CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Understanding the UnitedHealth Data Breach: Lessons Learned and Cybersecurity Imperatives
In recent months, the healthcare industry has been rocked by a significant number of cybersecurity breaches, the most prolific of which was at UnitedHealth Group. This breach sheds light on the critical importance of robust cybersecurity measures in safeguarding sensitive patient data and ensuring the continuity of essential services.
Below we delve into the details of this breach and explore its broader implications for cybersecurity in the healthcare industry as a whole.
The breach at UnitedHealth's tech unit on February 12th was orchestrated by hackers who gained remote access to the network using stolen login credentials. This breach, attributed to the cybercriminal gang AlphV, aka BlackCat, underscored the vulnerabilities inherent in relying solely on passwords for authentication, particularly the absence of multi-factor authentication (MFA). The compromised Change Healthcare Citrix portal, lacking MFA, provided an open gateway for cybercriminals to infiltrate and encrypt the systems, leading to a ransom demand to restore access.
The aftermath of the breach highlighted the significant disruption to American healthcare. Change Healthcare was locked out of the essential systems impacting medical claims processing across the country. UnitedHealth Group has been diligently working with law enforcement agencies and cybersecurity firms, including Google, Microsoft, Cisco, and Amazon, to investigate the breach and secure affected systems.
However, the ransom payment made by UnitedHealth Group underscores the complex ethical and practical considerations surrounding ransomware attacks. While paying the ransom may, or may not truly ensure the decryption of systems and the restoration of services, it also incentivizes cybercriminals to continue their nefarious activities.
In response to the breach, UnitedHealth Group has taken proactive measures to support affected healthcare providers, providing over $6.5 billion in accelerated payments and no-interest, no-fee loans to mitigate the financial impact.
This breach serves as a stark reminder of the urgent need for healthcare organizations to prioritize cybersecurity and implement robust defenses against evolving cyber threats. CyberSecOp continues to provide award winning services, standing ready to assist organizations in mitigating risks, conducting comprehensive risk assessments, and implementing tailored cybersecurity strategies to safeguard sensitive data and ensure the integrity of critical systems.
As the healthcare industry grapples with the fallout of this breach, it is imperative for organizations to learn from these events and strengthen their cybersecurity posture to protect patient privacy and maintain the trust of stakeholders.
Together, we can work towards building a more resilient and secure healthcare ecosystem where patient data remains protected and essential services remain uninterrupted.
Cyber Incident Response: A Comprehensive Guide
In today's world, cyber attacks are a fact of life. Every day, organizations of all sizes are targeted by hackers, criminals, and other malicious actors. While no organization is immune to attack, there are steps that can be taken to minimize the risk of a successful attack and to mitigate the damage caused by an attack that does occur.
One of the most important steps is to have a comprehensive cyber incident response plan in place. A good incident response plan will outline the steps that will be taken to identify, contain, and mitigate a cyber attack. It will also identify the roles and responsibilities of key personnel during an incident.
CyberSecOp is a leading provider of cyber security services. Our Emergency Incident Response team stands ready to support your organization in identifying, mitigating and preventing security incidents. We have the experience and expertise to help you respond to any type of cyber attack, quickly and effectively.
Our team of certified security professionals will work with you to:
Identify the nature of the attack
Contain the attack and prevent further damage
Restore your systems and data
Investigate the attack and identify the root cause
Develop a plan to prevent future attacks
We understand that a cyber attack can be a disruptive and stressful event. Our team is here to help you through the process and to get your business back up and running as quickly as possible.
The Cyber Incident Response Process
The cyber incident response process can be broken down into the following steps:
Identify the attack. The first step is to identify that an attack has occurred. This may involve detecting suspicious activity, such as unusual logins or changes to network configurations.
Contain the attack. Once an attack has been identified, it is important to contain the attack as quickly as possible. This may involve isolating the affected systems or networks, or removing malicious code.
Mitigate the damage. Once the attack has been contained, it is important to mitigate the damage. This may involve restoring data from backups, or repairing damaged systems. It is also important to investigate the attack to determine how it occurred and to prevent future attacks.
Investigate the attack. Once the attack has been contained, it is important to investigate the attack to determine how it occurred and to prevent future attacks. This may involve gathering evidence, such as logs and network traffic, and interviewing affected employees.
Develop a plan to prevent future attacks. Once the attack has been investigated, it is important to develop a plan to prevent future attacks. This may involve implementing security controls, such as firewalls and intrusion detection systems, and training employees on security best practices.
Cyber Incident Response Resources
There are a number of resources available to help organizations create and implement a cyber incident response plan. Some of these resources include:
CyberSecOp can assist with the development of a comprehensive incident response program.
The National Institute of Standards and Technology (NIST) has developed a set of guidelines for creating a cyber incident response plan. These guidelines can be found on the NIST website.
The SANS Institute offers a number of resources on cyber incident response, including a checklist for creating a plan. These resources can be found on the SANS website.
The International Organization for Standardization (ISO) has developed a number of standards for information security, including one for incident response. These standards can be found on the ISO website.
Conclusion
Cyber incident response is an essential part of any organization's security posture. By having a comprehensive plan in place, organizations can minimize the damage caused by a cyber attack and quickly recover from an incident.
If you need help with your cyber incident response plan, please contact CyberSecOp today. We would be happy to help you develop a plan that meets your specific needs.
What is a Data Breach?
A data breach is the unauthorized access, use, disclosure, or theft of sensitive, confidential, or personal information. Data breaches can occur when cybercriminals gain access to a system or database and steal or expose the information stored there. They can also occur when information is accidentally or improperly disclosed by an individual or organization.
Data breaches can have serious consequences, including financial losses, reputational damage, and legal liabilities. They can also have serious impacts on individuals whose information is compromised, including identity theft and other forms of fraud.
