CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Healthcare is a Top 3 Cyber Target
Attacks on the healthcare industry are on the rise as noted in a recent article published in CYBERSECOP. Healthcare providers of all sizes are subject to attack and in this case, CHRISTUS Health learned of “unauthorized access” likely similar to 254 ransomware incidents targeting patient care facilities between June 2020 and April 2022 worldwide. Patients are at risk, both their health and their PII where threat actors can alter and/or add to patient billings with no notice of impropriety. The true impact will be hard to discern until more time and data are collected but we know one thing for sure, the healthcare industry needs to take cybersecurity as seriously as they do patient care and follow their own advice; Plan, Prevent, Protect and Respond.
Plan – Get a Risk Assessment to identify and understand your cybersecurity vulnerabilities is one of the most critical steps as the awareness will lead to a prioritized remediation plan. Even a chink in the armor will have your patients, employees, and community concerned as a cyber-attack will likely affect critical operations because the prize is financial data, patient, and employee Personally Identifiable Information (PII).
Prevent - After an assessment is completed, you need a trusted and reliable security cyber organization to assist in leveraging the right framework and controls to be measured by such as HITURST, HITECH, HIPAA and PCI. These guidelines assist in defining the appropriate critical security controls for effective cyber defense. These efforts can be awareness training, policy creation & enforcement, and security controls as well as incident response readiness and governance. It’s a journey, not a sprint.
Protect – Within most remediation plans include investments in endpoint protection dark web monitoring and focusing on digital trust goals to ensure the technology investments already made as well as those in the future work in harmony. Like a Rubik’s cube, the goal is to have every facet of your organization in order, not just celebrating a single win. It is important to have a managed security partner to protect your patients, employees, devices, and data with monitored protection systems along with managed & encrypted backups with a Security Operations Center staffed with certified security professionals watching and engaging on your behalf 24x7x365.
Respond – Did you know that a threat actor will live in your ecosystem for an average of 121 days mining sensitive data, passwords, organization charts, and behaviors before acting? Nearly 95% of ransomware attacks are preventable so what starts as a threat becomes a technology issue, then a business risk issue, and eventually decision-making and communications issue at the board level. Do you pay the ransomware or not? Are we able to recover our data? Has the threat actor accessed our PII? And equally important is how do you keep from reaching this point again. Having an incident response assessment and plan might be the one thing you do if you don’t buy into everything else. You should receive an IT assessment of “how capable are we to thwart an attack?” and “how able are we to recover if breached?” Buying cyber insurance is not the silver bullet it used to be so having an incident partner who is proactively focused on your company’s sensitive data and reputation is paramount.
Not unlike a hospital, there are two main ways to address cyber security by coming through the Emergency Room or the front door proactively for testing; I recommend the latter. A proactive health check is the best step to understanding your ability to fight off an attack like a stress test. The results may drive adjustments in behavior and readiness, such as point endpoint detection, policy creation & enforcement, and security training. If you enter the ER, then don’t panic because you read this blog and signed up a reputable security partner to react & respond, including quarantining affected systems to prevent the ransom spread, resetting all passwords, checking your backups, activating your existing crisis/DR plans and negotiate with the threat actor if that is the best business decision communicating carefully along the way with detailed documentation. The moral of this story is that hope is not a strategy, so know your security scorecard and realize cyber readiness is a journey, not a sprint.
Author: Christopher Yula
Cybersecurity Risks in a Pandemic: What you need to know
The COVID-19 pandemic has alerted many organizations to gaps in their information security infrastructure heretofore unrealized. Most of these deficiencies have been revealed as a direct outcome of the shift from a workforce-in-place physical environment centered around a fixed and determinable worksite location to a distributed, unstructured environment where most employees and individuals are working remotely.
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations.
The lack of a centralized workspace raises a multiplicity of information security concerns, including but not limited to the following:
1. Does the company have an established Work-From-Home (WFH) information security policy, and if not, how is remote worker security managed?
2. Are employees adequately trained to work remotely, and do they have the appropriate tools at their disposal to ensure the preservation of the security environment?
3. How does the organization manage mobile device and laptop security, including encryption?
4. Control and testing of the commercial VPN?
5. Does the organization maintain a comprehensive data loss protection policy?
6. How, if at all does the organization address data loss protection?
7. Does the organization have a breach response plan for mobile and remote WFH employees?
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations. Our skilled team of information security professionals can provide a comprehensive assessment of your information security framework and suggest remediation and complementary additions to your existing framework, as the case may be.
