CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Healthcare Cyber Breaches and Statistics
Cyber breaches in the healthcare industry can have serious consequences, as they can compromise the confidentiality, integrity, and availability of sensitive patient information. These breaches can lead to financial loss, damage to reputation, and regulatory fines for the affected organizations. They can also have serious consequences for patients, including identity theft, financial loss, and harm to their physical and mental health.
According to a survey conducted by the Healthcare Information and Management Systems Society (HIMSS) in 2018, only 36% of healthcare organizations reported having a fully implemented cybersecurity program. The survey also found that only 37% of healthcare organizations had a formal incident response plan in place, and only 29% had regularly scheduled cybersecurity training for employees.
There have been several high-profile healthcare cyber breaches in recent years, including the 2017 WannaCry ransomware attack that affected the National Health Service in the UK and the 2018 breach of the health insurance company Anthem, which exposed the personal information of nearly 79 million individuals.
According to the US Department of Health and Human Services (HHS), the healthcare industry has consistently had the highest number of reported data breaches of any sector. In 2020, the HHS received reports of 1,363 breaches affecting a total of over 36 million individuals. The most common types of breaches reported were hacking/IT incidents (43.8%), unauthorized access/disclosure incidents (33.7%), and theft incidents (22.5%).
It is important for healthcare organizations to implement robust cybersecurity measures to protect patient information and prevent cyber breaches. This includes regularly updating and patching systems, training employees on cybersecurity best practices, and implementing strong passwords and access controls.
high-profile cyber breaches in the healthcare
There have been several high-profile cyber breaches in the healthcare industry in recent years. Some examples include:
In 2021, the health insurance company Premera Blue Cross announced a data breach that affected over 11 million individuals. The breach occurred in 2014, but was not discovered until 2015. The company discovered that hackers had gained access to its systems and had potentially accessed personal and medical information of its customers.
In 2020, the healthcare provider UnityPoint Health suffered a data breach that affected over 1.4 million individuals. The breach occurred when an employee fell victim to a phishing attack, which allowed hackers to gain access to the company's systems and potentially view or steal patient information.
In 2019, the healthcare provider Quest Diagnostics announced a data breach that affected nearly 12 million individuals. The breach occurred when an unauthorized third party gained access to the company's systems and potentially accessed patient information.
In 2018, the health insurance company Anthem suffered a data breach that affected nearly 79 million individuals. The breach occurred when hackers gained access to the company's systems and potentially accessed the personal and medical information of its customers.
It is important for healthcare organizations to implement robust cybersecurity measures to protect against cyber breaches and prevent the unauthorized access or disclosure of sensitive patient information.
healthcare HIPAA and cyber protection
The Health Insurance Portability and Accountability Act (HIPAA) is a US law that sets standards for protecting certain health information. HIPAA requires covered entities (such as healthcare providers, health plans, and healthcare clearinghouses) and their business associates to implement safeguards to protect the privacy and security of protected health information (PHI).
HIPAA requires covered entities to implement physical, technical, and administrative safeguards to protect PHI. These safeguards include:
Physical safeguards: measures to secure the physical environment where PHI is stored, such as locking doors and securing servers.
Technical safeguards: measures to protect against unauthorized access to PHI, such as firewalls, encryption, and access controls.
Administrative safeguards: policies and procedures to ensure the proper handling of PHI, such as training employees on HIPAA requirements and conducting risk assessments.
HIPAA also requires covered entities to report certain types of breaches of PHI to the Department of Health and Human Services (HHS) and, in some cases, to affected individuals.
It is important for covered entities and their business associates to comply with HIPAA requirements to protect the privacy and security of PHI and prevent cyber breaches. This includes implementing appropriate safeguards and regularly reviewing and updating their HIPAA compliance programs.
Cyber Security Breach Defense & Ransomware Risk Reduction
Cyber Security Breach Defense and Ransomware Risk Reduction by 98%, As ransomware evolves, so does CyberSecOp defense technologies.
Ransomware is the fastest growing attack-vector targeting all sorts of companies, institutions and organizations. No organization is immune to cyber attack. Cyber attackers can demand money from companies and institutions of all sizes and industries including nonprofit, enterprises and startups.
Ransomware Protection Solutions
Managed Detection & Respond - Managed advanced endpoint protection, this is basically monitoring an advanced antivirus, which have the following features: Antivius, Firewall, Host Inturstion Prevention, Auto Malware Containment, and Malicious URL filtering services.
SOC as a Service - Secure Operations Center 24/ monitoring- starts with a SIEM which correlated all logs into a central system, but SIEM can ingest data from multiple solution in the client environment, for example: Network Traffic, Intrusion Prevention, Cloud Assess Security Broker, Data Loss Prevention, Mircosoft Active Directory, Antivirus, Authentication System, Access Management, and other security logs.
Cyber Security Threat Hunting - Treat Hunting is not tied to any one a solution, and it is a service provided by a team utilizing multiple tools to understand if the client has been compromised, also call a compromised assessment, which may include the following but not limited to: Advanced Endpoint Protection (AEM), Security Information and Event Management (SIEM), Network Traffic, Intrusion Prevention, Cloud Assess Security Broker, Data Loss Prevention, Microsoft Active Directory, antivirus, Authentication System, Access Management, and others.
Data Loss Prevention (DLP) - Data loss prevention software (Common Terms data loss, data leak) detects potential data breaches/data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data. It is a standalone document, but its log data can be ingested by a SIEM correlation.
Preventing and Mitigating
Disable or remove remote services whenever possible; If not possible, use MFA/IP address restriction.
Do not allow remote access directly from the internet. Instead, enforce the use of remote access gateways along with a VPN that requires multi-factor authentication;
Require separate credentials for any remote access services; and administrative accounts.
Allow only VPN IP addresses to connect via RDP so that only trusted machines can connect;
Application whitelisting is critical to identify risks and unsanctioned application within your organization;
Network and domain segregation, isolation critical system from none critical system';
Deploy password lockout provisions to prevent brute-forcing attempts;
Implement awareness security training programs for employees;
Phishing simulation to identify employees who a susectiable to phishing emails;
Monthly external vulnerability testing;
Daily backup to a cloud provider, or take a copy of the backup offline Daily, Monthly, or Weekly depending on your business risk;
The best defense against ransomware is to outwit attackers by not being vulnerable to their threats in the first place. Ransomware penetrates organizations in multiple ways, so fighting it requires more than one product. CyberSecOp Ransomware Defense products provide ransomware protection from the network, DNS layer to email to the endpoint. As ransomware evolves, so does CyberSecOp defense technologies.
CyberSecOp is an ISO 27001 Certified Cyber Security Consulting Firm
CyberSecOp is proud ISO 27001 Certified Organization
The team at CyberSecOp is ISO/IEC 27001:2013 (ISO 27001) certified.
International Organization for Standardization (ISO) is an internationally recognized standard that ensures that firms such as CyberSecOp, meet best practices for information security management systems and vigorous risk-based framework approach.
We are committed to following a high-quality and consistent security management system. A-lign, an independent, third-party auditor, found CyberSecOp to have technical controls in place and formalized IT Security policies and procedures. A-lign is an ISO / IEC 27001 certification body accredited by the ANSI-ASQ National Accreditation Board (ANAB) to perform ISMS 27001 certifications. Therefore, through ISO 27001, we have developed and implemented processes and procedures in order to provide requirements for establishing, implementing, maintaining, and continually improving an information security management system. The entire certification leads us to the appropriate requirements for an Information Security Management System (ISMS) in our company — a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management processes.
Achieving the ISO 27001 certification is the result of a great amount of effort, dedication, and involvement from every member of the CyberSecOp team. We are constantly challenging ourselves to improve our service and provide the highest security and privacy standards to meet or exceed the needs and expectations of our customers.
Author: Carlos Neto
Information Security Officer
Top 14 Cyber Security Vendor Due Diligence Questions
What is a cybersecurity vendor due diligence questionnaire? Vendor cyber security due diligence questionnaire is a prewritten assessment gain visibility into supplier or vendor cybersecurity posture. Vendor cyber security due diligence questionnaire assist organizations with identify potential risks before onboarding vendors/suppliers.
CyberSecOp vendor management program supports multiple compliance requirement. The following four and other regulations are set forth by different regulatory bodies across the globe for various purposes, including the protection of financial, personal, and healthcare information.
- PCI DSS (The Payment Card Industry Data Security Standard). This is the information security standard for organizations handling branded credit cards.
- GDPR (The General Data Protection Regulation). This legal framework sets guidelines for the collection and processing of personal information for those living in the European Union (EU).
- HIPPA (Health Insurance Portability and Accountability Act of 1996). This U.S. legislation provides data privacy and security for safeguarding all medical information.
- OCC (The Office of the Comptroller of the Currency). This federal agency oversees the execution of laws for national banks, and functions to regulate and supervise banks in the United States.
Reputation Risk
Reputation risk refers to negative public opinion or customer perception that stems from irresponsible vendor practices. Unsecure vendor remote access can lead to a number of problems that may destroy customer relationships and harm your company's reputation, including:
- Customer complaints
- Dissatisfied customers
- Interactions inconsistent with company policies
- Security breaches resulting in the disclosure of customer information
- Violations of laws and regulations
Operational Risk
Operational risk results from internal breaches, processes, and system failures. Third-party vendors are increasing as an extension of operational risk since they are closely tied to operational processes and business practices. Operational risks may be caused by:
- Employee error
- Failure to adhere to internal policies
- Internal and external fraud or criminal activity
- System failures
Top 14 Cybersecurity Vendor Due Diligence Questionnaire
they have a security contact or chief information security officer in place? If a third party deploys dedicated resources to manage risks and safeguard its critical information, it shows they take their security posture with the utmost seriousness.
