CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
What is Cyber resilience?
Cyber resilience is the ability of an organization to withstand and recover from cyber attacks and other cybersecurity threats. It involves implementing measures to prevent cyber attacks, as well as having the necessary systems and processes in place to minimize the impact of a successful attack and to quickly recover from it.
There are several components of cyber resilience, including:
Risk assessment: Identifying and assessing potential vulnerabilities and threats to an organization's systems and data.
Prevention: Implementing measures to prevent cyber attacks, such as using strong passwords and enabling two-factor authentication.
Detection: Implementing systems and processes to detect potential cyber attacks in progress.
Response: Having a plan in place to respond to a cyber attack, including procedures for containing the attack and minimizing its impact.
Recovery: Having systems and processes in place to recover from a cyber attack, including data backup and recovery systems.
By building cyber resilience, organizations can protect themselves from cyber attacks and minimize the impact of successful attacks, enabling them to continue operating in the face of these threats.
Zero trust Cyber resilience
Zero trust is a cybersecurity approach that assumes that all actors, whether inside or outside an organization, are potentially untrustworthy and must be continuously authenticated and authorized before being granted access to resources. It is based on the idea that an organization should not trust any user or device, regardless of their location or whether they are inside or outside the organization's network.
The zero trust approach can be used to enhance cyber resilience by requiring all users and devices to be authenticated and authorized before they are granted access to resources. This can help to prevent unauthorized access to sensitive information and systems, and can also help to minimize the impact of a successful cyber attack.
To implement a zero trust approach, organizations typically use a combination of technologies, including multi-factor authentication, network segmentation, and access controls. These technologies help to ensure that only authorized users and devices are granted access to resources, and can help to prevent unauthorized access or the spread of malware within an organization.
By adopting a zero trust approach, organizations can significantly enhance their cyber resilience and reduce their risk of suffering a cyber attack.
zero trust cyber resilience technologies
There are several technologies that can be used to implement a zero trust approach and enhance cyber resilience. Some examples include:
Multi-factor authentication: This requires users to provide multiple forms of authentication, such as a password and a security token, before they are granted access to resources.
Network segmentation: This involves dividing an organization's network into smaller, isolated segments, which can help to prevent the spread of malware or unauthorized access within the network.
Access controls: This involves implementing controls to ensure that only authorized users and devices are granted access to specific resources.
Identity and access management (IAM) systems: These systems help to manage and secure user access to resources by controlling who is allowed to access specific resources and under what conditions.
Security information and event management (SIEM) systems collect and analyze security-related data from multiple sources, such as firewall logs and intrusion detection systems, to help organizations detect and respond to potential threats.
By using these technologies, organizations can implement a zero-trust approach and enhance their cyber resilience by preventing unauthorized access to sensitive information and systems and minimizing the impact of successful cyber attacks.
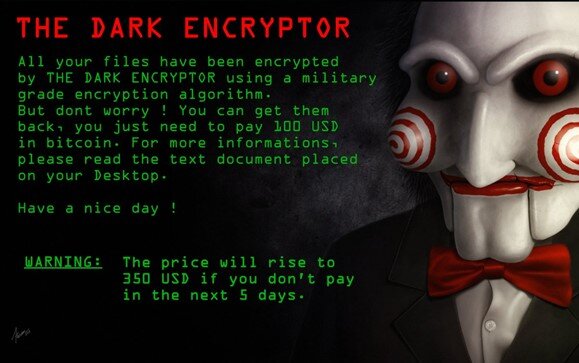
Three Reasons Why You Need an Incident Response Solution
Imagine the following scenario: you arrive early to work in the morning, plop down at your desk with coffee in hand, and log in to your computer. You’re excited to start working on a big project, but first you are greeted with this message:
Quickly, you dash over to a colleagues’ desk. They too, have the same message on their desk. You try dialing your IT department, but they don’t start until normal business hours.
What do you do? Where do you even start?
It’s easy to think that the above scenario would never happen to you. In reality, a 2020 survey of 600 businesses in the United States revealed that a staggering 78% had been infected with ransomware that year. The average cost of recovering from a ransomware attack has spiked to $1.85 million in 2021!
Ransomware isn’t the only threat to your business continuity. In February 2021, the state of Texas suffered massive power outages due to a severe winter storm. At least 151 people died as a result. Property damage has been estimated at more than $195 billion.