There are several things to consider if and when the time comes for firms to return to the office. CyberSecOp recommends:
Third-Party network risk assessment
Operational Responses to Security Incidents
Work from Home Security
Virtual Meeting Applications
Updates and Patches
A full virus scan on workstations returning to the office
Full Windows/Mac updates
Review Wi-Fi connections on returning devices: Some people may come back and still connect to Optimum Wi-Fi (This can be very risky)
Delete any accounts not for company use
Provisioning devices employees may have bought in haste (Hardening AV adding to the domain)
Mobile device management strategy for new mobiles, or devices that employees are using more
Pandemic Policy, Cybersecurity Policy Wireless policy
It is important for organizations to foresee possible consequences transitioning from working remotely to returning to the office. CyberSecOp can help facilitate this transition.
AUTHOR: Michael Young
Phishing Attack Prevention: What is Phishing?
What is Phishing?
Phishing is the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about to protect themselves.
Phishing Attack Prevention:
Why are so many companies vulnerable to phishing? Not having the right tools in place and failing to train employees on their role in information security.
Employees possess credentials and overall knowledge that is critical to the success of a breach of the company's security. One of how an intruder obtains this protected information is via phishing. The purpose of phishing is to collect sensitive information to use that information to gain access to otherwise protected data, networks, etc. A phisher's success is contingent upon establishing trust with its victims. We live in a digital age, and gathering information has become much easier as we are well beyond the dumpster diving days.