Do they have industry certification, or are they aligned with an industry framework such as NIST/ISO? While industry certification may not necessarily indicate the effectiveness of third-party security controls, it does provide additional assurance about the vendor's commitment to protecting their systems and customers' information.
Are penetration tests performed by a qualified third-party vendor? If so, how often are they performed and when was the last test performed? Ensuring your vendor has regularly scheduled penetration tests performed by a third party is essential in knowing how secure their environment is and where the weaknesses are so they can be secured before they’re exploited by an attacker.
Is there a formal information security program in place? A security program provides the framework for keeping a company at a desired security level by assessing the risks that are faced, deciding how those risks will be mitigated and planning for how to keep the program and security practices current.
Do they have a mature threat management and intelligence program in place? It's important to ascertain the effectiveness of their security controls. This can be done by reviewing independent security audit reports to assess the vendor's vulnerability management, secure software development processes and threat management programs, such as cyber intelligence.
Is there a formal logical access review process? Having regularly scheduled access reviews of users is essential in knowing who should have access to your system and who no longer needs access. Failures in logical access review procedures are the top reason for exceptions in SOC reports.
How has your vendor implemented the principle of least privilege? Role-based access privileges are vital in only allowing employees to have access to data they need while denying access to data they don’t need to perform their job.
How is data protected in transit between the vendor and the client as well as between the vendor and the end-user? How is data protected at rest on servers and backup media? Encryption of data in both in-transit and at-rest stages is extremely important to keeping it safe from unauthorized access.
How is retired media (hard drives, flash drives, CDs, documents, etc.) sanitized? Physical and electronic data should be disposed of in a secure manner when no longer needed to keep information from falling into the wrong hands. This has become more difficult with the adoption of public cloud services as data may move across multiple physical systems and reside on shared resources.
Are employees and contractors required to attend security training? Providing security awareness education to users of all systems is an important step in limiting user errors that could harm your IT infrastructure and information.
What due diligence is performed on contractors and vendors prior to and post contract? Completing due diligence over your vendor’s third party (your fourth party) is important especially if they have access to your data. You want to make sure they have a secure environment to help keep your information secure.
Do they have a good cyber score? It is prudent to ascertain exposure of an organization at the surface web, deep web and dark web to predict the likelihood of a potential breach due to their exposure. There are several organizations that provide cyber scoring for vendors and also allow you to benchmark them against similar vendors.
Is there a formal incident management program in place? Proper incident handling procedures allow situations to be analyzed and prioritized so that the next appropriate course of action can be taken to address the problem. Breach notification, a key component of incident management, is now included within multiple regulations with emphasis on vendor reporting.
Does your vendor describe technical prevention measures in place? Utilizing various security tools such as firewalls, anti-virus products and intrusion detection and prevention systems allow you to help secure your network from adversaries.
Strategic risk is created from failed business decisions, or the inability to implement strategies consistent with the organizational goals. Third-party vendors that are not aligned with your company’s practices may threaten operations or your ability to effectively execute business strategies. It may take some time to fully build and/or review a comprehensive cybersecurity questionnaire, but it could save you a lot of time and risk exposure in the future. It’s an invaluable questionnaire that provides a lot of insight.
Using Linux Won't Save You from Ransomware - Here's Why
"Ransomware attacks are becoming more targeted, sophisticated, and costly, even as the overall frequency of attacks remains consistent." (FBI, 2019)
Since early 2018, there has been a sharp spike in the cleverness, thoroughness, and precision of the security breaches we see in the ransomware landscape. Regardless of attack vector - whether it's from phishing, vishing, or the classic insider threat - once ransomware is on your computer, it's incredibly difficult to restore your files. It takes some serious intervention to stand a chance of recovering your business (or personal) data.
The easiest solution is to get the appropriate key and decryption tool, and use them together to unlock your files...but typically you only receive those resources in exchange for paying the ransom, and many companies can’t afford the ransom at its original price. By that time, there's a good chance you've taken a catastrophic financial blow. From hospitals, to insurance companies, to banks, there are plenty of highly valuable (and highly vulnerable) assets to be manipulated, and threat actors don’t hesitate to put lives at stake for the benefit of their wallets.
So how can we prevent these breaches? What is the key to staying safe from attackers?
The answer may be simpler than you think.
The three most impactful measures you can take to stay safe are as follows:
★ Quarantine
○ Take your computer off the network or wifi and reset your data by wiping the device entirely back to its factory settings (the way it came when you bought it) the moment you can confirm there has been a breach.
★ Have a backup
○ You can only take the first measure if you either don’t care at all about your data, or you have bothered to back it up so you have an unencrpted copy.
★ Get help negotiating your ransom down
○ If you need to pay the threat actor the ransom money to recover your data, there are many firms that can help you with this - don’t pay the full price of the ransom! Firms that can help with ransom negotiation and essential protections include CyberSecOp, which you can reach by using Our Contact Form.
So what’s so special about the threat of Linux-based malware? A Linux-based ransomware variant has the potential to take down any and every industry. Major cloud providers like AWS (Amazon Web Services), Oracle, and Microsoft base entire workloads on Linux; malware sweeping through those servers could bring down any company that uses a modernized cloud stack to host their sites and data.
And then there are hacktivists - hackers who hack to do activism for their cause (which can vary greatly in scope between organizations). Hacktivists have a history of using their ransomware attacks to make a point - whether it’s political or personal - and to incite fear in other companies or individuals who support the cause represented by the victim. While you might not think this presents a threat to you personally, or even to your business, the truth is that innovations in cyberattacks threaten us all. If the target were to have a Linux-based system, the hacktivist group targeting that individual would be devoted to finding a way to spread ransomware across Linux-based devices. When ransomware is evolved by perpetrators to this degree, we are likely to see major outages across all the cloud providers listed above, and it could cripple any business or personal account that is hosted therein.
To avoid such a catastrophic and monolithic problem, we should learn to govern our systems from a more ecosystem-centric approach, rather than depend on the classic signature-based antivirus alerts that have become standard. You may recognize Norton Antivirus alerts or even operating-system-based protection like Windows Defender presenting to you pop-ups about updating your signatures.
The truth is that we shouldn’t rely on the technical drivers of these updates, the people who hunt down and publish these known virus signatures, to keep us safe. We should be educating our employees, friends, and families, on the essentials of how to stay digitally secured and prevent breaches in the modern threat landscape. This concept is especially important as a mere tweak in the code of a virus and a quick recompilation of that code can cause the hash (or signature) of the virus to change, causing these famous signature-based antivirus softwares to completely miss the threat on your device.
A phenomenal example of how dangerous this variant-based workaround can be is what happened to the Colorado State Department of Transportation (CDOT) in early 2018.
“As CDOT’s Information Security group scrambled to contain the spread and impact of SamSam’s first wave, their efforts were quickly undermined by another variant of the same ransomware strain that was spreading throughout many of the newly sanitized zones of their network.”[1] (Richard Horne for the SANS Institute)
In an interview with the Denver Post, Brandi Simmons, a spokeswoman for the state's Office of Information Technology said, “The variant of SamSam ransomware just keeps changing. The tools we have in place didn't work. It's ahead of our tools.” The tools in question were signature-tracking antivirus software, like what many of us use on our home computers. In the end, Colorado's Office of Information Technology, the Colorado National Guard, and the FBI all had to collaborate to contain this threat, and by the time they had, over 2,000 computers running Windows and McAfee security software had been taken offline.
In conclusion, it seems inevitable that we will see Linux systems fall prey to the same types of ransomware we currently battle; it’s only a matter of time. Make sure you’re safe and you know how to protect your data: maintain a backup of all your files, be ready to quarantine in the event of a breach, and remember not to panic. We are here to help.
Sources:
https://www.sans.org/reading-room/whitepapers/tools/strings-me-linux-ransomware-39870
https://www.darkreading.com/attacks-breaches/second-ransomware-round-hits-colorado-dot/d/d-id/1331197
Authored by Alison Stuart
Pandemic & Post Pandemic Cyber Security Remote Workforce
The current pandemic gives cloud computing a push forward; our clients are taking advantage of CyberSecOp Alliance resilient cloud-based digital infrastructure for businesses of every size to protect their data. We have noticed 58% growth in our Cloud services, securing and protecting data while working remotely is one of the top concerns for most of our clients.
During the crisis, cyberattacks have increased worldwide, including against critical healthcare institutions, which have been the target of ransomware attacks. Private-sector data reveals a 350% surge in phishing websites since the start of the pandemic.
Our security professionals prepare for a new level of untrusted network activity and cyber attacks as remote working is expected to continue. What are the questions you should be asking, and what controls need to be in place?
Pandemic & Post Pandemic Cyber Security
While we are still very much on this transformation journey, we are working on the mindset of our clients to be prepared for quicker response to a crisis like COVID-19, by doing this we will increase business continuity and build-in security for all remote working processes. Removing legacy systems, introducing more automation, better identity and access management for remote systems, secure build for remote devices, extended security services such as Managed Detection and Response (MDR), IPS/IDS, Advanced Endpoint Protection, Application Firewall, DNS Filtering, Automated Virus Containment, and Filer Reputation Detection this will provide an additional layers of security for remote workforce, please see below for other recommendations.
