CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
NIST Practices in Cyber Supply Chain Risk Management
Company Overview
Through its products and solutions, CyberSecOp offers cyber security tools, such as network, email, and mobile security as well as forensic investigation following a breach. As stated by the business:
The landscape of cyber threats is quickly changing. Organized threat actors are laser-focused on hacking systems and stealing data using sophisticated attacks that are tailored to compromise a specific target and evade traditional signature-based defenses, a key component of what currently constitutes basic cyber hygiene, instead of the broad scattershot attacks of the past.
SolarWinds Supply Chain Against US Agencies
The recent SolarWinds attack made the entire world aware of the danger of a cyber supply chain attack, or an attack on or through the vendors or suppliers of your company. It is becoming increasingly apparent that your business and its data are only as secure as the weakest link among your suppliers, even if you take all the necessary precautions to secure your own computer systems. This risk includes potential computer system attacks as well as the possibility of a disruption to the operations of your suppliers.
Common Risks for Supply Chains
Many risks can cause supply chain disruption, and those threats can have severe consequences for your business. Some of the more common risks are:
Cybersecurity Risks
Hackers can enter your supply chain and then move throughout your firm. Cybersecurity breaches can also wreak havoc on your day-to-day operations. So information security should be at the forefront of your mind when considering new vendors.
Compliance Risks
You’ll need to make sure your vendor can meet any regulatory compliance requirements your company has, which will subsequently affect your supply chain. For example, suppose a vendor bribes foreign government officials on your behalf. In that case, your company will be charged with violating the U.S. Foreign Corrupt Practices Act and all the legal ramifications that it entails.
Financial Risks
When collaborating with other companies, the risk of financial loss is always present. For example, if your contractor goes bankrupt or faces its own supply issues, this could have significant economic consequences for you and your organization.
Reputational Risks
Reputational risk is the most unpredictable type of risk because incidents that affect your reputation might happen out of nowhere. Damage to your contractors’ reputations can also harm yours, so consider reputational risk when choosing providers.
Cyber Supply Chain Principles and Supply Chain Risks
NIST identifies primary principles to consider for successful C-SCRM. These considerations are comprehensive and broadly apply to critical infrastructure, business processes, and intellectual property.
Understand the Security Risks Posed by Your Supply Chain
Examine the specific dangers that each supplier exposes you to, the products or services they provide, and the value chain as a whole.
Supply chain risks come in a variety of shapes and sizes. A supplier, for example, may not have enough security, may have a hostile insider, or its employees may not correctly handle your information. Gather sufficient information to better evaluate these security concerns, such as an insider data collection report or risk assessment.
Develop Your Organizational Defenses With “Assume Breach” in Mind
Assuming a breach means an organization approaches its cybersecurity posture by anticipating that its networks, systems, and applications are already compromised. Treating an internal network as if it’s as open as the internet readies the system for various threats and compromises.
Set Minimum Security Requirements for Your Suppliers
You should establish minimum security requirements and metrics for suppliers that are justified, proportionate, and achievable. Make sure that these standards reflect not only your evaluation of security risks but also the maturity of your suppliers’ security arrangements and their capacity to achieve the requirements you’ve set.
Minimum requirements should be documented and standardized to streamline enforcement. This technique will help you lower your effort and prevent giving these parties unnecessary work.
Cybersecurity is a People, Process, and Technology Problem
People, processes, and technology are the triad of solving problems. Supply chain management also focuses on these three areas to enhance supply chain performance, make it more secure, and do more with less.
Look at the Entire Landscape
There are multiple security standards that interact with each other in a variety of cybersecurity frameworks and best practices. A few examples are the NIST Cybersecurity Framework (CSF), Center for Internet Security (CIS) Controls, and the International Organization for Standardization (ISO) series.
To be efficient and flexible, your C-SCRM should follow the guidelines established by your third-party risk management program. That is especially important today, where outsourcing is common. Always remember that your C-SCRM program is only as good as the data security provided by your least secure third- or fourth-party supplier.
Encourage the Continuous Improvement of Security within Your Supply Chain
Encourage your vendors to keep improving their security measures, emphasizing how this will help them compete for and win future contracts with you.
