CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
New York Information Security and Breach Law (SHIELD Act)
New York has joined the expanding list of states and countries to put in place a law that protects private information, empowering protection of data, and information security for operation that utilized PII information provided by New York residence. On July 26, 2019, Gov. Andrew Cuomo signed into law the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act).
BILL NUMBER: S5575B Stop Hacks and Improve Electronic Data Security Act
BILL NUMBER: S5575B New York's data breach notification law requires an organization to implement necessary safeguards to protect data and provide notification in the event of a breach. This bill broadens the scope of information covered under the notification law and updates the notification requirements when there has been a breach of data. It also broadens the definition of a data breach to include an unauthorized person gaining access to information. It also requires reasonable data security, provides standards tailored to the size of a business, and provides protection from liability for certain entities. This act shall be known and may be cited as the "Stop Hacks and Improve Electronic Data Security Act (SHIELD Act)”
Does it apply to your business?
SHIELD Act will apply to any person or business that owns or licenses personal private data in electronic form, regardless if the person or business operates in New York. For example, a person or business may have physical operations in New Jersey, but if that office has employees and customers that reside in New York, they will be subject to the Act and its requirements. Like many recent privacy laws, such as the California Consumer Privacy Act (CCPA) and the European Union’s General Data Protection Regulation (GDPR), it is becoming clear that physical boundaries will not restrict the reach of these laws and any future laws to be adopted by other states and countries.
What is private information?
is any piece of personal information that can be used to identify an individual and includes, but is not limited to, the following:
Full name
Home address
Email address
Social security number
Passport number
Driver’s license number
Credit card numbers
Date of birth
Telephone number
Data Security Solutions
Security policy for third-party service providers, “The organization must document written procedures and policies to ensure third-party risk management programs protect information systems and non-public information.”
Key provisions of these policies apply to the financial institution’s systems, including:
Written policies and procedures designed to protect users from risks posed by third-party service providers
The identification and risk assessment of third-party service providers
Minimum cybersecurity practices required of third parties
The evaluation of third-party cybersecurity practices through due diligence
Periodic risk-based assessments
Additionally, policies and procedures pertaining to third-party service providers are required to include relevant guidelines for due diligence as well as contractual protections, addressing:
Access controls, including multi-factor authentication
Encryption
Notifications to be provided to the primary organization in response to a cybersecurity event
·Representations and warranties for a third party’s cybersecurity policies and procedures
CyberSecOp drives leadership in data security solutions
New is asking organization to assess their security risks, and then develop policies for data governance, classification, access controls, system monitoring, and incident response and recovery. The regulation calls for companies to implement, at a minimum, specific controls in these areas (see the next section) that are typically part of compliance standards.
Risk Assessments – Conducted periodically and will be used to assess “confidentiality, integrity, security and availability of the IT infrastructure and PII.
Audit Trail – Designed to record and respond to cybersecurity events. The records will have to be maintained for five years.
Limitations on Data Retention – Develop policies and procedures for the “secure disposal” of PII that is “no longer necessary for business operations or for other legitimate business purposes”
Access Privileges – Limit access privileges to PII and periodically review those privileges.
Incident Response Plan – Develop a written plan to document internal processes for responding to cyber security events, including communication plans, roles and responsibilities, and necessary remediation of controls as needed
Organization must be able to:
Identify: Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Protect: Employ defense infrastructure to safeguard against those threats.
Detect: Implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond: Take appropriate action to mitigate all detected cybersecurity events.
Recover: Restore any capabilities or services that were impaired due to a cybersecurity event.
Breach and Who to Notify?
The SHIELD Act substantially changes the definition of a breach. Prior to the SHIELD Act, the definition of a breach was restricted to the unauthorized acquisition of private information. The SHIELD Act expands the definition to also include unauthorized access to private information. The inclusion of unauthorized access to private information will result in a substantial increase in the number of businesses that will be required to report a breach.
Security Breach Notification
Should a breach occur, you will need to notify the impacted individuals as well as: the New York State Attorney General, the Department of State, and the Division of State Police. If the breach impacts more than 5,000 New York residents, consumer reporting agencies must also be notified. If you are already subject to HIPAA, GLBA, or the NY DFS 500 Cyber Regulation, duplicate notifications to the individual is not required.
The SHIELD Act significantly amends New York's data breach notification law and data protection requirements. On July 25, 2019, New York Governor Andrew Cuomo signed into law the Stop Hacks and Improve Electronic Data Security Act ("SHIELD Act") amending New York's data breach notification law.
Connecticut Insurance Data and Information Security
Connecticut ACT Concerning Insurance Data and Information Security
Section 230 of the Connecticut budget bill is called the “Insurance Data Security Law”; Connecticut now requires registered entities to have Information security and Cyber security program similar to New York’s Department of Financial Services (NYDFS). Section 230 became effective as of October 1, 2019, and the information security program must be implemented by no later than October 1, 2020. The purpose of this section 230 is to establish standards for data and information security for persons licensed and required to be licensed by the Insurance Commissioner, require licensees to notify the commissioner following cybersecurity events,d require the commissioner to investigate such possibilities.
The requirements include the implementation and maintenance of a Written Information Security Program (WISP) based upon a risk assessment as well as administrative, technical and physical safeguards to protect non-public information: Board of Directors oversight, policies, procedures, and precautions, risk management program included risk assessment, risk evaluation, risk mitigation of internal and external systems, and third parties vendor/suppliers, cybersecurity awareness training, encryption of data in transit and at rest, multifactor authentication, and continuous monitoring to identify unauthorized access to, or unauthorized alteration, destruction, disclosure, misuse or transmission of, nonpublic information. Speak with an expert.
Section 230 affects Insurance Companies, and third parties Auto Insurance
· Life Insurance
· Business Insurance
· Recreational Insurance
· Umbrella Insurance
· Financial Insurance
· Health & Long Term Care Insurance
· Flood Insurance
· Health Insurance
· Homeowners Insurance
· Insurance company’s suppliers
Breach & Cyber Event Notification
Cybersecurity event, the notification must be made to the Commissioner within three business days. Suppose an insurance licensee notifies an individual under the Connecticut breach notification law. In that case, the insurer must inform not only the individuals but also the Connecticut Attorney General and the Insurance Commissioner and has a “continuing obligation to update and supplement such information.”
Enforcement of Section 230
The enforcement provisions allow the Commissioner permission to “suspend revoke or refuse to reissue or renew any license, certificate of registration or authorization to operate” … and state that the Commissioner can impose a civil penalty of not more than fifty thousand dollars for each violation of the provision of this section.
The bill also requires insurance licensees to offer 24 months of credit monitoring to affected individuals in a data breach, which is consistent with the Connecticut data breach notification law.
CyberSecOp is listed in FINRA's Compliance Vendor Directory
FINRA, Finance Industry Regulatory Authority, released its Compliance Vendor Directory as a convenient, one-stop source for firms searching for vendors that offer compliance-related products and services. CyberSecOp is pleased to announce that we are listed on FINRA's Compliance Vendor Directory as a data management vendor.
CyberSecOp team has been providing expert compliance consulting services to the financial services industry. We take security seriously, we maintaining client relationships and delivering the highest levels of compliance services. Our client base includes some of the most respected names in the financial services industry and ranges from large international firms to small firms. Our satisfied clients include advisers, institutional investors, private funds, investment companies, and broker-dealer.
CyberSecOp offers several services to help keep businesses compliant with a number of different regulations and governing bodies. As a member of the financial industry, keeping your organization compliant can be a source of constant stress that’s always in the back of your mind. Performing self-audits and constant reviewing of records to make sure you’re meeting the standards set by your industry can be time-consuming to the point that you’re slipping behind other important work. FINRA members can view the FINRA Compliance Vendor Directory here: http://www.finra.org/industry/cvd
Why You Need a Cybersecurity Management Program
Many organization’s cybersecurity teams (or information security teams as they used to be known) continue to struggle to communicate cybersecurity issues to senior leadership. Likewise, senior management also struggles to effectively articulate cybersecurity strategy to technical cybersecurity personnel. It is as though two parts of the same organization speak foreign languages to one another, and each party has a very limited, or no, knowledge of the other party’s language. However, it does not have to be like this.