What do these scenarios have in common? They demonstrate the need to prepare for the worst; this is the essence of Incident Response.
What is Incident Response anyway?
Every organization needs to have an Incident Response Plan (IRP). The team that executes the IRP is the Computer Incident Response Team (CIRT). The most important feature of both the IRP and CIRT is that they are clearly defined before the incident takes place! Disaster recovery is hardest when preparation is lacking.
The Incident Response Plan details who does what if an incident does happen. This can include using alternate systems, notifying stakeholders, or restoring from backups.
Perhaps the most important part of the Incident Response Plan is the postmortem. Now that you’ve recovered, what will you do in order to ensure that attackers won’t attack again using the exact same methods? The Incident Response Team will identify what door the attackers used to get in and make sure it stays shut.
Why do I need Incident Response?
I’m so glad you asked. Here’s three reasons why you need Incident Response for your organization:
1. The probability of an incident has never been higher.
Ransomware is pervasive. At this point, we need to ask ourselves not “will I get breached?” but “when will I get breached?”
A proper defense has multiple layers. Having a fence around your house is nice, but you’ll still have homeowners’ insurance. Incident Response is a way to mitigate the risks of ransomware that we can’t avoid.
2. The cost of an incident has never been higher.
How much would it cost to replace your entire infrastructure? The nasty aspect of ransomware is that, in some cases, the only way to ensure that the attackers have been completely removed from your environment is to start from scratch. This means replacing every workstation and server in your organization.
Sometimes, there simply isn’t a price to pay; there may not even be new hardware available to purchase with a global silicon chip shortage.
3. You can’t afford not to.
Every business owes itself to do a risk analysis of a ransomware attack. What would be the cost of not doing business for an hour? A day? A week? You will find that incident response is a necessary piece of the plan for protecting your assets and business continuity.
CyberSecOp is a leader in the Incident Response field. CyberSecOp consultants are cyber incident response subject matter experts who have collaborated on numerous security projects and operational improvement initiatives. We will support your security operational activities by helping to develop an incident response plan and work with your IT team to mitigate any potential risk. Our teams will create investigative processes and playbooks. In addition, we will be responsible for continuously identifying gaps and managing the improvements in the security response process, technologies, and monitoring. Working closely with internal architecture, engineering, and project management teams will ensure cyber-defense requirements are identified and communicated early in the project life cycle.
Security incident response services with CyberSecOp
Support cyber incident response actions to ensure proper assessment, containment, mitigation, and documentation
Support cyber investigations for large- and small-scale security incident breaches
Review and analyze cyber threats and provide SME support
Interact and assist other investigative teams within on time sensitive, critical investigations
Participate as part of a close team of technical specialists on coordinated responses and subsequent remediation of security incidents
Manage the security monitoring enrollment process to ensure adequate coverage and effectiveness of all new and existing cloud- and on-premise-based applications, services and platforms
Maintain detailed tracking plan of all internal/external enrollment outcomes/recommendations and provide support through to implementation
Act as a liaison between cyber-defense, engineering, security architecture, network & system operations, and functional project teams to ensure effective project implementation that meets incident response requirements
Define baseline security monitoring requirements for all new projects, services, and applications joining your organization's network
Facilitate the development and tuning of SIEM rules to support enrollments and ensure high fidelity alerting
Don’t delay in ensuring that your business can survive any threat. Join CyberSecOp on your journey towards a safe and protected future.
Author: Josh Cabrera
What is a Zero Trust Security Architecture?
What is Zero Trust Security?
Zero Trust Security, also referred to as Zero Trust Networks or Zero Trust Architecture, is a security concept with one basic principle: don’t automatically trust anything to access your data, whether it’s connecting from outside your organization or within. Implementing Zero Trust involves various technologies, policies, and processes that help you better respond to the sophisticated approaches cybercriminals are using to gain access to sensitive data.
CyberSecOp’s Zero Trust Security service offers a comprehensive solution to secure all access to your applications and environment from any user, device, and location. Zero trust is a security model based on maintaining strict access controls.