How do I protect against phishing attacks?
Free Email Protection
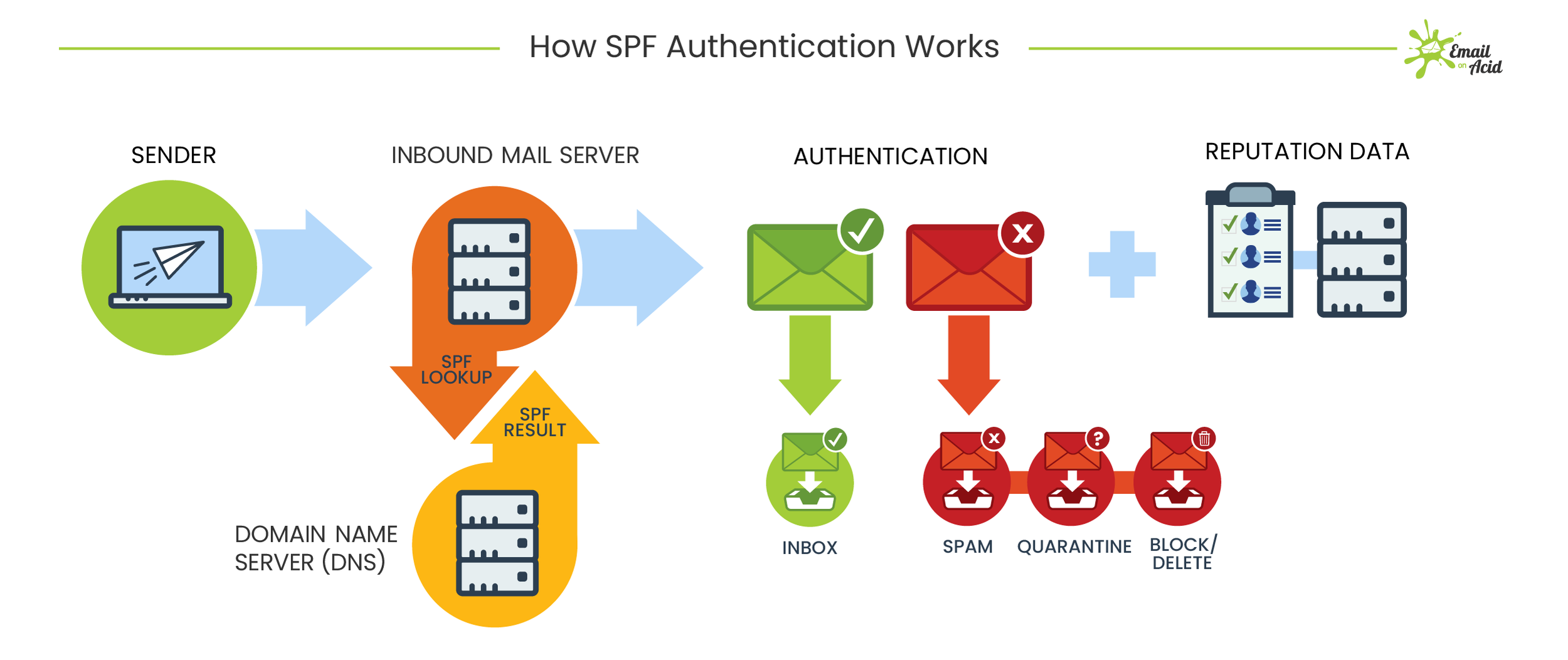
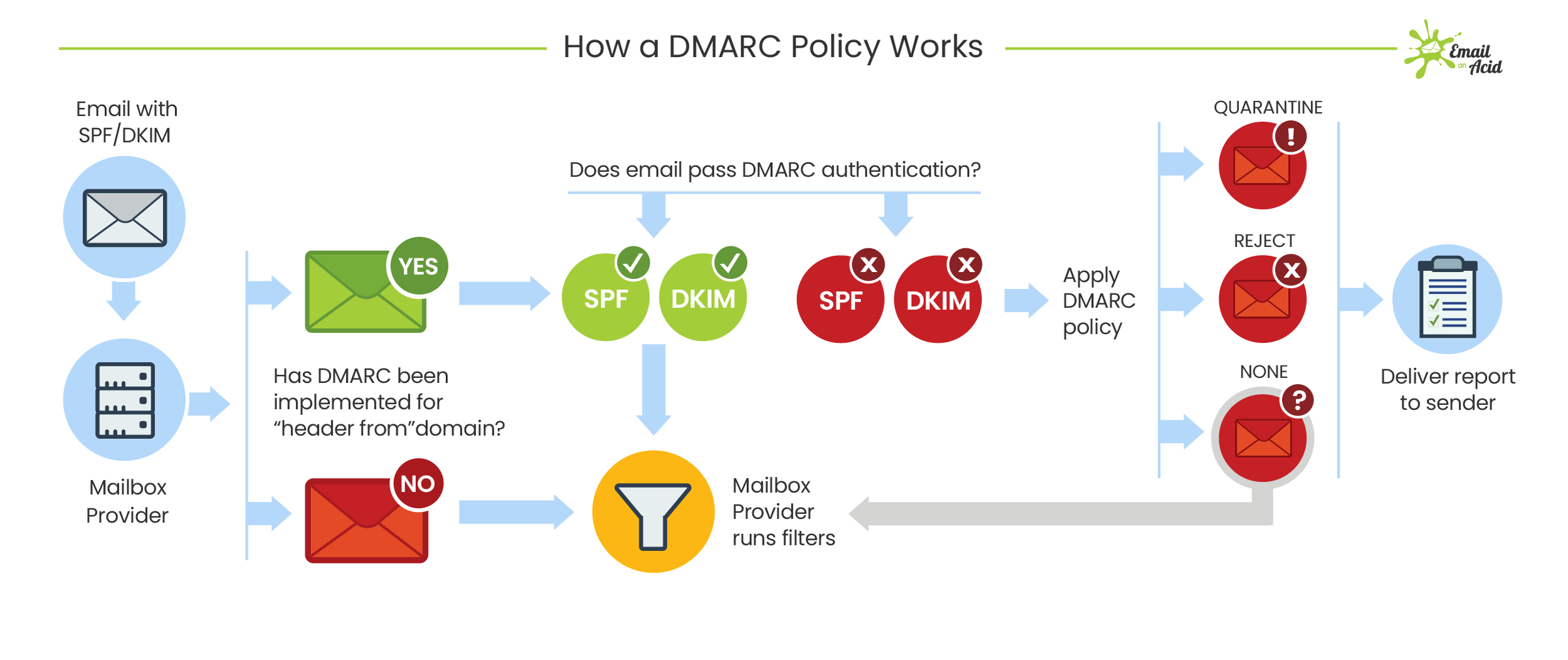
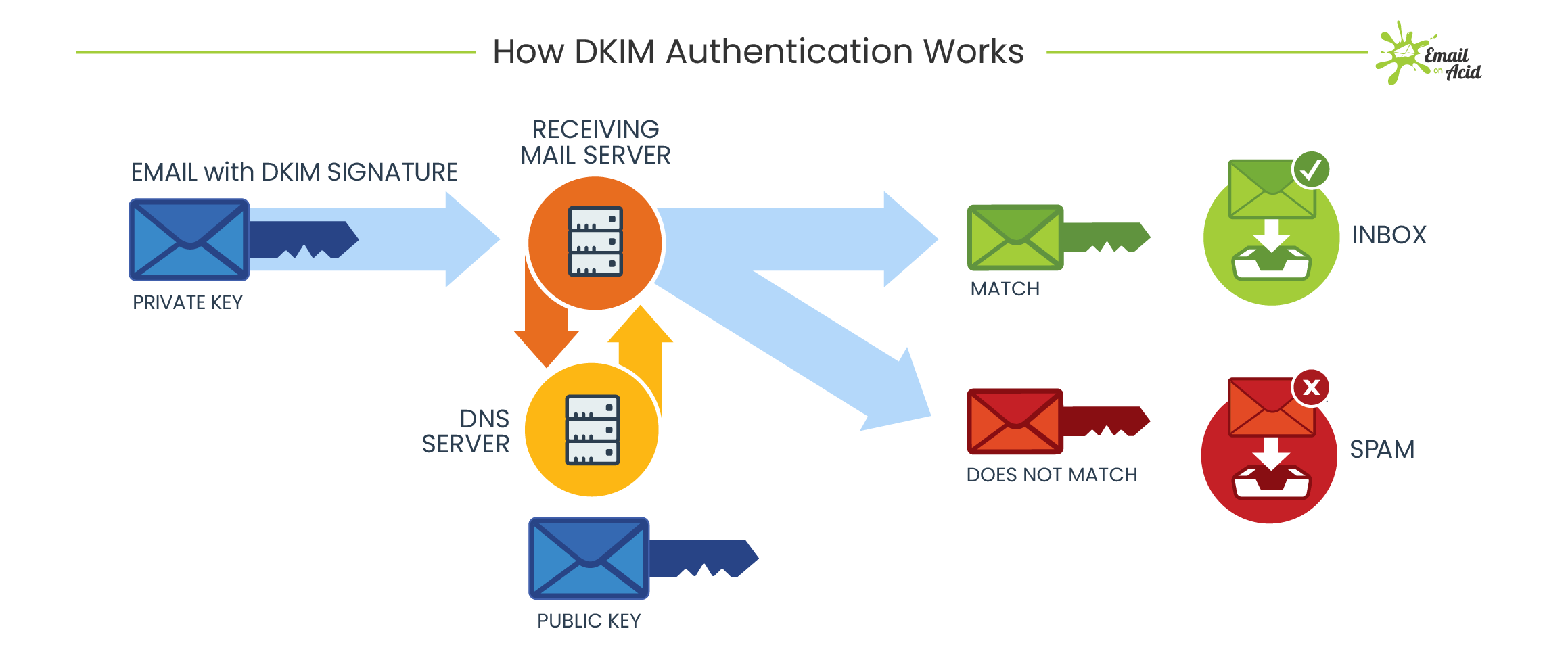
Free protocols that help organizations improve email security; Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM) were developed. SPF cross-checks the sender’s IP address with an approved list of IP addresses, and DKIM uses an encrypted digital signature to protect emails. While these are both individually effective, they have their own set of flaws. DMARC, developed in 2012, is a protocol that uses both SPF and DKIM authentication to secure email and has a mechanism that sends the domain owner a report whenever an email fails DMARC validation.
But here’s the thing: a recent report from phishing specialist Agari states that only 1/3 of the Fortune 500 have configured DMARC.
User education
One way to protect your organization from phishing is user education. Education should involve all employees. High-level executives are often a target. Teach them how to recognize a phishing email and what to do when they receive one. Simulation exercises are also key for assessing how your employees react to a staged phishing attack.
Security technology
No single cybersecurity technology can prevent phishing attacks. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control.
How does phishing work?
Phishing starts with a fraudulent email or other communication that is designed to lure a victim. The message is made to look as though it comes from a trusted sender. If it fools the victim, he or she is coaxed into providing confidential information, often on a scam website. Sometimes malware is also downloaded onto the target’s computer.
What are the dangers of phishing attacks?
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing.
Types of Phishing
Deceptive Phishing. The term "phishing" originally referred to account theft using instant messaging but the most common broadcast method today is a deceptive email message. Messages about the need to verify account information, system failure requiring users to re-enter their information, fictitious account charges, undesirable account changes, new free services requiring quick action, and many other scams are broadcast to a wide group of recipients with the hope that the unwary will respond by clicking a link to or signing onto a bogus site where their confidential information can be collected.
Malware-Based Phishing refers to scams that involve running malicious software on users' PCs. Malware can be introduced as an email attachment, as a downloadable file from a web site, or by exploiting known security vulnerabilities--a particular issue for small and medium businesses (SMBs) who are not always able to keep their software applications up to date.
Keyloggers and Screenloggers are particular varieties of malware that track keyboard input and send relevant information to the hacker via the Internet. They can embed themselves into users' browsers as small utility programs known as helper objects that run automatically when the browser is started as well as into system files as device drivers or screen monitors.
Session Hijacking describes an attack where users' activities are monitored until they sign in to a target account or transaction and establish their bona fide credentials. At that point the malicious software takes over and can undertake unauthorized actions, such as transferring funds, without the user's knowledge.