Why so many organizations struggle with Cyber Security
Failure to communicate issues is most often revealed in grassroots cybersecurity initiatives that have evolved into corporate cybersecurity programs. Typically, this resulted from an enterprise in startup mode implementing solutions to address specific technical challenges. Unfortunately, many organizations continue to employ a similar approach to secure much larger and more complex environments against threats that outmatch the capabilities of their original solutions. No longer simply a technical solution, cybersecurity management has become a business function in today’s industry. As a business function, a greater level of integration with other business units requires a greater level of transparency and performance reporting. The evolution of grassroots cybersecurity programs rarely results in the kind of mature cybersecurity solutions that are aligned with, and address business needs. And why should they? The initial programs were designed to solve technical challenges, such as preventing virus outbreak or infection, stopping cyber attackers from compromising or stealing valuable information. Such initial cybersecurity efforts were neither designed as business functions nor defined in business terms.
CyberSecOp Comprehensive Security Program - Going beyond compliance
Cyber Security Program Key Success Factors
The following key success factors are common to many successful cybersecurity programs. The programs:
Support and drive strong governance attitudes and actions
Are designed, developed, and implemented in a similar way to other business functions
Adopt a standard framework approach, usable for an extended period of many years with little or no changes to that framework
Are measureable in terms of their effectiveness
Organizations and executives that drive successful cybersecurity programs do so in the same manner as other successful business initiatives. Executives succeed at this not because of industry pressure, but because each aims to improve their organization. Having identified the opportunity, executives evaluate whether the initiative poses additional risks to their organizations and decide whether to accept this additional risk or not. After accepting such risk, executive sponsors continue to evaluate initiatives toward implementation. Even when initiatives are operational, executives still employ strong governance methods, including internal audit teams, to manage and monitor the effectiveness and efficiency of these initiatives. This business approach has become institutionalized across most enterprise units with the exception of IT and cybersecurity. Key stakeholders in IT and cybersecurity often claim that cybersecurity management programs are too technical, only internal facing, or too complex, to properly develop and implement using this approach.
The truth is if these same IT and cybersecurity groups adopted a common framework and designed their cybersecurity management programs based on said framework, cybersecurity management would truly become just a standard business function in their enterprises. Unfortunately, the cybersecurity world does not agree on a standard cybersecurity framework across all countries, industries, and states. Analysis of the commonalities and differences between these standard frameworks show that it is possible to create a universal cybersecurity management framework to address all countries, industries, and states. Such a framework is not firmly associated with any particular cybersecurity standard and can be adapted during implementation to address any specific security standard that organizations using it wishes to follow. This paper introduces a cybersecurity management framework where it is apparent that a successful approach is not too technical, addresses both internal and external concerns, and is not overly complex to implement, operationalize, and manage over the long term.
CyberSecOp Cyber Security Management - Aligning businesses with security
Cybersecurity Management Framework
The design of the CyberSecOP cybersecurity management framework (CMF) assumes cybersecurity management is a business function.
The framework, as a business function, is comprised of three discrete pillars with each subsequent layer unfolding increasing levels of specificity as follows:
The Executive Management (Strategy) Pillar directs Governance and Planning initiatives that drive the framework forward to operation.
The Executive Management Pillar requires people to identify why cybersecurity is needed, consider the business issues, and then define, document, and publish the direction the required cybersecurity program will adopt.
The Operations Pillar that defines what the cybersecurity program must address to comply with the requirements specified in the strategy, what supporting functions are needed, and what level of reporting/ governance monitoring should be provided. These needs are supported through the security intelligence, IT and Cybersecurity Assurance and IT Risk Management operations sub-pillars.
The Operations Pillar requires definitions of documented operational standards, processes, procedures, and other collateral that specify what operators should do and how they should do it.
The Tactical (Technology) Pillar defines how required cybersecurity controls mandated in the Operations and Executive Management pillars will be applied to the systems, networks and applications used by the organization and how evidence will be provided to management that the security controls implemented actually address the specific requirements and that they perform their job as expected.
The security controls in the Tactical pillar, whether requiring technology or not, are responsible for securing all aspects of an enterprise computing environment, continuously monitoring the environment for security events, collecting and analyzing captured events, and reporting defined security metrics, some of which are provided to the SLT.
Addressing Cybersecurity Challenges
Although addressing cybersecurity challenges with just three pillars is perfectly possible, adopting and using it in that way is difficult and potentially open to error or misinterpretation. To minimize these issues, these macro-level pillars must be divided into more manageable chunks. The CyberSecOp LocPar subdivides its three macro pillars into seven discrete focus areas:
Executive Management: Key decisions and accountability required to drive the program
IT Risk Management: Reducing risk exposure to the organization to a level acceptable to the SLT and Board of Directors.
Cybersecurity Intelligence: Required to provide the cybersecurity and IT teams with appropriate information to achieve and surpass IT Risk Management goals.
IT and Cybersecurity Assurance: Required to provide evidence to management and especially the SLT that their investments in cybersecurity are delivering the benefits they expected.
Secure Network: Required to support secure, on demand access to information to authorized personnel no matter where it is located within, or external to, the organization.
Secure Systems: Required to provide controlled access to applications, data and devices according to the identity of the requesting party. This focus area also includes how data is protected, whether at rest, or in transit.
Secure Applications: Required to control access to data and other networks, systems and applications according to the identity of the requesting party. For internally developed applications, requirements extend to how the application was designed, developed and managed throughout the whole development lifecycle.
Summary
Development, implementation, and maintenance of a cybersecurity management program for an organization is no small undertaking. However, the overall value that organizations achieve through development and implementation of such programs includes reduced instances of successful cyber attacks. Moreover, a cybersecurity management program provides organizations with a means to reduce a successful attack’s impact on the bottom line due to its programmatic predefined approach for identifying and responding to cybersecurity incidents. Read more about cybersecurity management programs and CyberSecOp Cybersecurity Services at https://www.cybersecop.com/
What is Cybersecurity Risk Management
Cyber Risk Management is the next evolution in enterprise technology risk and security for organizations that increasingly rely on digital processes to run their business. Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such doors and locks to protect homes and autos, vaults to protect money and precious jewels, and police, fire and security to protect against other physical risks.
What is cybersecurity risk management?
Rather than doors, locks and vaults, IT departments rely on a combination of strategies, technologies and user education to protect an enterprise against cybersecurity attacks that can compromise systems, steal data and other valuable company information, and damage an enterprise’s reputation. As the volume and severity of cyber attacks grow, the need for cybersecurity risk management grows with it.
Cybersecurity risk management takes the idea of real world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.
Setting up your risk management system
Before setting up a cybersecurity risk management system, the enterprise needs to determine what assets it needs to protect and place a priority on. As the National Institute of Standards and Technology (NIST) points out in its Framework for Improving Critical Infrastructure Cybersecurity, there is no one-size-fits all solution. Different organizations have different technology infrastructures and different potential risks. Some organizations such as financial services firms and healthcare organizations, have regulatory concerns in addition to business concerns that need to be addressed in a cybersecurity risk management system. Cybersecurity should follow a layered approach, with additional protections for the most important assets, such as corporate and customer data. Remember that reputational harm from a breach can do more damage than the breach itself.
Risk management with CyberSecOp
Identity Services
Identity services help companies manage the explosion of digital identities and access to critical resources, both internal and cloud-based. In this age of digital transformation, the spheres of the individual’s life―as a professional, consumer, and private citizen―are interlinked in a complex digital structure, like a piece of fabric. The growing ability to piece together a digital picture of a person’s life and identity carries both risk and opportunity.
Wherever an organization is on its journey, we can help them achieve efficiencies, reduce risk, and evolve to support the changing needs of the digital business. With 20 years of identity management experience across the major industries, we offer field-tested accelerators and methods that are scalable and adaptive to each client’s specific set of business requirements.
Data Protection
Data Protection services help implement capabilities and technologies to protect sensitive data. As infrastructure and applications become more virtualized and adaptive, new cybersecurity gaps can be created as fast as old ones have been addressed, making the prevention of data breaches more difficult than ever. By prioritizing preventative and detective defenses around highly sensitive data, security teams can help reduce data loss and risk when attackers get past network, application, and infrastructure controls.
Leveraging these principles and an understanding of each client’s risk profile, CyberSecOp helps organizations design, implement, and manage capabilities to help better protect sensitive information across the end-to-end data lifecycle, and at an organization’s last line of defense.Application Security
In the era of digital transformation, application portfolios are becoming exponentially more diverse—and support a growing community of users. As the application “surface area” expands, so does cyber risk. Amid the change, one thing remains constant: applications are the lifeline of the business—and need to be a front line of cyber defense. It’s an important time for organizations to reexamine their approaches to application security.