There are several ways that data breaches can occur, including through cyber attacks, such as hacking and ransomware, and through physical means, such as the loss or theft of a device containing sensitive information. To prevent data breaches, it is important for individuals and organizations to implement strong security measures, such as using strong passwords, regularly updating software and operating systems, and implementing controls to prevent unauthorized access to sensitive information.
data breach laws
There are various laws that protect against data breaches and provide consequences for individuals and organizations that fail to protect sensitive information. These laws vary by jurisdiction, but some common examples include:
The General Data Protection Regulation (GDPR) is a data protection law that applies to organizations in the European Union (EU) and European Economic Area (EEA). It requires organizations to protect personal data and to report certain types of data breaches to authorities and individuals affected by the breach.
The Health Insurance Portability and Accountability Act (HIPAA) is a law that applies to the healthcare industry in the United States. It requires organizations that handle protected health information (PHI) to implement safeguards to protect the privacy and security of PHI.
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards that apply to organizations that handle payment card information. It requires organizations to implement measures to protect against data breaches and to report certain types of data breaches to authorities and card issuers.
In addition to these laws, many countries have their own data protection laws that apply to the collection, use, and storage of personal information. It is important for organizations to be aware of and comply with these laws to protect against data breaches and the potential consequences of such breaches.
Prevent Data Breach
There are several steps that individuals and organizations can take to prevent data breaches and protect sensitive information:
Use strong, unique passwords: Use strong, unique passwords for all accounts and devices, and regularly update them. Avoid using the same password for multiple accounts.
Enable two-factor authentication: Enable two-factor authentication, which requires the use of a second form of authentication in addition to a password, for all accounts and devices.
Keep software and operating systems up to date: Regularly update software and operating systems to ensure that the latest security patches are installed.
Use a firewall: Use a firewall to block incoming connections from known malicious sources.
Use antivirus software: Use antivirus software to identify and block malware, including ransomware.
Implement access controls: Implement controls to prevent unauthorized access to sensitive information, such as by requiring users to authenticate before accessing certain data or systems.
Regularly back up data: Regularly back up data and store it in a secure location to minimize the impact of a data breach.
Train employees: Train employees on the importance of data security and best practices for protecting sensitive information.
By implementing these measures, individuals and organizations can significantly reduce their risk of suffering a data breach and the potential consequences of such a breach.
Decrease Potential Data Breach, with Simple Security Control
Some senior management folks might find this strange, but you can significantly make your organization harder to breach. In fact, just a handful of defenses can do more to lower your cybersecurity risk than anything else. These include fighting social engineering and phishing better, patching the most likely to be attacked software far better, and requiring multi-factor authentication (MFA) for all logons.
Zero-day and information system protection
Because zero-day flaws usually refer to software that is widely in use, it’s generally considered good form if one experiences such an attack to share any available details with the rest of the world about how the attack appears to work — in much the same way you might hope a sick patient suffering from some unknown, highly infectious disease might nonetheless choose to help doctors diagnose how the infection could have been caught and spread. patch management is critical in protecting information technology systems.
Ransomware Breach and Criminals
The typical use case for ransomware is a shotgun approach type distribution campaign of dropping ransomware on people's machines, and then you charge them for getting their data or services back,” says Jeffery Walker, CISO at CyberSecOp. “Another use case is for covering tracks. These tools have the façade of ransomware: They would encrypt data, they would post a ransom note, and they would ask for money. They will even give you details on how to pay, but they're used to remove things from the endpoint while throwing off defenders into believing that the reason why that data was lost was because of a random hit by ransomware, but in some cases this is a cover up of a more bigger breach”
Vulnerabilities and Exploits
These are all vulnerabilities that could be exploited by cybercriminals bent on stealing personally identifiable information and protected health information – activity that could also play havoc disrupting healthcare delivery processes.
The study, based on network traffic data monitored by CyberSecOp over a six-month period, found the most prevalent method attackers use to hide command-and-control communications in healthcare networks was hidden HTTPS tunnels.
CyberSecOp compliance solutions deliver cost-effective data protection, data discovery, data classification and data loss prevention for data privacy and compliance.
Ransomware Breach and Ransomware Prevention
Cyber-criminals have turned to ransomware as the latest go-to tool for attacking and extorting businesses using a wide range of variants such as Dharma, Wallet, WannaCry, Cryptowall, Samas, Locky, TeslaCrypt., RyUK and others. The outbreak of WannaCry was one of the largest and worst ransomware campaigns ever. Traditional signature-based antivirus and threat detection methods have proven to be woefully ineffective against such attacks. CyberSecOp use AI to help organization protect their data, and provide ransomware Incident response and remediation services.
HOW DO I RESPOND TO RANSOMWARE?
Implement your security incident response and business continuity plan. It may take time for your organization’s IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your organization’s essential functions according to your business continuity plan. Organizations should maintain and regularly test backup plans, disaster recovery plans, and business continuity procedures.
Contact law enforcement immediately. We encourage you to contact a local FBI or USSS field office immediately to report a ransomware event and request assistance. Contact CyberSecOp Security Consulting Firm for ransomware incident response & digital forensic services.
There are serious risks to consider before paying the ransom. We do not encourage paying a ransom. We understand that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. As you contemplate this choice, consider the following risks:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.
• Some victims who paid the demand have reported being targeted again by cyber actors.
• After paying the originally demanded ransom, some victims have been asked to pay more to get the promised decryption key.
• Paying could inadvertently encourage this criminal business model.
Ransomware Incident Response from CyberSecOp, the firm that provide ransomware protection, and ransomware ransom payment.
WHAT IS RANSOMWARE?
Ransomware is a type of malicious software cyber actors use to deny access to systems or data. The malicious cyber actor holds systems or data hostage until the ransom is paid. After the initial infection, the ransomware attempts to spread to shared storage drives and other accessible systems. If the demands are not met, the system or encrypted data remains unavailable, or data may be deleted.
HOW DO I PROTECT MY NETWORKS?