Telecommuting is the only way of working for many
1. Adoption of virtual desktop will finally see an upswing:
With tele-working likely to become the norm, virtual desktops could become the security baseline for IT teams to enforce data management standards. Virtual desktops emulate a computer system so that IT can control access as such adding input/output devices as well as software and applications. This could become an important control point when remote workers are operating outside the safety of a corporate network.
To meet the stringent criteria of regulatory and corporate compliance regarding data security, many companies will see the adoption of virtual desktops as the go-to solution.
2. We will notice surge in adoption of decentralized cyber security:
Traditional cyber security controls dictate a centralized approach where data is consolidated from different sources to perform analysis and investigation. With swift digitization, security controls will shift to data sources, similar to the trend witnessed in IoT. We could start seeing a new wave of anti-virus, data loss protection, digital rights management and endpoint-based firewalls and other security controls gaining traction.
With millions of employees working from home, hackers’ focus has shifted from enterprise to remote working individuals. To handle the menace that exists in cyberspace, decentralized cyber security will rise where greater emphasis will be placed on data sources such as actual remote employees themselves.
3. Rise in bio metric way of authentication:
User access controls have largely revolved around one or two-factor authentication. These methods rely on “something you know (username)” and “something you have (password)” and given hackers’ interest in employees as the weak link to start a technical exploit, we will see cyber attacks directed towards individuals.
This means identity protection will be of priority and the best defense should focus on building authentication systems which focus on “who you are.” This would require advanced bio metric solutions such as fingerprint/thumbprint/hand print, retina, iris, voice, and facial recognition technologies.
With bio metrics, hackers’ attempt at impersonating you just got a lot harder than trying to break into passwords.
New processes will govern our way of work
1. Global privacy regulation and policies will require a re-look:
The current state of privacy regulations is designed around the enterprise network and building the proverbial wall to keep sensitive data out of prying eyes. With remote working concepts taking center stage, re-evaluation of these policies is needed to address the new cyber threats.
From a risk management perspective, global privacy policies will need to encapsulate standard operating procedures regarding BYOD, GDPR, NYDFS, CCPA, SHIELD Act compliance and state privacy laws.
Governance around companies and employees’ social media profiles would also have to be included as these platforms are frequently trolled by hackers as they carry out reconnaissance before launching a cyber attack.
2. Cloud will become more important than ever before:
The shift to cloud services offers employees, customers, suppliers, and everyone else across the ecosystem a seamless and frictionless access to data and applications. Remote access by various users would compound security challenges and presents many new potential attack vectors.
In the post-pandemic world, IT resources would shift towards data, particularly keeping data secure across cloud platforms.
3. Containerization technology will be extended beyond enterprise network to include endpoints:
IT architectures will extend containerization and zoning concepts to include not just systems, but also people, roles, and the level of sensitive data they possess. Containerization, thus, will be extended beyond enterprise networks to include endpoints such as remote worker machines and mobile devices.
This will facilitate cyber security teams to apply varied access controls and demarcate data storage to minimize risk of cyber intrusion and data breach.
Source: Cybersecurity Ventures
What is Cybersecurity Maturity Model Certification (CMMC)
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard intended for implementing cybersecurity across DoD contractors.
The CMMC has been in development for a number of years, but the first details on the framework were released in January 2020. The framework makes use of a “maturity” model, in which audits will be conducted by third-party assessors. Firms will be assigned a “level” that represents the cybersecurity protections, or maturity level they have demonstrated.
Breach Report and predicted loss by 2024
A recent study predicted that business losses due to cybercrime will exceed $4.5 trillion by 2024. The threat to the Defense Industrial Base (DIB)--the network of more than 300,000 businesses, organizations, and universities that research, engineer, develop, acquire, design, produce, deliver, sustain, and operate military weapons systems--is especially alarming due to current cyber warfare activities by cybercriminals and state-sponsored actors.
Security is a foundational component of acquisition
The Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S) recognizes that security is a foundational component of acquisition and that some contractors are trading security to benefit cost, schedule, and performance. It's estimated that the DoD supply chain consists of more than 300,000 businesses and organizations, all of which are targets. Most of these organizations are small to mid-size businesses, which are the most vulnerable to cyber-attacks. Based on over 100 Data Breach Investigation's CyberSecOp recognized that organizations between 100 -300 employees are prime victims for cyber criminals because of lack of security controls.
CMMC Model Structure
The goal of CMMC is to provide a framework for the improvement of cybersecurity in DIB sector organizations. CMMC currently defines 17 domains of technical capability, each with five levels of certification (L1 through L5) and specific practices. The DoD will require an organization to have CMMC Level 3 certification before it can receive Controlled Unclassified Information (CUI) in any domain.
CMMC Domains
CMMC Leveled Practices
The majority of the practices (110 of 171) originate from the safeguarding requirements and security requirements specified in FAR Clause 52.204-21 and DFARS Clause 252.204-7012. The practices fall into five levels:
Level 1 represents basic cyber hygiene, and focuses on the protection of federal contract information (FCI). It consists of practices that correspond only to the basic safeguarding requirements specified in 48 CFR 52.204-21 ("Basic Safeguarding of Covered Contractor Information Systems").
Level 2 is a transitional step in cybersecurity maturity progression to protect CUI. Level 2 consists of a subset of the security requirements specified in NIST SP 800-171, as well as practices from other standards and references.
Level 3 focuses on the protection of CUI. It encompasses all of the security requirements specified in NIST SP 800‑171, as well as additional practices from other standards and references.
At Level 4, the model begins to focus more on the proactive activities an organization can take to protect, detect, and respond to threats. These practices enhance the organization's ability to address and adapt to the changing tactics, techniques, and procedures (TTPs) used by advanced persistent threats (APT)s.
Level 5 focuses on the protection of CUI from APTs. The practices increase the depth and sophistication of cybersecurity capabilities.
CMMC Cyber Compliance Services
DOD has made the effort to simplify CMMC, but it is surely still complicated. CMMC is based on several other standards, including DFARS, CERT RMM, 800-171, AU ACSC Essential Eight, UK NCSC Cyber Essentials, ISO 27001, CIS Critical Security Controls, and the NIST Cyber Security Framework. Utilizing all the above information security standards make it very challenging for most DOD contractors to copy with CMMC. Get compliant with CyberSecOp CMMC Assessment, Security Program & Advisory Services.
Author: Kaushik Reddy
Cybersecurity Risks in a Pandemic: What you need to know
The COVID-19 pandemic has alerted many organizations to gaps in their information security infrastructure heretofore unrealized. Most of these deficiencies have been revealed as a direct outcome of the shift from a workforce-in-place physical environment centered around a fixed and determinable worksite location to a distributed, unstructured environment where most employees and individuals are working remotely.
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations.
The lack of a centralized workspace raises a multiplicity of information security concerns, including but not limited to the following:
1. Does the company have an established Work-From-Home (WFH) information security policy, and if not, how is remote worker security managed?
2. Are employees adequately trained to work remotely, and do they have the appropriate tools at their disposal to ensure the preservation of the security environment?
3. How does the organization manage mobile device and laptop security, including encryption?
4. Control and testing of the commercial VPN?
5. Does the organization maintain a comprehensive data loss protection policy?
6. How, if at all does the organization address data loss protection?
7. Does the organization have a breach response plan for mobile and remote WFH employees?
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations. Our skilled team of information security professionals can provide a comprehensive assessment of your information security framework and suggest remediation and complementary additions to your existing framework, as the case may be.
There are several things to consider if and when the time comes for firms to return to the office. CyberSecOp recommends:
Third-Party network risk assessment
Operational Responses to Security Incidents
Work from Home Security
Virtual Meeting Applications
Updates and Patches
A full virus scan on workstations returning to the office
Full Windows/Mac updates
Review Wi-Fi connections on returning devices: Some people may come back and still connect to Optimum Wi-Fi (This can be very risky)
Delete any accounts not for company use
Provisioning devices employees may have bought in haste (Hardening AV adding to the domain)
Mobile device management strategy for new mobiles, or devices that employees are using more
Pandemic Policy, Cybersecurity Policy Wireless policy
It is important for organizations to foresee possible consequences transitioning from working remotely to returning to the office. CyberSecOp can help facilitate this transition.
AUTHOR: Michael Young
So, What Exactly Is the Dark Web, Anyway?
The first time I heard the term ‘Dark Web’ was in the context of a case of misappropriated identity. A close relative of mine had begun receiving all sorts of communications from credit card companies and debt collectors concerning delinquencies that they were completely unfamiliar with. One even included an attempt at collecting back premises rent for an apartment in Dallas, Texas where my relative had never visited in their life. After spending months fighting off financial claims and trying to repair their credit history, my relative contracted a computer security professional to perform a forensic investigation of their home PCs. It was ultimately discovered that some or all of the data breach enabling the identity theft had been the outcome of a fairly sophisticated spear-phishing attack combined with the installation of a key logger agent. The forensics also revealed that much of their Personal Identifying Information had migrated to the Dark Web and was presently freely available to whomever-or whichever entity-might be interested.
