CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Cybersecurity Future and Artificial Intelligence (AI)
As businesses struggle to combat increasingly sophisticated cybersecurity attacks, the severity of which is exacerbated by both the vanishing IT perimeters in today’s mobile and IoT era, coupled with an acute shortage of skilled security professionals, IT security teams need both a new approach and powerful new tools to protect data and other high-value assets. Increasingly, they are looking to artificial intelligence (AI) as a key weapon to win the battle against stealthy threats inside their IT infrastructures, according to a new global research study conducted by the Ponemon Institute on behalf of Aruba, a Hewlett Packard Enterprise company (NYSE:HPE).
The Ponemon Institute study, entitled “Closing the IT Security Gap with Automation & AI in the Era of IoT,” surveyed 4,000 security and IT professionals across the Americas, Europe and Asia to understand what makes security deficiencies so hard to fix, and what types of technologies and processes are needed to stay a step ahead of bad actors within the new threat landscape.
The research revealed that in the quest to protect data and other high-value assets, security systems incorporating machine learning and other AI-based technologies are essential for detecting and stopping attacks that target users and IoT devices. The majority of respondents agree that security products with AI functionality will help to:
Reduce false alerts (68 percent)
Increase their team’s effectiveness (63 percent)
Provide greater investigation efficiencies (60 percent)
Advance their ability to more quickly discover and respond to stealthy attacks that have evaded perimeter defense systems (56 percent)
Twenty-five percent of respondents said they currently use some form of an AI-based security solution, with another 26 percent stating they plan on deploying these types of products within the next 12 months.
Current Security Tools are not Enough
“Despite massive investments in cybersecurity programs, our research found most businesses are still unable to stop advanced, targeted attacks – with 45 percent believing they are not realizing the full value of their defense arsenal, which ranges from 10 to 75 security solutions,” said Larry Ponemon, chairman, Ponemon Institute. “The situation has become a ‘perfect storm,’ with nearly half of respondents saying it’s very difficult to protect complex and dynamically changing attack surfaces, especially given the current lack of security staff with the necessary skills and expertise to battle today’s persistent, sophisticated, highly trained, and well-financed attackers. Against this backdrop, AI-based security tools, which can automate tasks and free up IT personnel to manage other aspects of a security program, were viewed as critical for helping businesses keep up with increasing threat levels.”
IoT and Cloud Adds Significant Risk
Ponemon researchers found that the majority of IT security teams believe that a key gap in their company’s overall security strategy is their inability to identify attacks that use IoT devices as the point of entry. In fact, more than three-quarters of respondents believe their IoT devices are not secure, with 60 percent stating even simple IoT devices pose a threat. Two-thirds of respondents admitted they have little or no ability to protect their “things” from attacks. Continuous monitoring of network traffic, closed-loop detection and response systems, and detecting behavioral anomalies among peer groups of IoT devices, were cited as the most effective approaches to better protect their environments.
Even the ownership model for IoT security presents potential risk. When asked who inside their organization was responsible for IoT security, responses ranged from the CIO, CISO, CTO, and line-of-business leaders, with no majority consensus. Only 33 percent identified the CIO, with no other executive or functional group achieving response totals above 20 percent. Surprisingly, “No Function” was the third-highest answer (15 percent).
Survey results also highlighted the importance of visibility and the ability to define which resources that people and IoT devices can access, with 63 percent of respondents stating network access control is an important element of their company’s overall security strategy and critical for reducing the reach of inside exploits. Also cited as important was having detailed information about applications (71 percent), endpoints (69 percent), cloud (64 percent), and networks (63 percent), with more than half saying they currently deploy network access control solutions for enabling visibility and control across both wired and wireless networks.
Additionally, more than half of respondents said it’s hard to protect expanding and blurring IT perimeters resulting from requirements to concurrently support IoT, BYOD, mobile, and cloud initiatives (55%).
“Partnering with the Ponemon Institute helps us to improve customer experiences by better understanding security teams’ challenges, and then arming them with advanced solutions that enable quick identification and responses to an ever-changing threat landscape,” said Larry Lunetta, vice president of security solutions marketing for Aruba. “The insight gained from this study enables us to continually improve our ability to provide an enterprise wired and wireless network security framework with an integrated and more comprehensive approach for gaining back visibility and control.”
FBI: Protecting Your Networks from Ransomware
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
What is Ransomware”
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment. Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails. For additional information on Avoiding Social Engineering and Phishing Attacks.
Ransomware Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Ransomware Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. USG does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
How Law Enforcement Can Help
Any entity infected with ransomware should contact law enforcement immediately. Law enforcement may be able to use legal authorities and tools that are unavailable to most organizations. Law enforcement can enlist the assistance of international law enforcement partners to locate the stolen or encrypted data or identify the perpetrator. These tools and relationships can greatly increase the odds of successfully apprehending the criminal, thereby preventing future losses.
Federal law enforcement places a priority on conducting cyber investigations in a manner that causes minor disruption to a victim entity’s normal operations and seeks to work cooperatively and discreetly with that entity. Federal law enforcement uses investigative measures that avoid unnecessary downtime or displacement of a company’s employees. Federal law enforcement closely coordinates its activities with the affected organization to avoid unwarranted disclosure of information.
As an affected entity recovers from a cybersecurity incident, the entity should initiate measures to prevent similar incidents. Law enforcement agencies and the Department of Homeland Security’s National Cybersecurity and Communications Integration Center can assist organizations in implementing countermeasures and provide information and best practices for avoiding similar incidents in the future. Additionally, the affected organization should conduct a post-incident review of their response to the incident and assess the strengths and weaknesses of its incident response plan.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor ” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising .
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
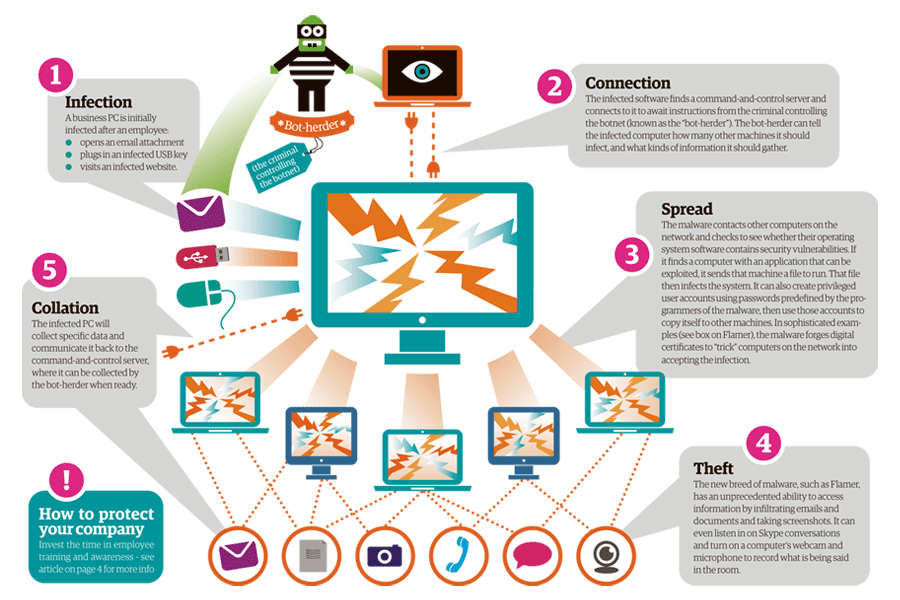
HOW DOES RANSOMWARE WORK?
HOW DOES RANSOMWARE WORK?
Ransomware infections occur when a user opens a malicious email attachment, clicks on a malicious link, or visits a website infected with malicious code, known as a drive-by download.
Once a system is infected, the ransomware contacts a command and control (C2) server to generate an encryption key and begins encrypting files on the victim’s machine.