A commitment to cyber hygiene and best practices is critical to protecting your networks. Here are some questions you may want to ask of your organization to help prevent ransomware attacks:
1. Backups: Do we backup all critical information? Are the backups stored offline? Have we tested our ability to revert to backups during an incident?
2. Risk Analysis: Have we conducted a cybersecurity risk analysis of the organization?
3. Staff Training: Have we trained staff on cybersecurity best practices?
4. Vulnerability Patching: Have we implemented appropriate patching of known system vulnerabilities?
5. Application Whitelisting: Do we allow only approved programs to run on our networks?
6. Incident Response: Do we have an incident response plan and have we exercised it?
7. Business Continuity: Are we able to sustain business operations without access to certain systems? For how long? Have we tested this?
8. Penetration Testing: Have we attempted to hack into our own systems to test the security of our systems and our ability to defend against attacks?
Protecting Your Networks from Ransomware
Ransomware is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016. This is a 300-percent increase over the approximately 1,000 attacks per day seen in 2015. There are very effective prevention and response actions that can significantly mitigate the risk posed to your organization.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections. Some ransomware variants display intimidating messages, such as:
“Your computer was used to visit websites with illegal content. To unlock your computer, you must pay a $100 fine.”
“You only have 96 hours to submit the payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.”
Ransomware?
Ransomware is a form of malware that targets your critical data and systems for the purpose of extortion. Ransomware is frequently
delivered through spearphishing emails. After the user has been locked out of the data or system, the cyber actor demands a ransom payment. After receiving payment, the cyber actor will purportedly provide an avenue to the victim to regain access to the system or data. Recent iterations target enterprise end users, making awareness and training a critical preventive measure.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organization by tricking a user to disclose a password or click on a virus-laden email attachment.
Remind employees to never click unsolicited links or open unsolicited attachments in emails. To improve workforce awareness, the internal security team may test the training of an organization’s workforce with simulated phishing emails.
You will need and experience security consulting firm to guide you remediate the ransomware.
Proactive Prevention is the Best Defense
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organization, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
The U.S. Government (USG) recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
Preventive Measures
• Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
• Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
• Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
• Configure firewalls to block access to known malicious IP addresses.
• Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
• Set anti-virus and anti-malware programs to conduct regular scans automatically.
• Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed; and those with a need for administrator accounts should only use them when necessary.
• Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
• Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
• Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
• Consider disabling Remote Desktop protocol (RDP) if it is not being used.
• Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
• Execute operating system environments or specific programs in a virtualized environment.
• Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units. Business Continuity Considerations
• Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
• Conduct an annual penetration test and vulnerability assessment.
• Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronization. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
What to Do If Infected with Ransomware
Should preventive measures fail, the USG recommends that organizations consider taking the following steps upon an infection with ransomware:
• Isolate the infected computer immediately. Infected systems should be removed from the network as soon as possible to prevent ransomware from attacking network or share drives.
• Isolate or power-off affected devices that have not yet been completely corrupted. This may afford more time to clean and recover data, contain damage, and prevent worsening conditions.
• Immediately secure backup data or systems by taking them offline. Ensure backups are free of malware.
• Contact law enforcement immediately. We strongly encourage you to contact a local field office of the Federal Bureau of Investigation (FBI) or U.S. Secret Service immediately upon discovery to report a ransomware event and contact CyberSecOp to request assistance.
• If available, collect and secure partial portions of the ransomed data that might exist.
• If possible, change all online account passwords and network passwords after removing the system from the network. Furthermore, change all system passwords once the malware is removed from the system.
• Delete Registry values and files to stop the program from loading.
Implement your security incident response and business continuity plan. Ideally, organizations will ensure they have appropriate backups, so their response to an attack will simply be to restore the data from a known clean backup. Having a data backup can eliminate the need to pay a ransom to recover data.
There are serious risks to consider before paying the ransom. CyberSecOp does not encourage paying a ransom to criminal actors. However, after systems have been compromised, whether to pay a ransom is a serious decision, requiring the evaluation of all options to protect shareholders, employees, and customers. Victims will want to evaluate the technical feasibility, timeliness, and cost of restarting systems from backup. Ransomware victims may also wish to consider the following factors:
• Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after paying a ransom.
• Some victims who paid the demand were targeted again by cyber actors.
• After paying the originally demanded ransom, some victims were asked to pay more to get the promised decryption key. CyberSecOp can negotiate the ransom for you, we have a 60% t rate of reducing the ransom.
• Paying could inadvertently encourage this criminal business model.
Ransomware Variants
Ransomware is a growing criminal activity involving numerous variants. Since 2012 when police locker ransomware variants first emerged, ransomware variants have become more sophisticated and destructive. Some variants encrypt not just the files on the infected device, but also the contents of shared or networked drives, externally attached storage media devices, and cloud storage services that are mapped to infected computers. These variants are considered destructive because they encrypt users’ and organizations’ files, and render those files useless until a ransom is paid.
Recent federal investigations by the FBI reveal that ransomware authors continue to improve ransomware code by using anonymizing services like “Tor” for end-to-end communication to infected systems and Bitcoin virtual currency to collect ransom payments. Currently, the top five ransomware variants targeting U.S. companies and individuals are CryptoWall, CTBLocker, TeslaCrypt, MSIL/Samas, and Locky. New ransomware variants are continually emerging.
CryptoWall
CryptoWall and its variants have been actively used to target U.S. victims since April 2014.
CryptoWall was the first ransomware variant that only accepted ransom payments in Bitcoin.
The ransom amounts associated with CryptoWall are typically between $200 and $10,000. Following the takedown of the CryptoLocker botnet, CryptoWall has become the most successful ransomware variant with victims all over the world. Between April 2014 and June 2015, IC3 received 992 CryptoWall-related complaints, with victims reporting losses totaling over $18 million. CryptoWall is primarily spread via spam email but also infects victims through drive-by downloads and malvertising.