With the recent and very public surge of cyber incidents affecting businesses and critical infrastructure, you may have heard the phrase ‘Zero Trust’ regarding cyber security and protecting business assets. So what is Zero Trust? Put Zero Trust is a model of thought that centers around never trusting any device, application, or person, regardless of whether they are attempting to connect from inside or outside the network. This methodology is gaining more and more traction as cloud application usage increases and the permanent shift to remote work is further implemented.
Zero trust is a strategy where everything (People, Data, Sessions, Devices, Applications) is treated as suspicious regardless of whether it's inside or outside the network. Essentially it is a ‘default deny’ posture, even for users within the organization. Instead of ‘Trust, verify the organization ‘Never Trusts, Always Verify.’ This is not accomplished by one tool but rather by policy, procedure, and means. Zero trust also focuses on Least Privilege- a Methodology that states no user should have more rights and permissions than what is needed to perform their work.
Zero Trust focuses on 5 pillars
1. Device Trust
2. User Trust
3. Transport and Session Trust
4. Application Trust
5. Data Trust
CyberSecOp can transform your business into a Zero Trust model by focusing on the tools, policy, and procedures to protect these five pillars and substantially decrease the odds of a successful breach.
ZERO TRUST SERVICES & ZERO TRUST PLATFORM
OVERVIEW: MANAGED SECURITY - MDR SERVICES - MANAGED COMPLIANCE
With Zero Trust network access for your private apps and systems, you no longer have to choose between user experience and security. CyberSecOp Managed Zero Trust services were built with a new approach that directly creates zero trust connections between the users and the applications to solve this unique challenge. As a scalable, cloud-native platform, it enables digital transformation by securely connecting users, devices, and applications anywhere without relying on network-wide access. This platform is delivered by five key architecture attributes unique to the CyberSecOp Managed Zero Trust services. Together, they enable organizations to provide strong security and a great user experience to their employees and customers.
ZERO TRUST SECURITY SOLUTION & SERVICES
When all employees have the same access privileges, the network is vulnerable. VPNs may provide adequate security for on-premise resources, but only Zero Trust solutions offer the user-based access rules required for proper cloud security.
Our Zero Trust solutions and services utilize multi-layered cybersecurity protection to transform your business with cybersecurity orchestration, automation, cybersecurity consulting, cloud, and managed security services. We implement a comprehensive approach to secure and protect businesses from cyber threats. Our cybersecurity services cover all the following areas needed for a zero-trust secure environment: Cybersecurity Program Strategy, Risk Management, Risk Assessment, Threat Intelligence, Incident Response, Advanced Malware & Ransomware Protection, Perimeter Security, Application Assessment, & Security Monitoring Services. We know where you are and how to protect your organization with a cybersecurity gap analysis to identify a more precise road map and a more robust cybersecurity program.
Zero Trust Cybersecurity Benefits and More
Zero trust networks, of course, extend beyond security. They are also inherently agile, a vital benefit for an increasingly remote workforce. As massive remote crews put unprecedented strain on cloud resources, the more stability and resilience you can build into your architecture, the better. Rather than backhauling remote data to a static data center, zero trust applications connect directly into your network from outside the perimeter, which helps free up bandwidth for DevOps and access business-critical cloud services.
ADOPT OUR ZERO TRUST SECURITY MODEL DEFENSE APPROACH
AUTOMATED PKI LIFECYCLE MANAGEMENT ZERO TRUST
The automated PKI lifecycle management platform enables Zero Trust by utilizing Public Key Infrastructure (PKI) certificates and key pairs, strengthening digital identities, and securing the connections between entities beyond the firewalled network architecture. In this age of digital transformation, the Zero Trust model increases the need for a consolidated, automated, and modern approach to PKI.
SECURE INTERNET GATEWAY
Control desktop, laptop, and mobile device access to malicious and inappropriate websites.
SECURE WEB GATEWAY
Protect against every kind of threat and ensure strict compliance with policies without slowing down your users.
ANTI SPAM & EMAIL GATEWAY
Secure Email Gateway protects organizations and employees from spear-phishing, malware, spam, and zero-day attacks. To ensure zero trust by removing spam and malicious email traffic before it enters your network to ensure zero trust.
ADVANCED ENDPOINT PROTECTION
Secure all your servers, desktops, laptops, and mobile devices from known and unknown malware–without requiring signatures or updates.