The ransomware runs quietly in the background performing in-depth searches of all disk folders, including removable drives and network shares, and encrypts as many files as it can.
Ransomware may also delete Shadow Volume Copies, destroy restore points, and overwrite free disk space to prevent victims from recovering their files and systems without paying the ransom.
If a system is powered off as files are being encrypted, some ransomware variants resume where they left off when the system or device is powered on again.
After files are encrypted, a ransom note is displayed on the screen with instructions on how and where to pay the ransom and the length of time before the hacker or software destroys the decryption key.
Some recent variants offer victims a ‘second chance’ to pay after the initial timer expires; however, the ‘second chance’ is often at least double the original ransom amount.
If the victim pays the ransom, the malware is supposed to contact the C2 server for the decryption key and begin decrypting the victim’s files; however, in many cases, the files are never decrypted.
Some ransomware files can delete themselves in order to avoid detection and analysis by security researchers or law enforcement.
CyberSecOP: Ransomware Remediation and Prevention Service
RANSOMWARE MITIGATION STRATEGIES
For many organizations, preventing ransomware entirely is nearly impossible, however, the impact of a successful infection can be greatly reduced if a robust data backup process is in place. Comprehensive data backups should be scheduled as often as possible and must be kept offline in a separate and secure location. The most effective method to prevent ransomware infections is to conduct regular training and awareness exercises with all employees to ensure users are proficient in safe Internet-browsing techniques and the ability to identify phishing emails. For specific recommendations for data protection, systems management, network management, mobile device management, and post-infection remediation.
5 steps for preventing ransomware
5 steps for preventing ransomware
Hardening Your Environment Against Ransomware
To avoid ransomware infection, follow these steps:
1. Back up your computers and servers regularly.
Regularly back up the files on both the client computers and servers. Either back up the files when the computers are offline or use a system that networked computers and servers cannot write to. If you do not have dedicated backup software, you can also copy the important files to removable media. Then eject and unplug the removable media; do not leave the removable media plugged in.
2. Lock down mapped network drives by securing them with a password and access control restrictions.
Use read-only access for files on network drives, unless it is absolutely necessary to have write access for these files. Restricting user permissions limits which files the threats can encrypt.
3. Deploy and enable the following Endpoint Protection:
Implement and managed endpoint antivirus on all endpoint to prevent ransomware, most ransomware can be detected by popular antivirus.
4. IPS/IDS
IPS blocks some threats that traditional virus definitions alone cannot stop. IPS is the best defense against drive-by downloads, which occurs when software is unintentionally downloaded from the Internet. Attackers often use exploit kits to deliver a web-based attack like CryptoLocker through a drive-by download.
See Enabling network intrusion prevention or browser intrusion prevention.
5. Download the latest patches for web application frameworks, web browsers, and web browser plug-ins.
Attacking exploit kits cannot deliver drive-by downloads unless there is an old version of a plug-in to exploit, such as Flash. Historically, attacks were delivered through phishing and web browsers. Recently, more attacks are delivered through vulnerable web applications, such as JBOSS, WordPress, and Joomla.
6. Use an email security product to handle email safely.
CryptoLocker is often spread through spam emails that contain malicious attachments. Scanning inbound emails for threats with a dedicated mail security product or service is critical to keep ransomware and other malware out of your organization. For important advice and recommendations, see:
How to remove ransomware
There is no ransomware removal tool or CryptoLocker removal tool. Instead, if your client computers do get infected with ransomware and your data is encrypted, follow these steps:
1. Do not pay the ransom.
If you pay the ransom:
· There is no guarantee that the attacker will supply a method to unlock your computer or decrypt your files.
· The attacker uses the ransom money to fund additional attacks against other users.
2. Isolate the infected computer before the ransomware can attack network drives to which it has access.
3. Update the virus definitions and scan the client computers.
New definitions are likely to detect and remediate the ransomware. Configure Endpoint Protection to automatically downloads virus definitions to the client, as long as the client is managed and connected to the Symantec Endpoint Protection Manager.
4. Restore damaged files from a known good backup.
No security Endpoint Protection cannot decrypt the files that ransom lockers have sabotaged.
Submit the malware to antivirus provider.
If you can identify the malicious email or executable, submit it to antivirus provider.
Remediate Ransomware Attack - Ransomware Survival
Made famous by the WannaCry attack that crippled the NHS in 2017, ransomware is continuing to hit businesses. According to security research firm Symantec, infections have steadily increased every year since 2013, reaching record levels in 2017.
Even over the last few months, ransomware has impacted multiple organizations, including the PGA of America, and the borough of Matanuska-Susitna in Alaska – where government workers were forced to use typewriters to carry out their daily tasks.
It is not surprising that governments are concerned about the impact of the malicious software, which locks a user’s device or data until they pay a ransom. In the UK, the National Cyber Security Centre (NCSC) has published advice on mitigating against ransomware. Meanwhile, the UK government’s behavioral change campaign for cybersecurity, Cyber Aware, promotes simple measures to stay more secure online.
RANSOMWARE REMEDIATION, RANSOMWARE PREVENTION, AND THREAT RESPONSE SERVICES
No need to configure cryptocurrency wallets or transaction with the cybercriminals. We support the transaction while charging you no commission or crypto exchange fees.
We will negotiate with the ransomware hacker to reduce ransom.
We will remove the ransomware virus or viruses
We will run the ransomware decryption tool, to ensure it doesn’t affect any other system.
But according to security researchers, there has been a decline in ransomware compared to other threats including cryptomining. Yet the malicious software remains a very real risk: attacks are becoming fewer but more targeted. “The major difference between 2017 and 2018 appears to be a trend towards more targeted ransomware,” says Matt Shabat, strategy director at Glasswall Solutions. “Instead of seeking mass infections through relatively blunt means, threat actors are using more precise infection vectors to achieve initial compromise.”
Identifying ransomware
Ransomware comes in two types. The first encrypts the files on a computer or network; the second locks a user's screen. “Some ransomware will also act like a worm – as was the case with WannaCry – and once inside a network, will spread laterally to other machines without interaction by the attacker or the infected user,” says a NCSC spokesman.
Occasionally, malware is presented as ransomware, but after the ransom is paid the files are not decrypted. This is known as ‘wiper’ malware.
The ‘ransom’ is often demanded in a cryptocurrency such as Bitcoin as a prepaid card or gift voucher. In many cases the ransom amount is modest, a tactic designed to make paying the quickest and cheapest way to resume use.
Generally, if a firm is hit by ransomware, they will have no problem realising. Infected computers will be inaccessible because key files have been encrypted, with a ransom note displayed on-screen.
Most ransomware pops up a pay page, either in a text editor or on a browser, says Paul Ducklin, senior technologist at Sophos. “But a lot of it also changes your desktop wallpaper to a graphical image of the pay page.”
And sadly, the first sign of compromise may already be too late, especially if ransomware has spread network-wide and every desktop is hijacked, says Chris Boyd, malware analyst at Malwarebytes. “Much of it comes down to basic social engineering, and fake emails aimed at HR with dubious receipt attachments harboring an infection.”
Recognizing the warning signs: Ransomware and email phishing
Email still remains the top attack vector for all malicious activity, says Adenike Cosgrove, cybersecurity strategist, EMEA, Proofpoint. She says the easiest route for cyber criminals is to exploit the vulnerability of humans “through simple yet sophisticated social engineering tactics”. She explains: “Cybercriminals have found new ways to exploit the human factor — the instincts of curiosity and trust that lead well-intentioned people to play into the hands of the attacker. This could be in the form of a disguised URL or seemingly benign attachment, but all it takes is one click and the ransomware can take hold immediately.”