Advise and support your suppliers as they seek to make these improvements. Allow your suppliers time to achieve improvements but require them to provide you with timelines and project plans.
Listen to and act on any issues arising from performance monitoring, incidents, or bottom-up supplier reports that imply current approaches aren’t functioning as well as they should.
Best Practices for Cyber Supply Chain Risk Management
An organization can employ a variety of best practices in its C-SCRM program. Best practices improve the ability to identify and mitigate potential risks over time. In addition, these practices include remediation steps to apply if you experience a data breach.
Here is a list of some of the best practices to keep in mind as you set to work on your cyber supply chain risk management program:
Security requirements need to be defined in requests for proposals (RFP). In addition, use security questionnaires to hone in on the current standards practiced by each bidder.
An organization’s security team must assess all vendors, and you must remediate vulnerabilities before sharing information, data, or goods and services with them.
Engineers must use secure software development programs and keep up-to-date on training.
Software updates need to be available to patch systems for vulnerabilities, and they must be downloaded and installed in real time.
Dedicated staff that is assigned to ongoing supply chain cybersecurity activities.
Implement and enforce tight access controls to service vendors.
The new NIST guidance reflects the increased attention companies are paying to manage cyber supply chain risks. It is a useful resource for enterprises of all sizes, though some of the recommendations may be too burdensome or complex for smaller organizations to reasonably adopt. Small businesses may lack the sufficient purchasing power to require their suppliers to complete certifications or participate in contingency planning, as NIST suggests, and may not have the resources to create internal councils and intricate review procedures.
Remote Working And Online Safety Tips
1. Avoid Creating Easy or Common Passwords
Password123 is a big no-no. Hackers have become bolder and have been using password deciphering tools to infiltrate vulnerable accounts. Multi-factor authentication (discussed later in this list) will most likely prevent them from going further, but it is always recommended to create a password with a mix of symbols, numbers, capital letters, and a lengthy number of characters to make it harder to crack. Also, the more frequently you change a password, the better. We also recommend using different passwords for different accounts. If the same password is used for multiple accounts, it becomes easier for hackers to infiltrate multiple accounts.
2 Connect Only to Protected Private WiFi Networks or (VPN) Virtual Private Networks
Always use private, password-protected WiFi networks to connect remotely. Security experts consider signing in to sensitive office networks with public WiFi or unsecured network connections akin to “swimming in shark-infested waters”—it’s only a matter of time before you get bit. Experts recommend consulting a trusted IT provider about setting up a VPN that can minimize the risk to devices and data.
3. Unusual Phrasings in subject lines/body, misspellings, poor-quality images or bad grammar
Although corona-virus-related phishing schemes are currently at an all-time high, the good news is that they aren’t much different from past attempts. Paying extra attention to message details—capitalization, punctuation, paragraph structure, sloppy design/formatting, or any language that seems out of the norm, makes detecting fake ones easier.
4. Don’t download unfamiliar attachments or click on unfamiliar links
In the age of remote work, collaborative OneDrive, Google Docs, or general Cloud sharing is a common way to redirect others to a malicious website. If you aren’t expecting a specific file from a specific sender, don’t open any attachments in an unknown message. This applies to links as well. To check if a link is safe, hover your mouse over the link to confirm the target URL matches what’s written (on a desktop or laptop). For extra precaution, type out the website to avoid being unknowingly redirected.
5. Activate multi-factor authentication (MFA) on every account you can
Many phishing schemes try to get you to re-enter your password for common apps or social media accounts—all in hopes that hackers can steal your password. Using multi-factor authentication can mitigate this since MFA requires something you know (your password) with something you have (a unique code delivered via text message or email).
6. Confirm the sender's email address
It’s easy for a hacker to mimic someone’s display or contact name—always double-check to confirm what shows up with the actual email address the message was sent from to make sure the sender is who he or she is claiming to be.