Improving application security requires technical attention to individual applications, but also a broad framework across the application portfolio—from custom-developed to commercial off-the-shelf (COTS) applications and whether managed on-premise, on a mobile platform, in the cloud, or in a hybrid environment. It also requires the flexibility to support varying and often coexisting system methodology processes from waterfall, to agile, to DevOps in order to address application-related cyber risk at the pace of the organization’s digital evolution.
CyberSecOp’s application security services help organizations to design and implement security mechanisms across the system development methodology that can flex to your operational requirements to drive value through IT while also protecting your application portfolio against the changing cyber threat landscape.Infrastructure Security
Infrastructure Security services focus on developing advanced protection of core systems and devices. Today’s critical business drivers—the need to digitally transform, modernize the supply chain, enhance customer experience, increase agility, reduce costs, etc.—are driving a major shift in technology priorities. This shift includes increasing focus on cloud adoption, the Internet of Things (IoT), hybrid computing, software-defined networks (SDN), robotic process automation (RPA), blockchain, artificial intelligence, and more. The infrastructure supporting it has become highly virtualized and automated—and the traditional means of securing infrastructure fall short.
CyberSecOp helps organizations move toward a modernized, risk-focused agile defense approach. While the basic infrastructure domains—physical facilities, networks, systems and storage, and endpoints—that need to be protected remain the same, the means to secure them must evolve. By providing assessment, strategy, architecture, implementation, and operational management assistance across the four infrastructure domains, we help clients face our brave new world with a transformed, agile defense capability.
Choosing A Managed Detection & Response Provider
Why Managed Detection & Response Provider may be the right move
Companies outsourcing security need Managed Detection & Response providers (MDR) more than ever to improve cyber resilience. With the security landscape growing more complex, and the costs of maintaining adequate in-house security teams high, it makes sense for many companies to outsource the tasks of threat hunting and response to ensure that they can promptly identify potential threats and react swiftly to mitigate damages. Managed Detection & Response providers often integrate tools such as Endpoint Detection & Response and other solutions to detect threats, analyze risk, and correlate threat data to pinpoint patterns that could indicate a larger attack.
How to choose the right Manged Detection & Response Provider
Smart moves: you’re making them. How do we know? For one, you’re investigating ways to close the gaps in your threat detection and incident response. Which makes sense, given that assembling the talent and tech to thoroughly thwart attackers requires more than most organizations can commit to. Even smarter, you’re checking out Managed Detection and Response (MDR) Services, an increasingly popular solution which combines expertise and tools to provide monitoring and alerting, as well as remote incident investigation and response that can help you detect and remediate threats.
9 things to look our for when choosing a Managed Detection & Response Provider
Your Managed Detection & Response Provider should combine numerous data inputs from security detection tools, threat intel feeds, third party data sources, and the IT asset database to identify not only where there is a threat but its risk compared to others in the queue.
Assess your company's present and future technology needs and initiatives. Qualify, quantify and communicate those needs throughout your company. Is the Managed Detection & Response Provider able to address your range of needs?
Technology strategies should encompass people and processes as part of the organization's mission and strategies. Do they offer ongoing employee training as part of their service?
Does the Managed Detection & Response Provider continuously assess your organization's performance for meeting objectives? You want a partner that focuses on continuous evaluation and improvement of your objectives.
Review your company's goals and mission. Ensure they are clear and concise and can be communicated to all organizational stakeholders as well as your new IT partner.
Perform annual policy and process reviews to assess organization's readiness for external reviews and incident response.
Identify and create teams within your organization to define current challenges and align initiatives to those challenges.
Through playbooks and pre-defined workflows, you can quickly assess and begin to remediate security incidents based on best practices. Ask a Managed Detection & Response Provider if they include such materials as part of their package.
CIOs/CISOs should have unprecedented transparency to all aspects of the security environment. Through dashboards and visualization techniques, CIOs/CISOs will be more easily able to communicate with Managed Detection & Response Providers which vulnerabilities and threats exist and the risks of inaction.
What is Regulatory Compliance & Services?
What is Compliance
Compliance means conforming to a rule, such as a specification, policy, standard or law. Regulatory compliance describes the goal that organizations aspire to achieve in their efforts to ensure that they are aware of and take steps to comply with relevant laws, policies, and regulations.
Business and Compliance
When it comes to a business and corporate management, compliance refers to the company obeying all of the legal laws and regulations in regards to how they manage the business, their staff, and their treatment towards their consumers. The concept of compliance is to make sure that corporations act responsibly.
The pressure to comply with constantly changing regulatory, third-party, and internal guidelines can be overwhelming. Being unprepared to manage risks yet meet mandates can lead to economic consequences and legal liabilities. Both can contribute to a significant financial impact and hurt to your reputation, which could prove even more damaging. You may be exposed to threats you’re not yet familiar with that could be putting your company’s reputation at risk—and even jeopardizing its future.Many major companies within the United States are subject to some type of security regulation.
Complying to regulatory compliance
Regulations that contain information security requirements are intended to improve the information security level of organizations within that industry and many organizations would welcome such information. The difficulty comes in determining which regulations apply and in interpreting the requirements of the regulation. The regulations are not written in a way that is easily understood by the average business person so many times a security professional is needed to understand the requirements and how to best implement them. Professionals have experience implementing systems, policies, and procedures to satisfy the requirements of the regulation and enhance the security of your organization and some have obtained credentials such as (CyberSecOp Information Security Practitioner) that signify their understanding of the regulations. Often the requirements are given in general terms leaving the company to determine how to best satisfy the requirements.
For those organizations without a robust security department, we provide a Virtual CISO offering with expertise in the following:
ISO 27001/27002
NIST & NIST Cybersecurity
GDPR
CCPA
FedRamp
NY DFS Requirements 23 NYCRR 500
FFIEC Handbook
FERPA
HIPAA/HITECH
Hi-Trust
PCI-DSS
Phishing Attack Prevention: What is Phishing?
What is Phishing?
Phishing is the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about to protect themselves.
Phishing Attack Prevention:
Why are so many companies vulnerable to phishing? Not having the right tools in place and failing to train employees on their role in information security.
Employees possess credentials and overall knowledge that is critical to the success of a breach of the company's security. One of how an intruder obtains this protected information is via phishing. The purpose of phishing is to collect sensitive information to use that information to gain access to otherwise protected data, networks, etc. A phisher's success is contingent upon establishing trust with its victims. We live in a digital age, and gathering information has become much easier as we are well beyond the dumpster diving days.
How do I protect against phishing attacks?