CTB-Locker
CTB-Locker emerged in June 2014 and is one of the first ransomware variants to use Tor for its C2 infrastructure. CTB-Locker uses Tor exclusively for its C2 servers and only connects to the C2 after encrypting victims’ files. Additionally, unlike other ransomware variants that utilize the Tor network for some communication, the Tor components are embedded in the CTBLocker malware, making it more efficient and harder to detect. CTB-Locker is spread through drive-by downloads and spam emails.
TeslaCrypt
TeslaCrypt emerged in February 2015, initially targeting the video game community by encrypting gaming files. These files were targeted in addition to the files typically targeted by ransomware (documents, images, and database files). Once the data was encrypted, TeslaCrypt attempted to delete all Shadow Volume Copies and system restore points to prevent file recovery. TeslaCrypt was distributed through the Angler, Sweet Orange, and Nuclear exploit kits.
MSIL or Samas (SAMSAM)
MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application. SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.
Locky
In early 2016, a destructive ransomware variant, Locky, was observed infecting computers belonging to businesses globally, including those in the United States, New Zealand, Australia, Germany and the United Kingdom. Locky propagates through spam emails that include malicious Microsoft Office documents or compressed attachments (e.g., .rar, .zip) that were previously associated with banking Trojans such as Dridex and Pony. The malicious attachments contain macros or JavaScript files to download the Locky files. Recently, this ransomware has also been distributed using the Nuclear Exploit Kit.
Links to Other Types of Malware
Systems infected with ransomware are also often infected with other malware. In the case of
CryptoLocker, a user typically was infected by opening a malicious attachment from an email.
This malicious attachment contained Upatre, a downloader, which infected the user with GameOver Zeus. GameOver Zeus was a variant of the Zeus Trojan used to steal banking information and other types of data. After a system became infected with GameOver Zeus, Upatre would also download CryptoLocker. Finally, CryptoLocker encrypted files on the infected system and demanded a ransom payment.
The disruption operation against the GameOver Zeus botnet also affected CryptoLocker, demonstrating the close ties between ransomware and other types of malware. In June 2014,
an international law enforcement operation successfully weakened the infrastructure of both
GameOverZeus and CryptoLocker.
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
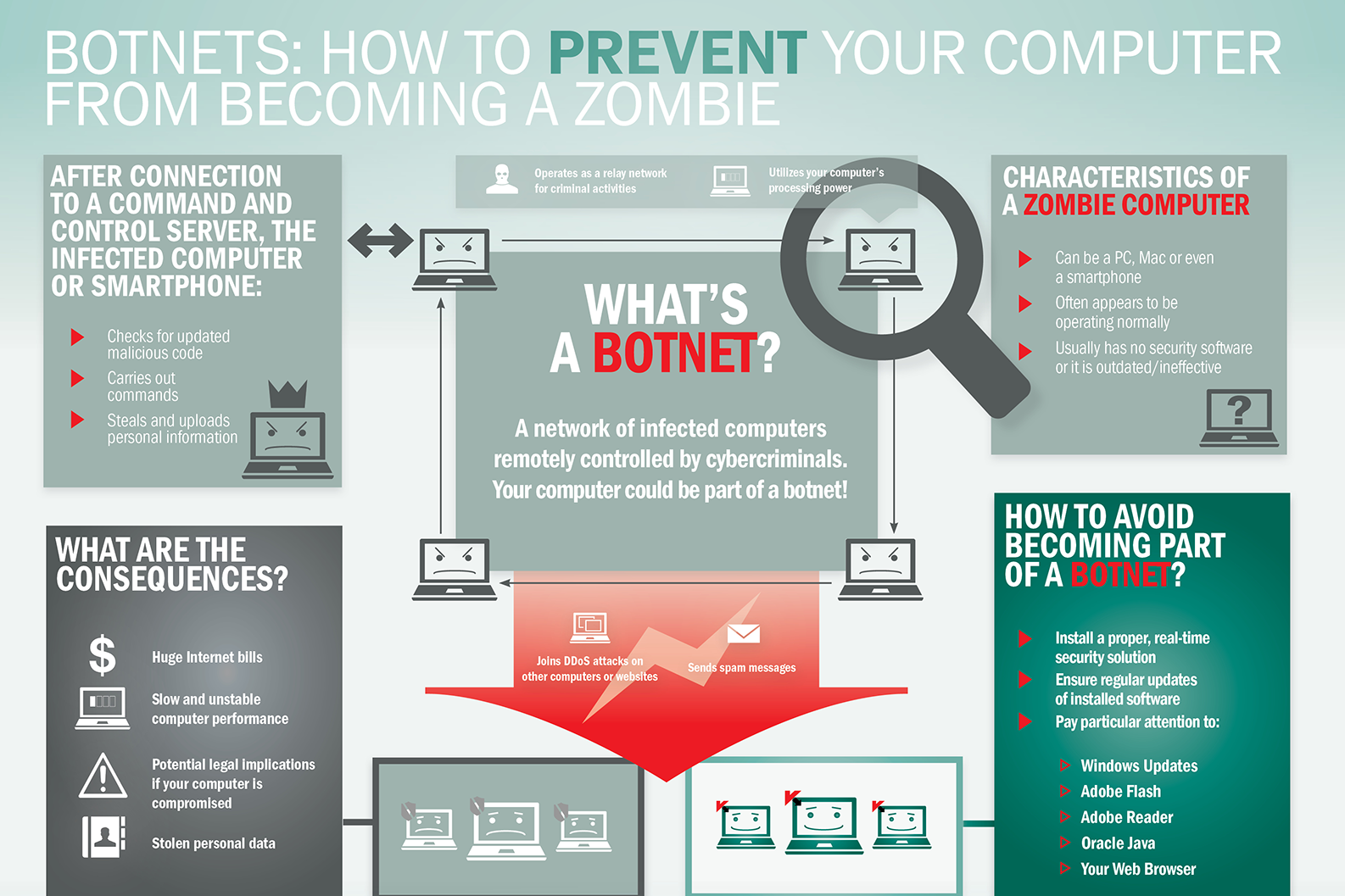
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
Ransomware campaign up around the world
A new email ransomware campaign is spreading around the world. Researchers at Fortinet say it’s a spam effort, meaning the messages are not targeted. Instead they are addressed generally, like “Dear customer.” The subject line in the email would be something like “Document number…”, “Your order number” or “Ticket number.” With the email is a malicious attachment that leads to the installation of malware. The initial targets are corporate mail servers used to forward this email. These have been found in Canada, the U.S. the United Kingdom and other countries.
