CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Microsoft Warns of Sneaky Phishing Campaign
Microsoft's Security Intelligence team sounds the alarm on a sneaky phishing email campaign with fake sender addresses. The phishing email also cleverly employs various detection evasion techniques to trick most automated filters and users in its attempt to garner Microsoft Office 365 credentials.
The alert was sent after observing an active campaign that was zoning in on Office 365 organizations with convincing emails.
In a statement by Microsoft, "An active phishing campaign is using a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to try and slip through email filters."
Microsoft notes that this campaign is sneakier than usual due to the convincing Microsoft logos with the link posing as a 'file share' request to access bogus reports. However, the main phishing URL relies on a Google storage resource that takes the victim to the Google App Engine domain Appspot. This results in hiding a second URL that directs the victim to a compromised SharePoint site, and thus allowing the attack to bypass sandboxes.
Researchers at Microsoft have published details
Accounting to the FBI
According to the FBI's latest figures, phishing attacks have cost Americans more than $4.2 billion last year. Fraudsters employ business email compromise (BEC) attacks, which rely on compromised email accounts or email addresses that are similar to legitimate ones and are difficult to filter as they blend within normal, expected traffic. BEC attacks are far more costly than high-profile ransomware attacks.
Vishing Awareness
Vishing
Spoofing a legitimate phone number, voice phishing scammers lead people to believe the call is legitimate
What is Vishing?
We’ve all heard the countless stories on phishing and how much of a threat is it in today’s information security landscape. Social engineering to solicit confidential information via email is a threat that all of us have been made aware of. Extensive efforts have been made to not only reduce the influx of phishing emails, but also to raise awareness so that users have the know-how to assess and respond to the threat when a malicious email hits their inbox.
In response, threat actors have turned to a newer form of exploitation: Vishing. Vishing is a form of criminal phone fraud that uses social engineering over the phone or SMS to gain confidential information. Here are some examples
Fake call from “Help Desk” asking for credentials
Unsolicited calls for credit and loans
Calls from a fake client asking about an invoice
Vishing is becoming an increasingly favored tool attackers use, due to the Covid-19 pandemic. With the shift to work-from-home environments, corporate VPNS, and elimination of in-person verification, threat actors are shifting their tactics to exploit this widespread weakness.
How do I protect my firm against Vishing?
Security awareness is the best line of defense against this type of attack, so be sure to incorporate vishing education into your information security awareness program. Policies and procedures should be established and communicated to ensure that employees can verify identity when the helpdesk or anyone else from the company calls and asks after proprietary topical information. It is imperative that information security managers instill a sense of suspicion for any caller asking for said information.
Enabling MFA for any system that has access to confidential information, network or system is non-negotiable; that second factor of authentication can halt many types of attacks. When you enable MFA you avoid the use of SMS as a means of authentication as SMS is easily manipulated and exploited.
Lastly, always apply least privilege so that in the event an account is compromised, there will be minimal damage.
AUTHOR: CARLOS NETO
Information Security Officer
Phishing Attack Prevention: What is Phishing?
What is Phishing?
Phishing is the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about to protect themselves.
Phishing Attack Prevention:
Why are so many companies vulnerable to phishing? Not having the right tools in place and failing to train employees on their role in information security.
Employees possess credentials and overall knowledge that is critical to the success of a breach of the company's security. One of how an intruder obtains this protected information is via phishing. The purpose of phishing is to collect sensitive information to use that information to gain access to otherwise protected data, networks, etc. A phisher's success is contingent upon establishing trust with its victims. We live in a digital age, and gathering information has become much easier as we are well beyond the dumpster diving days.
How do I protect against phishing attacks?