The majority of ransomware is spread via massive spam campaigns involving hundreds of thousands of emails sent daily, says Dick O'Brien, threat researcher at Symantec.
Ransomware may also be spread via websites compromised to host what’s known as an exploit kit. “This is a tool that scans the visitor’s computer to see if it’s running software with known vulnerabilities,” says O’Brien. “If it finds any, it will exploit one of these vulnerabilities to download and install ransomware on the victim’s computer.”
In a small number of cases, firms may be specifically targeted by groups who attempt to break into the company’s network and infect as many computers as possible before triggering the ransomware.
How to fight off ransomware
You’ve been hit. So, what do you do?
“A lot of ransomware is poorly coded, or master keys are leaked, and it's worth checking online to see if anyone has built a decryptor tool,” says Boyd. He says his firm Malwarebytes has released standalone versions for certain versions of Petya and Chimera, “and there's many more out there”.
Whatever you do, it is agreed that paying the ransom is a big mistake. Indeed, the National Crime Agency encourages industry and the public not to pay the ransom.
“We strongly advise not to pay the ransom, as it simply encourages the scammers to continue with their profitable business model,” agrees Boyd.
Jake Moore, cybersecurity specialist at ESET says he always advises against paying. “But I have seen CEOs with their heads in their hands asking me, ‘what else can we do?’ when they realise their resilience measures have also been attacked.”
Yet there is no guarantee that you will ever receive the data back and if you do, it might be damaged. “Funding cyber criminals also funds larger cyber-attacks, so it must be reiterated that paying won't always get make the issue go away,” says Moore.
Avoiding future attacks requires preparation such as incident response plans and educating employees.
organizations aren't training employees in security basics. “Perhaps they're not sending out emails warning about common scams, or maybe they aren't bothering with security tools known to prevent exploits and ransomware.”
Employees should be trained on how to spot attacks. This helps to avoid becoming a victim, and also means staff can raise the alarm straight away, says David Moore, managing director, CyberSecOp Security. “Employees can become your strongest line of defense. Attackers will hit as many people in an organization as possible, and one click is all it takes. So, having a workforce of people ready to sound the alarm will help prevent that one click.”
It’s important to look for less obvious attacks. “Looking out for the less obvious attacks is highly advisable. If any hint of files being corrupted or encrypted is immediately addressed at the source, it will help to reduce the extent of an attack.”
It might seem obvious, but backup is integral. Even without other measures, firms would still be able to bring their files back with ease if they had a sensible backup process in place.
Prevent DDoS attacks across your enterprise
DDoS (Distributed Denial of Service) attacks feature amongst the most dreaded kinds of cyber attacks, for any enterprise today. This is especially because, as the name itself suggests, there it causes a total denial of service; it exhausts all resources of an enterprise network, application or service and consequently it becomes impossible to gain access to the network, application or the service.
In general, a DDoS attack is launched simultaneously from multiple hosts and it would suffice to host the resources, the network and the internet services of enterprises of any size. Many prominent organizations today encounter DDoS attacks on a daily basis. Today DDoS attacks are becoming more frequent and they are increasing in size, at the same time becoming more sophisticated. In this context, it becomes really important that enterprises look for DDoS attack prevention services, in fact the best DDoS attack prevention services, so as to ensure maximum protection for their network and data.
The different kinds of DDoS attacks
Though there are different kinds of DDoS attacks, broadly speaking there are three categories into which all the different kinds of DDoS attacks would fit.
The first category is the volumetric attacks, which include those attacks that aim at overwhelming network infrastructure with bandwidth-consuming traffic or by deploying resource-sapping requests. The next category, the TCP state-exhaustion attacks, refer to the attacks that help hackers abuse the stateful nature of the TCP protocol to exhaust resources in servers, load balancers and firewalls. The third category of DDoS attacks, the application layer attacks, are basically the ones targeting any one aspect of an application or service at Layer 7.
Of the above-mentioned three categories, volumetric attacks are the most common ones; at the same time there are DDoS attacks that combine all these three vectors and such attacks are becoming commonplace today.
DDoS attacks getting sophisticated, complex and easy-to-use
Cybercriminals today are getting cleverer and smarter. They tend to package complex, sophisticated DDoS attack tools into easy-to-use downloadable programs, thereby making it easy even for non-techies to carry out DDoS attacks against organizations.
What are the main drivers behind DDoS attacks? Well, there could be many, ranging from ideology or politics to vandalism and extortion. DDoS is increasingly becoming a weapon of choice for hacktivists as well as terrorists who seek to disrupt operations or resort to extortion. Gamers too use DDoS as a means to gain competitive advantage and win online games.
There are clever cybercriminals who use DDoS as part of their diversionary tactics, intending to distract organizations during APT campaigns that are planned and executed in order to steal data.
How to prevent DDoS attacks
The first thing that needs to be done, to prevent DDoS attacks from happening, is to secure internet-facing devices and services. This helps reduce the number of devices that can be recruited by hackers to participate in DDoS attacks.
Since cybercriminals abuse protocols like NTP, DNS, SSDP, Chargen, SNMP and DVMRP to generate DDoS traffic, it’s advisable that services that use any of these ought to be carefully configured and run on hardened, dedicated servers.
Do repeated tests for security issues and vulnerabilities. One good example is doing penetration tests for detecting web application vulnerabilities.
Ensure that your enterprise implements anti-spoofing filters as covered in IETF Best Common Practices documents BCP 38 and BCP 84. This is because hackers who plan DDoS attacks would generate traffic with spoofed source IP addresses.
Though there are no fool-proof techniques that can prevent DDoS attacks completely, you can ensure maximum protection by ensuring proper configuration of all machines and services. This would ensure that attackers don’t harness publicly available services to carry out DDoS attacks.
It’s to be remembered that it’s difficult to predict or avoid DDoS attacks and also that even an attacker with limited resources can bring down networks or websites. Hence, for any organization, it becomes important that the focus is always on maximum level protection for enterprise networks, devices, websites etc.
