercise app MyFitnessPal was hacked in February of 2018. In the attack, cybercriminals managed to steal the usernames, emails and encrypted passwords for 150 million users. Under Armour did well to announce the data breach within a week of its discovery. On the flip side, the company used weak SHA1 encryption on some of the stolen passwords, meaning criminals could crack the passwords and reuse them on other popular websites.
Exactis | 340 million
The Exactis data breach is a little different in the sense that there’s no proof cybercriminals stole any data. However, the cybersecurity researcher who discovered the “data breach” believes that criminals did. Speaking with Wired, Vinny Troia said, “I’d be surprised if someone else didn't already have this.” Exactis, a Florida-based marketing firm, had records for 340 million Americans (that’s every single US citizen) stored on an unsecure server. Any cybercriminal could have found the data using a special search engine called Shodan that lets users find Internet-connected devices. While the breach did not include data like credit card and Social Security numbers it did include detailed lifestyle information, like religion and hobbies, that could be used in phishing attacks.
Myspace | 360 million
Remember Myspace? The social networking site that came before Facebook? If you had a Myspace account and you reuse passwords from site-to-site, you may be at risk. Cybercriminals stole data on 360 million pre-2013 Myspace users. This may not seem like a big deal, but the stolen passwords used that weak SHA1 encryption we keep talking about. As mentioned previously, criminals can try and reuse your old passwords on other popular sites in a credential stuffing attack.
AdultFriendFinder | 412 million
You’d think a site like AdultFriendFinder, billed as the “World’s Largest Sex and Swinger Community,” would know to use protection. Instead cybercriminals penetrated the site’s defenses and stole usernames, encrypted passwords, emails, date of last visit, and membership status for 412 million accounts. A previous data breach at AdultFriendFinder, affecting 4 million users, included sexual preference and whether or not the user was looking for an extramarital affair. Yikes.
Yahoo | 500 million
Yahoo? More like oh no! Yahoo makes its first appearance on our countdown with the 2014 attack on the former Internet tech giant. At its height during the dot-com boom years, Yahoo was one of the most visited sites on the web. This huge attack surface caught the attention of various bad actors. In the attack, cybercriminals made off with the personal information for as many as 500 million Yahoo users. In 2017, the US Department of Justice filed charges against four Russian nationals in connection with the Yahoo attack, two of whom were Russian government officials. To date, only one of the Russians has seen the inside of a jail cell.
Marriott International | 500 million
Just like housekeeping, hackers ignored the “Do Not Disturb Sign” and caught the world’s largest hotel company Marriott International in a compromising situation. The 2014 Starwood-Marriott attack wasn’t discovered until September of 2018. During the intervening years cybercriminals had unrestricted access to the personal information of 500 million Starwood-Marriott customers—anyone who ever booked a reservation at a Starwood property—including names, mailing addresses, phone numbers, email addresses, passport numbers, and dates of birth.
Yahoo—again | 3 billion
Yahoo has the embarrassing distinction of being the only company to make our list of biggest data breaches twice. To add insult to injury, Yahoo also takes the top spot. In August of 2013, cybercriminals stole data on every Yahoo user in the world—all three billion of them. The sheer size of the data breach is difficult to fathom. Over one-third of the world’s population was affected. When the attack was first revealed in 2016, Yahoo claimed only one billion of its users were affected by the data breach, later changing the figure to “all Yahoo user accounts” less than a year later. The timing couldn’t have been worse. At the time Yahoo revealed the updated data breach numbers, the company was in negotiations to be acquired by Verizon. News of the data breach allowed Verizon to scoop up Yahoo at a fire sale price. Yahoo was acquired by Verizon in 2017.
Popular Ransomware:
Ryuk: Ryuk the new ransomware in town that’s very carefully targeting enterprise and businesses. Say hello to Ryuk. In the first two weeks after its August debut, the ransomware has made their cyber attackers over $640,000 USD. By contrast, SamSam has taken about three years to make its author about $6 million USD.
Dharma: Dharma ransomware appeared as early as 2006, and has continued to this day with regular updates. Because of the continuous evolution of this ransomware, free decryptors for previous malware versions were released by Kaspersky and Eset. Unfortunately, files encrypted with the new variants of Dharma ransomware are not currently decryptable for free as was the case for the older variants.
LeChiffre: "Le Chiffre", which comes from the French noun "chiffrement" meaning "encryption", is the main villain from James Bond's Casino Royale novel who kidnaps Bond's love interest to lure him into a trap and steal his money. Unlike other variants, hackers must run LeChiffre manually on the compromised system. Cyber criminals automatically scan networks in search of poorly secured remote desktops, logging into them remotely and manually running an instance of the virus.
Locky: Locky's approach is similar to many other types of ransomware. The malware is spread in an email message disguised as an invoice. When opened, the invoice is scrambled and the victim is instructed to enable macros to read the document. When macros are enabled, Locky begins encrypting a large array of file types using AES encryption.
NotPetya: Initial reports categorized NotPetya as a variant of Petya, a strain of ransomware first seen in 2016. However, researchers now believe NotPetya is instead a malware known as a wiper with a sole purpose of destroying data instead of obtaining a ransom.
Petya: Unlike some other types of ransomware, Petya encrypts entire computer systems. Petya overwrites the master boot record, rendering the operating system unbootable.
Spider: A form of ransomware spread via spam emails across Europe. Spider ransomware is hidden in Microsoft Word documents that install the malware on a victim’s computer when downloaded. The Word document, which is disguised as a debt collection notice, contains malicious macros. When these macros are executed, the ransomware begins to download and encrypt the victim's data.
TeslaCrypt: TeslaCrypt is another new type of ransomware on the scene. Like most of the other examples here, it uses an AES algorithm to encrypt files. It's typically distributed via the Angler exploit kit specifically attacking Adobe vulnerabilities. Once a vulnerability is exploited, TeslaCrypt installs itself in the Microsoft temp folder.
TorrentLocker: TorrentLocker is typically distributed through spam email campaigns and is geographically targeted with email messages delivered to specific regions. TorrentLocker is often referred to as CryptoLocker, and it uses an AES algorithm to encrypt file types. In addition to encoding files, it also collects email addresses from the victim’s address book to spread malware beyond the initially infected computer—this is unique to TorrentLocker.