WEB APPLICATION FIREWALL
Powerful, real-time edge protection for
web apps and websites providing advanced
filtering, security, and intrusion protection.
SIMPLIFY COMPLIANCE REPORTING
Meet compliance requirements with no extra work. CyberSecOp Consultants have you covered, delivering streamlined reports of system access across the organization and zero trust technologies.
CYBER SECURITY OPERATIONS CENTER
Your always-on certified cybersecurity professionals team provides 24/7/365 surveillance and remediation services to ensure zero trust.
DATA LOSS PREVENTION
Monitor and control the movement of sensitive and confidential data across the network. Implement a ‘zero-trust’ data loss prevention (DLP) strategy utilizing activity, system-access, schedule, and content-based rules to ensure zero trust.
SINGLE SIGN-ON
A secure cloud single sign-on solution that IT, security, and users will love. Single sign-on solutions can quickly connect to and sync from identity stores including AD, LDAP, HR systems, and other third-party identity providers to ensure zero trust.
MULTI-FACTOR AUTHENTICATION
Secure, intelligent access to delight your workforce and customers. Secure your accounts and apps with a robust multi-factor authentication solution to keep the right people in and the wrong people out. Protect all your resources, including customer-facing and enterprise apps that store your most sensitive data to ensure zero trust.
SECURITY INCIDENT EVENT MANAGEMENT
We are providing actionable intelligence leveraging current events and data. Our SIEM collects logs and circumstances of the network traffic and web assets, security devices, operating systems, applications, and databases and reviews the vulnerabilities using artificial intelligence to process to ensure zero trust.
REMOTE MONITORING AND MANAGEMENT
Remote Monitoring and Management (RMM) is remote monitoring software that allows you to remotely monitor and manage endpoints, computers, mobile devices, and networks from a centralized console to ensure zero trust.
MANAGED CYBERSECURITY SERVICES
CyberSecOp is a cybersecurity service provider offering a range of solutions related to protecting computer systems within an organization. Cybersecurity is a constantly evolving industry created in response to hacking, viruses, and other personal and business data threats. CyberSecOp-managed cybersecurity services will provide your business with expertise in the three stages of business cybersecurity protection services: assessment, security program implementation, and governance. We implement external and internal cybersecurity solutions with advanced IT security software and hardware solutions. CyberSecOp provides several cybersecurity tools to ensure end-to-end cybersecurity protection. We also offer IT outsourcing services to address your company’s information technology needs.
End to End Cybersecurity Services
We offer cybersecurity and strategic advisory consulting, incident response, design, and deployment services. We will implement a security program strategy to align information security policy, security controls, and plan with business goals.
LEADING MANAGED CYBERSECURITY SERVICE PROVIDER
CyberSecOp is a leader in managed cybersecurity services. Our cybersecurity team will implement a secure framework and constantly monitor and protect your business from cyber threats. Our cybersecurity experts integrate business context intelligence, threat data, and cybersecurity insights to protect your assets and data. The risk scene develops with rising rates; it takes more oversight with cybersecurity services to effectively ensure your organization is secure from cyber threats. Our team will work with your firm to identify any risks or threats it may face. We will deliver recommendations highlighting security flaws in your environment and the immediate steps to these issues.
CYBERSECURITY AS A SERVICE (CSAAS)
CyberSecOp offers proactive Cybersecurity as a Service (CSaaS) to mitigate cyber risk. Every business needs defense in-depth, includincludessecurity solutions and cybersecurity experts who can deploy and monitor them.
Transform and strengthen your cybersecurity to become proactive, effective and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cybersecurity Services can help?
Why a vCISO may be right for your organization cyber security
Since the start of the COVID19 pandemic, several societal changes have shaped how firms function in the current climate. Many firms have implemented a work-from-home model to help prevent the spread of the novel coronavirus and ensure employees are comfortable with their surroundings. What many organizations didn’t anticipate are the cyber security-related risks.
Once employees leave the security of their offices, they increase their attack surface and open themselves and their employer to attendant Information Security vulnerabilities that may come with working remotely. Remote work changes have prompted heightened instances of cyber attacks that have worsened in style and quantity over time. The pandemic has created the perfect environment for hackers to attack with more accuracy, and with greater cost to the firm, than ever. Learn more about remote working in relation to the pandemic.