Free Email Protection
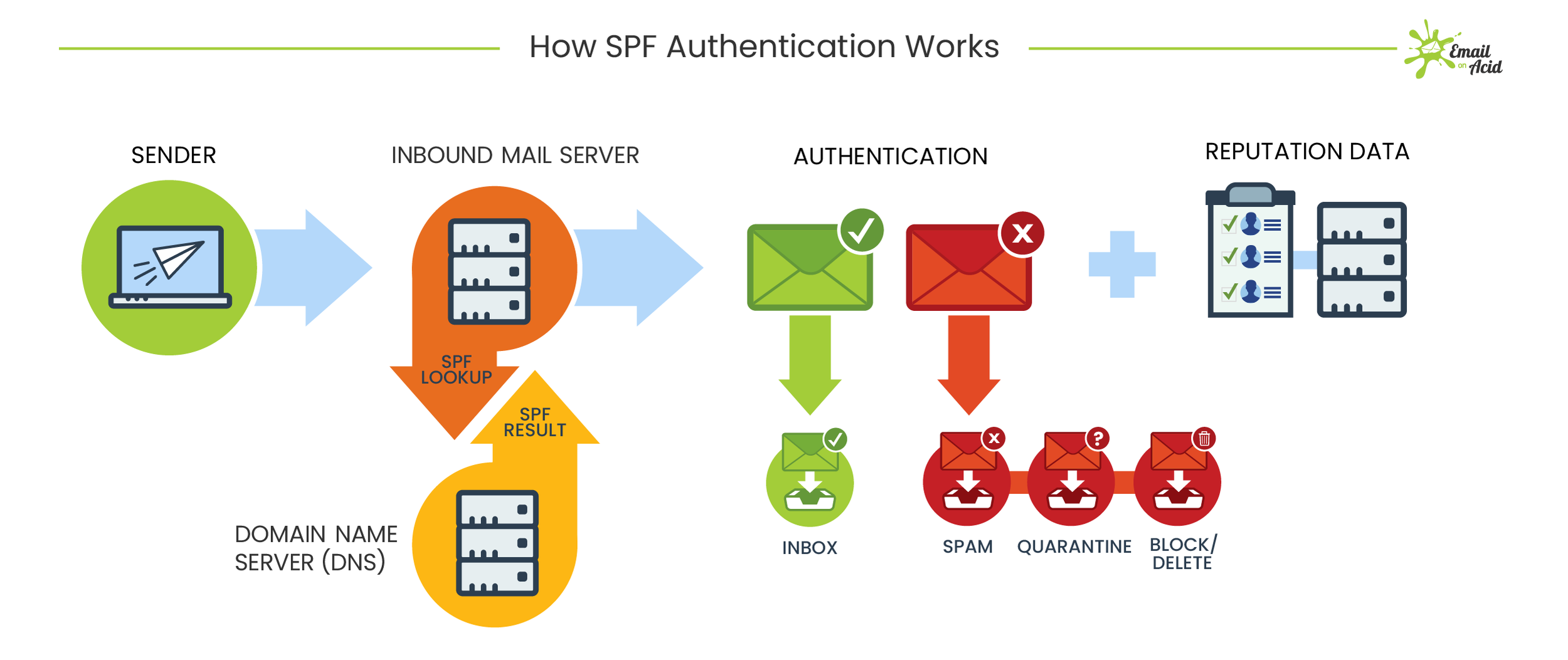
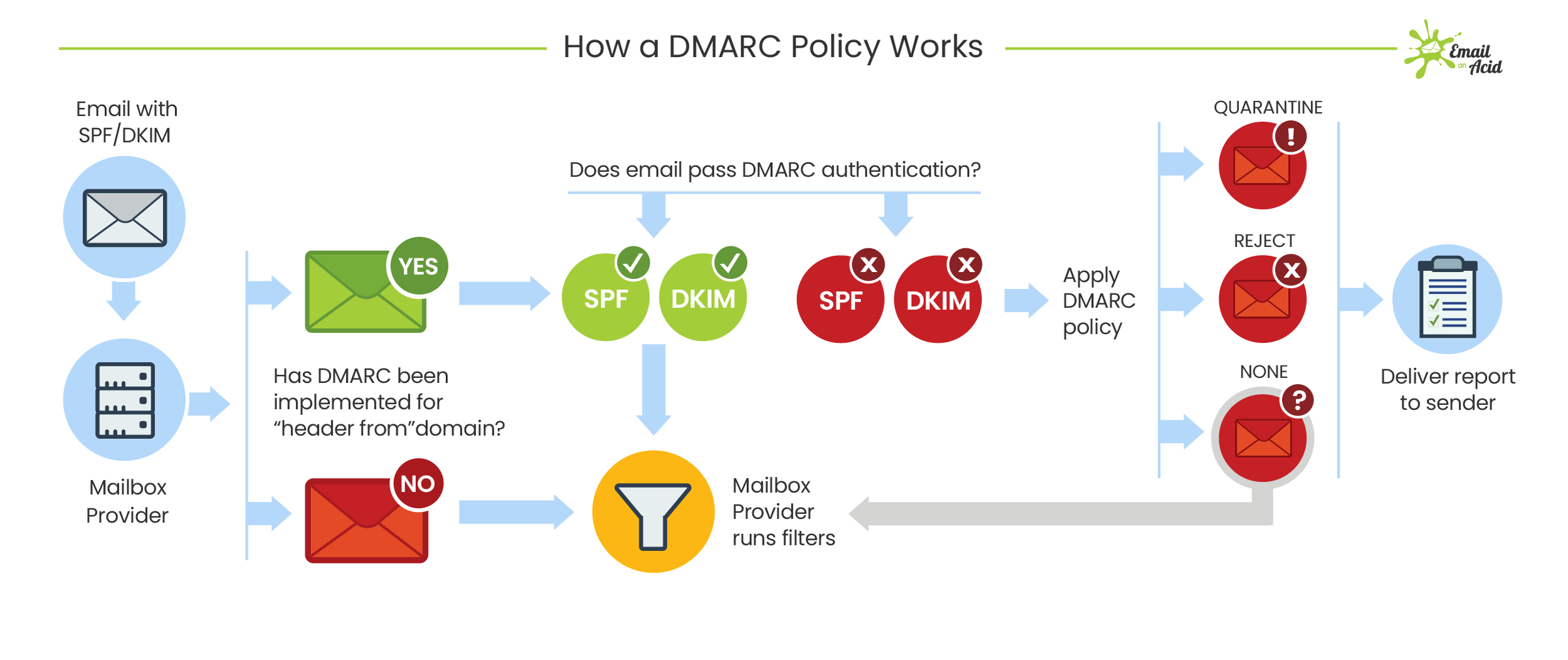
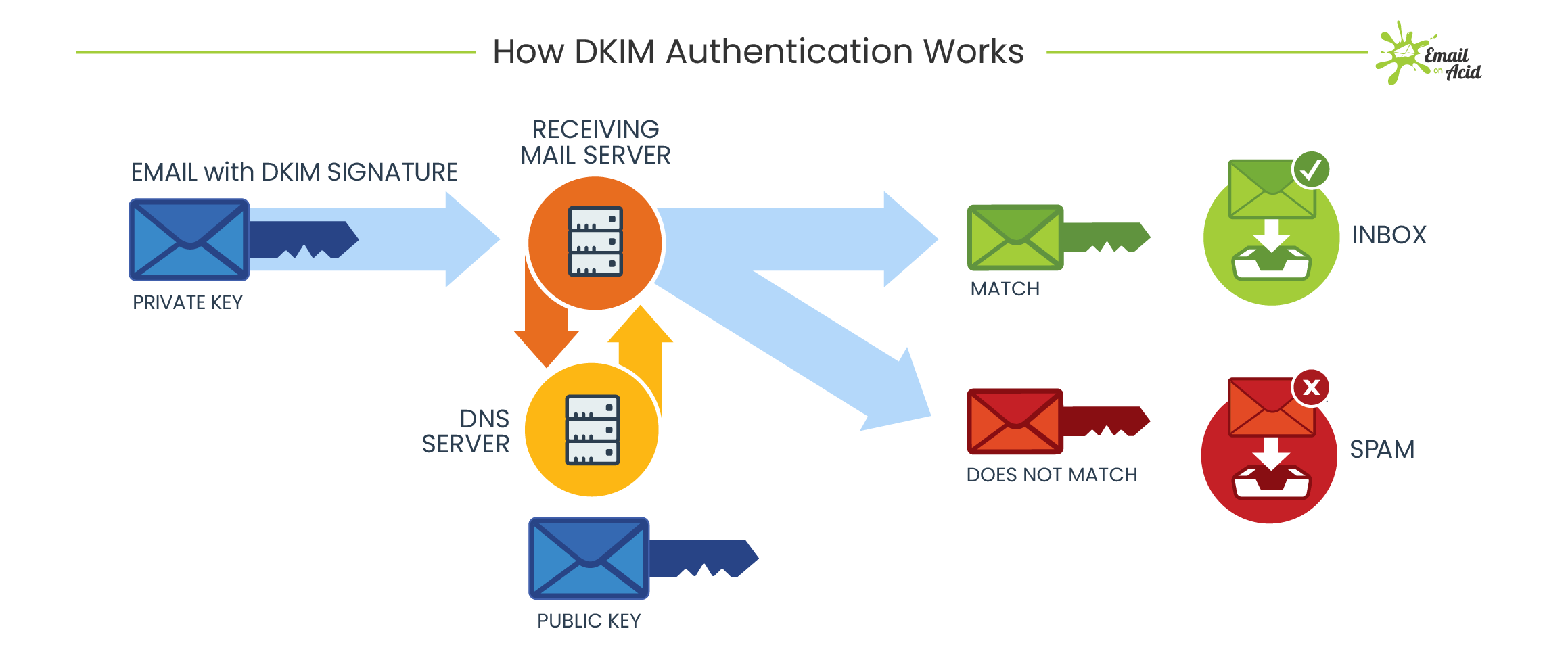
Free protocols that help organizations improve email security; Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM) were developed. SPF cross-checks the sender’s IP address with an approved list of IP addresses, and DKIM uses an encrypted digital signature to protect emails. While these are both individually effective, they have their own set of flaws. DMARC, developed in 2012, is a protocol that uses both SPF and DKIM authentication to secure email and has a mechanism that sends the domain owner a report whenever an email fails DMARC validation.
But here’s the thing: a recent report from phishing specialist Agari states that only 1/3 of the Fortune 500 have configured DMARC.
User education
One way to protect your organization from phishing is user education. Education should involve all employees. High-level executives are often a target. Teach them how to recognize a phishing email and what to do when they receive one. Simulation exercises are also key for assessing how your employees react to a staged phishing attack.
Security technology
No single cybersecurity technology can prevent phishing attacks. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control.
How does phishing work?