WannaCry: WannaCry is a widespread ransomware campaign that is affecting organizations across the globe. The ransomware hit over 125,000 organizations in over 150 countries. The ransomware strain is also known as WCry or WanaCrypt0r and currently affects Windows machines through a Microsoft exploit known as EternalBlue.
ZCryptor: ZCryptor is a self-propagating malware strain that exhibits worm-like behavior, encrypting files and also infecting external drives and flash drives so it can be distributed to other computers.
SamSam: SamSam ransomware is a custom infection used in targeted attacks, often deployed using a wide range of exploits or brute-force tactics. Based on our own run-ins with the infection, we’ve observed that attacks were made on targets via vulnerable JBoss, and RDP host servers during a previous wave of SamSam attacks in 2016 and 2017.
KeyPass: KeyPass ransomware first appeared on 8 August and so far has spread to hundreds of victims in more than 20 countries around the world via fake software installers which download the ransomware onto the victim's PC.
How to Clean Malware From Your Website
Cyberthreats will continue to grow as technology and big data evolve. Whether the motive is to steal money and data or simply wreak havoc, cybercriminals often have a solid return on investment of their time when they attack unprotected and vulnerable websites. They target websites with software that has a malicious intention – also known as malware – and they aren’t slowing down anytime soon.
Malware can change the appearance of your website, files, and even alter your computer operating system entirely. Cybercriminals gain unauthorized access to these systems by exploiting vulnerabilities found in weak entry points within system software. In fact, malware can cause your website to be flagged and removed from search engines, ultimately resulting in loss of traffic, decreased trust from your consumers or visitors, and a potential negative impact on your bottom line.
The impacts of malware can often depend on the overall goal of the attacker. Cyber-attacks can range from site defacements to a phishing email, and each has a different agenda. For example, a website defacement can be thought of as online graffiti, and the intention could simply be to make a statement of some kind. If you have an online business or simply have an online presence, there is a good chance you could be faced with malware on your website. To help you prepare, we’ve provided the following simple steps on how to remove malware from your website.
How to Determine if Your Website Has Been Infected By Malware
Cleaning your website of malware first requires identifying whether the site has been infected. An infected website has the following characteristics:
● Slow loading pages, or slow downloads
● Advertisements that pop up on the page, and re-pop up or do not go away even after attempting to close them
● Changes in your website theme or general appearance
● Spam email flooding your inbox
● Website comments full of comment spam or advertisements
● Traffic redirection to other websites resulting in low site traffic on your own page
● Removal from the general search results on various search engines
How to Clean Your Website
Step 1: Back up your site content
Before starting the malware removal process – always make a backup of your website files and database. This will allow you to restore your website if anything goes awry during the malware removal process such as file corruption. Look for a backup in your file manager or in a local drive as this may come in handy to replace files damaged by malware.
Step 2: Identify the malware
Use the file manager within your web hosting account or download an FTP manager to download and review your website files. This could be a time-consuming process depending on how many pages make up your website, but it’s a critically important step. When you do find files that look suspicious, review the code within the files for clues such as eval, base64, fromCharcode, gzinflate, shell_exec or error_reporting().
Step 3: Replace damaged files
Once malware has been successfully removed by restoring the file from a backup or completely removing the malicious file, try loading your website to ensure you are able to successfully view the content on the page. If your defacement is still visible or you have visible scripting errors on your page you must keep looking for the malware affecting your site. As a best practice, keep a current copy of the clean website files and database as well. This should be kept offsite in the event your website is re-infected.
Step 4: Enhance your website defense mechanisms
Removing malware and replacing all of your files can only do so much. If you don’t practice and implement proper cybersecurity protocols, such as keeping your software up-to-date and backing up your content, you’re leaving your online assets vulnerable to another cyber-attack. As a best practice, you should aim to improve your cyber defenses by implementing a web application firewall (WAF) to block cyber threats before they ever hit your website. In addition, it’s recommended to use a website scanner that can automatically detect and remediate malware and other threats as they happen.
Step 5: Protect your online accounts
It’s important to always use strong passwords for every account. Never write your passwords in a notebook or keep them in a spreadsheet online for someone to find. Always use a strong password that includes numbers, letters, and special characters. However, even if you are the only one who knows your password you aren’t doing yourself any favors by using the same strong password over and over for each account. Using a password manager will save you the hassle of remembering a plethora of passwords to logging to your accounts.
Staying Safe from Malware in the Future
Maintaining a clean and malware-free website is fundamental to the success of any website. And, if the website in question is connected to a business, it could prevent you from potential legal action. Case in point - the recent Equifax and Capital One data breaches have both resulted in class action lawsuits against each company, and new data breaches continue to occur resulting in additional lawsuits.
The truth is, if you are running a website of any kind, you owe it to your visitors to have security measures in place. Just a few of the things you can do include, but are not limited to:
● Installing a web application firewall (WAF) to protect your website and web applications from harmful traffic (such as cybercriminals and bad bots), and other cyber threats
● Use a malware scanner to automatically check your website for malicious software and cyber threats that can harm your website
● Update your website often, and keep a clean backup of all data and files at all times, so that in the event of infection you can install the clean copy and get back online faster
● Use a password manager to securely manage the logins for all of your online accounts
Conclusion
Malware can be dangerous for any website, and removing it is vital for the safety and protection of both the website owner, and its visitors. Therefore, understanding what malware is and how to remove it is the first step towards ensuring a malware-free site. Hopefully, the above information has inspired you to keep an eye on your website and ensure your business is protected from cybercriminals.
CyberSecOp and Coronet announce partnership
CyberSecOp and Coronet announce partnership
Bringing Coronet’s AI and cloud technology extends CyberSecOp capability to protect lean IT and SMB companies.
Stamford, CT – September 18, 2019 – CyberSecOp, a Cyber Security consulting firm based in Stamford, CT announced today its partnership with Coronet, the world leader in security as-as-service powered by AI and cloud.
Coronet, which provides security for cloud applications, BYOD and communications over public networks, brings enterprise grade security to companies of any size.
With Coronet’s AI platform, CyberSecOp will identify and remediate SaaS vulnerabilities, malware and ransomware spread through cloud services, malicious behavior by employees, and control access to SaaS based on the security posture of the device and network the user is using.
“We were very impressed with Coronet’s ability to identify and remediate risks. Most of our customers are moving to cloud platforms such as Office 365, Dropbox, Salesforce, and Slack to name a few. Practically all of our customers adopted a BYOD strategy.” Said Jeffery Walker CISO of CyberSecOp. “These cost and convenience driven advances leave organizations extremely exposed from a cybersecurity and regulatory perspective, and Coronet helps us protect our customers against these threats.”