The best defense against ransomware – or any email-delivered malware – is to watch out for it. Be cautious about unsolicited emails, especially those with attachments. And it’s vital you always have a separate backup of your data made it a way that can’t be infected, just in case you make a mistake.
Meanwhile McAfee reports some Canadian organizations have been victimized by a separate operation. A group security that researchers call Hidden Cobra, believed to be backed by North Korea, has been putting surveillance software on the systems of companies. The suspicion is the Canadian victims have been used as listening or data relay points. The malware that this campaign has installed has not stolen financial or sensitive data but appears to be there find out what’s on a computer, and be ready to launch further attacks.
Companies have to make sure their systems have the latest security patches. In addition, because the malware appears to be distributed through email, employees have to be reminded to be careful on what they click on.
For more on this see my story today on ITWorldCanada.com.
The U.S. National Security Agency has just suffered a black eye from an international standards body. According to a blog on Bitdefender, the International Organization of Standardization – known more commonly as ISO – rejected two new encryption algorithms suggested by the NSA to secure Internet of Things devices. The algorithms would scramble information on Internet-connected devices like home surveillance cameras and toys. But the NSA’s reputation for creating tools to hack into applications apparently give it a bad name at the ISO. One ISO delegate accused the NSA of telling half-truths and lies in its presentation.
If that allegation is accurate, it isn’t good. Internet of Things devices badly need better security. People and companies around the world buy tens of thousands of them a year. Insecure devices don’t improve security.
That’s it for Cyber Security Today. Subscribe on Apple Podcasts, Google Play, or add us to your Alexa Flash Briefing. Thanks for listening.
Cyber Security Developments
Cyber Security Is The Backbone Any Online Businesses – Here Are Some Quick Tips To Keep Yourself Informed About The Latest Threats Surrounding Your Business.
Cyber Security Developments
Within a standard nine to five working day, it’s said that there are almost two million data records lost or stolen. Cybercrime has become something of an epidemic in recent years – and it’s no exaggeration to say that everyone is at risk.
Hackers operate in an increasingly complex way and are happy to target small businesses and individuals, who are most likely to be vulnerable to attack. The nature of the threat changes as technology advances and so the only way to stay safe is to stay up to date.
But that’s easier said than done, right? How do you keep up to date with the latest cybersecurity developments?
Follow The News
When it comes to cyber security, ignorance is not bliss – it’s a recipe for disaster. It’s imperative that you identify and follow a news feed that you can trust. By doing so, you can keep on top of any fresh threats that have emerged, learn lessons from other cyber attacks and pick up the latest tips and advice from influencers and experts in this field.
News from this sector really shouldn’t be seen as the preserve of IT specialists – the scale and nature of the threat suggest that this should be of interest to everyone. There’s a burgeoning band of podcasts available on the subject for people who prefer to digest content in this way too.
Bring Up The ‘Security Question’
If you think that installing an anti-virus program is enough, then you’re mistaken. Don’t just presume that you’re safe because you have this because this is merely the first line of defense to root out attacks. By adopting a safety first mindset you can ensure that the way you handle your data is less risky.
Whether it’s securing your Wi-Fi network at home, managing and updating your passwords on a regular basis or the way you collect, collate and analyze data throughthe point of sale software at work, continually ask yourself ‘is this safe?’ Just as ignorance isn’t bliss, complacency could prove your undoing. Place ‘security’ high on the list of credentials to consider when buying new software or hardware, don’t just go for the cheapest option.
Training
Even the experts are constantly having to refresh their understanding of the threat posed by cyber attacks. It pays to search out training opportunities, especially if you’re a business. You are, after all, only as safe as the people operating your software and systems and you don’t want to put the security of your business in the hands of someone who is unsure about what they are doing. Individuals and businesses alike can find free learning materials on Cybrary to help plug any knowledge gaps they have.
It’s Good To Talk
Cyber attacks are incredibly common – but people don’t often enough talk about their experiences. Perhaps you’re afraid or embarrassed to have been caught out? There’s no need to be. In fact, talking with friends and colleagues could really help you to stay safe. Pass on tips about new apps, good software, neat tips and tricks and any new cyber attack tactics you have come across and you can help to do your own bit to combat the criminals.
By keeping up to speed with security news, refreshing your training, sharing tips and tricks and adopting a safety first attitude you’ll give yourself the best possible chance of staying on top of cyber security developments and, best of all, safe.
Cisco Switches vulnerable to remote hacking
Security researchers at Embedi have disclosed a critical vulnerability in Cisco IOS Software and Cisco IOS XE Software that could allow an unauthenticated, remote attacker to execute arbitrary code, take full control over the vulnerable network equipment and intercept traffic.
The stack-based buffer overflow vulnerability (CVE-2018-0171) resides due to improper validation of packet data in Smart Install Client, a plug-and-play configuration and image-management feature that helps administrators to deploy (client) network switches easily.
Embedi has published technical details and Proof-of-Concept (PoC) code after Cisco today released patch updates to address this remote code execution vulnerability, which has been given a base Common Vulnerability Scoring System (CVSS) score of 9.8 (critical).
Researchers found a total of 8.5 million devices with the vulnerable port open on the Internet, leaving approximately 250,000 unpatched devices open to hackers.
To exploit this vulnerability, an attacker needs to send a crafted Smart Install message to an affected device on TCP port 4786, which is opened by default.