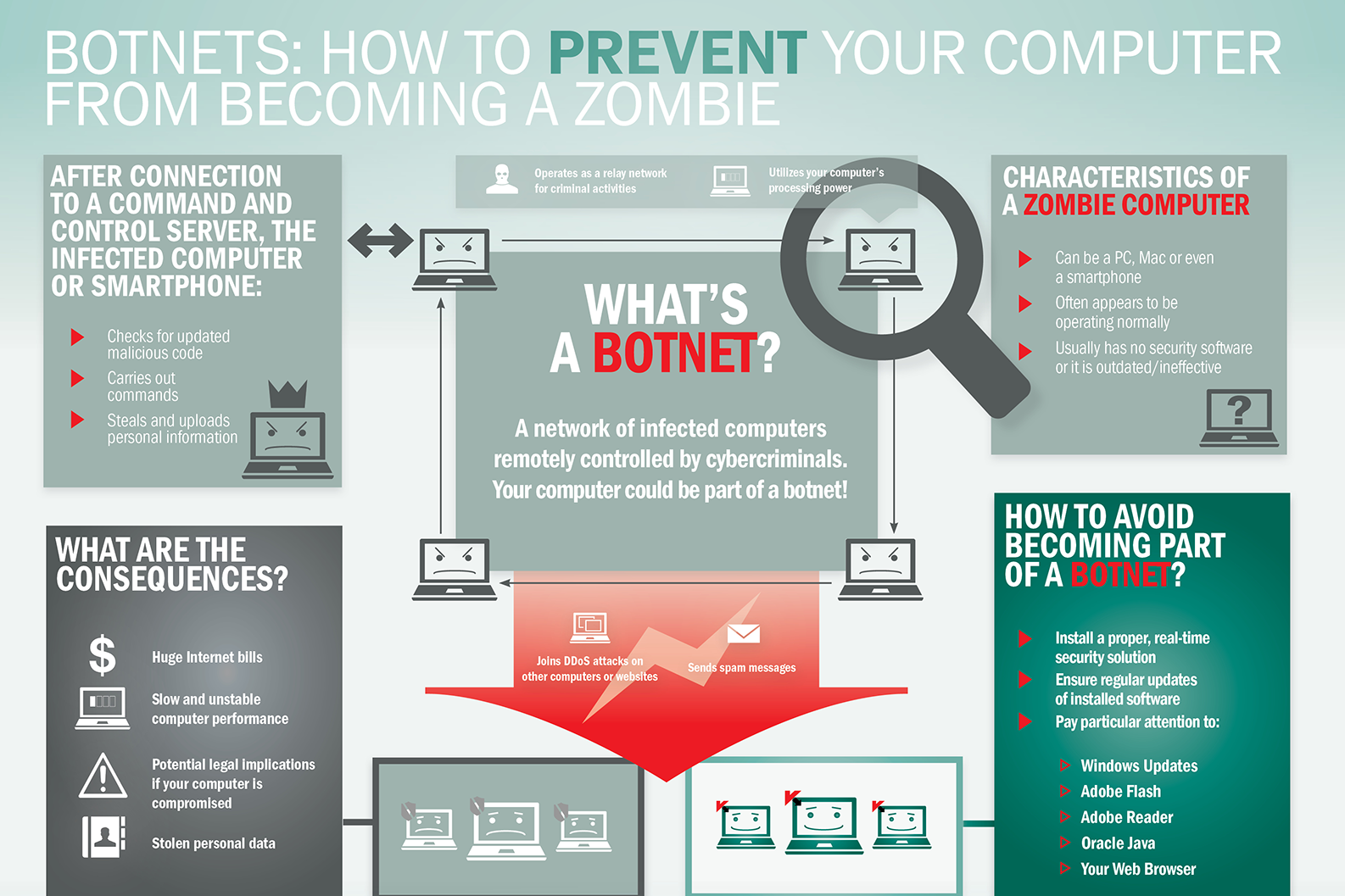
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
What advice does the world's first CISO have
What advice does the world's first CISO have for the current generation of CISOs? Stephen Katz emphasizes, first and foremost, that cybersecurity must be treated as a business risk management issue rather than a technology issue.
"Security has to evolve and grow at the same pace as the business," he stresses in an interview with Information Security Media Group.
The role of the CISO has to be recognized as a core business function, he adds. "Security has to be an enabler of the business; security has to earn a seat at the executive table. Too often, we give people the title of chief information security officer; they don't believe they're an executive, and executives don't believe they are an executive."
In this interview (see audio link below photo), Katz also discusses:
Changes in the threat landscape since becoming the world's first CISO;
Top priorities for CISOs in the coming year;
Why getting back to the basics of security remains so important;
The ongoing growth of machine learning models in all aspects of cybersecurity.
Katz is the founder and president of Security Risk Solutions LLC, an information security company providing consulting, mentoring, coaching and advisory services. He was formerly CISO at JPMorgan Chase, Citigroup and Merrill Lynch.
Secure Google Chrome from Hacking Attacks
Google Chrome is definitely one of the most popular web browsers being used today. Hackers, as we know, are perpetually after whatever gets popular in the world of the internet. This because whatever is popular would help them target more people and steal more data. Thus, Google Chrome too happens to be among the most favorite for cyber criminals across the world. Hence, securing Google Chrome against hacking attacks is really important.
So, how do we secure Google Chrome from cyber attacks? Well, it’s a multi-step process. Lots of things have to be done. Securing your browser is important as it helps secure your device, your internet connection and more importantly, your personal and business data.
Let’s discuss, in detail, what all needs to be done to secure Google Chrome from hacking attacks. Here we go:
Begin by ensuring that your Google account is properly secured!
This is something basic, your Google account needs to be properly secured. Chrome lets you sign in from any device, anytime. Hence, it’s important to ensure the security of your Google account. You need to make sure you are logged out of your account every time you sign in, on any device. You also need to ensure that your password is secure. If you aren’t signed out or if someone knows/cracks your password, it would be easy to manipulate things and cause you harm. Your data could be stolen.
Keeping the browser secured is equally important…
Keeping the browser secured is as important as securing your Google account. You could use a password to protect your browser, and thus, in your absence, no one would be able to take control of your browser and do mischiefs. Similarly, every time you leave your terminal, it’s good to go out of the browser as well.
Keep your browser ‘clean’!
You should make it a habit to keep your browser ‘clean’, by wiping out most of the information from it. In fact, there should be some plan/schedule as regards cleaning the browser. Clear the history periodically, either everytime you log out or at least once every week if not once a day.
Never save passwords on the browser
The browser might offer to ‘remember’ your passwords for you so that you could sign in easily the next time you’re using some service. But it’s always good not to save passwords on the browser. If you save your passwords, it would be possible for someone else to get into your account and misuse it or steal information.
Having a master password helps
Having a master password, which would help you get to your other saved passwords in Chrome, is a good thing to do. Thus you need not worry about remembering all of your passwords and you don’t have to be afraid of your passwords getting stolen or misused either.
Keep your device protected
The device that you use to browse needs to be protected from malware and hacking. For this, you must use whatever security tools you need and also have alerts that tell you if at all your device is compromised. Remember a compromised device means an unsecured browser!
Keep the device locked whenever you’re not using it
Always keep your device locked when you are not using it, be it a computer or any other mobile device. That prevents people from getting on to your device and hijacking your browser and your data as well. Locking your device also gets it off the WiFi network that you are using.
Secure your network, never use unsafe WiFi networks
Securing your network is important; it helps a lot in securing Google Chrome from hacking attacks. Hence you need to do all that is needed to secure your network. Similarly, it’s always advisable never to use unsafe WiFi networks. Whenever you’re using a WiFi network, ensure it’s properly encrypted and if possible use an app or program that would prevent hacking. In fact, using a secure network secures not just your browser, but everything on your device/system.
Trust Chrome for phishing detection
Google Chrome does its own phishing detection and protects you from many phishing websites. So, when your browser tells you that a website is not safe, it’s always advisable to trust it and avoid such sites.
Avoid phishing websites and attachments yourself
In addition to Google Chrome detecting phishing websites for you, it’s always good that you yourself stay away from websites/attachments that could be used for phishing scams. Staying away from such suspicious websites secures your browser, your system/network and your data.
Useful tips for implementing the cloud
Useful tips for implementing the cloud
“One very important thing is to not implement solutions on the cloud with a traditional mindset. Many clients are surprised when they see their first bill because they ‘lift and shift’ the infrastructure,”
“Remember, the cloud is highly elastic in nature and you can scale up and when you require. So, implement the minimum infrastructure needed and scale it based on load. That’s the secret to success in the cloud!”
Focus on entry and exit points in terms of network connectivity. Wherever possible, use private connections such as Microsoft express route, AWS direct connect.
In terms of cloud application connectivity, always encrypt the data in transit using SSL.
Ensure you implement least privileged and conditional based access to cloud administrative portals such as the Azure portal and AWS management console.
Implement RBAC access in providing access to cloud resources. Segregation and isolation of the resources using resource groups, virtual networks is key!
Utilise the security monitoring tools provided by cloud services provider to monitor the solution. Most of the basic functionality is free, such as Azure’s security centre.
In general, always divide the security focus areas into a matrix where rows are networks, compute, storage, applications, databases, and columns are data encryption at rest, encryption at transit, authentication and authorization etc; this will allow focussing on each security cell.
Carry out security risk assessment during the design phase to ensure the design has the appropriate security controls in place to mitigate possible risks.