Coronet’s platform not only protects against cyber threats, but identifies PII, PCI, and PHI regulatory violations in files that are stored in cloud services or sent through them. As regulators become more aggressive, with fines and penalties skyrocketing, Coronet’s ability to identify potential violations eliminates such regulatory exposure.
“We are very excited to have CyberSecOp join the Coronet family. We are very impressed with the caliber of talent that we saw at CyberSecOp, and know that Coronet in their hands would alleviate many risks and concerns their customers currently experience.”
About CyberSecOp
CyberSecOp Security Consulting Services is a leading provider in managed security and compliance services, providing clients with a comprehensive security team, with a board-level cyber security consultant to drive organization strategic planning. The CyberSecOp team will provide strategic leadership, security strategy, compliance, & corporate security consulting, aligning your GRC activities to business performance drivers. To explore our security solutions and services, visit us at www.cybersecop.com or follow us at @CyberSecOp on social media.
About Coronet
Coronet is a world leader in providing organizations of every size with security for their cloud applications, bring-your-own-devices, and communications over public networks. With over 2.5 million users, Coronet's platform uses AI to detect and mitigate threats, eliminating the need for a security team to chase down security events. Provided as a subscription service, with nothing to install on premises, Coronet brings enterprise grade cyber security to organizations of any size, at an affordable price, eliminating the complexity and laborious nature of traditional security platforms. To learn more about Coronet, visit us at www.coro.net or follow @coronetworks on social media.
Decrease Potential Data Breach, with Simple Security Control
Some senior management folks might find this strange, but you can significantly make your organization harder to breach. In fact, just a handful of defenses can do more to lower your cybersecurity risk than anything else. These include fighting social engineering and phishing better, patching the most likely to be attacked software far better, and requiring multi-factor authentication (MFA) for all logons.
Zero-day and information system protection
Because zero-day flaws usually refer to software that is widely in use, it’s generally considered good form if one experiences such an attack to share any available details with the rest of the world about how the attack appears to work — in much the same way you might hope a sick patient suffering from some unknown, highly infectious disease might nonetheless choose to help doctors diagnose how the infection could have been caught and spread. patch management is critical in protecting information technology systems.
Ransomware Breach and Criminals
The typical use case for ransomware is a shotgun approach type distribution campaign of dropping ransomware on people's machines, and then you charge them for getting their data or services back,” says Jeffery Walker, CISO at CyberSecOp. “Another use case is for covering tracks. These tools have the façade of ransomware: They would encrypt data, they would post a ransom note, and they would ask for money. They will even give you details on how to pay, but they're used to remove things from the endpoint while throwing off defenders into believing that the reason why that data was lost was because of a random hit by ransomware, but in some cases this is a cover up of a more bigger breach”
Vulnerabilities and Exploits
These are all vulnerabilities that could be exploited by cybercriminals bent on stealing personally identifiable information and protected health information – activity that could also play havoc disrupting healthcare delivery processes.
The study, based on network traffic data monitored by CyberSecOp over a six-month period, found the most prevalent method attackers use to hide command-and-control communications in healthcare networks was hidden HTTPS tunnels.
CyberSecOp compliance solutions deliver cost-effective data protection, data discovery, data classification and data loss prevention for data privacy and compliance.
Ransomware Breach and Ransomware Prevention
Cyber-criminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, TeslaCrypt., RyUK and others. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks. CyberSecOp use AI to help organization protect their data, and provide ransomware Incident response and remediation services.
HOW DO I RESPOND TO RANSOMWARE?
Implement your security incident response and business continuity plan. It may take time for your organization’s IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your organization’s essential functions according to your business continuity plan. Organizations should maintain and regularly test backup plans, disaster recovery plans, and business continuity procedures.
Contact law enforcement immediately. We encourage you to contact a local FBI or USSS field office immediately to report a ransomware event and request assistance. Contact CyberSecOp Security Consulting Firm for ransomware incident response & digital forensic services.
There are serious risks to consider before paying the ransom. We do not encourage paying a ransom. We understand that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. As you contemplate this choice, consider the following risks:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.
• Some victims who paid the demand have reported being targeted again by cyber actors.
• After paying the originally demanded ransom, some victims have been asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
Ransomware Incident Response from CyberSecOp, the firm that provide ransomware protection, and ransomware ransom payment.
WHAT IS RANSOMWARE?
Ransomware is a type of malicious software cyber actors use to deny access to systems or data. The malicious cyber actor holds systems or data hostage until the ransom is paid. After the initial infection, the ransomware attempts to spread to shared storage drives and other accessible systems. If the demands are not met, the system or encrypted data remains unavailable, or data may be deleted.
HOW DO I PROTECT MY NETWORKS?
A commitment to cyber hygiene and best practices is critical to protecting your networks. Here are some questions you may want to ask of your organization to help prevent ransomware attacks:
1. Backups: Do we backup all critical information? Are the backups stored offline? Have we tested our ability to revert to backups during an incident?
2. Risk Analysis: Have we conducted a cybersecurity risk analysis of the organization?
3. Staff Training: Have we trained staff on cybersecurity best practices?
4. Vulnerability Patching: Have we implemented appropriate patching of known system vulnerabilities?
5. Application Whitelisting: Do we allow only approved programs to run on our networks?
6. Incident Response: Do we have an incident response plan and have we exercised it?
7. Business Continuity: Are we able to sustain business operations without access to certain systems? For how long? Have we tested this?
8. Penetration Testing: Have we attempted to hack into our own systems to test the security of our systems and our ability to defend against attacks?
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
Ransomware?
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment.
Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails.
You will need and experience security consulting firm to guide you remediate the ransomware.
Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and contact CyberSecOp to request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. CyberSecOp does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key. CyberSecOp can negotiate the ransom for you, we have a 60% t rate of reducing the ransom.
• Paying could inadvertently encourage this criminal business model.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising.