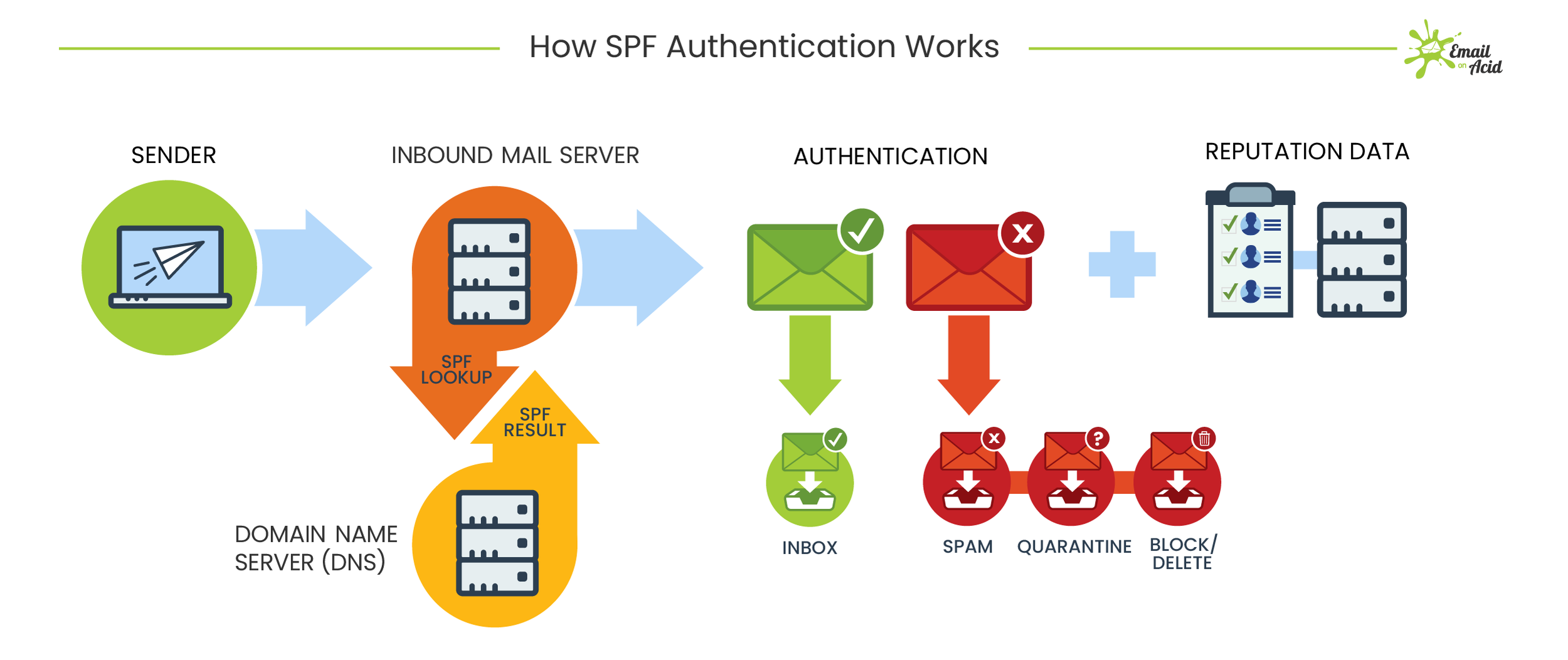
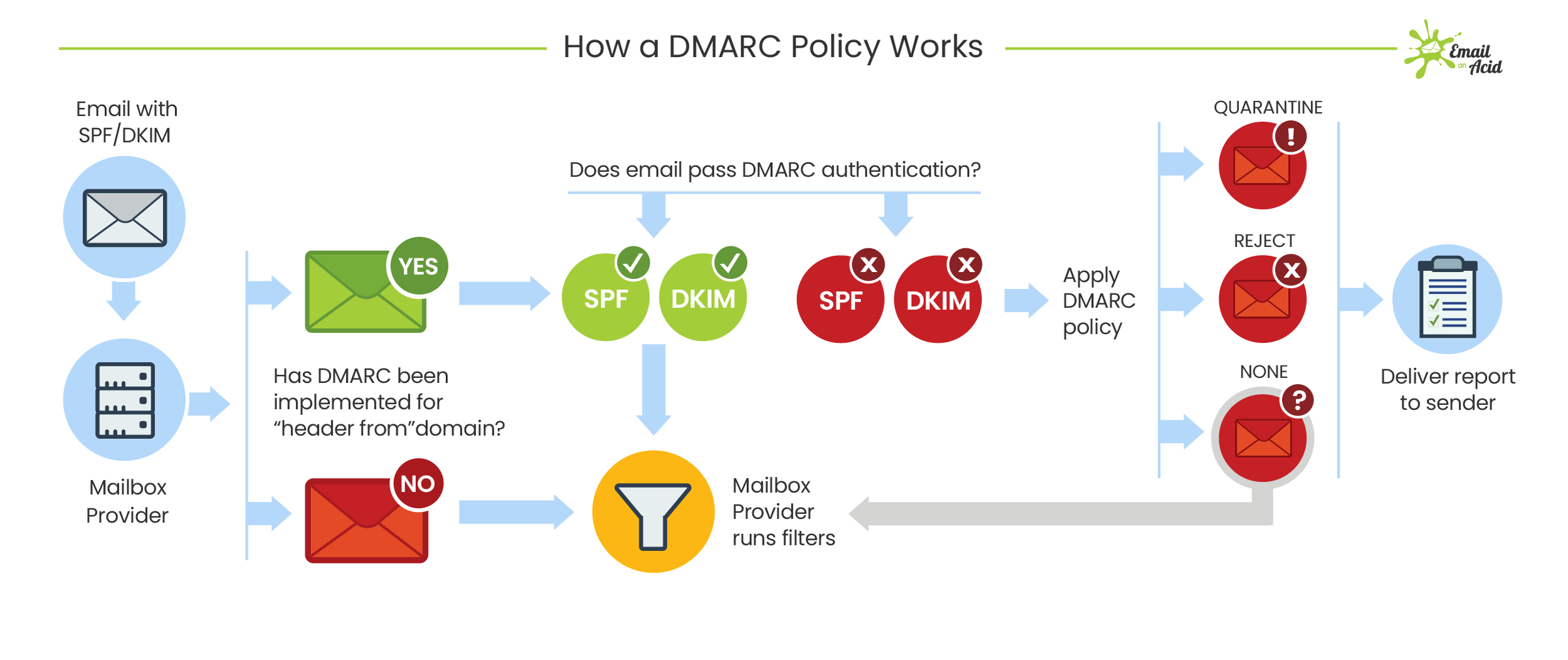
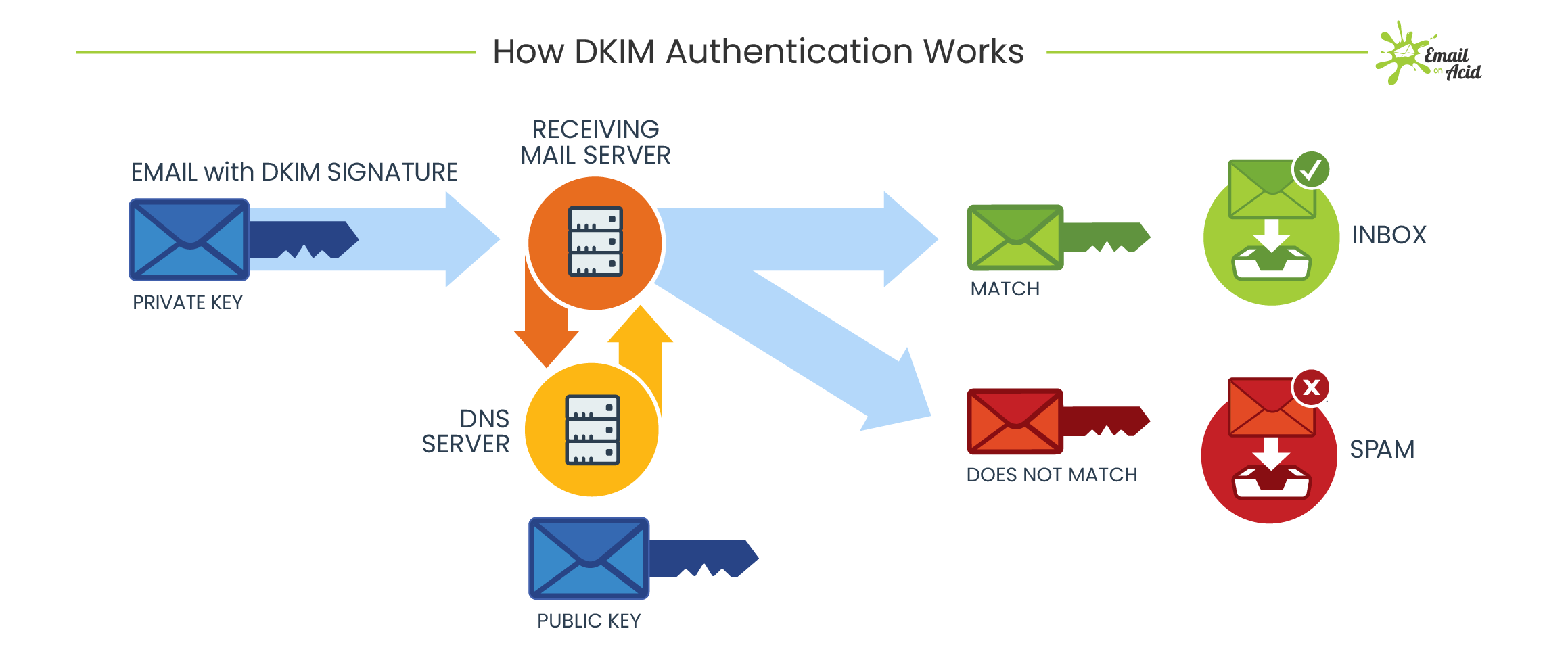
Free Email Protection
Free protocols that help organizations improve email security; Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM) were developed. SPF cross-checks the sender’s IP address with an approved list of IP addresses, and DKIM uses an encrypted digital signature to protect emails. While these are both individually effective, they have their own set of flaws. DMARC, developed in 2012, is a protocol that uses both SPF and DKIM authentication to secure email and has a mechanism that sends the domain owner a report whenever an email fails DMARC validation.