"To be more precise, the buffer overflow takes place in the function smi_ibc_handle_ibd_init_discovery_msg" and "because the size of the data copied to a fixed-size buffer is not checked, the size and data are taken directly from the network packet and are controlled by an attacker," Cisco explain in its advisory.
The vulnerability can also result in a denial-of-service condition (watchdog crash) by triggering indefinite loop on the affected devices.
Researchers demonstrated the vulnerability at a conference in Hong Kong after reporting it to Cisco in May 2017.
Affected Hardware and Software:
The vulnerability was tested on Catalyst 4500 Supervisor Engines, Cisco Catalyst 3850 Series Switches, and Cisco Catalyst 2960 Series Switches devices, as well as all devices that fall into the Smart Install Client type are potentially vulnerable, including:
- Catalyst 4500 Supervisor Engines
- Catalyst 3850 Series
- Catalyst 3750 Series
- Catalyst 3650 Series
- Catalyst 3560 Series
- Catalyst 2960 Series
- Catalyst 2975 Series
- IE 2000
- IE 3000
- IE 3010
- IE 4000
- IE 4010
- IE 5000
- SM-ES2 SKUs
- SM-ES3 SKUs
- NME-16ES-1G-P
- SM-X-ES3 SKUs
Cisco fixed the vulnerability in all of its affected products on 28th March 2018, and Embedi published a blog post detailing the vulnerability on 29th March. So, administrators are highly recommended to install free software updates to address the issue as soon as possible.
Cyber Security, New York Fights Back to Prevent Financial System Take Down
New York is quietly working to prevent a major cyber attack that could bring down the financial system.
As hackers become more sophisticated and cyber attacks more routine, New York is on notice.
With a lack of leadership from the federal government, New York is one of the first states to implement new cyber regulations.
The state is quietly working to prevent a major cyber attack that could bring down Wall Street's financial system.
But even with the strictest cybersecurity regulations in the country, experts warn New York's efforts may still not be enough.
NEW YORK — Five months before the 9/11 attacks, US Secretary of Defense Donald Rumsfeld sent a memo to one of his advisers with an ominous message.
"Cyberwar," read the subject line.
"Please take a look at this article," Rumsfeld wrote, "and tell me what you think I ought to do about it. Thanks."
Attached was a 38-page paper, published seven months prior, analyzing the consequences of society's increasing dependence on the internet.
It was April 30, 2001. Optimistic investors and frenzied tech entrepreneurs were still on a high from the dot-com boom. The World Wide Web was spreading fast.
Once America's enemies got around to fully embracing the internet, the report predicted, it would be weaponized and turned against the homeland.
The internet would be to modern warfare what the airplane was to strategic bombers during World War I.
The paper's three authors — two PhD graduates and the founder of a cyber defense research center — imagined the damage a hostile foreign power could inflict on the US. They warned of enemies infecting computers with malicious code, and launching mass denial of service attacks that could bring down networks critical to the functioning of the American economy.
"[We] are concerned that US leadership, and other decision makers about Internet use, do not fully appreciate the potential consequences of the current situation," the report said. "We have built a network which has no concept whatsoever of national boundaries; in a war, every Internet site is directly on the front line. If we do not change course soon, we will pay a very high price for our lack of foresight."
The US government had a problem on its hands and it seemed a long ways from figuring out how to handle it.
More than 17 years later, that problem seems to have only gotten worse.
Follow the money
Willie Sutton, the notorious Brooklynite who spent his life in and out of prison, once told a reporter he robbed banks because that's where the money is. Computer hackers aren't so different.
In 2016, hackers attacked companies in the financial services sector more than companies in any other industry, according to IBM. Over 200 million financial records were breached that year, a 937% increase from 2015. And that's not including the incidents that were never made public.
As hackers become more sophisticated and cyber attacks more routine, New York is on notice. Home to the most valuable stock exchange on Earth, New York City is the financial capital of the world. When the market moves here, it moves everywhere.
So it was no surprise when in September 2016, Gov. Andrew Cuomo announced that the New York State Department of Financial Services (NYDFS) was gearing up to implement sweeping, first-of-their-kind cybersecurity regulations to protect the state's financial services industry — an unprecedented move no other state or federal agency had taken anywhere in the US.
Cybersecurity in New York's financial industry was previously governed by voluntary frameworks and suggested best practices. But the NYDFS introduced, for the first time, regulations that would be mandatory, including charging firms fines if they didn't comply.
Maria Vullo, the state's top financial regulator, told Business Insider that her No. 1 job is to protect New Yorkers.
"They're buying insurance. They're banking. They're engaging in financial transactions. And in each of those activities, they're providing their social security information, banking information, etc.," she said. "The companies that are obtaining that personal information from New Yorkers must protect it as much as possible because a breach of that information is of great consequence to the average New Yorker."
On March 1, the regulations turn a year old, although some of the rules are not yet in effect and will phase in overtime.
The NYDFS oversees close to 10,000 state-chartered banks, credit unions, insurance companies, mortgage loan servicers, and other financial institutions, in addition to 300,000 insurance licensees.
The combined assets of those organizations exceed $6 trillion, according to the NYDFS — and they're all in constant danger of being hacked.
Banks are vulnerable
In the summer of 2014, an American, two Israelis, and two co-conspirators breached a network server of JPMorgan Chase, the largest US bank.
They got hold of roughly 83 million customers' personal information, including names, addresses, phone numbers, and email addresses.
The hackers didn't steal any money from personal bank accounts, but that wasn't the point.
They wanted access to a massive trove of emails that they could use for a larger, separate money scam. In just three years, that operation netted the hackers more than $100 million.
The JPMorgan hack wasn't the end game. It was a piece of the puzzle.
The attack began with the simple theft of a JPMorgan employee's login credentials, which were located on a server that required just one password.