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
Ransomware Attack: Threats, and Countermeasures
When you combine cryptography with malware, you get a very dangerous mix of problems. This is a type of computer virus that goes by another name, “ransomware”. This type of virus is part of a field of study called “cryptovirology”. Through the use of techniques called phishing, a threat actor sends the ransomware file to an unknowing victim. If the file is opened it will execute the virus payload, which is malicious code. The ransomware runs the code that encrypts user data on the infected computer or host. The data are user files like documents, spreadsheets, photos, multimedia files and even confidential records. The ransomware targets your personal computer files and applies an encryption algorithm like RSA which makes the file inaccessible. The only way to access them is if the user pays a ransom to the threat actor by following instructions which appear encoded into the encrypted files. Thus it is called ransomware, because a form of payment is demanded in order to fix the problem.
Once they have all publicly available email addresses, the fun starts. The more of your email addresses that are floating out there, the bigger your attack footprint is, and the higher the risk is. It’s often a surprise how many addresses are actually out there. Now they can send all employees an email supposedly coming from Accounting, Human Resources, the CEO or perhaps the mail room, and social engineer your users to click on a link. almost 90 percent of attack are done via the internet, based on the new software model, and yes the bad guys are also moving to the cloud. Software is shifting away from locally-installed apps to Software as a Service web applications that run in the cloud. Criminals are cashing in on this trend, which has led to the creation of Ransomware as a Service (RaaS), a growing threat to business.
RaaS refers to various online malware exploits that bad actors can use to attack the IT assets of businesses and individuals. These attack programs are created by criminal entrepreneurs who sell their services to other criminals. The people who buy these programs then extort or blackmail their victims by holding computer systems to ransom.
How does Ransomware spread?
Ransomware is typically spread through phishing emails that contain malicious attachments. These emails appear to come from a legitimate source and give a compelling reason that the document is important. Malicious attachments are often PDF, ZIP, DOC, XLS, PPT files that appear as invoices, legitimate business documents, or other work-related files. In some cases, Ransonware may end up on your computer by visiting infected web sites. To avoid malicious drive-by downloads, ensure that antivirus and all installed software is up-to-date.
How to Mitigate the Risk of Ransomware Infections
These recommendations are not comprehensive but provide general best practices.
Securing Networks and Systems
Have an incident response plan that includes what to do during a ransomware event.
Backups are critical. Use a backup system that allows multiple iterations of the backups to be saved, in case a copy of the backups includes encrypted or infected files. Routinely test backups for data integrity and to ensure it is operational.
Use antivirus and anti-spam solutions. Enable regular system and network scans with antivirus programs enabled to automatically update signatures. Implement an anti-spam solution to stop phishing emails from reaching the network. Consider adding a warning banner to all emails from external sources that reminds users of the dangers of clicking on links and opening attachments.
Disable macros scripts. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full office suite applications.
Keep all systems patched, including all hardware, including mobile devices, operating systems, software, and applications, including cloud locations and content management systems (CMS), patched and up-to-date. Use a centralized patch management system if possible. Implement application white-listing and software restriction policies (SRP) to prevent the execution of programs in common ransomware locations, such as temporary folders.
Restrict Internet access. Use a proxy server for Internet access and consider ad-blocking software. Restrict access to common ransomware entry points, such as personal email accounts and social networking websites.
Apply the principles of least privilege and network segmentation. Categorize and separate data based on organizational value and where possible, implement virtual environments and the physical and logical separation of networks and data. Apply the principle of least privilege.
Vet and monitor third parties that have remote access to the organization’s network and/or your connections to third parties, to ensure they are diligent with cybersecurity best practices.
Participate in cybersecurity information sharing programs and organizations, such as MS-ISAC and InfraGard.
Securing the End User
Provide social engineering and phishing training to employees. Urge them not to open suspicious emails, not to click on links or open attachments contained in such emails, and to be cautious before visiting unknown websites.
Remind users to close their browser when not in use.
Have a reporting plan that ensures staff knows where and how to report suspicious activity.
Responding to a Compromise/Attack
Immediately disconnect the infected system from the network to prevent infection propagation.
Call CyberSecOp.com Ransomware Response Team: They provide remediation and bitcoin payment services.
Determine the affected data as some sensitive data, such as electronic protected health information (ePHI) may require additional reporting and/or mitigation measures.
Determine if a decryptor is available. Online resources such as No More Ransom! can help.
Restore files from regularly maintained backups.
Report the infection. It is highly recommended that SLTT government agencies report ransomware incidents to MS-ISAC. Other sectors and home users may report to infections to local Federal Bureau of Investigation (FBI) field offices or to the Internet Crime Complaint Center (IC3).
Ransomware Checker & Removal Tools
Why You Need a Cybersecurity Management Program
Many organization’s cybersecurity teams (or information security teams as they used to be known) continue to struggle to communicate cybersecurity issues to senior leadership. Likewise, senior management also struggles to effectively articulate cybersecurity strategy to technical cybersecurity personnel. It is as though two parts of the same organization speak foreign languages to one another, and each party has a very limited, or no, knowledge of the other party’s language. However, it does not have to be like this.
Why so many organizations struggle with Cyber Security
Failure to communicate issues is most often revealed in grassroots cybersecurity initiatives that have evolved into corporate cybersecurity programs. Typically, this resulted from an enterprise in startup mode implementing solutions to address specific technical challenges. Unfortunately, many organizations continue to employ a similar approach to secure much larger and more complex environments against threats that outmatch the capabilities of their original solutions. No longer simply a technical solution, cybersecurity management has become a business function in today’s industry. As a business function, a greater level of integration with other business units requires a greater level of transparency and performance reporting. The evolution of grassroots cybersecurity programs rarely results in the kind of mature cybersecurity solutions that are aligned with, and address business needs. And why should they? The initial programs were designed to solve technical challenges, such as preventing virus outbreak or infection, stopping cyber attackers from compromising or stealing valuable information. Such initial cybersecurity efforts were neither designed as business functions nor defined in business terms.
CyberSecOp Comprehensive Security Program - Going beyond compliance
Cyber Security Program Key Success Factors
The following key success factors are common to many successful cybersecurity programs. The programs:
Support and drive strong governance attitudes and actions
Are designed, developed, and implemented in a similar way to other business functions
Adopt a standard framework approach, usable for an extended period of many years with little or no changes to that framework
Are measureable in terms of their effectiveness
Organizations and executives that drive successful cybersecurity programs do so in the same manner as other successful business initiatives. Executives succeed at this not because of industry pressure, but because each aims to improve their organization. Having identified the opportunity, executives evaluate whether the initiative poses additional risks to their organizations and decide whether to accept this additional risk or not. After accepting such risk, executive sponsors continue to evaluate initiatives toward implementation. Even when initiatives are operational, executives still employ strong governance methods, including internal audit teams, to manage and monitor the effectiveness and efficiency of these initiatives. This business approach has become institutionalized across most enterprise units with the exception of IT and cybersecurity. Key stakeholders in IT and cybersecurity often claim that cybersecurity management programs are too technical, only internal facing, or too complex, to properly develop and implement using this approach.