But here’s the thing: a recent report from phishing specialist Agari states that only 1/3 of the Fortune 500 have configured DMARC.
User education
One way to protect your organization from phishing is user education. Education should involve all employees. High-level executives are often a target. Teach them how to recognize a phishing email and what to do when they receive one. Simulation exercises are also key for assessing how your employees react to a staged phishing attack.
Security technology
No single cybersecurity technology can prevent phishing attacks. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control.
How does phishing work?
Phishing starts with a fraudulent email or other communication that is designed to lure a victim. The message is made to look as though it comes from a trusted sender. If it fools the victim, he or she is coaxed into providing confidential information, often on a scam website. Sometimes malware is also downloaded onto the target’s computer.
What are the dangers of phishing attacks?
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing.
Types of Phishing
Deceptive Phishing. The term "phishing" originally referred to account theft using instant messaging but the most common broadcast method today is a deceptive email message. Messages about the need to verify account information, system failure requiring users to re-enter their information, fictitious account charges, undesirable account changes, new free services requiring quick action, and many other scams are broadcast to a wide group of recipients with the hope that the unwary will respond by clicking a link to or signing onto a bogus site where their confidential information can be collected.
Malware-Based Phishing refers to scams that involve running malicious software on users' PCs. Malware can be introduced as an email attachment, as a downloadable file from a web site, or by exploiting known security vulnerabilities--a particular issue for small and medium businesses (SMBs) who are not always able to keep their software applications up to date.
Keyloggers and Screenloggers are particular varieties of malware that track keyboard input and send relevant information to the hacker via the Internet. They can embed themselves into users' browsers as small utility programs known as helper objects that run automatically when the browser is started as well as into system files as device drivers or screen monitors.
Session Hijacking describes an attack where users' activities are monitored until they sign in to a target account or transaction and establish their bona fide credentials. At that point the malicious software takes over and can undertake unauthorized actions, such as transferring funds, without the user's knowledge.
Web Trojans pop up invisibly when users are attempting to log in. They collect the user's credentials locally and transmit them to the phisher.
Hosts File Poisoning. When a user types a URL to visit a website it must first be translated into an IP address before it's transmitted over the Internet. The majority of SMB users' PCs running a Microsoft Windows operating system first look up these "host names" in their "hosts" file before undertaking a Domain Name System (DNS) lookup. By "poisoning" the hosts file, hackers have a bogus address transmitted,taking the user unwittingly to a fake "look alike" website where their information can be stolen.
System Reconfiguration Attacks modify settings on a user's PC for malicious purposes. For example: URLs in a favorites file might be modified to direct users to look alike websites. For example: a bank website URL may be changed from "bankofabc.com" to "bancofabc.com".
Data Theft. Unsecured PCs often contain subsets of sensitive information stored elsewhere on secured servers. Certainly PCs are used to access such servers and can be more easily compromised. Data theft is a widely used approach to business espionage. By stealing confidential communications, design documents, legal opinions, employee related records, etc., thieves profit from selling to those who may want to embarrass or cause economic damage or to competitors.
DNS-Based Phishing ("Pharming"). Pharming is the term given to hosts file modification or Domain Name System (DNS)-based phishing. With a pharming scheme, hackers tamper with a company's hosts files or domain name system so that requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site. The result: users are unaware that the website where they are entering confidential information is controlled by hackers and is probably not even in the same country as the legitimate website.
Content-Injection Phishing describes the situation where hackers replace part of the content of a legitimate site with false content designed to mislead or misdirect the user into giving up their confidential information to the hacker. For example, hackers may insert malicious code to log user's credentials or an overlay which can secretly collect information and deliver it to the hacker's phishing server.
Man-in-the-Middle Phishing is harder to detect than many other forms of phishing. In these attacks hackers position themselves between the user and the legitimate website or system. They record the information being entered but continue to pass it on so that users' transactions are not affected. Later they can sell or use the information or credentials collected when the user is not active on the system.
Search Engine Phishing occurs when phishers create websites with attractive (often too attractive) sounding offers and have them indexed legitimately with search engines. Users find the sites in the normal course of searching for products or services and are fooled into giving up their information. For example, scammers have set up false banking sites offering lower credit costs or better interest rates than other banks. Victims who use these sites to save or make more from interest charges are encouraged to transfer existing accounts and deceived into giving up their details.
CEOs and Cyber Security: are they the road block?
CEOs and cybersecurity: are they the road block?
Senior executives may be the weakest link in the corporate cyber security chain and are a primary target of hackers, fraud and phishing scams, says report. it also should be know that the are the road block to approve budget for information security, and most often security takes back sit to profit.
Report by many source and research done by many firm identity senior executive has the road block to good security within their firms, Many CEOs think they are immune to hackers, at least that’s what a new report According to the report, these findings are ironic given that CEOs are the ideal victim.
Senior Executive Are You the Weakest Link?
According to the report, Are You the Weakest Link? How Senior Executives Can Avoid Breaking the Cybersecurity Chain, many senior executives ignore the threat from hackers and cyber criminals and often feel that security policies in their respective organisations do not apply to their unique position.
In reality, their often privileged access to company information makes their personal accounts extremely valuable to exploit and heightens the need for extra care.
Professional hackers and adversaries will usually do a thorough investigation into a senior executive or board level director, including full analysis which could entail in-depth monitoring of the company website and associated social media accounts (including employees and their extended networks).
It appears that many CEOs commonly view cyber security as a responsibility for the IT department only. In reality, IT security has now become a remit for all individuals.
“All employees — especially those at the top of the corporate ladder — need to realise that cybercriminals use social engineering, email phishing and malware to access personal accounts, and C-level staff especially need to avoid becoming the weakest link in the cybersecurity chain by adhering to regularly updated, company-wide security policies regarding data sharing and backup,”
“Reviewing corporate policies, with a focus on people, premises, processes, systems and suppliers will provide valuable insights into which areas to improve, and by championing a ‘security first’ corporate culture, organisations and their senior executives will be well positioned to avoid the high financial costs, reputation damage and unexpected downtime that could result from a cyberattack or data breach.”
CCPA Data Privacy - California Consumer Privacy Act (CCPA)
CCPA Data Privacy
The California Consumer Privacy Act of 2018 (CCPA) into effect. This new consumer privacy law comes post Europe’s General Data Protection Regulation (GDPR) and, for some, is seen as a smaller version – without the option to opt-out of data collection all-together that the GDPR has.
CCPA is a consumer privacy law that will be coming into effect on January 1, 2020. The bill – which is aggressive for American privacy policy standards – will put guidelines on personal information collection and post-data-acquisition data usage by businesses.
Come 2020, the California Consumer Privacy Act (“CCPA”) may significantly impact businesses’ data practices, with new and burdensome compliance obligations such as “sale” opt-out requirements and, in certain circumstances, restrictions on tiered pricing and service levels. The breadth of personal information covered by the CCPA, going beyond what is typically covered by U.S. privacy laws, will complicate compliance and business operations.
Who need to comply with CCPA
Companies, especially those outside of California, may wonder whether they are subject to the CCPA. CCPA applies to for-profit entities that (1) have greater than $25 million in gross annual revenues; (2) annually handle personal information of 50,000 or more consumers, households, or devices; or (3) derive 50% or more of annual revenue from selling personal information. These criteria will result in a wide swath of businesses being subject to the CCPA. For example, a website might only need 137 unique visitors from California per day to reach the threshold of 50,000 consumers. That website’s collection of data through cookies may be captured by the CCPA’s broad definition of personal information. And given the third criterion focused on revenue percentage, even very small businesses that regularly exchange data, for example in the online ecosystem, might be captured if their activities are deemed to be a “sale” under the CCPA.
CCPA PRIVACY OVERSIGHT
The CCPA will impose substantial compliance obligations on all businesses that handle personal information of California consumers. Such obligations may pose particular challenges for the ever increasing array of businesses that leverage consumer data for analytics, profiling, advertising, and other monetization activities, particularly as the compliance requirements are not easily gleaned from the statutory language. Addressing these challenges will require creative, thoughtful approaches and may potentially involve industry-wide coordination to develop and advance practical solutions.