Phishing starts with a fraudulent email or other communication that is designed to lure a victim. The message is made to look as though it comes from a trusted sender. If it fools the victim, he or she is coaxed into providing confidential information, often on a scam website. Sometimes malware is also downloaded onto the target’s computer.
What are the dangers of phishing attacks?
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing.
Types of Phishing
Deceptive Phishing. The term "phishing" originally referred to account theft using instant messaging but the most common broadcast method today is a deceptive email message. Messages about the need to verify account information, system failure requiring users to re-enter their information, fictitious account charges, undesirable account changes, new free services requiring quick action, and many other scams are broadcast to a wide group of recipients with the hope that the unwary will respond by clicking a link to or signing onto a bogus site where their confidential information can be collected.
Malware-Based Phishing refers to scams that involve running malicious software on users' PCs. Malware can be introduced as an email attachment, as a downloadable file from a web site, or by exploiting known security vulnerabilities--a particular issue for small and medium businesses (SMBs) who are not always able to keep their software applications up to date.
Keyloggers and Screenloggers are particular varieties of malware that track keyboard input and send relevant information to the hacker via the Internet. They can embed themselves into users' browsers as small utility programs known as helper objects that run automatically when the browser is started as well as into system files as device drivers or screen monitors.
Session Hijacking describes an attack where users' activities are monitored until they sign in to a target account or transaction and establish their bona fide credentials. At that point the malicious software takes over and can undertake unauthorized actions, such as transferring funds, without the user's knowledge.
Web Trojans pop up invisibly when users are attempting to log in. They collect the user's credentials locally and transmit them to the phisher.
Hosts File Poisoning. When a user types a URL to visit a website it must first be translated into an IP address before it's transmitted over the Internet. The majority of SMB users' PCs running a Microsoft Windows operating system first look up these "host names" in their "hosts" file before undertaking a Domain Name System (DNS) lookup. By "poisoning" the hosts file, hackers have a bogus address transmitted,taking the user unwittingly to a fake "look alike" website where their information can be stolen.
System Reconfiguration Attacks modify settings on a user's PC for malicious purposes. For example: URLs in a favorites file might be modified to direct users to look alike websites. For example: a bank website URL may be changed from "bankofabc.com" to "bancofabc.com".