The truth is if these same IT and cybersecurity groups adopted a common framework and designed their cybersecurity management programs based on said framework, cybersecurity management would truly become just a standard business function in their enterprises. Unfortunately, the cybersecurity world does not agree on a standard cybersecurity framework across all countries, industries, and states. Analysis of the commonalities and differences between these standard frameworks show that it is possible to create a universal cybersecurity management framework to address all countries, industries, and states. Such a framework is not firmly associated with any particular cybersecurity standard and can be adapted during implementation to address any specific security standard that organizations using it wishes to follow. This paper introduces a cybersecurity management framework where it is apparent that a successful approach is not too technical, addresses both internal and external concerns, and is not overly complex to implement, operationalize, and manage over the long term.
CyberSecOp Cyber Security Management - Aligning businesses with security
Cybersecurity Management Framework
The design of the CyberSecOP cybersecurity management framework (CMF) assumes cybersecurity management is a business function.
The framework, as a business function, is comprised of three discrete pillars with each subsequent layer unfolding increasing levels of specificity as follows:
The Executive Management (Strategy) Pillar directs Governance and Planning initiatives that drive the framework forward to operation.
The Executive Management Pillar requires people to identify why cybersecurity is needed, consider the business issues, and then define, document, and publish the direction the required cybersecurity program will adopt.
The Operations Pillar that defines what the cybersecurity program must address to comply with the requirements specified in the strategy, what supporting functions are needed, and what level of reporting/ governance monitoring should be provided. These needs are supported through the security intelligence, IT and Cybersecurity Assurance and IT Risk Management operations sub-pillars.
The Operations Pillar requires definitions of documented operational standards, processes, procedures, and other collateral that specify what operators should do and how they should do it.
The Tactical (Technology) Pillar defines how required cybersecurity controls mandated in the Operations and Executive Management pillars will be applied to the systems, networks and applications used by the organization and how evidence will be provided to management that the security controls implemented actually address the specific requirements and that they perform their job as expected.
The security controls in the Tactical pillar, whether requiring technology or not, are responsible for securing all aspects of an enterprise computing environment, continuously monitoring the environment for security events, collecting and analyzing captured events, and reporting defined security metrics, some of which are provided to the SLT.
Addressing Cybersecurity Challenges
Although addressing cybersecurity challenges with just three pillars is perfectly possible, adopting and using it in that way is difficult and potentially open to error or misinterpretation. To minimize these issues, these macro-level pillars must be divided into more manageable chunks. The CyberSecOp LocPar subdivides its three macro pillars into seven discrete focus areas:
Executive Management: Key decisions and accountability required to drive the program
IT Risk Management: Reducing risk exposure to the organization to a level acceptable to the SLT and Board of Directors.
Cybersecurity Intelligence: Required to provide the cybersecurity and IT teams with appropriate information to achieve and surpass IT Risk Management goals.
IT and Cybersecurity Assurance: Required to provide evidence to management and especially the SLT that their investments in cybersecurity are delivering the benefits they expected.
Secure Network: Required to support secure, on demand access to information to authorized personnel no matter where it is located within, or external to, the organization.
Secure Systems: Required to provide controlled access to applications, data and devices according to the identity of the requesting party. This focus area also includes how data is protected, whether at rest, or in transit.
Secure Applications: Required to control access to data and other networks, systems and applications according to the identity of the requesting party. For internally developed applications, requirements extend to how the application was designed, developed and managed throughout the whole development lifecycle.
Summary
Development, implementation, and maintenance of a cybersecurity management program for an organization is no small undertaking. However, the overall value that organizations achieve through development and implementation of such programs includes reduced instances of successful cyber attacks. Moreover, a cybersecurity management program provides organizations with a means to reduce a successful attack’s impact on the bottom line due to its programmatic predefined approach for identifying and responding to cybersecurity incidents. Read more about cybersecurity management programs and CyberSecOp Cybersecurity Services at https://www.cybersecop.com/
Addressing Cyber Threats and Enabling Security in your Enterprise
Cybersecurity threats from hacktivists, criminals, and hostile nation states are enough to keep government officials, businesses, and consumers up at night. These attacks are growing in sophistication and frequency and pose serious threats to our national and economic security.
Everyone impacted by these vicious and dangerous acts must work together to help prevent, protect against, and effectively respond to them.
What are the biggest cyber threats CISOs are worried about in 2019? In today's age of breaches, staying ahead of cyber threats is becoming more critical than ever. Dive into how organizations are addressing the threat of cyber attacks, how they are measuring risk, and what they are doing about improving security from some of the top experts in the field.
Ransomware is still a large risk, affecting a large number of businesses
Data Loss and Data Breach based on information available on dark web, proves that organization can’t protect customers data.
Small business with no security program are at risk more than large organization.
All industry need to have some type of cyber regulations based on secure standards such as NIST or ISO.
What can business do, to enable a stronger security posture in their enterprise
Businesses adopt standalone cyber insurance policies as boards and executives wake up to cyber liability. As boards and executives experience and witness the impact of cyber attacks, including reduced earnings, operational disruption, and claims brought against directors and officers, businesses will turn to tailored enterprise cyber insurance policies, rather than relying on “silent” components in other policies. Adoption will spread beyond traditional buyers of cyber insurance, such as retail, financial, and healthcare sectors, to others vulnerable to cyber-related business disruption, including manufacturing, transportation, utility, and oil and gas.
As the physical and cyber worlds collide, chief risk officers take center stage to manage cyber as an enterprise risk. As sophisticated cyber attacks generate real-world consequences that impact business operations at increasing scale, C-suites will wake up to the enterprise nature of cyber risk. In 2018, expect CROs to have a seat at the cyber table, working closely with chief information security officers (CISOs) to help organizations understand the holistic impact of cyber risk on the business.