CyberSecOp CCPA privacy consultants incorporates your CCPA compliance requirements, powered by a unique combination of deep privacy expertise developed over two decades, proven methodologies refined through tens of thousands of engagements, and powerful technology operating at scale for 20 years.
WHAT DO SECURITY CONSULTANTS DO?
WHAT DO SECURITY CONSULTANTS DO?
Security consults deal with various threats to physical and computer security. Security threats come in many forms such as computer hackers, terrorists, and attacks on physical assets. There are specializations for security consultants of building security, natural and man-made disaster prevention, or with computer security issues.
Some of the roles security consultants may do for companies or private individuals are installing physical protections of video surveillance and alarm systems. Physical security risks are issues for many companies and security consultants may determine physical security risks such as threats of violence in the workplace, the stability of a building during tornadoes, earthquakes, fires, or other natural disasters, and development of evacuation plans for personnel during emergencies. Security consultants also may advise on building maintenance issues.
What services does a security consultants provide?
Security consultants can also help to incorporate security changes at all levels of the company. Based upon the security audit that’s conducted, a security consultant, if allowed to, can implement various new security measures and procedures throughout the company, which can include security related to:
Analyzing areas that are currently exposed and if they have had their security compromised in the past;
Performing a gap analysis in order to determine if any areas of a company’s current security does not meet accepted industry standards;
Gauging the work environment through performing interviews with important personnel and company employees;
Providing a list of recommendations based upon found security vulnerabilities, which includes security measures that should be incorporated.
Policies and procedures;
Electronic surveillance and alarm systems;
Security personnel.
A security consultant will work closely with management for the purposes of transparent communication and to make sure that any security changes that are implemented are done so within the allotted budget. The degree to which a security consultant can incorporate security changes depends largely upon this, in addition to the management’s instructions.
CyberSecOp Security Services has been providing expert security consulting services for decades. Make sure to contact us today to ask about our advanced security consulting services, which will be personalized to your company’s particular needs.
HHS voluntary healthcare cybersecurity practices
The Department of Health and Human Services has released voluntary cybersecurity practices to the healthcare industry to move organizations “towards consistency” in mitigating cyber threats.
According to HHS, the four-volume publication guides “cost-effective methods that a range of healthcare organizations at every size and resource level can use to reduce cybersecurity risks.” It is meant to raise awareness of cyber threats and provide vetted practices.
“Cybersecurity is everyone’s responsibility—it is the responsibility of every organization working in healthcare and public health,” says HHS Acting Chief Information Security Officer Janet Vogel. “In all of our efforts, we must recognize and leverage the value of partnerships among government and industry stakeholders to tackle the shared problems collaboratively.”
HHS Headquarters in Washington, D.C.
Mandated by the Cybersecurity Act of 2015, HHS convened more than 150 cyber and healthcare experts from government and industry to develop the recommended practices as part of the Healthcare and Public Health Sector Critical Infrastructure Security and Resilience Public-Private Partnership.
“The healthcare industry is truly a varied digital ecosystem—we heard loud and clear through this process that providers need actionable and practical advice, tailored to their needs, to manage modern cyber threats,” says Erik Decker, industry co-lead and chief information security and privacy officer at the University of Chicago Medicine. “That is exactly what this resource delivers; recommendations stratified by the organization's size, written for both the clinician and the IT subject matter expert.”
In addition to the main document, which lays out the five most relevant and current threats to the industry, the publication also recommends ten cybersecurity practices to help mitigate these threats. It also includes two technical volumes geared for IT and security professionals: Technical Volume 1 focuses on cybersecurity practices for small healthcare organizations. In contrast, Technical Volume 2 focuses on techniques for medium and large healthcare organizations.
Microsoft's Emergency Internet Explorer Patch - Kills Lenovo Laptops
Only a few days ago, Microsoft released an emergency Internet Explorer patch bundled in a cumulative update. The patch was rolled out to fix the zero-day vulnerability in Internet Explorer first discovered by a
However, it seems like the patch is creating more problems than fixing them. Out of many known issues, as mentioned by Microsoft in the changelog, one can be regarded as a more severe issue since it is leaving many Lenovo laptops unbootable after installing the patch.
Microsoft mentions that the issue is only affecting Windows 10 users who have a Lenovo laptop that has less than 8 GB RAM. On the other hand, few sources tell that the issue has only affected PC’s that are still on the 1607 version, or Windows 10 Anviersary Update (2016).
Considering only enterprise PCs have the ability to delay updates, they are most likely have been affected by the unbootable issue.
If you have installed the latest “KB4467691” cumulative update on your PC, and are facing the same issue, here are some steps that Microsoft wants you to follow —
Restart the affected machine using UEFI. After this, disable Secure Boot and then perform restart.
If BitLocker is enabled on your computer, you may have to go through BitLocker recovery after Secure Boot has been disabled.
HIPAA Modernization of Security Standards
HIPAA Modernization of Security Standards
The Health Insurance Portability and Accountability Act, better known (if not always spelled correctly) as HIPAA, was signed into law by President Bill Clinton in August 1996.
A lot has changed in the two decades since – in the ways consumers interact with health systems and the ways technology is transforming care delivery and the patient experience. So maybe it's time to give the privacy law a refresh, said the American Medical Informatics Association and the American Health Information Management Association.
WHY IT MATTERS
As access to personal health information is easier than ever, with smartphones now ubiquitous and apps and connected devices proliferating by the day, both AMIA and AHIMA have voiced support for HIPAA modernization.
In a joint appearance on Capitol Hill, in a presentation about unlocking data for patient empowerment, experts from the two groups highlighted how healthcare has a lot of catching up to do to serve a population used to online shopping, travel booking, review sites and more.
Webinar: The Future of Medicine: Protecting Privacy Without Impacting Quality of Care
Toward this vision of improved patient experience, AMIA and AHIMA said U.S. policymakers should take steps to update HIPAA to enable greater data access and portability – something that looks more likely than it did even a few months ago.
It could be done in a couple different ways, they said. First, potentially, by establishing a new concept of a health data set, with that HDS comprising all the clinical, biomedical and claims data maintained by a covered entity or business associate.
Another option is to revise HIPAA's existing "designated record set" definition, requiring certified health IT products to provide that amended DRS to patients digitally – enabling in a way that enables them to use and reuse their data.
They explained that a new definition for HDS would support individual HIPAA right of access and guide the future development of ONC's Certification Program so individuals could view, download, or transmit to a third party this information electronically and access this information via application programming interface.
Revising the existing DRS definition, meanwhile, offer more clarity and predictability for both providers and patients, AMIA and AHIMA said.
THE LARGER TREND
Even as the availability and maturity of consumer technology has improved, "more than two decades after Congress declared access a right guaranteed by law, patients continue to face barriers," said Dr. Thomas Payne, medical director, IT Services at UW Medicine. "We need a focused look at both the technical as well as social barriers."
AMIA and AHIMA called a broader conversation regarding consumer data privacy, and called on Congress to "extend the HIPAA individual right of access and amendment to non-HIPAA Covered Entities that manage individual health data, such as mHealth and health social media applications. The goal is uniformity of data access policy, regardless of covered entity, business associate, or other commercial status."
Moreover, the groups said regulators should clarify existing regulatory guidance related, for example, to third-party legal requests, such as those by lawyers looking for information without appropriate patient permissions.
ON THE RECORD
"Congress has long prioritized patients' right to access their data as a key lever to improve care, enable research, and empower patients to live healthy lifestyles," said Dr. Doug Fridsma, president and CEO and AMIA. "But enacting these policies into regulations and translating these regulations to practice has proven more difficult than Congress imagined."
"AHIMA's members are most aware of patient challenges in accessing their data as they operationalize the process for access across the healthcare landscape," said AHIMA CEO Wylecia Wiggs Harris, in a statement. "The language in HIPAA complicates these efforts in an electronic world."
MSSP Cybersecurity & Managed Detection and Response
MSSP Cybersecurity & Managed Detection and Response
Managed detection and response enables a proactive approach to security with its ability to detect and fully analyze threats and promptly respond to incidents. CyberSecOp Threat intelligence is one of the key aspects our security consultants used to help organizations make decisions on how to combat threats. Through managed detection and response, organizations can take advantage of the threat intelligence capabilities of security experts.