Web Trojans pop up invisibly when users are attempting to log in. They collect the user's credentials locally and transmit them to the phisher.
Hosts File Poisoning. When a user types a URL to visit a website it must first be translated into an IP address before it's transmitted over the Internet. The majority of SMB users' PCs running a Microsoft Windows operating system first look up these "host names" in their "hosts" file before undertaking a Domain Name System (DNS) lookup. By "poisoning" the hosts file, hackers have a bogus address transmitted,taking the user unwittingly to a fake "look alike" website where their information can be stolen.
System Reconfiguration Attacks modify settings on a user's PC for malicious purposes. For example: URLs in a favorites file might be modified to direct users to look alike websites. For example: a bank website URL may be changed from "bankofabc.com" to "bancofabc.com".
Data Theft. Unsecured PCs often contain subsets of sensitive information stored elsewhere on secured servers. Certainly PCs are used to access such servers and can be more easily compromised. Data theft is a widely used approach to business espionage. By stealing confidential communications, design documents, legal opinions, employee related records, etc., thieves profit from selling to those who may want to embarrass or cause economic damage or to competitors.
DNS-Based Phishing ("Pharming"). Pharming is the term given to hosts file modification or Domain Name System (DNS)-based phishing. With a pharming scheme, hackers tamper with a company's hosts files or domain name system so that requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site. The result: users are unaware that the website where they are entering confidential information is controlled by hackers and is probably not even in the same country as the legitimate website.
Content-Injection Phishing describes the situation where hackers replace part of the content of a legitimate site with false content designed to mislead or misdirect the user into giving up their confidential information to the hacker. For example, hackers may insert malicious code to log user's credentials or an overlay which can secretly collect information and deliver it to the hacker's phishing server.
Man-in-the-Middle Phishing is harder to detect than many other forms of phishing. In these attacks hackers position themselves between the user and the legitimate website or system. They record the information being entered but continue to pass it on so that users' transactions are not affected. Later they can sell or use the information or credentials collected when the user is not active on the system.
Search Engine Phishing occurs when phishers create websites with attractive (often too attractive) sounding offers and have them indexed legitimately with search engines. Users find the sites in the normal course of searching for products or services and are fooled into giving up their information. For example, scammers have set up false banking sites offering lower credit costs or better interest rates than other banks. Victims who use these sites to save or make more from interest charges are encouraged to transfer existing accounts and deceived into giving up their details.
CEOs and Cyber Security: are they the road block?
CEOs and cybersecurity: are they the road block?
Senior executives may be the weakest link in the corporate cyber security chain and are a primary target of hackers, fraud and phishing scams, says report. it also should be know that the are the road block to approve budget for information security, and most often security takes back sit to profit.
Report by many source and research done by many firm identity senior executive has the road block to good security within their firms, Many CEOs think they are immune to hackers, at least that’s what a new report According to the report, these findings are ironic given that CEOs are the ideal victim.
Senior Executive Are You the Weakest Link?
According to the report, Are You the Weakest Link? How Senior Executives Can Avoid Breaking the Cybersecurity Chain, many senior executives ignore the threat from hackers and cyber criminals and often feel that security policies in their respective organisations do not apply to their unique position.
In reality, their often privileged access to company information makes their personal accounts extremely valuable to exploit and heightens the need for extra care.
Professional hackers and adversaries will usually do a thorough investigation into a senior executive or board level director, including full analysis which could entail in-depth monitoring of the company website and associated social media accounts (including employees and their extended networks).
It appears that many CEOs commonly view cyber security as a responsibility for the IT department only. In reality, IT security has now become a remit for all individuals.
“All employees — especially those at the top of the corporate ladder — need to realise that cybercriminals use social engineering, email phishing and malware to access personal accounts, and C-level staff especially need to avoid becoming the weakest link in the cybersecurity chain by adhering to regularly updated, company-wide security policies regarding data sharing and backup,”
“Reviewing corporate policies, with a focus on people, premises, processes, systems and suppliers will provide valuable insights into which areas to improve, and by championing a ‘security first’ corporate culture, organisations and their senior executives will be well positioned to avoid the high financial costs, reputation damage and unexpected downtime that could result from a cyberattack or data breach.”
Cyber Insurance - Is a must have - you will need it
Cyber Insurance - Is a must have - you will need it.
It’s every healthcare organization’s nightmare to get the call that their data has been breached or hacked. As a result, many have turned to cyber insurance to protect assets and business operations.