7. Do not respond to email correspondence from any financial institution
This goes for any communications via email or phone. You will not be prompted to sign in to your account or receive a call from your financial institution asking for your PIN or other personal information. In fact, most updates are sent with a 'do-not reply' email handle. Most official communications from financial firms are usually sent via snail mail. To ensure you are in contact with an actual representative of the firm, call the number on the back of your card or the phone number provided on your financial statements.
We hope you find these tips helpful.
Safe remote working and browsing!
- The CyberSecOp Team
Choosing A Managed Detection & Response Provider
Why Managed Detection & Response Provider may be the right move
Companies outsourcing security need Managed Detection & Response providers (MDR) more than ever to improve cyber resilience. With the security landscape growing more complex, and the costs of maintaining adequate in-house security teams high, it makes sense for many companies to outsource the tasks of threat hunting and response to ensure that they can promptly identify potential threats and react swiftly to mitigate damages. Managed Detection & Response providers often integrate tools such as Endpoint Detection & Response and other solutions to detect threats, analyze risk, and correlate threat data to pinpoint patterns that could indicate a larger attack.
How to choose the right Manged Detection & Response Provider
Smart moves: you’re making them. How do we know? For one, you’re investigating ways to close the gaps in your threat detection and incident response. Which makes sense, given that assembling the talent and tech to thoroughly thwart attackers requires more than most organizations can commit to. Even smarter, you’re checking out Managed Detection and Response (MDR) Services, an increasingly popular solution which combines expertise and tools to provide monitoring and alerting, as well as remote incident investigation and response that can help you detect and remediate threats.
9 things to look our for when choosing a Managed Detection & Response Provider
Your Managed Detection & Response Provider should combine numerous data inputs from security detection tools, threat intel feeds, third party data sources, and the IT asset database to identify not only where there is a threat but its risk compared to others in the queue.
Assess your company's present and future technology needs and initiatives. Qualify, quantify and communicate those needs throughout your company. Is the Managed Detection & Response Provider able to address your range of needs?
Technology strategies should encompass people and processes as part of the organization's mission and strategies. Do they offer ongoing employee training as part of their service?
Does the Managed Detection & Response Provider continuously assess your organization's performance for meeting objectives? You want a partner that focuses on continuous evaluation and improvement of your objectives.
Review your company's goals and mission. Ensure they are clear and concise and can be communicated to all organizational stakeholders as well as your new IT partner.
Perform annual policy and process reviews to assess organization's readiness for external reviews and incident response.
Identify and create teams within your organization to define current challenges and align initiatives to those challenges.
Through playbooks and pre-defined workflows, you can quickly assess and begin to remediate security incidents based on best practices. Ask a Managed Detection & Response Provider if they include such materials as part of their package.
CIOs/CISOs should have unprecedented transparency to all aspects of the security environment. Through dashboards and visualization techniques, CIOs/CISOs will be more easily able to communicate with Managed Detection & Response Providers which vulnerabilities and threats exist and the risks of inaction.
CCPA Data Privacy - California Consumer Privacy Act (CCPA)
CCPA Data Privacy
The California Consumer Privacy Act of 2018 (CCPA) into effect. This new consumer privacy law comes post Europe’s General Data Protection Regulation (GDPR) and, for some, is seen as a smaller version – without the option to opt-out of data collection all-together that the GDPR has.
CCPA is a consumer privacy law that will be coming into effect on January 1, 2020. The bill – which is aggressive for American privacy policy standards – will put guidelines on personal information collection and post-data-acquisition data usage by businesses.
Come 2020, the California Consumer Privacy Act (“CCPA”) may significantly impact businesses’ data practices, with new and burdensome compliance obligations such as “sale” opt-out requirements and, in certain circumstances, restrictions on tiered pricing and service levels. The breadth of personal information covered by the CCPA, going beyond what is typically covered by U.S. privacy laws, will complicate compliance and business operations.
Who need to comply with CCPA
Companies, especially those outside of California, may wonder whether they are subject to the CCPA. CCPA applies to for-profit entities that (1) have greater than $25 million in gross annual revenues; (2) annually handle personal information of 50,000 or more consumers, households, or devices; or (3) derive 50% or more of annual revenue from selling personal information. These criteria will result in a wide swath of businesses being subject to the CCPA. For example, a website might only need 137 unique visitors from California per day to reach the threshold of 50,000 consumers. That website’s collection of data through cookies may be captured by the CCPA’s broad definition of personal information. And given the third criterion focused on revenue percentage, even very small businesses that regularly exchange data, for example in the online ecosystem, might be captured if their activities are deemed to be a “sale” under the CCPA.