Nevertheless, problems can arise when storing data in the cloud. “Services & data in the cloud is accessible from the internet. Unless proper controls in place, your users can access and download the data from anywhere in the world,” warns Varma.
Cloud storage security
“The majority of clients require their data to be encrypted in the cloud. Although cloud supports ‘bring your own key’ options, these encryption keys are stored in cloud providers key vaults. So, there is a very narrow chance that cloud providers can access those keys and decrypt the data. It’s also vital to note that cloud providers have very strict governance and accreditations in place to mitigate the same.”
Cloud providers generally keep their cloud services up-to-date with advancements in technology, according to Varma. “On the other end, many of the clients’ data centers he has worked within the past have out-of-date IT infrastructure systems & applications which takes a lot of time and money to replace and are prone to attacks”, he adds.
Varma also advises that you must ask your service provider the following questions about cloud storage security:
What is the authentication and authorization approach to cloud services?
How do you implement access controls for cloud services?
What’s the approach to secure transit and rest data?
What is preventive security monitoring are in place against risks and threats?
Are their solution adheres to such as cyber essentials, cloud security principles, ISO 27002?
Businesses Expansion of Attack Surfaces
One of the main reasons cyber risk increases exponentially is the rapid expansion of attack surfaces. In these places, software programs are vulnerable to attack or probe by an adversary. According to the SANS Institute, attack surfaces can include any part of a company’s infrastructure that exposes its networks and systems to the outside, from servers and open ports to SQLs, email authentication, and even employees with “access to sensitive information.” It can also include user input via keyboard or mouse, network traffic, and external hardware that is not protected by cyber hardening technology.
It would be easy to blame the Internet of Things (IoT) for expanding attacks, as Intel projects two billion smart devices worldwide by 2020. But in reality, the IoT is only part of the attack surface epidemic.
According to Cybersecurity Ventures, there are now 111 billion new lines of code written each year, introducing vulnerabilities both known and unknown. Not to be overlooked as a flourishing attack vector are humans, which some argue are both the most important and the weakest link in the cyberattack kill chain. In fact, in many cybersecurity circles, there is a passionate and ongoing debate regarding just how much burden businesses should put on employees to prevent and detect cyber threats. However, what is not up for debate open is just how vulnerable humans are to intentionally or unintentionally open the digital door for threat actors to walk in. This is most evident because 9 out of 10 cyberattacks begin with some form of email phishing targeting workers with mixed levels of cybersecurity training and awareness.
Critical Infrastructure Protection Remains a Challenge
Critical infrastructure, often powered by SCADA systems and equipment now identified as part of the Industrial Internet of Things (IIoT), is a significant contributor to attack surface expansion. Major attacks targeting these organizations occur more from memory corruption errors and buffer overflows exploits than from spear-phishing or email spoofing and tends to be the motive of nation-states and cyber terrorists more so than generic hackers.
“Industrial devices are designed to have a long life span, but most legacy equipment still in use was not originally built to achieve automation and connectivity.” The IIoT does provide many efficiencies and cost-savings benefits to companies in which operational integrity, confidentiality, and availability are of the utmost importance. Still, introducing technology into heavy machinery and equipment that wasn’t built to communicate outside of a facility has proven challenging. The concept of IT/OT integration, which is meant to merge the physical and digital security of corporations and facilities, has failed to reduce vulnerabilities in a way that significantly reduces risk. As a result, attacks seeking to exploit critical infrastructure vulnerabilities, such as WannaCry, have become the rule and not the exception.
To date, ARE CYBERCRIMINALS winning?
Critical infrastructure cybersecurity has relied too much upon network monitoring and anomaly detection to detect suspicious traffic before it turns problematic. The challenge with this approach is that it is reactionary and only effective after an adversary has breached some level of defense.
We take an entirely different approach, focusing on prevention by denying malware the uniformity it needs to propagate. We use a binary randomization technique that shuffles the basic constructs of a program, known as basic blocks, to produce functionally identical code but legally unique. When an attacker develops an exploit for a known vulnerability in a program, it is helpful to know where all the code is located so that they can repurpose it to do their bidding. Binary randomization renders that prior knowledge useless, as each instance of a program has code in different locations.
One way to visualize the concept of binary randomization is to picture the Star Wars universe at the time when Luke Skywalker and the Rebel Alliance set off to destroy the Death Star. The Rebel Alliance had the blueprints to the Death Star and used those blueprints to find its only weakness. Luke set off in his X-Wing and delivered a proton torpedo directly to the weak spot in the Death Star, destroying it. In this scenario, the Death Star is a vulnerable computer program, and Luke is an adversary trying to exploit said computer program.
Now imagine that the Galactic Empire built 100 Death Stars, protected by RunSafe’s new Death Star Weakness Randomization. This protection moves the weakness to a different place on each Death Star. Now imagine you are Luke, flying full speed toward the flaw in the Death Star, chased by TIE fighters, only to find that the weakfaultnot where the blueprint showed. The Rebel attack fails, and the Galactic Empire celebrates by destroying another planet. Like the Death Star scenario above, code protected with binary randomization will still contain vulnerabilities. Still, an attacker’s ability to successfully exploit that vulnerability on multiple targets becomes much more difficult.
Cyber Criminals Loves the Cloud (Hackers Cloud Life)
Are hackers smarter and more creative than cyber guardians? This is becoming the eternal question of the digital age. While we would like to think the protection of customer passwords and personal credentials is the job of IT experts, reports of recent data breaches now suggest we are losing the battle against online criminals. The situation at hand can be likened to a carjacker who enters a parking lot and simply strolls to the stall where all the keys are kept. The parking guard is mysteriously missing, and the keys are ripe for the taking, even to the big, expensive vehicles. This is essentially the situation hackers are now enjoying on the Cloud—a relatively unguarded and highly accessible environment.
Organizational growth and development have led to increased use of the Cloud, which has exacerbated the problem of compromised user data. Companies have essentially transferred VPN and cloud access credentials to available cloud storage. Hackers are sending bots to scour GitHub, the source code administration framework, searching for advanced access keys to Amazon Web Services and other cloud frameworks. In 2015, one indiscreet developer woke to discover his stolen keys were being utilized to run 140 AWS servers mining bitcoin. Indeed, even U.S. Intelligence facts, including security keys to access “distributed intelligence systems,” were also left exposed to the public suggest Bay Area security firm, UpGuard.
Further, even if credentials aren’t left in a discoverable location, hackers can break into a network and find unprotected or unencrypted keys lying around to gain access. In spite of the dangers, developers are still consistently putting away the digital assets and resources and even client data in the source code, setup documents, and different random, unencrypted areas. Not like run of the mill user who can remember their passwords or store them with a protected secret word, engineers and IT professionals regularly need to keep security credentials where automated programs can find them. What’s more, the sensitive information of ordinary clients is also being inadvertently left unattended on some organization networks, where hackers don’t have to work very hard for access.
SECURING THE CLOUD
Cloud managers are struggling to stop the leak of critical data. Sophisticated new cybersecurity tools designed to safely store these important credentials in a legitimate, automated way are looking to revamp accessibility by scanning uploaded files to the cloud storage to ensure passwords and keys aren’t exposed. According to industry experts, this effort is doing much to turn the tide of cybercrime.
Cloud managers are also trying to close the entryway leading to the exposure of more basic data. Refined new cybersecurity tools want to safely store these sorts of credentials in a genuine way that grants access to automated procedures but not hackers.
Armon Dadgar, founder and co-CTO of San Francisco-based software company HashiCorp explains, “Everyone knew this was a bad thing to do. It wasn’t like anyone had an illusion that keeping these credentials in plain text was smart or sane, but no one had a better answer.”