As cyber policies and carriers lack a universal policy, there’s an even greater worst case scenario: An organization is breached, and the policy doesn’t cover what the leaders thought it did. Now, not only is the healthcare provider strapped with the burden of the breach, it wasted money on a useless cyber insurance policy.
To get a better grasp on how to choose the right policy, Healthcare IT News asked attorney Matthew Fisher, partner with Mirick O’Connell, and Jane Harper, Henry Ford Health System’s director of privacy and security risk management, to outline the biggest policy mistakes -- and how to avoid them.
Mistake #1: Rushing the process
When buying a policy, a carrier will provide a questionnaire that will evaluate your organization’s security posture, program, tools and policies. The biggest mistake is to rush the pre-policy process to see the rates and what the carrier will cover, explained Fisher.
Organizations need to be conservative with how they answer the questions, as “it could be a ground for denial, if you don’t have the policies you said you have in place,” said Fisher. “You have to make sure you’re not unintentionally misleading the insurance company when it comes to coverage.”
Often these questionnaires attempt to create a black and white policy and “it can be tough to answer correctly,” explained Fisher.
“Your ability to be as transparent and truthful upfront is critical to the nonpayment discussion,” said Harper. “If you tell the insurance company that you have everything in place and are compliant, if you tell them that and then you have an issue, and you weren’t truthful, it ends up being a legal battle.”
“When you submit your checklist that they have you fill out, meet with the underwriter to make sure you understand what you’ve documented,” she added. “You also need the copy that was provided to the insurance company because it will come back into play when you submit the final documents.”
For example, if you say you have a specific control in place, and you actually don’t, Harper explained that can create a situation where “they thought they had an understanding of something, but they didn’t.”
“Be honest, transparent and accurate -- because they can deny your policy if you were inaccurate or misleading in your responses,” she said.
Mistake #2: Lax, incomplete risk assessment
It’s easier to prevent a misleading or false statement to an underwriter, when an organization has a strong assessment and inventory of the processes and tools on the system. But far too often, hospitals “don’t know everything about the control environment,” explained Harper.
“When you talk about protecting an system and preventing a cyber incident, you have to have a good understanding of the organization’s overall control environment,” Harper said. “It’s key, as the longer it takes you to identify that you’ve had an incident, it leads to more exposure and the longer it takes to recover.”
But it’s also important to remember to update this inventory or assessment when buying new tools, merging with other organizations, hiring new staff and the like, Harper explained.
“Think about all of the activities and operations that happen,” she said. “And every three years, you’re updating a cybersecurity checklist -- that may not be frequent enough.”
For example, Harper explained that an organization filling out the policy questionnaire may have all of the right elements in place. But if another tool was purchased and the controls weren’t updated or the control was removed and the underwriter was not notified, there could be a problem.
“If those controls played into how the underwriter rated you: that can be key,” said Harper. “Think about your own home: you get additional discounts when you have a burglar alarm. So if you get one, and let them know, you may get a lower rate… But if you no longer have that control, you have to tell the carrier.”
“It’s the same kind of practice that we want to get into when we get into cyber insurance for our organization,” she added.
Mistake #3: Failing to involve the right people
Many organizations understand that security needs to exist outside of the IT team. In the same vein, it’s crucial when buying a cyber insurance policy that the same mentality is applied to make sure all of your bases are covered.
“Make sure you are talking to the right individuals,” Harper said. “The appropriate key stakeholders are not only involved with the evaluation process - how many patients, how much data, etc. -- but also the responses to the questions the policy is going to ask.”
“Risk folks typically talk about it as it relates to patients,” she continued. “Those folks are key, but in addition, you need your privacy and security risk professionals, security officers, IT leader, your key business leaders/owners and those driving the data. It’s key.”
Also crucial? Making sure the facilities team is involved, as there can sometimes be a cyber incident based on a physical issue. Harper explained that “often people tend to focus on things like electronic PHI, but there’s physical PHI. If there’s a break in at a warehouse and data is stolen, OCR considers that a breach.”
Mistake #4: Failing to understand coverage
Far too often organizations make large assumptions as to just what cyber insurance will cover. Fisher explained that these leaders are often shocked to learn that they did not receive the full spectrum of coverage they wanted.
“Relying on blind faith on those terms, or what the broker or agent is telling you is a major mistake,” said Fisher. “It’s always up to up to you to go into something with eyes fully wide open to make sure you know what you’re actually buying.”
Harper took it a step further and laid to rest a common misconception when it comes to coverage: “Insurance will not cover fines and penalties associated with noncompliance. If you’re not complaint, and you didn’t do risk assessments, cyber insurance won’t protect you from that, so don’t expect it.”