How a vCISO can help protect your firm from cyber attacks
A vCISO can function as an additional set of eyes that constantly monitors your firm’s security operations. The additional security will aid in preventing possible security breaches. A vCISO can also bring expertise to assist in developing a strategy to strengthen your firm’s security program.
The benefits of a vCISO:
A board-level cyber security consultant fulfilling the CISO responsibilities
A team of security risk assessment experts
Employee security awareness education
Dark Web Monitoring 24/7/365
Full enterprise risk management for any required compliance
Comprehensive third party/vendor management
Compliance support for NIST, ISO, GDPR, CCPA, NYDFS, PCI/DSS among others
A more affordable approach as opposed to hiring a full-time CISO
Eliminate internal training costs and have our seasoned experts handle your security
CyberSecOp offers vCISO services. Click here to learn more.
Penetration Testing and its Benefits
Understanding your vulnerabilities through vulnerability and penetration testing can play an essential role in your firm’s security. We recommend the steps below to sideline these threats:
Discover if your systems are prepared for a cyber-attack
A security expert or ethical hacker will launch a simulated attack using external and internal attacks on your servers, web apps, wireless networks, intranets, network devices, mobile devices, and any other entry point.
Reporting with findings on vulnerabilities in your systems
Once the simulation is complete, the security team will present reports of their findings and recommend the next steps for securing your systems. Since there are several potential entry points into your plans, the team will attempt to exploit those vulnerabilities.
Know where your weaknesses lie and patch up those vulnerabilities before they can be exploited
Conduct an IT penetration testing to identify gaps in your security system, problems with your IT security policy, and vulnerabilities in your firewall and or antivirus. You will obtain a report with all the problematic access points in your system and suggestions for hardware and software improvements. The test will help you determine if you may need to upgrade your Firm’s security.
Internal vulnerabilities
Whether a disgruntled employee or accidental, internal vulnerabilities can be a window for malicious actors to exploit.
Not all Ethical Hackers are created equally
Be sure to hire the most seasoned experts in the field. Your ethical hacker will attempt to exploit the vulnerabilities as a real hacker would – but the effectiveness of the penetration test will ultimately depend on the amount of experience the engineer has.
Once is not enough
As we know, hackers have been becoming increasingly bold with their techniques to infiltrate the most sophisticated systems yet, as proven in the Sunburst Hack; therefore, CyberSecOp recommends testing your systems quarterly and keeping up with systems patches and updates.
CyberSecOp offers:
CyberSecOp has security experts with a combined experience of 40 years. Ask about our pen test sample report.
Cyber Security Breach Defense & Ransomware Risk Reduction
Cyber Security Breach Defense and Ransomware Risk Reduction by 98%, As ransomware evolves, so does CyberSecOp defense technologies.
Ransomware is the fastest growing attack-vector targeting all sorts of companies, institutions and organizations. No organization is immune to cyber attack. Cyber attackers can demand money from companies and institutions of all sizes and industries including nonprofit, enterprises and startups.
Ransomware Protection Solutions
Managed Detection & Respond - Managed advanced endpoint protection, this is basically monitoring an advanced antivirus, which have the following features: Antivius, Firewall, Host Inturstion Prevention, Auto Malware Containment, and Malicious URL filtering services.
SOC as a Service - Secure Operations Center 24/ monitoring- starts with a SIEM which correlated all logs into a central system, but SIEM can ingest data from multiple solution in the client environment, for example: Network Traffic, Intrusion Prevention, Cloud Assess Security Broker, Data Loss Prevention, Mircosoft Active Directory, Antivirus, Authentication System, Access Management, and other security logs.
Cyber Security Threat Hunting - Treat Hunting is not tied to any one a solution, and it is a service provided by a team utilizing multiple tools to understand if the client has been compromised, also call a compromised assessment, which may include the following but not limited to: Advanced Endpoint Protection (AEM), Security Information and Event Management (SIEM), Network Traffic, Intrusion Prevention, Cloud Assess Security Broker, Data Loss Prevention, Microsoft Active Directory, antivirus, Authentication System, Access Management, and others.
Data Loss Prevention (DLP) - Data loss prevention software (Common Terms data loss, data leak) detects potential data breaches/data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data. It is a standalone document, but its log data can be ingested by a SIEM correlation.