CCPA PRIVACY OVERSIGHT
The CCPA will impose substantial compliance obligations on all businesses that handle personal information of California consumers. Such obligations may pose particular challenges for the ever increasing array of businesses that leverage consumer data for analytics, profiling, advertising, and other monetization activities, particularly as the compliance requirements are not easily gleaned from the statutory language. Addressing these challenges will require creative, thoughtful approaches and may potentially involve industry-wide coordination to develop and advance practical solutions.
CyberSecOp CCPA privacy consultants incorporates your CCPA compliance requirements, powered by a unique combination of deep privacy expertise developed over two decades, proven methodologies refined through tens of thousands of engagements, and powerful technology operating at scale for 20 years.
Cyber Security: Information Data Protection
CyberSecOp assist clients with managing privacy risk while keeping thier existing controls as effective and efficient as possible to withstand a complex privacy risk environment. We focus on testing, and training based on common employee mistakes and remediate gaps in the process, eeping your systems in line with current regulations,
The revolution that has taken place over the past 20 years has had an impact on both consumers and enterprises. The devices and applications that millions of individuals use on a daily basis contain increasingly more complex information, within a constantly evolving technological environment. The growing digital innovation trends such as cloud computing, big data and the IoT create new opportunities to communicate and exchange information. However, this massive amount of confidential data must consequently be managed and secured efficiently and continuously.
How can a company guarantee the security of its data and of its users' data? What solutions are currently available on the market that can help enterprises optimize the management of information while maintaining their privacy?
CyberSecOp, an american base market leader in the Managed Security Service Provider industry, responds to the companies' need for security, offering a range of solutions and services designed to help customers identify cyber security risks in order to mitigate and monitor them over time.
Through its diverse solutions portfolio, CyberSecOp provides the right mix of technology, processes and sector-specific knowledge, supporting customers during the initial planning phase, from design to implementation, in order to identify the best solutions both in terms of process, as well as technology. The company’s strategic partnerships with key suppliers and expertise with market technologies guarantee customers a solution that provides effective operational coverage, on-premise or remote, with vertical expertise throughout the duration of the project and during the delivery of services.
Moreover, thanks to a Cyber Security Operations Center (CSOC), the delivery of timely services and continuous security monitoring are seamlessly integrated to reduce cyber security-related risks. The service is designed to offer the customer a growth-oriented path aimed at improving the company’s overall security position and risk level awareness.
The Industry 4.0 evolution and the arrival of the IoT have significantly increased the complexity and the level of risk to which all enterprises are subject, necessitating an efficient management of corporate security. In a changing environment characterized by increasing opportunities, while at the same time offset by an exponential increase in associated risks, the availability of CSOC services represents an essential guarantee of security.
MSSP Cybersecurity & Managed Detection and Response
MSSP Cybersecurity & Managed Detection and Response
Managed detection and response enables a proactive approach to security with its ability to detect and fully analyze threats and promptly respond to incidents. CyberSecOp Threat intelligence is one of the key aspects our security consultants used to help organizations make decisions on how to combat threats. Through managed detection and response, organizations can take advantage of the threat intelligence capabilities of security experts.
How Managed Detection and Response Provides Effective Threat Intelligence
Capture full visibility across your entire IT environment
Detect the most advanced threats (known and unknown) designed to bypass your traditional perimeter security controls, even when no malware is used
Expose threat actors currently hiding in your environment
Gain 24x7 monitoring by an advanced team of security experts that are specially trained to analyze advanced threats, determine the severity of any incidents and provide actionable guidance to remediate
Quickly elevate the alerts that matter most so you can focus limited resources where it matters most
Managed Detection and Response Service
Managed Detection and Response (MDR) is an all-encompassing cybersecurity service used to detect and respond to cyber-attacks. Using the best of signature, behavioral and anomaly detection capabilities, along with forensic investigation tools and threat intelligence, human analysts hunt, investigate and respond to known and unknown cyber threats in real time 24x7x365. Get Managed Detection and Response Services for your business www.cybersecop.com.