Amazon launched AWS Secrets Manager last month, its own credential management tool. This was followed by Microsoft’s Azure Key Vault which securely stores, monitors, and controls access to this kind of data. But even as these tools become available, companies with avid developers, all of whom have a wide array of remote tools using credentials, are being continually challenged by security issues. Christoffer Fjellström, a developer at Swedish security firm Detectify says, “The main problem is that companies really don’t have policies for it or they don’t follow up and make sure those policies are followed.”
Recent hacks have made it clear that few organizations can hope to keep their networks entirely free from intrusion. Dadgar goes on to explain, “Many companies paid less attention to the security of data within their firewalls. In that world, things like secret management were just less important. Does it matter that you have my database credential if you’re not on my network?”
Other new tools help detect if secure data is being sent and stored where it doesn’t belong. UpGuard, known for its frequent role in detecting leaks tied to data stored on insecure cloud machines, has released BreachSight which scours the internet for its clients’ exposed code, credentials, personally identifiable information, and other sensitive data.
“You might have this world-class team, but the project manager has an online Kanban board sitting out in the open that he’s using for notes, and it’s full of API keys. But nobody thought to look for it because the company believes everything’s internal,” co-founder and co-CEO Mike Baukes says. “It’s examples like that, which are things happening in the real world, that nobody’s had an answer for until now.”
Amazon has also offered a service called Amazon Macie, which uses machine learning to detect unusual access patterns in cloud storage and uploads of potentially sensitive data like access keys. Amazon also released open source software to prevent the accidental storing of passwords and keys to source code repositories, while other developers have offered similar tools to scrub credentials from existing code. According to Fast Company, those types of tools will be automatically provided as part of cloud computing contracts, just like standard seatbelts in a new car.
A Step-by-Step Guide to a Successful SIEM Deployment
SIEM (Security Information and Event Management) deployment based on firsthand experience implementing SIEM for a broad range of customers.
Discovery Phase - Laying the Groundwork
- Review the organizational security posture and the initial business case for SIEM. Then prioritize the goals of the SIEM implementation from the most critical to the optional—taking into account the tasks that must be performed in order to support the effort.
- Review in detail the organizational security policy to consider the intent behind the policy. Separate those policies from a priority standpoint. Determine what’s critical, what’s necessary for mandatory compliance and what policies are best practices to ensure a secure environment.
- Identify current controls that are auditing those policies to determine compliance level. Ideally, a SIEM implementation should not be the first time the organization identifies that its security policy or how it’s implemented isn’t working according to plan. The reality is that these deployments often expose gaps in security execution that must be remediated before those elements can be integrated into a daily alerting and reporting structure.
- Identify a smaller representative subset of the current policy and devices where SIEM can be applied and enough data can be gathered to determine what changes need to occur.
Pilot Phase - Beginning the Implementation
The primary goal of this phase is to determine which specific SIEM project goals can be implemented in order to establish initial ROI while creating a baseline operational model and run-book.
- The lessons learned from the discovery phase are used to implement a larger subset of technology.
- The assumptions developed during the discovery phase are tested in real time.
- The list of devices should be expanded to incorporate a wider set of technologies and numbers.
- The information developed from this phase is used to determine the final steps of controlled deployment and maturity phase.
Controlled Deployment Phase - Building Capacity
The primary goal of this phase is to develop a deployment workflow that enables the organization to build capacity as full deployment approaches. This phase also serves as the initial production test run and the completion of operational run-books necessary to manage a full deployment.
Maturity Phase - Continuing to Evolve
Significant work must be performed in order to mature the organization’s security posture and implement the finer points of the deployment. This phase never has an end point—since SIEM must continually evolve.
Cyber-Digital Task Force
The Department of Justice’s internal “Cyber-Digital Task Force,” created by Attorney General Jeff Sessions in February, will release its first-ever public report later this month at the Aspen Institute’s annual Security Forum, a department spokesperson told CyberScoop.
The report is expected to detail a series of security recommendations that the government should consider to protect future U.S. elections from a myriad of different threats, including foreign hacking attempts.
A statement by the DOJ previously explained that the Task Force will “prioritize its study of efforts to interfere with our elections; efforts to interfere with our critical infrastructure; the use of the Internet to spread violent ideologies and to recruit followers; the mass theft of corporate, governmental, and private information; the use of technology to avoid or frustrate law enforcement; and the mass exploitation of computers and other digital devices to attack American citizens and businesses.”
When Sessions launched the group earlier this year, he requested that an initial report be completed by June 30. The recommendations were submitted ahead of time, according to DOJ spokesperson Ian Prior. The answers are currently being reviewed ahead of publication.
The DOJ’s disclosure was made hours after the Democratic National Committee (DNC) issued a press release criticizing the department and Trump administration for missing various cybersecurity policy deadlines, including the June 30 submission. The agency contends that it in fact made the deadline, although the publication won’t occur for a few weeks. The Aspen Security Forum begins on July 18.
The creation of the Cybersecurity Task Force on Feb. 20 came less than a week after Special Counsel Robert Mueller indicted a group of Russian internet trolls for interfering in U.S. politics. The Russians allegedly ran an extensive social media campaign that worked to trick American voters in the run-up to the 2016 presidential election, the indictment claims.
Deputy Attorney General Rod Rosenstein is expected to make “an exclusive policy announcement” on July 19 at the Aspen Institute event.
Data Protection Officer- Consultants
Why do I need a Data Protection Officer?
While the desire to protect company, customer, and vendor information isn’t new, there are new laws that are requiring organizations to take a more active role in protecting their data. The EU recently passed the General Data Protection Regulation that requires certain businesses to have a Data Protection Officer. In order to comply with the rule, it has been estimated that nearly 28,000 DPOs will be needed by the end of 2018.
Specifically, the General Data Protection Regulation requires companies that process data with a public authority or that regularly monitor data subjects on a large scale to have a DPO and a plan in place to protect that data. It’s important to note that the rule not only effects companies that are biased in the EU, but also those that conduct business with its partner countries.
Because of the non-specific wording of the GDPR, one of the first steps that any company operating within the EU will need to take is to determine whether or not they are subject to the regulations in the law. It may be necessary to hire a security consultant on a short-term basis to determine this. Fortunately, CyberSecOp has plenty of experience in helping companies comply with EU law and IT security background that this position would require.
What is a Data Protection Officer?
In order to comply with the new regulation, a Data Protection Officer must have, “expert knowledge of data protection law and practices”. Additionally, the DPO must have a good understanding of the organizations' technical structure, organization, IT infrastructure, and technology.
It’s important to note that as long as an employee is capable of performing the basic functions of the role, there is no formal training requirement. This means that the job can be assigned to an existing employee. It is also permissible for an organization to hire an outside consultant or security firm to take on this role.
How will this affect my company?
Due to the massive penalties involved with ignoring the new GDPR, any company that meets the criteria and operates in at least some capacity in the EU will need to appoint a Data Protection Officer. For larger companies, this role is most likely already filled by a data security team. Small companies will most likely find it to be the most cost-effective to hire an outside company to handle its data security issues.
Mid-size companies, however, will likely struggle to come into compliance with this rule. Keeping a full-time Data Protection Officer on staff might prove to be cost prohibitive, but it’s also possible that contracting with an outside firm may also run up costs beyond a sustainable level. In many cases, the solution might be to find a professional with multiple skill sets who could act as the company’s Data Protection Officer while also performing other duties. CyberSecop have a team of security professionals dedicated to helping an organization in comping with GDPR and other data security frameworks.
Secure all networks, from the Internet?
In the coming years in 2019-2020, the active mobile users will cross the 5 billion mark globally, and add to this the number of tablet user will also increase. When we analyze these figures it is not difficult to estimate that there are more than 20 million IoT devices in the pipeline ready to hit the base by 2020. It means the above-given figures are all set to be part of the connected world.