Dark Web and how it functions
Dark Web, I thought. Huh. I’ve heard of the Dark Web but don’t know much about what it is or more specifically, how it functioned. Heretofore I’d (wrongly) believed it was composed of a bunch of gamers sharing logins to cloud gaming services along with the ever-present and always thriving market for pornography. My investigatory efforts yielded that the Dark Web is so, so much more, however; and I thought it was important to share my findings to clear up any popular misconceptions of which there is legion. Therefore, I’ve decided to put together a brief post that provides the nuts and bolts of what’s become an increasingly important cog in the global economy for ill-gotten bits and pieces of data and information. It turns out, the Dark Web wasn’t nearly as elemental as I’d initially suspected.
The Dark Web is a collection of thousands of websites that use anonymity tools to hide their IP addresses. While it's most famously been used for black market drug sales and even child pornography, the Dark Web also enables anonymous whistleblowing and protects users from surveillance and censorship. Readers will recall that the Dark Web played an intermediary role in WikiLeaks dissemination of certain confidential U.S. Department of Defense documents related to the conflicts in Iraq and Afghanistan.
Who created the Dark Web and how can it be assessed?
The majority of Dark Web sites use the anonymity software Tor with was created by the U.S. Department of Defense, though a smaller number also uses a similar tool called I2P. Both of those systems encrypt web traffic in layers and bounce it through randomly-chosen computers around the world, each of which removes a single layer of encryption before passing the data on to its next hop in the network. In theory, that prevents any spy—even one who controls one of those computers in the encrypted chain—from matching the traffic’s origin with its destination. In layman’s terms-traffic on the Dark Web is untraceable.
Though the Dark Web is most commonly associated with the sale of drugs, weapons, counterfeit documents, and child pornography, not everything on the Dark Web is quite so “dark.” One of the first high profile Dark Web sites was the Tor hidden service WikiLeaks created to accept leaks from anonymous sources. Even Facebook has launched a Dark Web site aimed at better catering to users who visit the site using Tor to evade surveillance and censorship. The Dark Web is also a vehicle for hackers to buy and sell personal information such as names, addresses, social security numbers, credit card information, etc. The more information they obtain from the unsuspecting victim, the higher the price.
Can Dark Web provide privacy
Just how completely Dark Web users can evade the surveillance of highly-resourced law enforcement and intelligence agencies, however, remains an open question. The FBI and EUROPOL have both launched successful Dark Web investigations aimed at stopping human trafficking, identity theft, and drug smuggling, and in most cases, the agencies were able to identify the threat actor by setting up relays and scripts on websites they frequently visit. It's also possible that the agencies employed sophisticated DNS attacks on TOR servers or used other exploits; then again, it’s also possible they were able to rely on good old Human Intelligence-informants. Everyone seems to have a price.
So in summary, we know that the Dark Web exists, it’s a marketplace for all sorts of data and information exchange, not all of it legal or voluntarily disclosed. The best way to ensure you don’t wind up on the wrong side of information exchange? Secure your information systems, be very, very judicious in responding to emails and if you have any questions or concerns, contact a licensed information technology security professional. The stakes are high, and only getting higher.
Author: Rich Fiore
Moving to the cloud: Efficiency and Reduced Organizational Risk Posture
Moving to the cloud: A Study in Security, Efficiency & Reduced Organizational Risk Posture
A recent Gartner study indicates that cyber crimes are at an all-time high, up 30% year over year. This is and should be of tremendous concern to C-suite executives and boards of directors.
The root cause of cybercrimes varies; however, most organizations will experience vulnerabilities arising from technological gaps due to neglected software patching initiatives, outdated firmware, continued use of hardware beyond manufacturer ‘end of life’ standards, limited resources, limited budgets, multiple new compliances, and of course externalities such as the recent global pandemic.
In efforts to protect against threat actors while simultaneously acknowledging their companies’ limitations, more and more C-suite information security executives are proposing complete moves to cloud-based computing environments along with the ‘shared resource’ model characteristic thereof. This will help ensure information security integrity, reduce or eliminate the threat of bad actors wreaking havoc on the company’s information systems and will allow the organization to achieve its goals with some element of cost-efficiency. To ensure these systems are implemented in the most efficient manner possible, many concerns will turn to Managed Security Services Providers (MSSPs).
1. Lack of resources create an unintended risk appetite
Some specific security challenges organizations face in today’s operating environment, based on experience include: A lack of resources creates an unintended risk appetite leads to organizational dysfunction and job loss. Organizations need to provide their CISO with their own budget, independent of IT, and the CISO needs to report at the same level as the CIO with a direct line to the Board of Directors and should feel comfortable addressing any vulnerabilities that may arise, notwithstanding resource requirements to address them. Recently, we were tasked with performing a security assessment and reporting our results directly to the client’s Chief Information Officer. The Chief Information Officer, in turn, requested that we provide our findings simultaneously, at a joint meeting of the Board of Directors. The Chief Information Security Officer had previously briefed the board on the organization’s information security posture and had suggested that risk levels were at a minimum and that there were no vulnerabilities or deficiencies that could pose mission-critical faults; in this, the CISO had sought to ‘paper over’ problems that had not been budgeted for and instead treated with an ‘it’s your job, you fix it’ mentality, creating a lose-lose proposition. Our findings and report directly contravened what the Board had previously been told, and this led to the firm initiating a comprehensive systems audit which resulted in the dismissal of multiple information technology executives.
2. Cloud Security Competency, Efficiency, and Cost-Effectiveness. As the cloud computing environment becomes mainstream, organizations will realize the competitive benefit of having so many competitors offering similar services. This allows organizations to seek out the best technology and team while adhering to internal resource limits.
3. Application and Network Monitoring
This service is critical for identifying potential risks and attacks from internal and external threats and one of the single largest information security infrastructure areas of investment for companies today. CyberSecOp has seen a volumetric increase in requests for our Security Information and Event Management (SIEM), Managed Detection and Response (MDR), Data Loss Prevention (DLP), Security Operations Center (SOC) and Cloud Access Security Brokers (CASB) services over the last year, which dovetails with broader global market trends. With ransomware and data security breaches at an all-time high, organizations are looking to managed IT security and managed compliance services providers to bridge the resource gap.
4. Data Security Governance Framework
Organizations are utilizing the cloud to aid with compliance, reducing the upfront cost of buying all the necessary security solutions and related resources needed to get them configured and managed; indeed, the focus has switched to using cloud and shared resources provided by managed IT and managed security providers.
5. Enterprise Security Partners
Bringing on an Enterprise Partner enables companies to focus on those factors that promote business growth as opposed to focusing on back-end solutions and internal control structures. In turn, the Enterprise Partner (MSSP) is often able to provide its services at a substantially more cost-efficient and competency structure than if the company had attempted to replicate those services internally; examples of specific areas of favorability are hiring and staffing the function, keeping up with and implementing vulnerability management, leaner staffing levels, and overall cost efficiencies.
6. Authentication
Over the past year, we have seen a 70% increase in the adoption of multifactor authentication technologies, including but not limited to ‘password-lite’ cloud-based solutions capable of biometric authentication, geolocation fence authentication, anomaly detection, end-user based risk scoring, and evaluation. Partnering with an Enterprise Security Partner can ensure such technologies are rolled out across all organization information technology platforms in a coordinated and effective manner, with a minimum risk of non-adoption and systemic conflicts.
CyberSecOp provides proven Risk Management and Digital Transformation: As one of the most called on firms for security breach response services per Google Analytics, we have assisted with over 550 incident responses spanning 2019 and 2020. CyberSecOp helps organizations assess their cloud or on-premise environments and implement a security program that provides the safeguards needed in the cloud or on-premises. We also offer incident response and forensics teams to assist with containment, remediation, recovery from ransomware attacks, and other security breaches.
COVID-19 Prompts Increased Ransomware Attacks Against SMBs Healthcare Providers
With the inception of the COVID-19 pandemic, malicious actors are increasingly targeting small hospitals and health centers with ransomware attacks. This is likely because these organizations are more likely to pay the ransom to recover data, as they weigh the perceived cost/benefit to strengthening their IT infrastructure security, or moving part or all of their IT operations to cloud-based solutions.
Cybercriminals tend to specifically target direct patient care facilities such as hospitals, healthcare centers, medical practices and health and wellness centers; although their efforts are certainly not confined to the above-referenced provider classes. The average ransomware demand is in the neighborhood of $60,000; however, simply paying the ransom in no way guarantees that the attacker will remit the decryption key; in fact, quite the opposite may occur; paying a ransom may encourage the attacker to maintain the leverage they enjoy over the target.
The ultimate consequences of ransomware attacks can and often are quite severe, ranging from continued involuntary exploitation of the attacker/victim relationship, to business closure. In some cases, class action lawsuits (dependent on the attack vector and information yield).
As more organizations move employees to work from home, remote staff make it increasingly difficult for IT teams to police computer systems and prevent cyber-attacks. Attackers now have far more access points and endpoints to probe or exploit, with little to no security oversight.
Here at CyberSecOp, we have formulated several countermeasures that healthcare employers should employ to minimize the risk of their networks being penetrated and secure their sensitive information.
Add data storage: After backing up data, the next step is to store data offline, on a different network, or a cloud-based environment.
Maintain a strong information encryption policy: Healthcare data must be encrypted at rest and transit with the highest standards available so that even if cybercriminals acquired it, they would not be able to read it.
Formulate and maintain an Incident Response Plan: Develop and test an incident response plan to help mitigate the impact of certain destructive malware attacks.
Track all data: Security personnel should closely monitor the company’s digital assets within the organization. This is of particular importance now as healthcare facilities’ attack surface expands and becomes more complex with some staff working remotely.