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
Prevent DDoS attacks across your enterprise
DDoS (Distributed Denial of Service) attacks feature amongst the most dreaded kinds of cyber attacks, for any enterprise today. This is especially because, as the name itself suggests, there it causes a total denial of service; it exhausts all resources of an enterprise network, application or service and consequently it becomes impossible to gain access to the network, application or the service.
In general, a DDoS attack is launched simultaneously from multiple hosts and it would suffice to host the resources, the network and the internet services of enterprises of any size. Many prominent organizations today encounter DDoS attacks on a daily basis. Today DDoS attacks are becoming more frequent and they are increasing in size, at the same time becoming more sophisticated. In this context, it becomes really important that enterprises look for DDoS attack prevention services, in fact the best DDoS attack prevention services, so as to ensure maximum protection for their network and data.
The different kinds of DDoS attacks
Though there are different kinds of DDoS attacks, broadly speaking there are three categories into which all the different kinds of DDoS attacks would fit.
The first category is the volumetric attacks, which include those attacks that aim at overwhelming network infrastructure with bandwidth-consuming traffic or by deploying resource-sapping requests. The next category, the TCP state-exhaustion attacks, refer to the attacks that help hackers abuse the stateful nature of the TCP protocol to exhaust resources in servers, load balancers and firewalls. The third category of DDoS attacks, the application layer attacks, are basically the ones targeting any one aspect of an application or service at Layer 7.
Of the above-mentioned three categories, volumetric attacks are the most common ones; at the same time there are DDoS attacks that combine all these three vectors and such attacks are becoming commonplace today.
DDoS attacks getting sophisticated, complex and easy-to-use
Cybercriminals today are getting cleverer and smarter. They tend to package complex, sophisticated DDoS attack tools into easy-to-use downloadable programs, thereby making it easy even for non-techies to carry out DDoS attacks against organizations.
What are the main drivers behind DDoS attacks? Well, there could be many, ranging from ideology or politics to vandalism and extortion. DDoS is increasingly becoming a weapon of choice for hacktivists as well as terrorists who seek to disrupt operations or resort to extortion. Gamers too use DDoS as a means to gain competitive advantage and win online games.
There are clever cybercriminals who use DDoS as part of their diversionary tactics, intending to distract organizations during APT campaigns that are planned and executed in order to steal data.
How to prevent DDoS attacks
The first thing that needs to be done, to prevent DDoS attacks from happening, is to secure internet-facing devices and services. This helps reduce the number of devices that can be recruited by hackers to participate in DDoS attacks.
Since cybercriminals abuse protocols like NTP, DNS, SSDP, Chargen, SNMP and DVMRP to generate DDoS traffic, it’s advisable that services that use any of these ought to be carefully configured and run on hardened, dedicated servers.
Do repeated tests for security issues and vulnerabilities. One good example is doing penetration tests for detecting web application vulnerabilities.
Ensure that your enterprise implements anti-spoofing filters as covered in IETF Best Common Practices documents BCP 38 and BCP 84. This is because hackers who plan DDoS attacks would generate traffic with spoofed source IP addresses.
Though there are no fool-proof techniques that can prevent DDoS attacks completely, you can ensure maximum protection by ensuring proper configuration of all machines and services. This would ensure that attackers don’t harness publicly available services to carry out DDoS attacks.
It’s to be remembered that it’s difficult to predict or avoid DDoS attacks and also that even an attacker with limited resources can bring down networks or websites. Hence, for any organization, it becomes important that the focus is always on maximum level protection for enterprise networks, devices, websites etc.