Regulatory spotlight widens and becomes more complex, provoking calls for harmonization. EU holds global companies to account over General Data Protection Regulation (GDPR) violation; big data aggregators come under scrutiny in the U.S. In 2018, regulators at the international, national and local levels will more strictly enforce existing cybersecurity regulations and introduce new regulations. Expect to see EU regulators holding major U.S. and global companies to account for GDPR violations. Across the Atlantic, big data organizations (aggregators and resellers) will come under scrutiny on how they are collecting, using, and securing data. Industry organizations will push back on regulators, calling for alignment of cyber regulations.
Criminals look to attack businesses embracing the Internet of Things, in particular targeting small to mid-sized businesses providing services to global organizations. In 2018, global organizations will need to consider the increased complexities when it comes to how businesses are using the IoT in relation to third-party risk management. The report predicts large companies will be brought down by an attack on a small vendor or contractor that targets the IoT, using it as a way into their network. This will serve as a wake-up call for large organizations to update their third-party risk management, and for small and mid-sized businesses to implement better security measures or risk losing business.
As passwords continue to be hacked, and attackers circumvent physical biometrics, multi-factor authentication becomes more important than ever before. Beyond passwords, companies are implementing new methods of authentication – from facial recognition to fingerprints. However, these technologies are still vulnerable and as such, the report anticipates that a new wave of companies will embrace multi-factor authentication to combat the assault on passwords and attacks targeting biometrics. This will require individuals to present several pieces of evidence to an authentication instrument. With the new need for multi-factor authentication, and consumer demand for unobtrusive layers of security, expect to see the implementation of behavioral biometrics.
Criminals will target transactions that use reward points as currency, spurring mainstream adoption of bug bounty programs: Companies beyond the technology, government, automotive and financial services sectors will introduce bug bounty platforms into their security programs. As criminals target transactions that use points as currency, businesses with loyalty, gift and rewards programs –such as airlines, retailers, and hospitality providers– will be the next wave of companies implementing bug bounty programs. As more organizations adopt the programs, they will require support from external experts to avoid introducing new risks with improperly configured programs.
Ransomware attackers get targeted; crypto currencies help ransomware industry flourish. In 2018, ransomware criminals will evolve their tactics. The reports predicts that attackers utilizing forms of benign malware—such as software designed to cause DDoS attacks or launch display ads on thousands of systems— will launch huge outbreaks of ransomware. While attackers will continue to launch scatter-gun-style attacks to disrupt as many systems as possible, the report predicts an increase in instances of attacks targeting specific companies and demanding ransomware payments proportional to the value of the encrypted assets. Crypto currencies will continue to support the flourishing ransomware industry overall, despite law enforcement becoming more advanced in their ability to trace attacks, for example through bitcoin wallets.
Insider risks plague organizations as they underestimate their severe vulnerability and liability while major attacks fly under the radar. In 2017, businesses under invested in proactive insider risk mitigation strategies, and 2018 will be no different. According to the report, a continued lack of security training and technical controls, coupled with the changing dynamics of the modern workforce, the full extent of cyber attacks and incidents caused by insiders will not become fully public. Many companies will continue to reactively responding to incidents behind closed doors and remain unaware of the true cost and impact of insider risk on the organization.
What is Cybersecurity Risk Management
Cyber Risk Management is the next evolution in enterprise technology risk and security for organizations that increasingly rely on digital processes to run their business. Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such doors and locks to protect homes and autos, vaults to protect money and precious jewels, and police, fire and security to protect against other physical risks.
What is cybersecurity risk management?
Rather than doors, locks and vaults, IT departments rely on a combination of strategies, technologies and user education to protect an enterprise against cybersecurity attacks that can compromise systems, steal data and other valuable company information, and damage an enterprise’s reputation. As the volume and severity of cyber attacks grow, the need for cybersecurity risk management grows with it.
Cybersecurity risk management takes the idea of real world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.
Setting up your risk management system
Before setting up a cybersecurity risk management system, the enterprise needs to determine what assets it needs to protect and place a priority on. As the National Institute of Standards and Technology (NIST) points out in its Framework for Improving Critical Infrastructure Cybersecurity, there is no one-size-fits all solution. Different organizations have different technology infrastructures and different potential risks. Some organizations such as financial services firms and healthcare organizations, have regulatory concerns in addition to business concerns that need to be addressed in a cybersecurity risk management system. Cybersecurity should follow a layered approach, with additional protections for the most important assets, such as corporate and customer data. Remember that reputational harm from a breach can do more damage than the breach itself.
Risk management with CyberSecOp
Identity Services
Identity services help companies manage the explosion of digital identities and access to critical resources, both internal and cloud-based. In this age of digital transformation, the spheres of the individual’s life―as a professional, consumer, and private citizen―are interlinked in a complex digital structure, like a piece of fabric. The growing ability to piece together a digital picture of a person’s life and identity carries both risk and opportunity.
Wherever an organization is on its journey, we can help them achieve efficiencies, reduce risk, and evolve to support the changing needs of the digital business. With 20 years of identity management experience across the major industries, we offer field-tested accelerators and methods that are scalable and adaptive to each client’s specific set of business requirements.
Data Protection
Data Protection services help implement capabilities and technologies to protect sensitive data. As infrastructure and applications become more virtualized and adaptive, new cybersecurity gaps can be created as fast as old ones have been addressed, making the prevention of data breaches more difficult than ever. By prioritizing preventative and detective defenses around highly sensitive data, security teams can help reduce data loss and risk when attackers get past network, application, and infrastructure controls.
Leveraging these principles and an understanding of each client’s risk profile, CyberSecOp helps organizations design, implement, and manage capabilities to help better protect sensitive information across the end-to-end data lifecycle, and at an organization’s last line of defense.Application Security
In the era of digital transformation, application portfolios are becoming exponentially more diverse—and support a growing community of users. As the application “surface area” expands, so does cyber risk. Amid the change, one thing remains constant: applications are the lifeline of the business—and need to be a front line of cyber defense. It’s an important time for organizations to reexamine their approaches to application security.
Improving application security requires technical attention to individual applications, but also a broad framework across the application portfolio—from custom-developed to commercial off-the-shelf (COTS) applications and whether managed on-premise, on a mobile platform, in the cloud, or in a hybrid environment. It also requires the flexibility to support varying and often coexisting system methodology processes from waterfall, to agile, to DevOps in order to address application-related cyber risk at the pace of the organization’s digital evolution.