Establish and maintain firewalls: To harden networks and connected equipment, healthcare facilities with devices running open services should place them behind the latest application firewalls. They should also implement proper change management and firewall reviews to ensure proper documentation and optimization of these devices.
Follow the trends: Be aware of current ransomware threats, attack trends, and make sure those trends are socialized and communicated throughout the organization. Awareness is key.
Remote Working And Online Safety Tips
1. Avoid Creating Easy or Common Passwords
Password123 is a big no-no. Hackers have become bolder and have been using password deciphering tools to infiltrate vulnerable accounts. Multi-factor authentication (discussed later in this list) will most likely prevent them from going further, but it is always recommended to create a password with a mix of symbols, numbers, capital letters, and a lengthy number of characters to make it harder to crack. Also, the more frequently you change a password, the better. We also recommend using different passwords for different accounts. If the same password is used for multiple accounts, it becomes easier for hackers to infiltrate multiple accounts.
2 Connect Only to Protected Private WiFi Networks or (VPN) Virtual Private Networks
Always use private, password-protected WiFi networks to connect remotely. Security experts consider signing in to sensitive office networks with public WiFi or unsecured network connections akin to “swimming in shark-infested waters”—it’s only a matter of time before you get bit. Experts recommend consulting a trusted IT provider about setting up a VPN that can minimize the risk to devices and data.
3. Unusual Phrasings in subject lines/body, misspellings, poor-quality images or bad grammar
Although corona-virus-related phishing schemes are currently at an all-time high, the good news is that they aren’t much different from past attempts. Paying extra attention to message details—capitalization, punctuation, paragraph structure, sloppy design/formatting, or any language that seems out of the norm, makes detecting fake ones easier.
4. Don’t download unfamiliar attachments or click on unfamiliar links
In the age of remote work, collaborative OneDrive, Google Docs, or general Cloud sharing is a common way to redirect others to a malicious website. If you aren’t expecting a specific file from a specific sender, don’t open any attachments in an unknown message. This applies to links as well. To check if a link is safe, hover your mouse over the link to confirm the target URL matches what’s written (on a desktop or laptop). For extra precaution, type out the website to avoid being unknowingly redirected.
5. Activate multi-factor authentication (MFA) on every account you can
Many phishing schemes try to get you to re-enter your password for common apps or social media accounts—all in hopes that hackers can steal your password. Using multi-factor authentication can mitigate this since MFA requires something you know (your password) with something you have (a unique code delivered via text message or email).
6. Confirm the sender's email address
It’s easy for a hacker to mimic someone’s display or contact name—always double-check to confirm what shows up with the actual email address the message was sent from to make sure the sender is who he or she is claiming to be.
7. Do not respond to email correspondence from any financial institution
This goes for any communications via email or phone. You will not be prompted to sign in to your account or receive a call from your financial institution asking for your PIN or other personal information. In fact, most updates are sent with a 'do-not reply' email handle. Most official communications from financial firms are usually sent via snail mail. To ensure you are in contact with an actual representative of the firm, call the number on the back of your card or the phone number provided on your financial statements.
We hope you find these tips helpful.
Safe remote working and browsing!
- The CyberSecOp Team
Board Oversight of Cybersecurity Risk
Why CISOs and Boards Should Work Together to Improve Cybersecurity
Corporate board members often ask management specific questions that stop short of demanding metrics, It is this lack of measurable criteria which often hinder the effectiveness of cyber-security efforts.
First and foremost, it is imperative for the board to appreciate the impact that information security can have on the business. Boards should treat security as a top business risk as well as a top business opportunity. Major security events can have a significant impact on revenue, brand, and can lead to catastrophic results.
Board oversight of cyber-security has increased over the years. Even board members without technical expertise have had to become rapidly acquainted with IT risk and security concepts. In recent years, frameworks and best practices have emerged to help boards get a grip on their organizations’ cyber-security posture.
Specific Areas of Focus:
Improved emergency response times and evacuation management with real-time tracking of personnel movements around your site.
Information related to how the organization manages cyber-security, security awareness, and the enterprise risk management (ERM) program.
Actively monitor workers within a zone, on local or remote sites.
Ensure blast zones have been cleared before explosives are detonated.
Monitor the movement of people to a muster area during an evacuation.
Ensure the security control room is aware of workers who are alone on remote sites.
Monitor personnel who remain within a high security area at the end of a working day or shift.
Breach Response Protocol
Corporate boards should receive regular reports from executives about the company’s cyber-security risks, management review processes, overall health, and readiness to respond to an incident. Best practices include quarterly reports from firm leaders and more frequent reporting if needed.
Company leaders should carry out incident response plan tabletop exercises annually at a minimum. Board members should expect reports on the test outcomes. Details about how the plan will be updated are based on the test results.
Third-Party Risk
Regulators are increasingly targeting third-party risk. Wide-reaching laws like GDPR, industry-specific regulations such as the New York Department of Financial Services (NYDFS) Cyber-security Regulation and NERC CIP-013 in the utilities industry, provide specific requirements for managing third-party risk.
User-Related Risk
Human error can expose an organization to a wide array of cyber-attacks.. Business leaders commonly state that employee negligence is the most common cause of data breaches. Phishing for example, was implicated in 32% of data breaches in 2018. In addition, poor password practices, connecting to public Wi-Fi from company devices, and sharing files that contain malware are all examples of employee errors that could translate into huge costs for any organization.
In terms of board qualifications, 41% of companies reported highlighting cybersecurity expertise as an area of focus for new board directors. But when it came to interactions with management, only 34% of organizations mentioned the frequency of board reports, with just 11% reporting briefing the board annually or quarterly.
Recommendations for Boards of Directors
Questions to ask:
Has responsibility for cyber-security been formally assigned at management level (e.g., CISO) and on the board itself (e.g., audit committee)?
Is the board getting regular briefings on the organization’s strategy regarding cyber-security risks and cyber resilience?
How engaged is the board in reviewing the organization’s cyber-risk management program and security-related investments?
How has the organization (i.e., management) fared in recent tabletop exercises or simulations? Are directors taking part in such activities?
Vinny La Rocca
CEO
CyberSecOp.com
How to Clean Malware From Your Website
Cyberthreats will continue to grow as technology and big data evolve. Whether the motive is to steal money and data or simply wreak havoc, cybercriminals often have a solid return on investment of their time when they attack unprotected and vulnerable websites. They target websites with software that has a malicious intention – also known as malware – and they aren’t slowing down anytime soon.
Malware can change the appearance of your website, files, and even alter your computer operating system entirely. Cybercriminals gain unauthorized access to these systems by exploiting vulnerabilities found in weak entry points within system software. In fact, malware can cause your website to be flagged and removed from search engines, ultimately resulting in loss of traffic, decreased trust from your consumers or visitors, and a potential negative impact on your bottom line.
The impacts of malware can often depend on the overall goal of the attacker. Cyber-attacks can range from site defacements to a phishing email, and each has a different agenda. For example, a website defacement can be thought of as online graffiti, and the intention could simply be to make a statement of some kind. If you have an online business or simply have an online presence, there is a good chance you could be faced with malware on your website. To help you prepare, we’ve provided the following simple steps on how to remove malware from your website.
How to Determine if Your Website Has Been Infected By Malware
Cleaning your website of malware first requires identifying whether the site has been infected. An infected website has the following characteristics:
● Slow loading pages, or slow downloads
● Advertisements that pop up on the page, and re-pop up or do not go away even after attempting to close them
● Changes in your website theme or general appearance
● Spam email flooding your inbox
● Website comments full of comment spam or advertisements
● Traffic redirection to other websites resulting in low site traffic on your own page
● Removal from the general search results on various search engines
How to Clean Your Website
Step 1: Back up your site content
Before starting the malware removal process – always make a backup of your website files and database. This will allow you to restore your website if anything goes awry during the malware removal process such as file corruption. Look for a backup in your file manager or in a local drive as this may come in handy to replace files damaged by malware.
Step 2: Identify the malware
Use the file manager within your web hosting account or download an FTP manager to download and review your website files. This could be a time-consuming process depending on how many pages make up your website, but it’s a critically important step. When you do find files that look suspicious, review the code within the files for clues such as eval, base64, fromCharcode, gzinflate, shell_exec or error_reporting().
Step 3: Replace damaged files
Once malware has been successfully removed by restoring the file from a backup or completely removing the malicious file, try loading your website to ensure you are able to successfully view the content on the page. If your defacement is still visible or you have visible scripting errors on your page you must keep looking for the malware affecting your site. As a best practice, keep a current copy of the clean website files and database as well. This should be kept offsite in the event your website is re-infected.
Step 4: Enhance your website defense mechanisms
Removing malware and replacing all of your files can only do so much. If you don’t practice and implement proper cybersecurity protocols, such as keeping your software up-to-date and backing up your content, you’re leaving your online assets vulnerable to another cyber-attack. As a best practice, you should aim to improve your cyber defenses by implementing a web application firewall (WAF) to block cyber threats before they ever hit your website. In addition, it’s recommended to use a website scanner that can automatically detect and remediate malware and other threats as they happen.
Step 5: Protect your online accounts
It’s important to always use strong passwords for every account. Never write your passwords in a notebook or keep them in a spreadsheet online for someone to find. Always use a strong password that includes numbers, letters, and special characters. However, even if you are the only one who knows your password you aren’t doing yourself any favors by using the same strong password over and over for each account. Using a password manager will save you the hassle of remembering a plethora of passwords to logging to your accounts.