How Managed Detection and Response Provides Effective Threat Intelligence
Capture full visibility across your entire IT environment
Detect the most advanced threats (known and unknown) designed to bypass your traditional perimeter security controls, even when no malware is used
Expose threat actors currently hiding in your environment
Gain 24x7 monitoring by an advanced team of security experts that are specially trained to analyze advanced threats, determine the severity of any incidents and provide actionable guidance to remediate
Quickly elevate the alerts that matter most so you can focus limited resources where it matters most
Managed Detection and Response Service
Managed Detection and Response (MDR) is an all-encompassing cybersecurity service used to detect and respond to cyber-attacks. Using the best of signature, behavioral and anomaly detection capabilities, along with forensic investigation tools and threat intelligence, human analysts hunt, investigate and respond to known and unknown cyber threats in real time 24x7x365. Get Managed Detection and Response Services for your business www.cybersecop.com.
Data Breaches Ransomware and Cyber Attacks
Data Breaches Ransomware and Cyber Attacks
It’s unrealistic to think that you can completely avoid cyberattacks and data breaches, so it’s vital to have a proper data recovery plan in place. You can also tighten your defenses significantly by ensuring all of your network devices are properly configured, and by putting some thought into all of your potential network borders.
Data Recovery Capability
Do you have a proper backup plan in place? Have you ever tested it to see that it works? Disaster recovery is absolutely vital, but an alarming number of companies do not have an adequate system in place. A survey of 400 IT executives by IDG Research revealed that 40% rate their organizations’ ability to recover their operations in the event of disaster or disruption as “fair or poor.” Three out of four companies fail from a disaster recovery standpoint, according to the Disaster Recovery Preparedness Benchmark.
A successful malware attack can lead to altered data on all compromised machines and the full effects are often very difficult to determine. The option to roll back to a backup that predates the infection is vital. Backed up data must be encrypted and physically protected. It’s also important that a test team routinely checks a random sampling of system backups by restoring them and verifying data integrity.
Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
The default configurations for network devices like firewalls, routers, and switches are all about ease of use and deployment. They aren’t designed with security in mind and they can be exploited by determined attackers. There’s also a risk that companies will create exceptions for business reasons and then fail to properly analyze the potential impact.
The 2015 Information Security Breaches Survey found that failure to keep technical configuration up to date was a factor in 19% of incidents. Attackers are skilled at seeking out vulnerable default settings and exploiting them. Organizations should have standardized secure configuration guidelines applied across devices. Security updates must be applied in a timely fashion.
You need to employ two-factor authentication and encrypted sessions when managing network devices, and engineers should use an isolated, dedicated machine without Internet access. It’s also important to use automated tools to monitor the network and track device configurations. Changes should be flagged and rule sets analyzed to ensure consistency.
Boundary Defense
When the French built the Maginot Line in World War II, a series of impregnable fortifications that extended along the border with Germany and beyond, it failed to protect them because the Germans invaded around the North end through neutral Belgium. There’s an important lesson there for security professionals: Attackers will often find weaknesses in perimeter systems and then pivot to get deeper into your territory.
They may gain access through a trusted partner, or possibly an extranet, while your defensive eye is focused on the Internet. Effective defenses are multi-layered systems of firewalls, proxies, and DMZ perimeter networks. You need to filter inbound and outbound traffic and take caution not to blur the boundaries between internal and external networks. Consider network-based IDS sensors and IPS devices to detect attacks and block bad traffic.
Segment your network and protect each sector with a proxy and firewall to limit access as far as possible. If you don’t have internal network protection, then intruders can get their hands on the keys to the kingdom by successfully breaching the outer defenses.
The real cost
A lot of businesses argue that they can’t afford a comprehensive disaster recovery plan, but they should really consider whether they can afford to lose all their data or be uncertain about its integrity. They may lack the expertise to ensure that network devices are securely configured, but attackers don’t lack the skills to exploit that. It’s understandably common to focus on the outer boundary of your network and forget about threats that come from unexpected directions or multiply internally, but it could prove costly indeed.
Compared to the cost of a data breach, all of these things are cheap and easy to set up
Cyber Insurance - Is a must have - you will need it
Cyber Insurance - Is a must have - you will need it.
It’s every healthcare organization’s nightmare to get the call that their data has been breached or hacked. As a result, many have turned to cyber insurance to protect assets and business operations.
As cyber policies and carriers lack a universal policy, there’s an even greater worst case scenario: An organization is breached, and the policy doesn’t cover what the leaders thought it did. Now, not only is the healthcare provider strapped with the burden of the breach, it wasted money on a useless cyber insurance policy.
To get a better grasp on how to choose the right policy, Healthcare IT News asked attorney Matthew Fisher, partner with Mirick O’Connell, and Jane Harper, Henry Ford Health System’s director of privacy and security risk management, to outline the biggest policy mistakes -- and how to avoid them.
Mistake #1: Rushing the process
When buying a policy, a carrier will provide a questionnaire that will evaluate your organization’s security posture, program, tools and policies. The biggest mistake is to rush the pre-policy process to see the rates and what the carrier will cover, explained Fisher.
Organizations need to be conservative with how they answer the questions, as “it could be a ground for denial, if you don’t have the policies you said you have in place,” said Fisher. “You have to make sure you’re not unintentionally misleading the insurance company when it comes to coverage.”
Often these questionnaires attempt to create a black and white policy and “it can be tough to answer correctly,” explained Fisher.
“Your ability to be as transparent and truthful upfront is critical to the nonpayment discussion,” said Harper. “If you tell the insurance company that you have everything in place and are compliant, if you tell them that and then you have an issue, and you weren’t truthful, it ends up being a legal battle.”
“When you submit your checklist that they have you fill out, meet with the underwriter to make sure you understand what you’ve documented,” she added. “You also need the copy that was provided to the insurance company because it will come back into play when you submit the final documents.”
For example, if you say you have a specific control in place, and you actually don’t, Harper explained that can create a situation where “they thought they had an understanding of something, but they didn’t.”
“Be honest, transparent and accurate -- because they can deny your policy if you were inaccurate or misleading in your responses,” she said.
Mistake #2: Lax, incomplete risk assessment
It’s easier to prevent a misleading or false statement to an underwriter, when an organization has a strong assessment and inventory of the processes and tools on the system. But far too often, hospitals “don’t know everything about the control environment,” explained Harper.
“When you talk about protecting an system and preventing a cyber incident, you have to have a good understanding of the organization’s overall control environment,” Harper said. “It’s key, as the longer it takes you to identify that you’ve had an incident, it leads to more exposure and the longer it takes to recover.”
But it’s also important to remember to update this inventory or assessment when buying new tools, merging with other organizations, hiring new staff and the like, Harper explained.
“Think about all of the activities and operations that happen,” she said. “And every three years, you’re updating a cybersecurity checklist -- that may not be frequent enough.”
For example, Harper explained that an organization filling out the policy questionnaire may have all of the right elements in place. But if another tool was purchased and the controls weren’t updated or the control was removed and the underwriter was not notified, there could be a problem.
“If those controls played into how the underwriter rated you: that can be key,” said Harper. “Think about your own home: you get additional discounts when you have a burglar alarm. So if you get one, and let them know, you may get a lower rate… But if you no longer have that control, you have to tell the carrier.”
“It’s the same kind of practice that we want to get into when we get into cyber insurance for our organization,” she added.
Mistake #3: Failing to involve the right people
Many organizations understand that security needs to exist outside of the IT team. In the same vein, it’s crucial when buying a cyber insurance policy that the same mentality is applied to make sure all of your bases are covered.
“Make sure you are talking to the right individuals,” Harper said. “The appropriate key stakeholders are not only involved with the evaluation process - how many patients, how much data, etc. -- but also the responses to the questions the policy is going to ask.”
“Risk folks typically talk about it as it relates to patients,” she continued. “Those folks are key, but in addition, you need your privacy and security risk professionals, security officers, IT leader, your key business leaders/owners and those driving the data. It’s key.”
Also crucial? Making sure the facilities team is involved, as there can sometimes be a cyber incident based on a physical issue. Harper explained that “often people tend to focus on things like electronic PHI, but there’s physical PHI. If there’s a break in at a warehouse and data is stolen, OCR considers that a breach.”