Data Theft. Unsecured PCs often contain subsets of sensitive information stored elsewhere on secured servers. Certainly PCs are used to access such servers and can be more easily compromised. Data theft is a widely used approach to business espionage. By stealing confidential communications, design documents, legal opinions, employee related records, etc., thieves profit from selling to those who may want to embarrass or cause economic damage or to competitors.
DNS-Based Phishing ("Pharming"). Pharming is the term given to hosts file modification or Domain Name System (DNS)-based phishing. With a pharming scheme, hackers tamper with a company's hosts files or domain name system so that requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site. The result: users are unaware that the website where they are entering confidential information is controlled by hackers and is probably not even in the same country as the legitimate website.
Content-Injection Phishing describes the situation where hackers replace part of the content of a legitimate site with false content designed to mislead or misdirect the user into giving up their confidential information to the hacker. For example, hackers may insert malicious code to log user's credentials or an overlay which can secretly collect information and deliver it to the hacker's phishing server.
Man-in-the-Middle Phishing is harder to detect than many other forms of phishing. In these attacks hackers position themselves between the user and the legitimate website or system. They record the information being entered but continue to pass it on so that users' transactions are not affected. Later they can sell or use the information or credentials collected when the user is not active on the system.
Search Engine Phishing occurs when phishers create websites with attractive (often too attractive) sounding offers and have them indexed legitimately with search engines. Users find the sites in the normal course of searching for products or services and are fooled into giving up their information. For example, scammers have set up false banking sites offering lower credit costs or better interest rates than other banks. Victims who use these sites to save or make more from interest charges are encouraged to transfer existing accounts and deceived into giving up their details.
Bypass Two-factor authentication - 2FA Bypass
A majority of users and companies are moving to Two-factor authentication (2FA) for enhancing the security of its data and systems. But contrary to popular belief, it cannot provide a fool-proof layer of security to online accounts since Kevin Mitnick at KnowBe4 has demonstrated that it is very easy to deceive this defensive measure.
KnowBe4 is the world’s leading security awareness training provider and simulated phishing firm with a massive customer base of 17,000 organizations across the world. Mitnick is the company’s chief hacking officer.
In his new exploit, he proved that 2FA is exploitable because hackers can spoof the 2FA requests by sending a fake login page to the user. This may lead to stealing of sensitive user data including username, password and session cookie.
The hacking technique can be seen in the video uploaded here:
The purpose of using 2FA is to add an extra layer of security by combining what an employee already has and what they know. This combination could be between username and password or a code that is sent to the user on the phone or an app.
To exploit the 2FA method of security, the victim is lured into visiting a typo-squatting domain such as LunkedIn.com in order to steal the required user data. Once the information is obtained, the hacker can easily access the actual website and capture session cookie. Once this is achieved, the hacker can remain logged in indefinitely. But this is reliant on accessing the 2FA authentication code once.
As per the CEO of KnowBe4Stu Sjouwerman, Kuba Gretzy, a white hat hacker, and friend of Mitnick, developed a tool for bypassing the 2FA authentication via social engineering techniques and this tool can be “weaponized” for just about any website.
“Two-factor authentication is intended to be an extra layer of security, but in this instance, we clearly see that you can’t rely on it alone to protect your organization,” added Sjouwerman.
The tool is called evilginx. The attack method is based upon proxying the user via the hacker’s system through a credentials phishing technique, which requires the use of a typo-squatting domain. The idea is to let the user give away his/her credentials so that the hacker could steal session cookie.
The phishing email is the core of the attack method. In this particular case, the phishing email is supposedly sent by LinkedIn to a member of the site indicating that somebody is trying to contact through the social network. The email looks authentic initially but if looked closely, it becomes evident that it is a fake email since the return address is incorrect. But, if the user falls for it and clicks on the “interested” button, the malware will soon be downloaded onto the device.
This is the stage when the victim is taken to the authentic LinkedIn website so as to enter login information, which the hacker required. The login information is recorded by the malware as well as the session cookie using the cookie, the attacker acquires direct access to the account and manages to avoid the 2FA phase of the signing-in process.
Watch The Demonstration Here