Staying Safe from Malware in the Future
Maintaining a clean and malware-free website is fundamental to the success of any website. And, if the website in question is connected to a business, it could prevent you from potential legal action. Case in point - the recent Equifax and Capital One data breaches have both resulted in class action lawsuits against each company, and new data breaches continue to occur resulting in additional lawsuits.
The truth is, if you are running a website of any kind, you owe it to your visitors to have security measures in place. Just a few of the things you can do include, but are not limited to:
● Installing a web application firewall (WAF) to protect your website and web applications from harmful traffic (such as cybercriminals and bad bots), and other cyber threats
● Use a malware scanner to automatically check your website for malicious software and cyber threats that can harm your website
● Update your website often, and keep a clean backup of all data and files at all times, so that in the event of infection you can install the clean copy and get back online faster
● Use a password manager to securely manage the logins for all of your online accounts
Conclusion
Malware can be dangerous for any website, and removing it is vital for the safety and protection of both the website owner, and its visitors. Therefore, understanding what malware is and how to remove it is the first step towards ensuring a malware-free site. Hopefully, the above information has inspired you to keep an eye on your website and ensure your business is protected from cybercriminals.
Ransomware - SMEs Faces Greatest Risk - Attacks Grown 235%
Enterprises, beware. Threat actors are continuing to eye businesses for high returns on investment in Q1 2019, breaching infrastructure, exfiltrating or holding data hostage, and abusing weak credentials for continued, targeted monitoring. From a steadfast increase of pervasive Trojans, such as Emotet, to a resurgence of ransomware lodged against corporate targets, cybercriminals are going after organizations with a vengeance.
Ransomware attacks on business targets have seen a substantial increase in the first quarter of 2019, up by 195 percent since the fourth quarter of 2018, according to a recent Malwarebytes report.
Malwarebytes researchers analyzed the combined statistics and intel collected from its intelligence, research, and data science teams between January 1 and March 31, 2019. They also leveraged telemetry from both consumer and business products on PC, Mac, and mobile devices.
Overall, they found that business detection of ransomware attacks increased by more than 500 percent from the same time frame in 2018 with 336,634 detections.
SMEs face the greatest risk from attacks as overall business detections have grown 235%
“Zero day attacks are on the rise and estimated to be a daily occurrence by 2021. This is largely down to digitisation within organisations and there’s more pressure on developers to deliver software faster – leaving systems vulnerable. This problem is exacerbated by hackers becoming more sophisticated, enabling them to bypass defences more easily.
“IT teams often prioritise stopping a breach occurring at all, but in today’s cyber climate a successful breach is inevitable. The most important aspect of cyber security is that businesses prepare for the worst and have effective data recovery and backup systems in place. Zero day recovery makes sure critical systems are down for as little time as possible. It’s often true that real damage from these breaches doesn’t come from the attack itself, but the resultant downtime after a breach – the time taken to become fully operational dictates the financial and operational fallout on a business.”
Key takeaways
cryptomining seems to have gone the way of the dodo. Detections of consumer-focused Bitcoin miners have dropped significantly over the last year and even from last quarter, while business-focused miners have increased from the previous quarter, especially in the APAC region.
Adware in Macs and mobile devices was problematic.
While all Mac malware saw a more than 60 percent increase from Q4 2018 to Q1 2019, adware was particularly pervasive, clocking in at over 200 percent from the previous quarter. Mobile adware detections also trended upward, as supply chain attacks delivered malware pre-installed on mobile devices. However, overall adware detections were fewer in Q1 2019 than they were during the same time period last year.
Exploit authors developed some attention-grabbing techniques. A new Flash Player zero-day was discovered in Q1 and quickly implemented into popular exploit kits, including Underminer and Fallout EK, as well as a new exploit kit called Spelevor. In addition, a Chrome zeroday required users to take action, fully shutting down and restarting their browser in order to patch the vulnerability. Finally, the popular software WinRAR was being used to deliver payloads to users.
As attacks against businesses ramped up, user trust in businesses to protect their data reached a new low.
In a survey conducted by Malwarebytes in Q1 2019 of nearly 4,000 respondents, users expressed deep concerns about abuse, misuse, and theft of PII, especially from social media and search engine companies. In a new section of our Cybercrime Tactics and Techniques report, we examine how cybercriminals found success by exploiting infrastructure weaknesses, gaps in policy and regulation, and even corporate negligence to not only walk away with valuable data, but establish persistence within the network.
Businesses are still the prime target. Overall detections of threats to businesses have steadily risen, while consumer threats have dropped off. Business detections increased by about 7 percent from the previous quarter, while consumer detections declined by nearly 40 percent, resulting in an overall dip in malware volume of 35 percent quarter over quarter. Compared to Q1 2018, business detections have skyrocketed 235 percent, with consumer detections dropping 24 percent year over year. This reinforces the observed trend of cybercriminals focusing more on business targets today.
Emotet shows no signs of stopping. Emotet, the most fearsome and dangerous threat to businesses today, has made a total shift away from consumers, reinforcing the intent of its creators to focus on enterprise targets, except for a few outlier spikes. Detections of Trojans (Emotet’s parent category) on business endpoints increased more than 200 percent from the previous quarter, and almost 650 percent from the same time last year.
Ransomware is back to business.
Ransomware has made a tremendous comeback against business targets in Q1 2019, with an increase of 195 percent in detections from Q4 2018 to Q1 2019. In comparison to the same time last year, business detections of ransomware have seen an uptick of over 500 percent, thanks in large part to a massive attack by the Troldesh ransomware against US organizations in early Q1.
Consumer detections of ransomware died down. Meanwhile, ransomware consumer detections have continued to drop, despite activity by families such as GandCrab, which primarily targeted consumers over the last quarter as it switched to a ransomware-asa-service and began brute-forcing RDP to infiltrate systems. Consumer detections of ransomware decreased by 10 percent quarter over quarter, and by 33 percent year over year.
Ransomware Breach and Ransomware Prevention
Cyber-criminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, TeslaCrypt., RyUK and others. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks. CyberSecOp use AI to help organization protect their data, and provide ransomware Incident response and remediation services.
HOW DO I RESPOND TO RANSOMWARE?
Implement your security incident response and business continuity plan. It may take time for your organization’s IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your organization’s essential functions according to your business continuity plan. Organizations should maintain and regularly test backup plans, disaster recovery plans, and business continuity procedures.
Contact law enforcement immediately. We encourage you to contact a local FBI or USSS field office immediately to report a ransomware event and request assistance. Contact CyberSecOp Security Consulting Firm for ransomware incident response & digital forensic services.
There are serious risks to consider before paying the ransom. We do not encourage paying a ransom. We understand that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. As you contemplate this choice, consider the following risks:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.
• Some victims who paid the demand have reported being targeted again by cyber actors.
• After paying the originally demanded ransom, some victims have been asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
Ransomware Incident Response from CyberSecOp, the firm that provide ransomware protection, and ransomware ransom payment.
WHAT IS RANSOMWARE?
Ransomware is a type of malicious software cyber actors use to deny access to systems or data. The malicious cyber actor holds systems or data hostage until the ransom is paid. After the initial infection, the ransomware attempts to spread to shared storage drives and other accessible systems. If the demands are not met, the system or encrypted data remains unavailable, or data may be deleted.
HOW DO I PROTECT MY NETWORKS?
A commitment to cyber hygiene and best practices is critical to protecting your networks. Here are some questions you may want to ask of your organization to help prevent ransomware attacks:
1. Backups: Do we backup all critical information? Are the backups stored offline? Have we tested our ability to revert to backups during an incident?
2. Risk Analysis: Have we conducted a cybersecurity risk analysis of the organization?
3. Staff Training: Have we trained staff on cybersecurity best practices?
4. Vulnerability Patching: Have we implemented appropriate patching of known system vulnerabilities?
5. Application Whitelisting: Do we allow only approved programs to run on our networks?
6. Incident Response: Do we have an incident response plan and have we exercised it?
7. Business Continuity: Are we able to sustain business operations without access to certain systems? For how long? Have we tested this?
8. Penetration Testing: Have we attempted to hack into our own systems to test the security of our systems and our ability to defend against attacks?
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
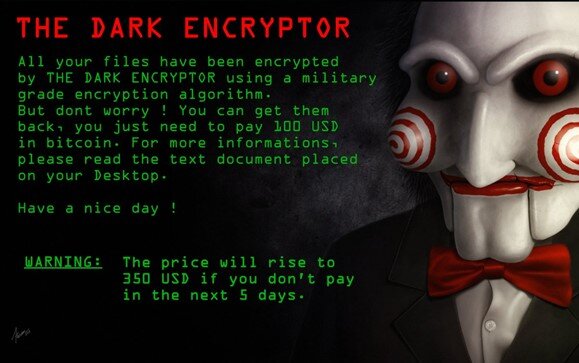
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
Ransomware?
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment.
Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails.
You will need and experience security consulting firm to guide you remediate the ransomware.
Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and contact CyberSecOp to request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. CyberSecOp does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key. CyberSecOp can negotiate the ransom for you, we have a 60% t rate of reducing the ransom.
• Paying could inadvertently encourage this criminal business model.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising.
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
What is Computer Security, Network Security and Cyber Security?