CyberSecOp’s application security services help organizations to design and implement security mechanisms across the system development methodology that can flex to your operational requirements to drive value through IT while also protecting your application portfolio against the changing cyber threat landscape.Infrastructure Security
Infrastructure Security services focus on developing advanced protection of core systems and devices. Today’s critical business drivers—the need to digitally transform, modernize the supply chain, enhance customer experience, increase agility, reduce costs, etc.—are driving a major shift in technology priorities. This shift includes increasing focus on cloud adoption, the Internet of Things (IoT), hybrid computing, software-defined networks (SDN), robotic process automation (RPA), blockchain, artificial intelligence, and more. The infrastructure supporting it has become highly virtualized and automated—and the traditional means of securing infrastructure fall short.
CyberSecOp helps organizations move toward a modernized, risk-focused agile defense approach. While the basic infrastructure domains—physical facilities, networks, systems and storage, and endpoints—that need to be protected remain the same, the means to secure them must evolve. By providing assessment, strategy, architecture, implementation, and operational management assistance across the four infrastructure domains, we help clients face our brave new world with a transformed, agile defense capability.
Data Protection Solutions & Data Security
Protect and secure data and data privacy is critical since most companies hold clients/costumers sensitive data, and protect that data is not only critical to its clients/costumes. Data protection is also critical for companies intellectual properties and reputation.
Data Protection Services
As more organizations move to hybrid or multi-cloud IT strategy, managing data protection services has become increasingly more complex. Various systems, technologies and environments require different tools for data protection management, and many IT teams find they must use a variety of tools to perform backup operations. In addition to greater inefficiency and rising costs, this intensive focus on data protection services diverts IT teams from higher value tasks and other strategic priorities.
Data Protection Simplified by CyberSecOp LocVault services
To simplify data protection services, CyberSecOp offers a Managed Data Protection solution that can protect digital assets across all your environments. Powered by Locvault's best-in-class data backup and recovery software, CyberSecOps Managed Data protection services help simplify data protection by enabling IT teams to use a single tool for backup and restore processes.
Efficiently Protect, Manage and Recover Your Data
Protect, manage and access the information you need with a heterogeneous data protection solution
A single interface manages data at a fraction of the time, effort and cost required by separate point products
Simplify data management in complex networked storage environments with a consistent way to locate and manage data and applications
With Privacy and Data Protection, CyberSecOp LocVault will help you protect your sensitive business data and help you meet compliance requirements related to data storage and protection.
We’ll also help you assess your risk, create custom policies to encrypt and restrict access to sensitive data, and report on data access — helping to ensure that your important data remains protected. Speak with an expert
Are Users Your Weakest Link - To Your Cybersecurity Posture
Humans remain the weak link in corporate data protection
Humans remain the weak link in corporate data protection, but you might be surprised that it isn't only rank-and-file employees duped by phishing scams who pose risks. Some companies are lulled into a false sense of cybersecurity by vendors. You read that right, Some enterprises believe the shiny new technologies they've acquired will protect them from anything.
As we continue to build defense in depth and deploy security appliances utilizing AI and other emerging technologies, attackers will continue to pivot to the perennial weak spot: the users. Recently I hosted the Social Engineering Capture The Flag competition at Hackfest in Quebec, and similar to last year, the results were sobering. Every single targeted company had employees that gave detailed information over the phone on their OS and service pack level, and 88 percent gave detailed information on the browser they were using. Three quarters went to a URL that they were given over the phone. The information that the companies bled was disheartening but not shocking. Until we train employees to trust their instincts and tell them it's okay to say no to a customer, things won't change. In the current environment where companies ask their customers to leave a positive review online, employees increasingly feel less empowered to terminate a call they feel is suspicious. Your friendly neighborhood hacker is happy to exploit this weakness.
Billions being send on security tools
The threat of cyber crime has created a significant increase in interest on the topic of cyber security, with organizations spending billions of dollars to protect themselves against a fast evolving array of current and potential future threats. Many spend heavily on monitoring, surveillance and software; however, they often neglect the risk exposure created by their own people – and, in this digital age, by their customers.
Businesses are losing the fight, pay ransom, or lose their lively hood
Businesses are forced to make exceedingly difficult decisions. On one hand, it feels wrong to negotiate with the cybercriminals and give them what they want. On the other hand, the looming financial hit and business interruption is typically far more detrimental than the payoff amount. If business owners don’t engage with the ransomers, they face the prospect that they, and their employees, may lose their livelihood. I see ransomware as a continuing cyber threat in 2019 and beyond. It’s up to business owners to implement the best security practices and ensure that their employees are properly trained to identify and avoid potential threats.
WHAT DO SECURITY CONSULTANTS DO?
WHAT DO SECURITY CONSULTANTS DO?
Security consults deal with various threats to physical and computer security. Security threats come in many forms such as computer hackers, terrorists, and attacks on physical assets. There are specializations for security consultants of building security, natural and man-made disaster prevention, or with computer security issues.
Some of the roles security consultants may do for companies or private individuals are installing physical protections of video surveillance and alarm systems. Physical security risks are issues for many companies and security consultants may determine physical security risks such as threats of violence in the workplace, the stability of a building during tornadoes, earthquakes, fires, or other natural disasters, and development of evacuation plans for personnel during emergencies. Security consultants also may advise on building maintenance issues.
What services does a security consultants provide?
Security consultants can also help to incorporate security changes at all levels of the company. Based upon the security audit that’s conducted, a security consultant, if allowed to, can implement various new security measures and procedures throughout the company, which can include security related to:
Analyzing areas that are currently exposed and if they have had their security compromised in the past;
Performing a gap analysis in order to determine if any areas of a company’s current security does not meet accepted industry standards;
Gauging the work environment through performing interviews with important personnel and company employees;
Providing a list of recommendations based upon found security vulnerabilities, which includes security measures that should be incorporated.
Policies and procedures;
Electronic surveillance and alarm systems;
Security personnel.
A security consultant will work closely with management for the purposes of transparent communication and to make sure that any security changes that are implemented are done so within the allotted budget. The degree to which a security consultant can incorporate security changes depends largely upon this, in addition to the management’s instructions.
CyberSecOp Security Services has been providing expert security consulting services for decades. Make sure to contact us today to ask about our advanced security consulting services, which will be personalized to your company’s particular needs.