Cyber security IT skills in-demand in US
There’s no doubt that demand for the technologically skilled will only increase in the upcoming years, as practically every company becomes a software-driven enterprise. A survey by the jobs site Monster found that in the US, jobs in the digital sector have multiplied at more than twice the rate of other non-digital tech sectors, and are predicted to grow by 20% in the next decade.
However, which skills will be particularly in demand? While it’s unlikely that the IT skills demanded by the jobs market today will become redundant within our lifetimes, the field is constantly evolving, and there are certainly growth areas on the horizon that IT professionals would do well to educate themselves in.
Cyber security
Cyber security is an area set to grow exponentially in importance in the upcoming years. Every time a breach is suffered by an organisation, there is a huge cost both in terms of financial loss and loss of reputation and brand value.
A recent study carried out by jobs site Indeed indicated that the US is dangerously short on cyber security skills and that the number of cyber security jobs advertised in the US is the third highest globally, meaning demand exceeded candidate interest by more than three times.
Development
Demand for skills in development is here to stay (for the time being anyway – this could change as soon as AI is more widely used to code). In 2017, the demand for software developers and engineers increased by 13% in the UK.
Devops
Another important area of growth is the trend for companies to take a devops approach to their IT departments, meaning that developers well versed in this outlook will be the most employable.
Cloud computing
It’s widely recognised that cloud computing is the future, and every IT professional should feel comfortable using these systems. Demand for cloud infrastructure specialists is increasing across the board.
Machine Learning and AI
These are two obvious areas of increasing growth. In the US, demand for AI jobs increased threefold between 2015 and 2018, even surpassing the UK in terms of demand.
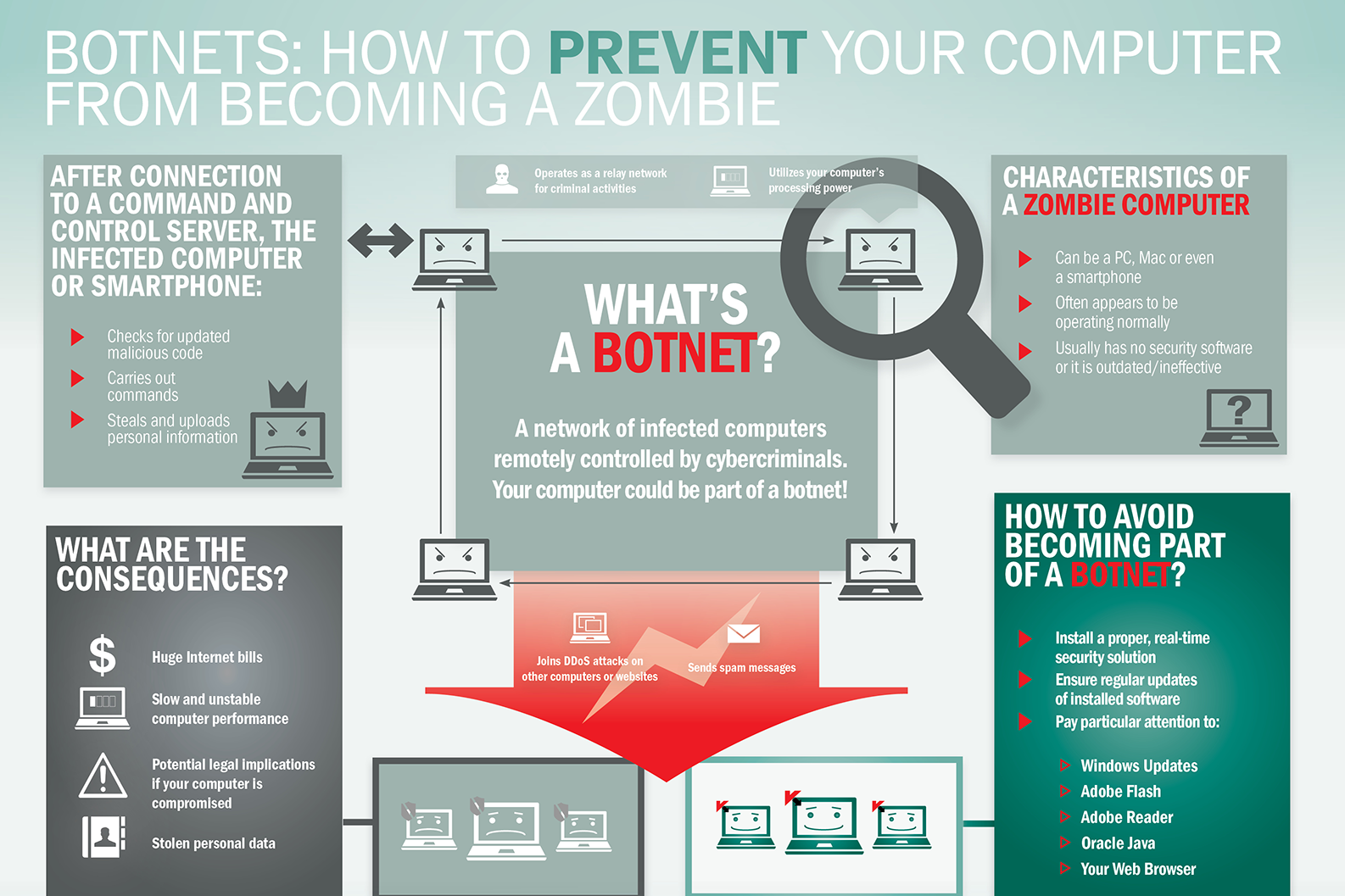
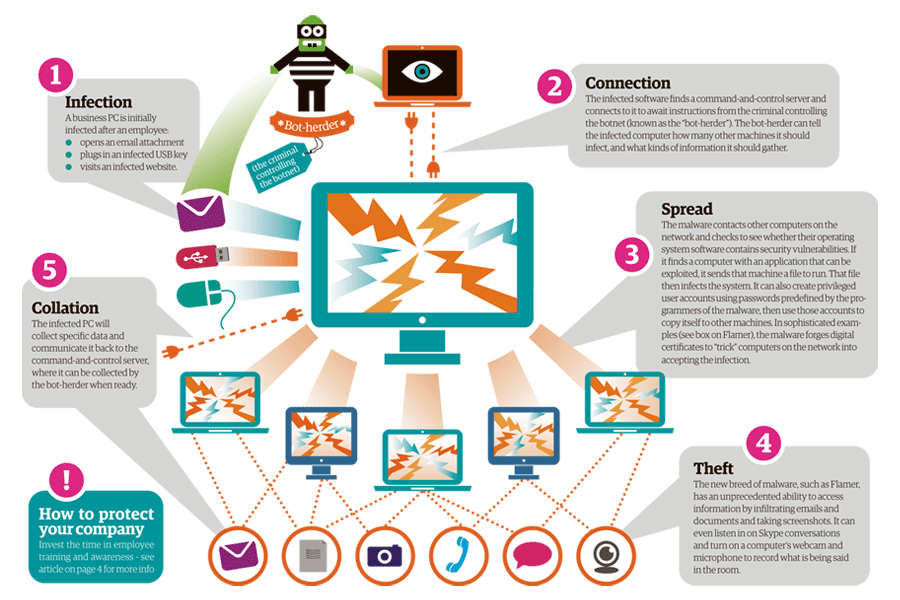
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
Small Business Benefits from Cybersecurity Consulting Services