They have different responsibilities, but both plays apart in securing your organization
Network security is concerned about maintaining peace and calm within the walls of the castle. It focuses on maintaining the fortifications, of course, but its primary purpose is to guard against problems from within. A person concerned with network security will be focusing on protecting a company's internal information by monitoring employee and network behavior in several ways. They are the shire reeve responsible for keeping peace in the land.
IDs and passwords - making certain they are effective and updated frequently
Firewalls - keeping outside threats at bay
Internet access - monitoring the sites employees visit on the company's computers
Encryption - making certain that company information is useless to anyone outside the company
Backups - scheduling regular backups of company information in case of a hardware malfunction or successful outside threat
Scans - conducting regular virus and malware scans to detect any outside infection
Cyber security is much more concerned with threats from outside the castle. Where network security is worried about what is going on within the castle walls, cyber security is watching who is trying to pass through the gate or breach the parapets. The two areas have a lot of overlap, but their areas of concern are quite different. The cyber security specialist is the crusading knight defending the kingdom. Cyber security focuses on the barbarians at the gate and how the castle connects to the world around it.
Network protection - detecting and protecting against outside attempts to get into the network
Up-to-date information - staying informed on how attackers and hackers are improving their efforts
Intelligence - identifying the sources of outside attacks and protecting against them
Applications - monitoring the use of applications to avoid unintended breaches from within
What is Computer Security/Network Security
Computer security, or information technology security is the protection of computer systems from theft or damage to their hardware, software or electronic data, as well as from disruption or misdirection of the services they provide. information technology consulting as a field of activity focuses on advising organizations on how best to use information technology in achieving their business objectives, computer security is. usually managed by a network engineer or a network consultant.
What is an Network Consultant
a network consultant might be a network architect, a system administrator, a security specialist, or a number of different things. These consultants are responsible for designing, setting up, maintaining, and securing computer networks. Computer network architects gather extensive knowledge of an organization’s business plan in order to design and build data communication networks that can help the organization achieve its goals. This data communication network includes local area networks (LANs), wide area networks (WANs), and intranets.
Network Engineer Responsibilities: Maintaining and administering computer networks and related computing environments including systems software, applications software, hardware, and configurations. ... Protecting data, software, and hardware by coordinating, planning and implementing network security measures
What is Cyber Security
Cybersecurity is the protection of internet-connected systems, including hardware, software and data, from cyberattacks. In a computing context, security comprises cybersecurity and physical security -- both are used by enterprises to protect against unauthorized access to data centers and other computerized systems.
What is a cyber security consultant
A cyber security consultant performs a variety of roles within the cyber security field. They play both the attacker and the defender in computer systems, networks, and software programs. Seeing what weaknesses there are and figuring out how to strengthen systems to prevent hackers from exploiting vulnerabilities.
A security consultant is a catch-all cybersecurity expert. They assess cybersecurity risks, problems and solutions for different organizations and guide them in protecting and securing their physical capital and data, Earn a mid-level role as a security administrator, analyst, engineer or auditor.
Cyber Security Engineer Responsibilities: Planning, implementing, managing, monitoring and upgrading security measures for the protection of the organizations data, systems and networks. Troubleshooting security and network problems. Responding to all system and/or network security breaches.
Why You Need a Cybersecurity Management Program
Many organization’s cybersecurity teams (or information security teams as they used to be known) continue to struggle to communicate cybersecurity issues to senior leadership. Likewise, senior management also struggles to effectively articulate cybersecurity strategy to technical cybersecurity personnel. It is as though two parts of the same organization speak foreign languages to one another, and each party has a very limited, or no, knowledge of the other party’s language. However, it does not have to be like this.
Why so many organizations struggle with Cyber Security
Failure to communicate issues is most often revealed in grassroots cybersecurity initiatives that have evolved into corporate cybersecurity programs. Typically, this resulted from an enterprise in startup mode implementing solutions to address specific technical challenges. Unfortunately, many organizations continue to employ a similar approach to secure much larger and more complex environments against threats that outmatch the capabilities of their original solutions. No longer simply a technical solution, cybersecurity management has become a business function in today’s industry. As a business function, a greater level of integration with other business units requires a greater level of transparency and performance reporting. The evolution of grassroots cybersecurity programs rarely results in the kind of mature cybersecurity solutions that are aligned with, and address business needs. And why should they? The initial programs were designed to solve technical challenges, such as preventing virus outbreak or infection, stopping cyber attackers from compromising or stealing valuable information. Such initial cybersecurity efforts were neither designed as business functions nor defined in business terms.
CyberSecOp Comprehensive Security Program - Going beyond compliance
Cyber Security Program Key Success Factors
The following key success factors are common to many successful cybersecurity programs. The programs:
Support and drive strong governance attitudes and actions
Are designed, developed, and implemented in a similar way to other business functions
Adopt a standard framework approach, usable for an extended period of many years with little or no changes to that framework
Are measureable in terms of their effectiveness
Organizations and executives that drive successful cybersecurity programs do so in the same manner as other successful business initiatives. Executives succeed at this not because of industry pressure, but because each aims to improve their organization. Having identified the opportunity, executives evaluate whether the initiative poses additional risks to their organizations and decide whether to accept this additional risk or not. After accepting such risk, executive sponsors continue to evaluate initiatives toward implementation. Even when initiatives are operational, executives still employ strong governance methods, including internal audit teams, to manage and monitor the effectiveness and efficiency of these initiatives. This business approach has become institutionalized across most enterprise units with the exception of IT and cybersecurity. Key stakeholders in IT and cybersecurity often claim that cybersecurity management programs are too technical, only internal facing, or too complex, to properly develop and implement using this approach.
The truth is if these same IT and cybersecurity groups adopted a common framework and designed their cybersecurity management programs based on said framework, cybersecurity management would truly become just a standard business function in their enterprises. Unfortunately, the cybersecurity world does not agree on a standard cybersecurity framework across all countries, industries, and states. Analysis of the commonalities and differences between these standard frameworks show that it is possible to create a universal cybersecurity management framework to address all countries, industries, and states. Such a framework is not firmly associated with any particular cybersecurity standard and can be adapted during implementation to address any specific security standard that organizations using it wishes to follow. This paper introduces a cybersecurity management framework where it is apparent that a successful approach is not too technical, addresses both internal and external concerns, and is not overly complex to implement, operationalize, and manage over the long term.
CyberSecOp Cyber Security Management - Aligning businesses with security
Cybersecurity Management Framework
The design of the CyberSecOP cybersecurity management framework (CMF) assumes cybersecurity management is a business function.
The framework, as a business function, is comprised of three discrete pillars with each subsequent layer unfolding increasing levels of specificity as follows:
The Executive Management (Strategy) Pillar directs Governance and Planning initiatives that drive the framework forward to operation.
The Executive Management Pillar requires people to identify why cybersecurity is needed, consider the business issues, and then define, document, and publish the direction the required cybersecurity program will adopt.
The Operations Pillar that defines what the cybersecurity program must address to comply with the requirements specified in the strategy, what supporting functions are needed, and what level of reporting/ governance monitoring should be provided. These needs are supported through the security intelligence, IT and Cybersecurity Assurance and IT Risk Management operations sub-pillars.
The Operations Pillar requires definitions of documented operational standards, processes, procedures, and other collateral that specify what operators should do and how they should do it.
The Tactical (Technology) Pillar defines how required cybersecurity controls mandated in the Operations and Executive Management pillars will be applied to the systems, networks and applications used by the organization and how evidence will be provided to management that the security controls implemented actually address the specific requirements and that they perform their job as expected.
The security controls in the Tactical pillar, whether requiring technology or not, are responsible for securing all aspects of an enterprise computing environment, continuously monitoring the environment for security events, collecting and analyzing captured events, and reporting defined security metrics, some of which are provided to the SLT.
Addressing Cybersecurity Challenges
Although addressing cybersecurity challenges with just three pillars is perfectly possible, adopting and using it in that way is difficult and potentially open to error or misinterpretation. To minimize these issues, these macro-level pillars must be divided into more manageable chunks. The CyberSecOp LocPar subdivides its three macro pillars into seven discrete focus areas:
Executive Management: Key decisions and accountability required to drive the program
IT Risk Management: Reducing risk exposure to the organization to a level acceptable to the SLT and Board of Directors.
Cybersecurity Intelligence: Required to provide the cybersecurity and IT teams with appropriate information to achieve and surpass IT Risk Management goals.
IT and Cybersecurity Assurance: Required to provide evidence to management and especially the SLT that their investments in cybersecurity are delivering the benefits they expected.
Secure Network: Required to support secure, on demand access to information to authorized personnel no matter where it is located within, or external to, the organization.
Secure Systems: Required to provide controlled access to applications, data and devices according to the identity of the requesting party. This focus area also includes how data is protected, whether at rest, or in transit.
Secure Applications: Required to control access to data and other networks, systems and applications according to the identity of the requesting party. For internally developed applications, requirements extend to how the application was designed, developed and managed throughout the whole development lifecycle.
Summary
Development, implementation, and maintenance of a cybersecurity management program for an organization is no small undertaking. However, the overall value that organizations achieve through development and implementation of such programs includes reduced instances of successful cyber attacks. Moreover, a cybersecurity management program provides organizations with a means to reduce a successful attack’s impact on the bottom line due to its programmatic predefined approach for identifying and responding to cybersecurity incidents. Read more about cybersecurity management programs and CyberSecOp Cybersecurity Services at https://www.cybersecop.com/
Addressing Cyber Threats and Enabling Security in your Enterprise
Cybersecurity threats from hacktivists, criminals, and hostile nation states are enough to keep government officials, businesses, and consumers up at night. These attacks are growing in sophistication and frequency and pose serious threats to our national and economic security.