Mistake #4: Failing to understand coverage
Far too often organizations make large assumptions as to just what cyber insurance will cover. Fisher explained that these leaders are often shocked to learn that they did not receive the full spectrum of coverage they wanted.
“Relying on blind faith on those terms, or what the broker or agent is telling you is a major mistake,” said Fisher. “It’s always up to up to you to go into something with eyes fully wide open to make sure you know what you’re actually buying.”
Harper took it a step further and laid to rest a common misconception when it comes to coverage: “Insurance will not cover fines and penalties associated with noncompliance. If you’re not complaint, and you didn’t do risk assessments, cyber insurance won’t protect you from that, so don’t expect it.”
Ransomware Business Impacts, Ransomware Business Cost
Projecting the overall cost of a ransomware attack can be tricky for security executives considering the many factors that can come into play when responding to and recovering from one. Information from numerous previous incidents show the costs go well beyond any demanded ransom amount and the costs associated with cleaning infected systems.
Ransomware is defined as a form of malicious software that is designed to restrict users from accessing their computers or files stored on computers till they pay a ransom to cybercriminals. Ransomware typically operates via the crypto virology mechanism, using symmetric as well as asymmetric encryption to prevent users from performing managed file transfer or accessing particular files or directories. Cybercriminals use ransomware to lock files from being used assuming that those files have extremely crucial information stored in them and the users are compelled to pay the ransom in order to regain access.
Ransomware History
It’s been said that Ransomware was introduced as an AIDS Trojan in 1989 when Harvard-educated biologist Joseph L. Popp sent 20,000 compromised diskettes named “AIDS Information – Introductory Diskettes” to attendees of the internal AIDS conference organized by the World Health Organization. The Trojan worked by encrypting the file names on the customers’ computer and hiding directories. The victims were asked to pay $189 to PC Cyborg Corp. at a mailbox in Panama.
From 2006 and on, cybercriminals have become more active and started using asymmetric RSA encryption. They launched the Archiveus Trojan that encrypted the files of the My Documents directory. Victims were promised access to the 30-digit password only if they decided to purchase from an online pharmacy.
After 2012, ransomware started spreading worldwide, infecting systems and transforming into more sophisticated forms to promote easier attack delivery as the years rolled by. In Q3, about 60,000 new ransomware was discovered, which doubled to over 200,000 in Q3 of 2012.
The first version of CryptoLocker appeared in September 2013 and the first copycat software called Locker was introduced in December of that year.
Ransomware has been creatively defined by the U.S. Department of Justice as a new model of cybercrime with a potential to cause impacts on a global scale. Stats indicate that the use of ransomware is on a steady rise and according to Veeam, businesses had to pay $11.7 on average in 2017 due to ransomware attacks. Alarmingly, the annual ransomware-induced costs, including the ransom and the damages caused by ransomware attacks, are most likely to shoot beyond $11.5 billion by 2019.
Ransomware Business Impacts Can Be Worrisome
Ransomware can cause tremendous impacts that can disrupt business operations and lead to data loss. The impacts of ransomware attacks include:
Loss or destruction of crucial information
Business downtime
Productivity loss
Business disruption in the post-attack period
Damage of hostage systems, data, and files
Loss of reputation of the victimized company
You will be surprised to know that apart from the ransom, the cost of downtime due to restricted system access can bring major consequences. As a matter of fact, losses due to downtime may cost tens of thousands of dollars daily.
As ransomware continues to become more and more widespread, companies will need to revise their annual cybersecurity goals and focus on the appropriate implementation of ransomware resilience and recovery plans and commit adequate funds for cybersecurity resources in their IT budgets.
Consider the following examples. The Erie County Medical Center (ECMC) in Buffalo, NY, last July estimated it spent $10 million responding to an attack involving a $30,000 ransom demand. About half the amount went toward IT services, software, and other recovery-related costs. The other half stemmed from staff overtime, costs related to lost revenues, and other indirect costs. ECMC officials estimated the medical center would need to spend hundreds of thousands of dollars more on upgrading technology and employee awareness training.
Public records show that the City of Atlanta spent almost $5 million just in procuring emergency IT services following a March 2018 ransomware attack that crippled essential city services for days. The costs included those associated with third-party incident response services, crisis communication, augmenting support staff and subject matter expert consulting services.
In Colorado, Gov. John Hickenlooper had to set aside $2 million from the state disaster emergency fund after ransomware infected some 2,000 Windows systems at CDOT, the state department of transportation, this February. In less than eight weeks, CDOT officials spent more than half that amount just returning systems to normal from the attack.
Not surprisingly, industry estimates relating to ransomware damages have soared recently. Cybersecurity Ventures, which pegged ransomware costs at $325 million in 2015, last year estimated damages at $5 billion in 2017 and predicted it would exceed $11.5 billion in 2019.
For security executives trying to prepare a total ransomware cost estimate, the key is not to get fixated on the ransom amount itself. Even if you end up paying it to recover your data—something that most security analysts advocate against—the actual costs of the attack in most cases will end up being greater.
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
Prevent DDoS attacks across your enterprise
DDoS (Distributed Denial of Service) attacks feature amongst the most dreaded kinds of cyber attacks, for any enterprise today. This is especially because, as the name itself suggests, there it causes a total denial of service; it exhausts all resources of an enterprise network, application or service and consequently it becomes impossible to gain access to the network, application or the service.
In general, a DDoS attack is launched simultaneously from multiple hosts and it would suffice to host the resources, the network and the internet services of enterprises of any size. Many prominent organizations today encounter DDoS attacks on a daily basis. Today DDoS attacks are becoming more frequent and they are increasing in size, at the same time becoming more sophisticated. In this context, it becomes really important that enterprises look for DDoS attack prevention services, in fact the best DDoS attack prevention services, so as to ensure maximum protection for their network and data.
The different kinds of DDoS attacks
Though there are different kinds of DDoS attacks, broadly speaking there are three categories into which all the different kinds of DDoS attacks would fit.
The first category is the volumetric attacks, which include those attacks that aim at overwhelming network infrastructure with bandwidth-consuming traffic or by deploying resource-sapping requests. The next category, the TCP state-exhaustion attacks, refer to the attacks that help hackers abuse the stateful nature of the TCP protocol to exhaust resources in servers, load balancers and firewalls. The third category of DDoS attacks, the application layer attacks, are basically the ones targeting any one aspect of an application or service at Layer 7.
Of the above-mentioned three categories, volumetric attacks are the most common ones; at the same time there are DDoS attacks that combine all these three vectors and such attacks are becoming commonplace today.
DDoS attacks getting sophisticated, complex and easy-to-use
Cybercriminals today are getting cleverer and smarter. They tend to package complex, sophisticated DDoS attack tools into easy-to-use downloadable programs, thereby making it easy even for non-techies to carry out DDoS attacks against organizations.
What are the main drivers behind DDoS attacks? Well, there could be many, ranging from ideology or politics to vandalism and extortion. DDoS is increasingly becoming a weapon of choice for hacktivists as well as terrorists who seek to disrupt operations or resort to extortion. Gamers too use DDoS as a means to gain competitive advantage and win online games.
There are clever cybercriminals who use DDoS as part of their diversionary tactics, intending to distract organizations during APT campaigns that are planned and executed in order to steal data.
How to prevent DDoS attacks
The first thing that needs to be done, to prevent DDoS attacks from happening, is to secure internet-facing devices and services. This helps reduce the number of devices that can be recruited by hackers to participate in DDoS attacks.
Since cybercriminals abuse protocols like NTP, DNS, SSDP, Chargen, SNMP and DVMRP to generate DDoS traffic, it’s advisable that services that use any of these ought to be carefully configured and run on hardened, dedicated servers.
Do repeated tests for security issues and vulnerabilities. One good example is doing penetration tests for detecting web application vulnerabilities.
Ensure that your enterprise implements anti-spoofing filters as covered in IETF Best Common Practices documents BCP 38 and BCP 84. This is because hackers who plan DDoS attacks would generate traffic with spoofed source IP addresses.
Though there are no fool-proof techniques that can prevent DDoS attacks completely, you can ensure maximum protection by ensuring proper configuration of all machines and services. This would ensure that attackers don’t harness publicly available services to carry out DDoS attacks.
It’s to be remembered that it’s difficult to predict or avoid DDoS attacks and also that even an attacker with limited resources can bring down networks or websites. Hence, for any organization, it becomes important that the focus is always on maximum level protection for enterprise networks, devices, websites etc.