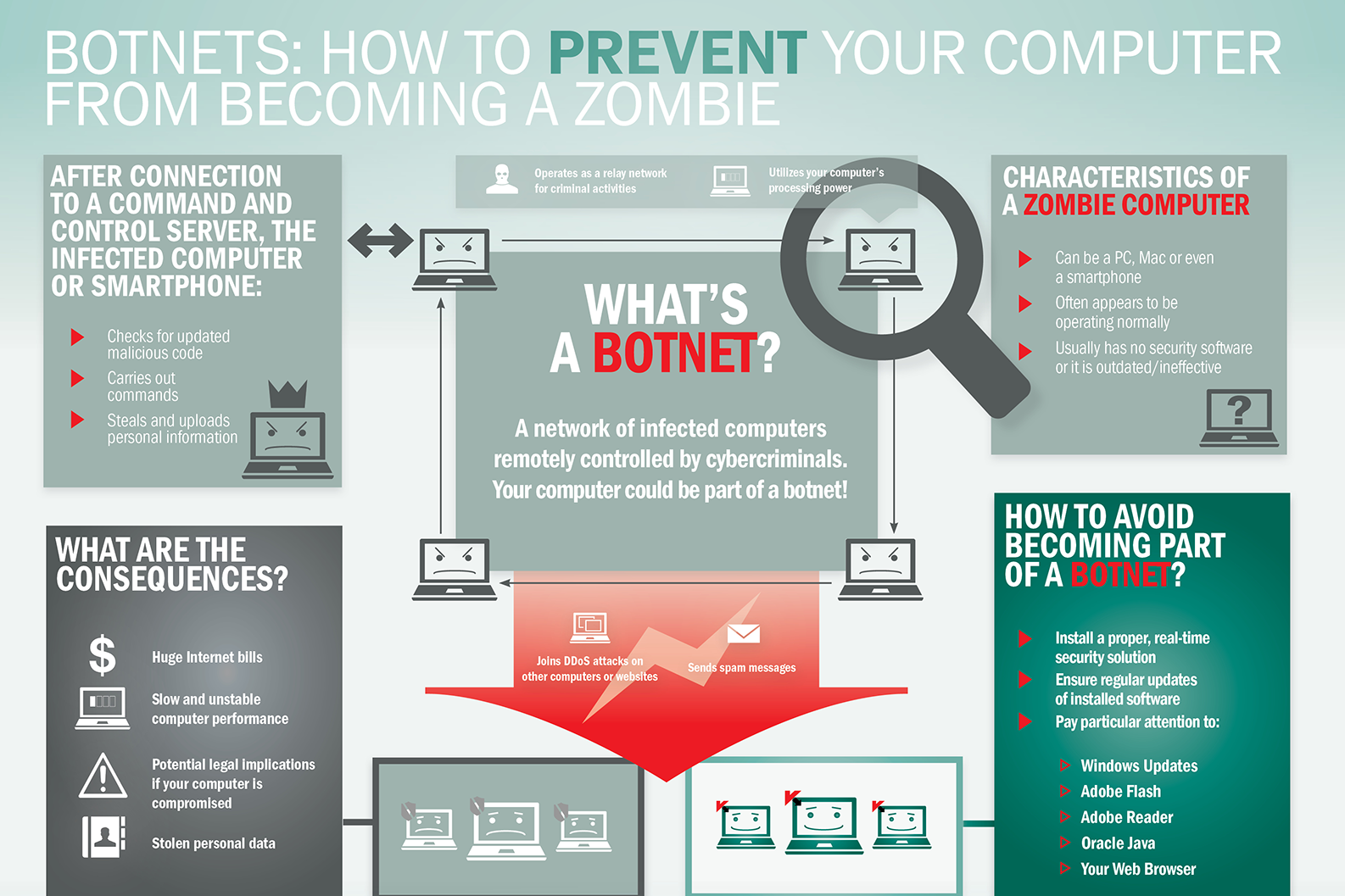
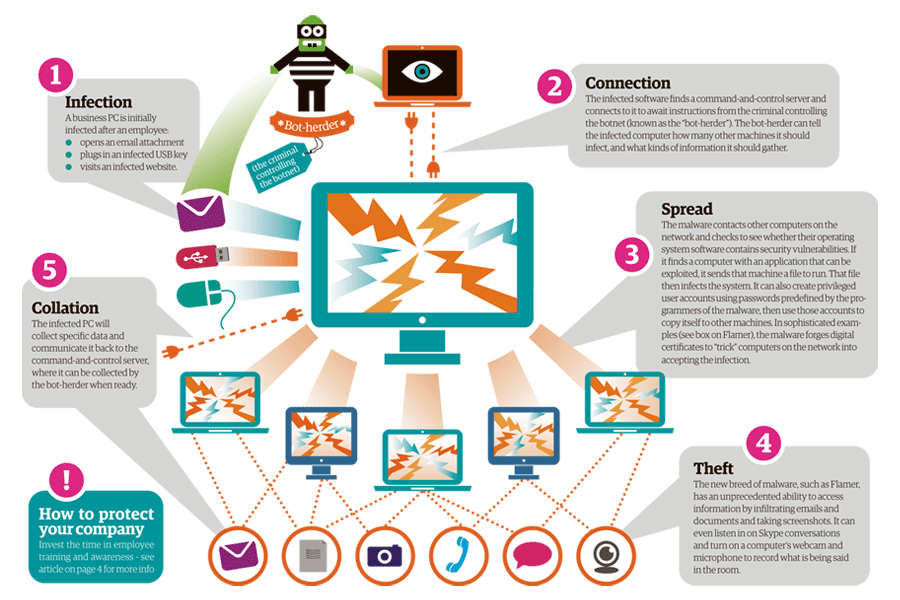
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
What advice does the world's first CISO have
What advice does the world's first CISO have for the current generation of CISOs? Stephen Katz emphasizes, first and foremost, that cybersecurity must be treated as a business risk management issue rather than a technology issue.
"Security has to evolve and grow at the same pace as the business," he stresses in an interview with Information Security Media Group.
The role of the CISO has to be recognized as a core business function, he adds. "Security has to be an enabler of the business; security has to earn a seat at the executive table. Too often, we give people the title of chief information security officer; they don't believe they're an executive, and executives don't believe they are an executive."
In this interview (see audio link below photo), Katz also discusses:
Changes in the threat landscape since becoming the world's first CISO;
Top priorities for CISOs in the coming year;
Why getting back to the basics of security remains so important;
The ongoing growth of machine learning models in all aspects of cybersecurity.
Katz is the founder and president of Security Risk Solutions LLC, an information security company providing consulting, mentoring, coaching and advisory services. He was formerly CISO at JPMorgan Chase, Citigroup and Merrill Lynch.
Secure Google Chrome from Hacking Attacks
Google Chrome is definitely one of the most popular web browsers being used today. Hackers, as we know, are perpetually after whatever gets popular in the world of the internet. This because whatever is popular would help them target more people and steal more data. Thus, Google Chrome too happens to be among the most favorite for cyber criminals across the world. Hence, securing Google Chrome against hacking attacks is really important.
So, how do we secure Google Chrome from cyber attacks? Well, it’s a multi-step process. Lots of things have to be done. Securing your browser is important as it helps secure your device, your internet connection and more importantly, your personal and business data.
Let’s discuss, in detail, what all needs to be done to secure Google Chrome from hacking attacks. Here we go:
Begin by ensuring that your Google account is properly secured!
This is something basic, your Google account needs to be properly secured. Chrome lets you sign in from any device, anytime. Hence, it’s important to ensure the security of your Google account. You need to make sure you are logged out of your account every time you sign in, on any device. You also need to ensure that your password is secure. If you aren’t signed out or if someone knows/cracks your password, it would be easy to manipulate things and cause you harm. Your data could be stolen.
Keeping the browser secured is equally important…
Keeping the browser secured is as important as securing your Google account. You could use a password to protect your browser, and thus, in your absence, no one would be able to take control of your browser and do mischiefs. Similarly, every time you leave your terminal, it’s good to go out of the browser as well.
Keep your browser ‘clean’!
You should make it a habit to keep your browser ‘clean’, by wiping out most of the information from it. In fact, there should be some plan/schedule as regards cleaning the browser. Clear the history periodically, either everytime you log out or at least once every week if not once a day.