Cybersecurity news stories are becoming more and more prevalent, especially over the last few years. Whether the stories are about stolen emails or huge data breaches, it has been virtually impossible to ignore them.
While the major stories about compromised corporations and hacked email accounts make the news, cybersecurity is something that concerns everyone who uses a computer. Even small business owners can become victims of cybercrime. In fact, small business owners, in particular, need to be concerned with cybersecurity so they can protect their intellectual property. No matter whether the intellectual property is research or recipes, it is one of the greatest assets a small business has. Intellectual property is a prime target for hackers, whether they are stealing information for a competitor or running a ransomware scheme where a hacker demands something in return for the stolen information.
The trouble is that protecting that intellectual property and keeping other sensitive information, such as client and customer data, isn’t cheap. Many small business owners may not have the available capital to afford a cybersecurity system. Although this puts an owner in a tough spot, you can’t put a price on peace of mind, and neither can a small business owner afford the losses associated with becoming the victim of a cybercrime.
As with most things for small-business owners, cybersecurity comes down to a cost analysis. A cybersecurity system can be a big expense. On the other hand, a small business owner has to consider the cost of not having their systems protected from hackers. It’s hard enough for a large corporation to recover from a cyber attack, even with all the resources and infrastructure they have. According to the U.S. National Cyber Security Alliance, 60 percent of small businesses fold within six months of a cyber attack.
Ultimately, each business owner has to decide if and when a formal data security protection plan is necessary. A consultation with an expert may help you better weigh the pros and cons of taking on this type of business expense. Start with this list of Cybersecurity Consulting Providers as a jumping off point for your research. After comparing the benefits of these companies’ plans, set up a few consultations to see if and how these providers can best help protect your business, and what it costs to do so. You may find that it’s worth the investment.