Microsoft's Emergency Internet Explorer Patch - Kills Lenovo Laptops
Only a few days ago, Microsoft released an emergency Internet Explorer patch bundled in a cumulative update. The patch was rolled out to fix the zero-day vulnerability in Internet Explorer first discovered by a
However, it seems like the patch is creating more problems than fixing them. Out of many known issues, as mentioned by Microsoft in the changelog, one can be regarded as a more severe issue since it is leaving many Lenovo laptops unbootable after installing the patch.
Microsoft mentions that the issue is only affecting Windows 10 users who have a Lenovo laptop that has less than 8 GB RAM. On the other hand, few sources tell that the issue has only affected PC’s that are still on the 1607 version, or Windows 10 Anviersary Update (2016).
Considering only enterprise PCs have the ability to delay updates, they are most likely have been affected by the unbootable issue.
If you have installed the latest “KB4467691” cumulative update on your PC, and are facing the same issue, here are some steps that Microsoft wants you to follow —
Restart the affected machine using UEFI. After this, disable Secure Boot and then perform restart.
If BitLocker is enabled on your computer, you may have to go through BitLocker recovery after Secure Boot has been disabled.
Ransomware Cyberattack - 92% of MSSPs Expect Ongoing Attacks
Ransomware is the leading cyberattack experienced by small and medium-sized businesses (SMBs), according to a survey of more than 2,400 managed service providers (MSSPs) conducted by data protection company Datto.
Datto’s State of the Channel Ransomware Report provides unique visibility into the ransomware epidemic from the perspective of the IT Channel and the SMB clients who are dealing with these infections on a daily basis. The report provides a wealth of detail on ransomware, including year-over-year trends, frequency, targets, impact, and recommendations for ensuring recovery and continuity in the face of the growing threat.
Key findings from Datto’s “State of the Channel Ransomware Report” included:
79 percent of MSSPs reported ransomware attacks against customers.
85 percent indicated that victims had antivirus software installed, 65 percent reported victims had email/spam filters installed and 29 percent reported victims used pop-up blockers.
89 percent are “highly concerned” about ransomware attacks.
92 percent predict the number of ransomware attacks will continue at current, or worse, rates.
MSPs ranked phishing emails as the top ransomware delivery method, followed by malicious websites, web ads and clickbait.
The average requested ransom for SMBs is roughly $4,300, while the average cost of downtime related to such an attack is approximately $46,800.
The number of MSPs reporting OS/iOS attacks increased by nearly 500 percent year over year in the first six months of 2018.
No single solution is guaranteed to prevent such attacks, Datto indicated. Conversely, SMBs require a multilayered approach to identify and stop ransomware attacks before they cause brand reputation damage, revenue loss and other problems.
How Can SMBs Address Ransomware Attacks?
CyberSecop offered the following recommendations to help SMBs safeguard their data and assets against such attacks:
Leverage business continuity and disaster recovery (BCDR) technology. BCDR technology won’t stop ransomware attacks; instead, it helps an SMB determine how to limit downtime and maintain operations despite a ransomware attack.
Provide cybersecurity training. By offering regular and mandatory cybersecurity training, an SMB can ensure all of its employees can identify and avoid potential phishing scams that otherwise lead to such an attack.
Employ a dedicated cybersecurity professional. It may be difficult for an SMB to hire a full-time cybersecurity professional. Fortunately, working with an MSSP allows an SMB to receive cybersecurity monitoring and other security services.
Data Breaches Ransomware and Cyber Attacks
Data Breaches Ransomware and Cyber Attacks
It’s unrealistic to think that you can completely avoid cyberattacks and data breaches, so it’s vital to have a proper data recovery plan in place. You can also tighten your defenses significantly by ensuring all of your network devices are properly configured, and by putting some thought into all of your potential network borders.
Data Recovery Capability
Do you have a proper backup plan in place? Have you ever tested it to see that it works? Disaster recovery is absolutely vital, but an alarming number of companies do not have an adequate system in place. A survey of 400 IT executives by IDG Research revealed that 40% rate their organizations’ ability to recover their operations in the event of disaster or disruption as “fair or poor.” Three out of four companies fail from a disaster recovery standpoint, according to the Disaster Recovery Preparedness Benchmark.
A successful malware attack can lead to altered data on all compromised machines and the full effects are often very difficult to determine. The option to roll back to a backup that predates the infection is vital. Backed up data must be encrypted and physically protected. It’s also important that a test team routinely checks a random sampling of system backups by restoring them and verifying data integrity.
Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
The default configurations for network devices like firewalls, routers, and switches are all about ease of use and deployment. They aren’t designed with security in mind and they can be exploited by determined attackers. There’s also a risk that companies will create exceptions for business reasons and then fail to properly analyze the potential impact.
The 2015 Information Security Breaches Survey found that failure to keep technical configuration up to date was a factor in 19% of incidents. Attackers are skilled at seeking out vulnerable default settings and exploiting them. Organizations should have standardized secure configuration guidelines applied across devices. Security updates must be applied in a timely fashion.
You need to employ two-factor authentication and encrypted sessions when managing network devices, and engineers should use an isolated, dedicated machine without Internet access. It’s also important to use automated tools to monitor the network and track device configurations. Changes should be flagged and rule sets analyzed to ensure consistency.
Boundary Defense
When the French built the Maginot Line in World War II, a series of impregnable fortifications that extended along the border with Germany and beyond, it failed to protect them because the Germans invaded around the North end through neutral Belgium. There’s an important lesson there for security professionals: Attackers will often find weaknesses in perimeter systems and then pivot to get deeper into your territory.
They may gain access through a trusted partner, or possibly an extranet, while your defensive eye is focused on the Internet. Effective defenses are multi-layered systems of firewalls, proxies, and DMZ perimeter networks. You need to filter inbound and outbound traffic and take caution not to blur the boundaries between internal and external networks. Consider network-based IDS sensors and IPS devices to detect attacks and block bad traffic.
Segment your network and protect each sector with a proxy and firewall to limit access as far as possible. If you don’t have internal network protection, then intruders can get their hands on the keys to the kingdom by successfully breaching the outer defenses.
The real cost
A lot of businesses argue that they can’t afford a comprehensive disaster recovery plan, but they should really consider whether they can afford to lose all their data or be uncertain about its integrity. They may lack the expertise to ensure that network devices are securely configured, but attackers don’t lack the skills to exploit that. It’s understandably common to focus on the outer boundary of your network and forget about threats that come from unexpected directions or multiply internally, but it could prove costly indeed.
Compared to the cost of a data breach, all of these things are cheap and easy to set up