Everyone impacted by these vicious and dangerous acts must work together to help prevent, protect against, and effectively respond to them.
What are the biggest cyber threats CISOs are worried about in 2019? In today's age of breaches, staying ahead of cyber threats is becoming more critical than ever. Dive into how organizations are addressing the threat of cyber attacks, how they are measuring risk, and what they are doing about improving security from some of the top experts in the field.
Ransomware is still a large risk, affecting a large number of businesses
Data Loss and Data Breach based on information available on dark web, proves that organization can’t protect customers data.
Small business with no security program are at risk more than large organization.
All industry need to have some type of cyber regulations based on secure standards such as NIST or ISO.
What can business do, to enable a stronger security posture in their enterprise
Businesses adopt standalone cyber insurance policies as boards and executives wake up to cyber liability. As boards and executives experience and witness the impact of cyber attacks, including reduced earnings, operational disruption, and claims brought against directors and officers, businesses will turn to tailored enterprise cyber insurance policies, rather than relying on “silent” components in other policies. Adoption will spread beyond traditional buyers of cyber insurance, such as retail, financial, and healthcare sectors, to others vulnerable to cyber-related business disruption, including manufacturing, transportation, utility, and oil and gas.
As the physical and cyber worlds collide, chief risk officers take center stage to manage cyber as an enterprise risk. As sophisticated cyber attacks generate real-world consequences that impact business operations at increasing scale, C-suites will wake up to the enterprise nature of cyber risk. In 2018, expect CROs to have a seat at the cyber table, working closely with chief information security officers (CISOs) to help organizations understand the holistic impact of cyber risk on the business.
Regulatory spotlight widens and becomes more complex, provoking calls for harmonization. EU holds global companies to account over General Data Protection Regulation (GDPR) violation; big data aggregators come under scrutiny in the U.S. In 2018, regulators at the international, national and local levels will more strictly enforce existing cybersecurity regulations and introduce new regulations. Expect to see EU regulators holding major U.S. and global companies to account for GDPR violations. Across the Atlantic, big data organizations (aggregators and resellers) will come under scrutiny on how they are collecting, using, and securing data. Industry organizations will push back on regulators, calling for alignment of cyber regulations.
Criminals look to attack businesses embracing the Internet of Things, in particular targeting small to mid-sized businesses providing services to global organizations. In 2018, global organizations will need to consider the increased complexities when it comes to how businesses are using the IoT in relation to third-party risk management. The report predicts large companies will be brought down by an attack on a small vendor or contractor that targets the IoT, using it as a way into their network. This will serve as a wake-up call for large organizations to update their third-party risk management, and for small and mid-sized businesses to implement better security measures or risk losing business.
As passwords continue to be hacked, and attackers circumvent physical biometrics, multi-factor authentication becomes more important than ever before. Beyond passwords, companies are implementing new methods of authentication – from facial recognition to fingerprints. However, these technologies are still vulnerable and as such, the report anticipates that a new wave of companies will embrace multi-factor authentication to combat the assault on passwords and attacks targeting biometrics. This will require individuals to present several pieces of evidence to an authentication instrument. With the new need for multi-factor authentication, and consumer demand for unobtrusive layers of security, expect to see the implementation of behavioral biometrics.
Criminals will target transactions that use reward points as currency, spurring mainstream adoption of bug bounty programs: Companies beyond the technology, government, automotive and financial services sectors will introduce bug bounty platforms into their security programs. As criminals target transactions that use points as currency, businesses with loyalty, gift and rewards programs –such as airlines, retailers, and hospitality providers– will be the next wave of companies implementing bug bounty programs. As more organizations adopt the programs, they will require support from external experts to avoid introducing new risks with improperly configured programs.
Ransomware attackers get targeted; crypto currencies help ransomware industry flourish. In 2018, ransomware criminals will evolve their tactics. The reports predicts that attackers utilizing forms of benign malware—such as software designed to cause DDoS attacks or launch display ads on thousands of systems— will launch huge outbreaks of ransomware. While attackers will continue to launch scatter-gun-style attacks to disrupt as many systems as possible, the report predicts an increase in instances of attacks targeting specific companies and demanding ransomware payments proportional to the value of the encrypted assets. Crypto currencies will continue to support the flourishing ransomware industry overall, despite law enforcement becoming more advanced in their ability to trace attacks, for example through bitcoin wallets.
Insider risks plague organizations as they underestimate their severe vulnerability and liability while major attacks fly under the radar. In 2017, businesses under invested in proactive insider risk mitigation strategies, and 2018 will be no different. According to the report, a continued lack of security training and technical controls, coupled with the changing dynamics of the modern workforce, the full extent of cyber attacks and incidents caused by insiders will not become fully public. Many companies will continue to reactively responding to incidents behind closed doors and remain unaware of the true cost and impact of insider risk on the organization.
What is Cybersecurity Risk Management
Cyber Risk Management is the next evolution in enterprise technology risk and security for organizations that increasingly rely on digital processes to run their business. Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such doors and locks to protect homes and autos, vaults to protect money and precious jewels, and police, fire and security to protect against other physical risks.
What is cybersecurity risk management?
Rather than doors, locks and vaults, IT departments rely on a combination of strategies, technologies and user education to protect an enterprise against cybersecurity attacks that can compromise systems, steal data and other valuable company information, and damage an enterprise’s reputation. As the volume and severity of cyber attacks grow, the need for cybersecurity risk management grows with it.
Cybersecurity risk management takes the idea of real world risk management and applies it to the cyber world. It involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to make sure your organization is adequately protected.
Setting up your risk management system
Before setting up a cybersecurity risk management system, the enterprise needs to determine what assets it needs to protect and place a priority on. As the National Institute of Standards and Technology (NIST) points out in its Framework for Improving Critical Infrastructure Cybersecurity, there is no one-size-fits all solution. Different organizations have different technology infrastructures and different potential risks. Some organizations such as financial services firms and healthcare organizations, have regulatory concerns in addition to business concerns that need to be addressed in a cybersecurity risk management system. Cybersecurity should follow a layered approach, with additional protections for the most important assets, such as corporate and customer data. Remember that reputational harm from a breach can do more damage than the breach itself.
Risk management with CyberSecOp
Identity Services
Identity services help companies manage the explosion of digital identities and access to critical resources, both internal and cloud-based. In this age of digital transformation, the spheres of the individual’s life―as a professional, consumer, and private citizen―are interlinked in a complex digital structure, like a piece of fabric. The growing ability to piece together a digital picture of a person’s life and identity carries both risk and opportunity.
Wherever an organization is on its journey, we can help them achieve efficiencies, reduce risk, and evolve to support the changing needs of the digital business. With 20 years of identity management experience across the major industries, we offer field-tested accelerators and methods that are scalable and adaptive to each client’s specific set of business requirements.
Data Protection
Data Protection services help implement capabilities and technologies to protect sensitive data. As infrastructure and applications become more virtualized and adaptive, new cybersecurity gaps can be created as fast as old ones have been addressed, making the prevention of data breaches more difficult than ever. By prioritizing preventative and detective defenses around highly sensitive data, security teams can help reduce data loss and risk when attackers get past network, application, and infrastructure controls.
Leveraging these principles and an understanding of each client’s risk profile, CyberSecOp helps organizations design, implement, and manage capabilities to help better protect sensitive information across the end-to-end data lifecycle, and at an organization’s last line of defense.Application Security
In the era of digital transformation, application portfolios are becoming exponentially more diverse—and support a growing community of users. As the application “surface area” expands, so does cyber risk. Amid the change, one thing remains constant: applications are the lifeline of the business—and need to be a front line of cyber defense. It’s an important time for organizations to reexamine their approaches to application security.
Improving application security requires technical attention to individual applications, but also a broad framework across the application portfolio—from custom-developed to commercial off-the-shelf (COTS) applications and whether managed on-premise, on a mobile platform, in the cloud, or in a hybrid environment. It also requires the flexibility to support varying and often coexisting system methodology processes from waterfall, to agile, to DevOps in order to address application-related cyber risk at the pace of the organization’s digital evolution.
CyberSecOp’s application security services help organizations to design and implement security mechanisms across the system development methodology that can flex to your operational requirements to drive value through IT while also protecting your application portfolio against the changing cyber threat landscape.Infrastructure Security
Infrastructure Security services focus on developing advanced protection of core systems and devices. Today’s critical business drivers—the need to digitally transform, modernize the supply chain, enhance customer experience, increase agility, reduce costs, etc.—are driving a major shift in technology priorities. This shift includes increasing focus on cloud adoption, the Internet of Things (IoT), hybrid computing, software-defined networks (SDN), robotic process automation (RPA), blockchain, artificial intelligence, and more. The infrastructure supporting it has become highly virtualized and automated—and the traditional means of securing infrastructure fall short.
CyberSecOp helps organizations move toward a modernized, risk-focused agile defense approach. While the basic infrastructure domains—physical facilities, networks, systems and storage, and endpoints—that need to be protected remain the same, the means to secure them must evolve. By providing assessment, strategy, architecture, implementation, and operational management assistance across the four infrastructure domains, we help clients face our brave new world with a transformed, agile defense capability.