Preventing and Mitigating
Disable or remove remote services whenever possible; If not possible, use MFA/IP address restriction.
Do not allow remote access directly from the internet. Instead, enforce the use of remote access gateways along with a VPN that requires multi-factor authentication;
Require separate credentials for any remote access services; and administrative accounts.
Allow only VPN IP addresses to connect via RDP so that only trusted machines can connect;
Application whitelisting is critical to identify risks and unsanctioned application within your organization;
Network and domain segregation, isolation critical system from none critical system';
Deploy password lockout provisions to prevent brute-forcing attempts;
Implement awareness security training programs for employees;
Phishing simulation to identify employees who a susectiable to phishing emails;
Monthly external vulnerability testing;
Daily backup to a cloud provider, or take a copy of the backup offline Daily, Monthly, or Weekly depending on your business risk;
The best defense against ransomware is to outwit attackers by not being vulnerable to their threats in the first place. Ransomware penetrates organizations in multiple ways, so fighting it requires more than one product. CyberSecOp Ransomware Defense products provide ransomware protection from the network, DNS layer to email to the endpoint. As ransomware evolves, so does CyberSecOp defense technologies.
CyberSecOp is an ISO 27001 Certified Cyber Security Consulting Firm
CyberSecOp is proud ISO 27001 Certified Organization
The team at CyberSecOp is ISO/IEC 27001:2013 (ISO 27001) certified.
International Organization for Standardization (ISO) is an internationally recognized standard that ensures that firms such as CyberSecOp, meet best practices for information security management systems and vigorous risk-based framework approach.
We are committed to following a high-quality and consistent security management system. A-lign, an independent, third-party auditor, found CyberSecOp to have technical controls in place and formalized IT Security policies and procedures. A-lign is an ISO / IEC 27001 certification body accredited by the ANSI-ASQ National Accreditation Board (ANAB) to perform ISMS 27001 certifications. Therefore, through ISO 27001, we have developed and implemented processes and procedures in order to provide requirements for establishing, implementing, maintaining, and continually improving an information security management system. The entire certification leads us to the appropriate requirements for an Information Security Management System (ISMS) in our company — a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management processes.
Achieving the ISO 27001 certification is the result of a great amount of effort, dedication, and involvement from every member of the CyberSecOp team. We are constantly challenging ourselves to improve our service and provide the highest security and privacy standards to meet or exceed the needs and expectations of our customers.
Author: Carlos Neto
Information Security Officer
Top 14 Cyber Security Vendor Due Diligence Questions
What is a cybersecurity vendor due diligence questionnaire? Vendor cyber security due diligence questionnaire is a prewritten assessment gain visibility into supplier or vendor cybersecurity posture. Vendor cyber security due diligence questionnaire assist organizations with identify potential risks before onboarding vendors/suppliers.
CyberSecOp vendor management program supports multiple compliance requirement. The following four and other regulations are set forth by different regulatory bodies across the globe for various purposes, including the protection of financial, personal, and healthcare information.
- PCI DSS (The Payment Card Industry Data Security Standard). This is the information security standard for organizations handling branded credit cards.
- GDPR (The General Data Protection Regulation). This legal framework sets guidelines for the collection and processing of personal information for those living in the European Union (EU).
- HIPPA (Health Insurance Portability and Accountability Act of 1996). This U.S. legislation provides data privacy and security for safeguarding all medical information.
- OCC (The Office of the Comptroller of the Currency). This federal agency oversees the execution of laws for national banks, and functions to regulate and supervise banks in the United States.
Reputation Risk
Reputation risk refers to negative public opinion or customer perception that stems from irresponsible vendor practices. Unsecure vendor remote access can lead to a number of problems that may destroy customer relationships and harm your company's reputation, including:
- Customer complaints
- Dissatisfied customers
- Interactions inconsistent with company policies
- Security breaches resulting in the disclosure of customer information
- Violations of laws and regulations
Operational Risk
Operational risk results from internal breaches, processes, and system failures. Third-party vendors are increasing as an extension of operational risk since they are closely tied to operational processes and business practices. Operational risks may be caused by:
- Employee error
- Failure to adhere to internal policies
- Internal and external fraud or criminal activity
- System failures
Top 14 Cybersecurity Vendor Due Diligence Questionnaire
they have a security contact or chief information security officer in place? If a third party deploys dedicated resources to manage risks and safeguard its critical information, it shows they take their security posture with the utmost seriousness.