Never save passwords on the browser
The browser might offer to ‘remember’ your passwords for you so that you could sign in easily the next time you’re using some service. But it’s always good not to save passwords on the browser. If you save your passwords, it would be possible for someone else to get into your account and misuse it or steal information.
Having a master password helps
Having a master password, which would help you get to your other saved passwords in Chrome, is a good thing to do. Thus you need not worry about remembering all of your passwords and you don’t have to be afraid of your passwords getting stolen or misused either.
Keep your device protected
The device that you use to browse needs to be protected from malware and hacking. For this, you must use whatever security tools you need and also have alerts that tell you if at all your device is compromised. Remember a compromised device means an unsecured browser!
Keep the device locked whenever you’re not using it
Always keep your device locked when you are not using it, be it a computer or any other mobile device. That prevents people from getting on to your device and hijacking your browser and your data as well. Locking your device also gets it off the WiFi network that you are using.
Secure your network, never use unsafe WiFi networks
Securing your network is important; it helps a lot in securing Google Chrome from hacking attacks. Hence you need to do all that is needed to secure your network. Similarly, it’s always advisable never to use unsafe WiFi networks. Whenever you’re using a WiFi network, ensure it’s properly encrypted and if possible use an app or program that would prevent hacking. In fact, using a secure network secures not just your browser, but everything on your device/system.
Trust Chrome for phishing detection
Google Chrome does its own phishing detection and protects you from many phishing websites. So, when your browser tells you that a website is not safe, it’s always advisable to trust it and avoid such sites.
Avoid phishing websites and attachments yourself
In addition to Google Chrome detecting phishing websites for you, it’s always good that you yourself stay away from websites/attachments that could be used for phishing scams. Staying away from such suspicious websites secures your browser, your system/network and your data.
Useful tips for implementing the cloud
Useful tips for implementing the cloud
“One very important thing is to not implement solutions on the cloud with a traditional mindset. Many clients are surprised when they see their first bill because they ‘lift and shift’ the infrastructure,”
“Remember, the cloud is highly elastic in nature and you can scale up and when you require. So, implement the minimum infrastructure needed and scale it based on load. That’s the secret to success in the cloud!”
Focus on entry and exit points in terms of network connectivity. Wherever possible, use private connections such as Microsoft express route, AWS direct connect.
In terms of cloud application connectivity, always encrypt the data in transit using SSL.
Ensure you implement least privileged and conditional based access to cloud administrative portals such as the Azure portal and AWS management console.
Implement RBAC access in providing access to cloud resources. Segregation and isolation of the resources using resource groups, virtual networks is key!
Utilise the security monitoring tools provided by cloud services provider to monitor the solution. Most of the basic functionality is free, such as Azure’s security centre.
In general, always divide the security focus areas into a matrix where rows are networks, compute, storage, applications, databases, and columns are data encryption at rest, encryption at transit, authentication and authorization etc; this will allow focussing on each security cell.
Carry out security risk assessment during the design phase to ensure the design has the appropriate security controls in place to mitigate possible risks.
Nevertheless, problems can arise when storing data in the cloud. “Services & data in the cloud is accessible from the internet. Unless proper controls in place, your users can access and download the data from anywhere in the world,” warns Varma.
Cloud storage security
“The majority of clients require their data to be encrypted in the cloud. Although cloud supports ‘bring your own key’ options, these encryption keys are stored in cloud providers key vaults. So, there is a very narrow chance that cloud providers can access those keys and decrypt the data. It’s also vital to note that cloud providers have very strict governance and accreditations in place to mitigate the same.”
Cloud providers generally keep their cloud services up-to-date with advancements in technology, according to Varma. “On the other end, many of the clients’ data centers he has worked within the past have out-of-date IT infrastructure systems & applications which takes a lot of time and money to replace and are prone to attacks”, he adds.
Varma also advises that you must ask your service provider the following questions about cloud storage security:
What is the authentication and authorization approach to cloud services?
How do you implement access controls for cloud services?
What’s the approach to secure transit and rest data?
What is preventive security monitoring are in place against risks and threats?
Are their solution adheres to such as cyber essentials, cloud security principles, ISO 27002?