All these devices mean lots of valuable data, and where there’s valuable data there are hackers trying to get access to it. Not only do we need to wrestle with new kinds of networks, many of them wireless, but we need to tackle the security of these networks while simultaneously tackling the massive scale of the problem.
Now imagine the kind of valuable data that will be churned out from these devices, and how it will be a gala time for the hackers to break into these devices and get access. No doubt we need to bring such device in our daily life, but the challenge is to get them all secured taking into account the massive breach in the line.
We asked vendors and resellers how they approach security of the WAN in this challenging environment
The internet is the network
The data center is no more the enter of the universe, but it is the Internet that new network that brings all the network closer to each other.
Mobile phone networks are rapidly being repurposed as a general-purpose data network over which voice calls are just one more application. Inside the telcos themselves, the core networking is already running over IP networks, and consumers are very comfortable with messaging applications that talk over IP networks instead of SMS. Devices in the field are adding LTE interfaces as a cheap and easy way to add networking capability to what were once disconnected devices.
“We have to rethink how we approach things,” Kopelke says. “We need to change our thinking from ‘How do I secure and protect the network?’ to ‘How do I secure and protect the data and applications?’”
Gavin Wilson, Asia-Pacific managing director at Cradlepoint “People expect to always be connected. Increasingly the connection is a mix of technologies, rather than a single layer-1 or layer-2 approach.” Instead of a loose collection of isolated technologies, the network is now an abstraction operating at a higher level, and there is no longer a functional difference between “the internet” of decades past and what all these modern mobile devices use to connect”.
The connected world and benefits
This ubiquitous networking is enabling associations to do things that basically weren’t conceivable previously. Without a system to send the information, gadgets in trucks or conveyed by field laborers would need to store information for later use. Presently they can stream a lot of information back to a server farm or straight into the cloud, and they can be inconsistent contact with different parts of the framework.
“The ability to get information out to remote people is a massive benefit, and, if a truck roll over on a delivery, an immediate duress notification can let others know the driver is in trouble,” says Michael Dyson, general manager at Advanced Mobile IT
“We also have digital signage that can be remotely updated,” Dyson says. “You can receive diagnostics from remote locations without having to send a technician out to the site and there are buses in New Zealand that can do on-board ticketing and have a GPS for accurate next-stop announcements.”
As it turned out to be consistently more steadily and reasonable, the requirement for the specialist like; satellite telephones, CB radios have dropped abruptly. These more seasoned technologies are turning into a fallback — as opposed to the essential strategy for building up correspondences. The generously higher transfer speed access, combined with the across the board accessibility of the supporting framework, influences the cost/to profit examination straightforward: you’d be distraught not to.
Security
Obviously, simply being associated isn’t sufficient. We likewise need to keep information and applications secure when they’re interfacing with an indistinguishable web from each content kiddie and solidified digital crime with a hunger for other individuals’ data.
“The traditional way to secure the WAN was using firewalls at each branch or backhauling branch traffic to a datacenter and use firewalls there to protect the traffic,” says Stree Naidu, vice president. Asia-Pacific and Japan for Cato Networks. “As long as we think about the firewall as a box that sits somewhere, that box defines the perimeter. But what if the perimeter was defined by a firewall that is everywhere? This is the notion of Firewall as a Service (FWaaS).”
Moving from the physical system of security that is as pervasive as the availability itself is it all about. “Systems that are secured from commencement is the name of the diversion. Rather than being a bit of hindsight or an extra, security in a world with no border implies heating it in from the start.
“It has to be about more than taking an appliance and virutalizing it,” says Zscaler’s Kopelke. “We say that’s just cloud-washing.”
Cato Networks’ Scree agrees. “The challenge most organizations face is how to extend enterprise-grade security to all their branches and mobile users globally,” he says. “Cloud networks with built-in network security can offer a way forward.”
“With users expecting a higher standard of service, these standalone appliances won’t cut it anymore,” says Dell EMC’s Elmarji. “You need to be able to provide full security on all connected devices, fast access to data, and 24/7 connectivity.”
While it’s still relatively early days for software-defined networks, it’s clear where the momentum is. Customers and resellers alike should be investigating how they can move to using software-based networking to create the secure, ubiquitous networks of the future
Corporate Information Security Steering Committee
Organizations are becoming increasingly aware that if they fail to implement successful security management processes, it could expose them to untenable risk.
The role of the corporate information security steering committee has become an essential tool in the quest for a coordinated corporate security strategy, for reducing duplication in security spending, taking control of complex infrastructures, and, ultimately, reducing security risk.
One of the first steps for many organizations has been to set up a common security team and embark on enterprise-wide information security programs. However, many of these teams have struggled to align corporate business objectives with strategic security investment.
META Group's research indicates that the majority of new security teams struggle to define and establish their corporate missions, scope, influence, and power bases. Furthermore, these security teams have poorly defined executive charters and operate without effective communications plans. The unfortunate result of such poor grounding is the temptation for newly established teams to immerse themselves in technology quests, searching for elusive enterprise-wide technical solutions.
In contrast, the most effective security organizations are those with clear responsibilities and well-defined processes based upon five primary organizational roles:
Leadership - this is the role of the chief information security officer who deals with both the day to day management of the security team as well as continuous communication of the importance and value of security measures
Analysis/design - these security analysts help information owners develop meaningful security policies as well as adequate security solutions
Security administration - these people look after the day to day administration of access rights, passwords, etc
Security operations - resources that continuously monitor the organization's security status and manage incident response procedures.
Awareness communication - resources that design and manage ongoing security awareness and training programs.
Executive custody and governance -represented by an information security committee
The role of the corporate security steering committee is to coordinate corporate security initiatives at the executive level and thus enable an organization to optimize spending, manage their infrastructure, and minimize security risk. Obtaining consensus and support for corporate-wide security initiatives is especially difficult in highly decentralized and multinational organizations with devolved authority and autonomy. In this type of organization, an executive governance body becomes essential.
Corporate information security steering committees (CISSC) must have a clear charter with a range of functions that should include:
Managing the development and executive acceptance of an enterprise security charter.
Assessing and accepting corporate-wide security policy (e.g., the corporate policy on security incident response, general behavioral approach). This function's primary objective is to ensure that business requirements are reflected in the security policy, thus ensuring that the procedure enables rather than restricts business operations.
Assessing any requests for policy exceptions from individual business units.
Assessing, accepting, and sponsoring corporate-wide security investment (e.g., identity infrastructure deployment, remote access infrastructure) and requests to be excluded from common investment.
Providing a forum for discussion and arbitration of any disputes or disagreements regarding common policy or investment issues.
Acting as custodian and governance body of the enterprise security program by ensuring visible executive support and monitoring progress and achievements. The role of a permanent governance structure reinforces the message that enterprise security becomes an ongoing, long-term initiative.
Assessing and approving the outsourcing of common security services and coordinating investment of inappropriate relationship management resources. As the lack of skilled resources increases the need to outsource operational services, executive due diligence, risk assessment, and ongoing effectiveness assessment must be coordinated through the steering committee.
Initiating ad hoc projects to investigate the advantages, disadvantages, risks, and costs of common security initiatives and advising the committee with appropriate recommendations.
Representing the executive (board of directors) or its nominated information governance body (e.g., an information executive board) in all corporate security matters. Reporting back to these forums on the activities and effectiveness of corporate security programs and investments.
Acting as custodian of corporate-wide strategic security processes (e.g., role analysis, data classification) by validating process ownership, responsibilities, and stakeholders.
Acting as the respondent to enterprise-level audit exceptions (i.e., those audit exceptions where a specific individual cannot be found to be responsible).
Coordinating and validating any external, security-related corporate communications plans and activities (e.g., in the event of a high-profile, publicized security breach).