Most servers with sensitive information like a person's banking data require what's called multi-factor, or two-factor authentication.
But JPMorgan's security team had lapsed and failed to upgrade the server to include the dual password scheme, The New York Times reported at the time.
The attack, the breach, and the reputational damage that followed could have been avoided with tighter security. Instead, the hack went down as one of the largest thefts of customer data in US history.
"Banks are especially vulnerable," Matthew Waxman, a professor at Columbia Law School and co-chair of the Cybersecurity Center at the Columbia Data Science Institute, told Business Insider. "Disruption to the information systems on which banks rely could have shockwaves throughout the financial system, undermining public confidence in banking or knocking off line the ability to engage in commercial transactions."
That's the kind of catastrophic damage that worried the authors cited in Defense Secretary Rumsfeld's 2001 memo.
They weren't only concerned about stolen email addresses and social security numbers. They were worried about the fallout from such activity.
Banking works because consumers trust the system. But what if people lose trust?
Waiting until a catastrophe
News of impending cybersecurity regulations in New York in the fall of 2016 was both welcomed and shunned.
Some companies saw it as a chance to improve their own security standards while others complained of government overreach. Some were relieved to find they wouldn't have to make any adjustments to the way they operated. Others were overwhelmed by the heavy lifting they would have to do to comply.
How a company views the regulations depends in large part on its size. Bigger institutions with more cybersecurity professionals and more resources at their disposal tend to already have in place much of what the regulations require. Many smaller companies, which tend to be under-staffed and under-resourced, have a lot more work to do to catch up.
Jenny Cheng/Business Insider
The only additional thing Berkshire Bank has to do is sign off on its annual compliance form, which it sends to NYDFS to prove that it's doing everything it's supposed to be doing.
"We actually have to do nothing [new] from a compliance standpoint," the company's chief risk officer Gregory Lindenmuth told Business Insider.
While several cybersecurity consultants told Business Insider they acknowledge the NYDFS rules as a positive step in the right direction, they also point to a new law in Europe as a leading example of the role government has to play in protecting individuals' privacy rights and ensuring that companies secure consumers' personal information.
In 2016, the European parliament passed a law called the General Data Protection Regulation (GDPR) — landmark legislation that imposes millions of euros in fines on companies that do not adequately protect their customers' data.
Whereas the NYDFS regulations cover just one industry in one US state, the GDPR affects companies in all industries across all 28 member states of the European Union. Companies that do not report a data breach or fail to comply with the law more generally could be fined up to €20 million or 4% of its global revenue.
Matthew Waxman, the Columbia professor, says it's not surprising that the implementation of such a law remains far-fetched in the US.
"It's sometimes very difficult to get the government to take action against certain threats until a catastrophe takes place," Waxman said. "But that could change very suddenly if the banking system were knocked offline or another very major disruption to everyday life affected the lives and security of citizens on a massive scale."
But are the deterrents strong enough?
Data protection advocates calling for stricter cybersecurity regulations in the US are generally happy about the NYDFS rules.
For the first time, a state government is taking seriously the protection of consumer data, they say. It's giving companies in the financial sector an ultimatum: protect New Yorkers or face punishment.
"My big criticism of the regulations is there's no clear consequence for non-compliance," Thomas Boyden, the president of GRA Quantum and a cybersecurity expert who helps companies defend against cyber attacks, told Business Insider. "If companies don't feel like there's going to be any consequence for any action on their part, companies aren't going to take [the regulations] seriously."
In fact, for many companies, Boyden thinks "that's the default position."
Vullo, the head of the NYDFS, said she has the ability to fine companies that are not complying and is willing to exercise that authority, although how much that cost may be would depend case-by-case.
"I don't want this to be a punitive atmosphere, but obviously if institutions are not taking this seriously, then there will be consequences," she said. "But it's not the objective."
If anything, the objective is to make it clear that cyber threats are real and that New Yorkers and the companies that maintain their personal information are facing higher risks of attack.
Cybersecurity affects everyone, and Vullo said she hopes the regulations will help companies prioritize it.
"Everyone is part of our cybersecurity team," Theresa Pratt, the chief information security officer at Market Street Trust, a private trust company in New York, told Business Insider. "It doesn't matter what myself or my colleagues do from a technical perspective. If I have one user who clicks a bad link or answers a phisher's question over the phone, it's all for naught."
New York leading the way
The new rules have far-reaching implications beyond New York. A business in the state that has a parent company based in Germany, for example, still has to comply with the regulations.
This leaves some organizations in the precarious position of having to either restructure company-wide cybersecurity practices or build an entirely new and unique security apparatus that is specific to its New York offices.
"I do think that because of the scope of some of these regulations, they're kind of blurring the lines between countries and continents. I think we're going to see more and more of this," GreyCastle Security CEO Reg Harnish told Business Insider. The New York-based consulting firm is helping companies comply with the new regulations.
In the absence of leadership from the federal government on certain issues related to cybersecurity and data protection, states like New York are beginning to fill the void. Several cybersecurity experts told Business Insider that the NYDFS regulations could become a model for other industries or even policies at the national level.
Last year, at least 42 states introduced more than 240 bills or resolutions related to various cybersecurity issues, according to the National Conference of State Legislatures. And since the NYDFS rules took effect, financial regulators in Colorado and Vermont have followed New York's lead with cybersecurity regulations of their own.
Indeed, cyber experts have come a long way in better understanding the threats we face since Rumsfeld's dire cyberwar memo in 2001. But 17 years on, the former secretary of defense's concerns still seem as relevant as ever.
Perhaps the memo was a prescient warning — a warning that fell on deaf ears, but is not too late to address.
Enterprises understand cyber risks
Enterprises understand cyber risks
Hackers and cyber criminals often seek to exploit human errors like misconfigurations, poor security practices and the use of shadow IT.
In order to help businesses assess the risk CyberSecOP is launching an automated advanced persistent threat (APT) simulation platform, LocPar, to continuously expose all attack vectors, above and below the surface.
LocPar uses advanced attack techniques to expose the most critical blind spots. In the process, it provides data-driven remediation that focuses on an organization's most critical assets, reduces its IT risk and enables it to optimize its cyber resources.
"The best way to prevent a cyber attack is to identify in advance the attack vectors hackers will use to compromise an organization's critical assets," says CEO and co-founder of XM Cyber Noam Erez. "Even when an organization has deployed and configured modern security controls, applied patches and refined policies, it should still ask 'Are my crown jewels really secure?' as there is a plethora of ways hackers can still infiltrate the system and compromise critical assets. This is why we founded CyberSecOp: to equip enterprises with a continuous 360° view of which critical assets are at risk, what security issues they should focus on, and how best to harness their resources to resolve them."
Features of LocPar include full mapping of all attack paths at any given time, automatic adaptation to the context of the organization, using misconfigurations, user activity, credentials and security vulnerabilities in the network.
Comprehensive and up-to-date attack scenarios use the latest hackers' techniques and methods, giving the ability to detect and remediate IT-related risks in real-time. Reports are produced based on how critical the attack vector is.
Image Credit: SergeyNivens / depositphotos.com
Secure Your Website, from Cyber Attacks
The average website was attacked 44 times a day during the last quarter of 2017, according to new research from security specialist SiteLock.
The company analyzed six million sites to identify trends in the behavior and tactics of attackers. Though the number of attacks represents a 25 percent decrease over the previous quarter, it still means a site could be attacked 16,000 times a year.
"A decrease in attacks does not mean that websites are safer. In fact, it may even be the opposite," says Neill Feather, president of SiteLock on the company's blog. "Hackers are constantly trying new avenues and even leveraging older tactics that continue to be successful. As our research shows, cybercriminals are now able to successfully breach a site with fewer, more targeted attacks. Now more than ever, businesses need to evaluate their current security posture and ensure they have both the right technology and a response plan in place should a hack occur."
Among other findings are that around one percent of sites sampled are infected with malware each week. Yet only 19 percent of infected sites are blacklisted by search engines. WordPress sites using plugins are twice as likely to be infected as sites that don’t employ a content management system. In addition, 46 percent of infected WordPress sites have the latest core updates. The average number of infected files per site increased by 0.8 percent to 309.
The malware being used is increasingly complex too. 51 of the malware found was categorized as Encoded Malware, meaning it was randomly generated or difficult to decode. These are often parts of groups of files called 'attack kits'. Backdoors made up 12 percent of files, resulting in more files being uploaded to infected sites.
NYDFS Cybersecurity Retain a CISO, CSO -Regulation Compliance
With cyber-attacks on the rise and comprehensive federal cybersecurity policy lacking for the financial services industry, New York is leading the nation with strong cybersecurity regulation requiring, among other protective measures, set minimum standards of a cybersecurity program based on the risk assessment of the entity, personnel, training, and controls in place in order to protect data and information systems, said Superintendent in a press release issued by DFS, CyberSecOP helping financial organisation comply with the NYDFS manadates.
With the New York Department of Financial Services’ (NY DFS) new terms poised to come into effect next month, banks and financial services companies operating in the state must start preparing for the change.
One of the most discussed issues in the controversial proposal is the requirement to appoint a CISO (chief information security officer). The move was met by heavy criticism at a hearing in December last year, leading to a massive backtrack from the DFS in a revised proposal.
Requirements of the CISO
The latest proposal removes any explicit requirement to hire a CISO, which is good news for many smaller or rural financial institutions that don’t currently have one in place. What this means, practically, is that the position is no longer necessarily exclusive. Banks can choose to designate someone to complete the tasks of a CISO while also performing other duties. Alongside this, the proposal does not state that the specific title of ‘CISO’ is required.
So what will the CISO (or CISO by any other name) be asked to do? The role now covers a broader set of responsibilities but in a less detailed manner. The designated person will have to provide an annual report to the board of directors (previously proposed as a biannual report) on the “cybersecurity program and material cybersecurity risks”, according to the proposal. It is now specified that the report must be “in writing” but it no longer needs to be provided to the NY DFS upon request.
The required content of the report will now also be less extensive. The CISO must identify and report only on material cyber risks rather than all cyber risks. This will involve “consider[ing]” those issues “to the extent applicable.” Additionally, the CISO will be able to tailor their focus to the issues appropriate to their organization.
Finding the right candidate
The NY DFS’ revision allowing the CISO to be an employee of the covered entity (i.e. an internal hire), or an affiliate or third-party service provider offers crucial flexibility for smaller financial institutions.
Companies with only a handful of employees – the most vocal in their frustration at the DFS’ initial plans – may look to shuffle their existing staff.
When doing that – or in making a new hire – there are certain things organizations need to look for. The CISO role is not just a tech-specific position, notes John Linkous, RSA Conference’s technology advisor, but they must now be “a trusted advisor to the business as a whole”. He adds:
“One of the most critical capabilities is simply the ability to understand the business much more intimately than his or her predecessors. Business drives the need for technology, and so security must be focused on how data is used within those business functions, across the end-to-end spectrum. Without a solid understanding of what the organization does, and how it makes money, an information security officer is going to have a fundamental disconnect with what’s needed to protect the enterprise.”
Third-party service providers or affiliates
Given the responsibility placed on the CISO, outsourcing the role to a third party can be an appealing proposition.
Going down this route presents its own set of issues, though. As TechTarget reported, third parties are “almost always” involved when it comes cyber breaches – arguing that it is either through a lack of accountability or oversight. While service-level agreements (SLAs) are always advised, the DFS has taken steps to ensure the right measures are in place. In response to the fear that financial services firms would not always have sufficient power to force third parties to accept their preferred provisions, the NY DFS now dictates that all third-party services must be performed under contractual provisions rather than by way of “relevant guidelines for due diligence.”
Source: www.itgovernanceusa.com