Tracking major line-of-business IT initiatives to identify synergy opportunities or leverage security investment.
Governing trust relationships with major e-business partners.
It is essential that steering committee members can make decisions at meetings. This requires the active participation of senior executive business managers, or it must be a permanent subcommittee of an organizational information board. To prevent the committee from becoming an ineffective 'debating society' or forum for driving political agendas, the committee's scope, powers, and objectives should be documented and measured.
Typical members of an information security steering committee include all line of business managers, application owners, regional managers, IT managers, the IT director, the chief security officer, the corporate risk manager, and the chief internal auditor. A clear distinction must be made between the role of the CISSC (i.e., executive custody and governance) and the leadership role (i.e., day-to-day management of the security team) of the chief information security officer.
By developing the emerging role of the chief security officer (CSO) and the security team, enterprises can foster a holistic approach to information security - one that recognizes that policy, process, and communication are as important as technology.
Cloud to Streamline Security for Strategic Growth
As the technology director at Inspira Health Network, François Bodhuin and his staff have their work cut out for them, as they strive to support the organization’s strategic growth, stay on top of technology needs and keep patient data secure.
The New Jersey-based organization, in fact, is constantly looking to expand. “We are a medium-sized system, but we are very active in our expansion plans,” Bodhuin said, noting that the system now has more than 150 service locations in five counties. The health network is currently building a new hospital, adding a two- story patient tower to one of its existing hospitals, expanding its behavioral health program, renovating a satellite ER, recently opened a senior emergency department and purchased a regional medical transport company.
In addition, the Inspira technology department has developed an app to better serve all the patients that will flow into this continually growing health system. The app enables patients to request appointments, get directions to facilities, access a list of providers, view emergency department and urgent care wait times, pay bills and even participate in virtual visits.
So, it made perfect sense for Inspira to move its compliance management software to the cloud when FairWarning introduced a cloud-based managed shared services solution that works to ensure all data is secure by continually monitoring user activity and sending out alerts for any suspicious actions. After all, the health system had already moved a variety of systems to the cloud including its electronic health records, security information and event management (SIEM) and wound care solutions, and has experienced myriad benefits by doing so.
“The cloud saves costs; because you are getting a virtual server, the hardware itself costs less,” he said. In addition, when a managed services provider hosts a solution in the cloud, the healthcare organization does not incur on-boarding or ongoing training costs.
By hosting the compliance solution in the cloud under a managed services arrangement, Inspira will be positioned to:
Take advantage of a team of privacy and security experts. “The team concept to me is a key with managed services. We’re always being asked to work more efficiently. In this case, we will be able to really do that because we will have a team of experts that is performing the function,” Bodhuin said. “Because they’re experts, they know when a complaint is significant. They know when an alert is significant. They know when to ask for an investigation.” In addition, because these experts are well versed in the compliance solution, the learning curve that is typically associated with implementing a new solution is eliminated.
Reduce the need to search for IT staff. Hiring experienced, qualified IT staff is a challenge for all healthcare organizations. “In South Jersey, it is especially difficult to attract people to work in security and privacy. [With managed services], we don’t have to search for IT staff and we won’t have any onboarding costs. All that is built-in to our fees,” he said.
Maintain flexibility. With a managed solution in the cloud, it will be easy for Inspira to grow – as the organization does not need to add staff but can instead simply adjust the services agreement to meet evolving needs.
More readily deal with infrastructure challenges. With managed services, Inspira staff do not need to “worry about patching or managing the server,” he said. In addition, staff don’t need to be concerned with “upgrading the hardware, or the software . . . or worry about disaster recovery,” something that traditionally generates significant downtime, according to Bodhuin.
Leverage the experiences of many. Managed services providers work with a variety of organizations making it possible to “bring many best practices to the table,” which is difficult to do when hosting and maintaining systems internally, Bodhuin noted.
Save considerable time. “There's a lot of daily work that, all of a sudden, you don't have to do because it’s being done by the managed service. In privacy and security, we expect to regain about one to two hours a day for each analyst,” he said. “Now, they can focus their time on responding to issues that are reported to them. All that saved time can be allocated to another function.”
Doing managed services right
While Bodhuin expects to realize these benefits when moving the compliance software to the cloud, his past experience with managed services has provided a litany of lessons learned. More specifically, he knows that to successfully work with a managed services provider requires:
- Defining expectations explicitly. “You have to define what you trust them to do. You could let the managed service provider run the whole show if you wanted to, in certain functions,” or limit their scope to a defined set of functions, according to Bodhuin.
- Proactively managing the working relationship. “You really have to keep them on their toes. Make sure they deliver what they say they will deliver,” he advised. “So you really have to pay attention to your statement of work to ensure that you will get what you expect.”
- Treating the managed service provider as one of our own. “It’s really important that you make these people a part of your team. And if you do that, then you’ll get success. If you don’t do that, then there will be a lot instances where there are conflicts in your priorities,” Bodhuin said.
In the final analysis, with the expertise gained via a managed services arrangement, Bodhuin expects Inspira to save time, reduce costs while minimizing the organization’s overall risk profile. As such, Bodhuin can help the health system support its strategic growth goals. “The technology/security must be ‘a department of yes’, not a ‘department of no’. When you start saying no to people, you're going against the business itself and that can be a real problem,” he concluded.
Bypass Two-factor authentication - 2FA Bypass
A majority of users and companies are moving to Two-factor authentication (2FA) for enhancing the security of its data and systems. But contrary to popular belief, it cannot provide a fool-proof layer of security to online accounts since Kevin Mitnick at KnowBe4 has demonstrated that it is very easy to deceive this defensive measure.
KnowBe4 is the world’s leading security awareness training provider and simulated phishing firm with a massive customer base of 17,000 organizations across the world. Mitnick is the company’s chief hacking officer.
In his new exploit, he proved that 2FA is exploitable because hackers can spoof the 2FA requests by sending a fake login page to the user. This may lead to stealing of sensitive user data including username, password and session cookie.
The hacking technique can be seen in the video uploaded here:
The purpose of using 2FA is to add an extra layer of security by combining what an employee already has and what they know. This combination could be between username and password or a code that is sent to the user on the phone or an app.
To exploit the 2FA method of security, the victim is lured into visiting a typo-squatting domain such as LunkedIn.com in order to steal the required user data. Once the information is obtained, the hacker can easily access the actual website and capture session cookie. Once this is achieved, the hacker can remain logged in indefinitely. But this is reliant on accessing the 2FA authentication code once.
As per the CEO of KnowBe4Stu Sjouwerman, Kuba Gretzy, a white hat hacker, and friend of Mitnick, developed a tool for bypassing the 2FA authentication via social engineering techniques and this tool can be “weaponized” for just about any website.
“Two-factor authentication is intended to be an extra layer of security, but in this instance, we clearly see that you can’t rely on it alone to protect your organization,” added Sjouwerman.
The tool is called evilginx. The attack method is based upon proxying the user via the hacker’s system through a credentials phishing technique, which requires the use of a typo-squatting domain. The idea is to let the user give away his/her credentials so that the hacker could steal session cookie.
The phishing email is the core of the attack method. In this particular case, the phishing email is supposedly sent by LinkedIn to a member of the site indicating that somebody is trying to contact through the social network. The email looks authentic initially but if looked closely, it becomes evident that it is a fake email since the return address is incorrect. But, if the user falls for it and clicks on the “interested” button, the malware will soon be downloaded onto the device.
This is the stage when the victim is taken to the authentic LinkedIn website so as to enter login information, which the hacker required. The login information is recorded by the malware as well as the session cookie using the cookie, the attacker acquires direct access to the account and manages to avoid the 2FA phase of the signing-in process.
Watch The Demonstration Here