Do they have industry certification, or are they aligned with an industry framework such as NIST/ISO? While industry certification may not necessarily indicate the effectiveness of third-party security controls, it does provide additional assurance about the vendor's commitment to protecting their systems and customers' information.
Are penetration tests performed by a qualified third-party vendor? If so, how often are they performed and when was the last test performed? Ensuring your vendor has regularly scheduled penetration tests performed by a third party is essential in knowing how secure their environment is and where the weaknesses are so they can be secured before they’re exploited by an attacker.
Is there a formal information security program in place? A security program provides the framework for keeping a company at a desired security level by assessing the risks that are faced, deciding how those risks will be mitigated and planning for how to keep the program and security practices current.
Do they have a mature threat management and intelligence program in place? It's important to ascertain the effectiveness of their security controls. This can be done by reviewing independent security audit reports to assess the vendor's vulnerability management, secure software development processes and threat management programs, such as cyber intelligence.
Is there a formal logical access review process? Having regularly scheduled access reviews of users is essential in knowing who should have access to your system and who no longer needs access. Failures in logical access review procedures are the top reason for exceptions in SOC reports.
How has your vendor implemented the principle of least privilege? Role-based access privileges are vital in only allowing employees to have access to data they need while denying access to data they don’t need to perform their job.
How is data protected in transit between the vendor and the client as well as between the vendor and the end-user? How is data protected at rest on servers and backup media? Encryption of data in both in-transit and at-rest stages is extremely important to keeping it safe from unauthorized access.
How is retired media (hard drives, flash drives, CDs, documents, etc.) sanitized? Physical and electronic data should be disposed of in a secure manner when no longer needed to keep information from falling into the wrong hands. This has become more difficult with the adoption of public cloud services as data may move across multiple physical systems and reside on shared resources.
Are employees and contractors required to attend security training? Providing security awareness education to users of all systems is an important step in limiting user errors that could harm your IT infrastructure and information.
What due diligence is performed on contractors and vendors prior to and post contract? Completing due diligence over your vendor’s third party (your fourth party) is important especially if they have access to your data. You want to make sure they have a secure environment to help keep your information secure.
Do they have a good cyber score? It is prudent to ascertain exposure of an organization at the surface web, deep web and dark web to predict the likelihood of a potential breach due to their exposure. There are several organizations that provide cyber scoring for vendors and also allow you to benchmark them against similar vendors.
Is there a formal incident management program in place? Proper incident handling procedures allow situations to be analyzed and prioritized so that the next appropriate course of action can be taken to address the problem. Breach notification, a key component of incident management, is now included within multiple regulations with emphasis on vendor reporting.
Does your vendor describe technical prevention measures in place? Utilizing various security tools such as firewalls, anti-virus products and intrusion detection and prevention systems allow you to help secure your network from adversaries.
Strategic risk is created from failed business decisions, or the inability to implement strategies consistent with the organizational goals. Third-party vendors that are not aligned with your company’s practices may threaten operations or your ability to effectively execute business strategies. It may take some time to fully build and/or review a comprehensive cybersecurity questionnaire, but it could save you a lot of time and risk exposure in the future. It’s an invaluable questionnaire that provides a lot of insight.
Facilitation of Ransomware Payment Sanction Risk
US Treasury Department Issues Ransomware Advisory
The ransomware advisories provides guidances and tools to recognize, resist, and report attacks.
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) is issuing this advisory to highlight the sanctions risks associated with ransomware payments related tomalicious cyber-enabled activities. Demand for ransomware payments has increased during the COVID-19 pandemic as cyber actors target online systems that U.S. persons rely on to continue conducting business. Companies that facilitate ransomware payments to cyber actors on behalf of victims, including financial institutions, cyber insurance firms, and companies involved in digital forensics and incident response, not only encourage future ransomware payment demands but also may risk violating OFAC regulations. This advisory describes these sanctions risks and provides information for contacting relevant U.S. government agencies, including OFAC, if there is a reason to believe the cyber actor demanding ransomware payment may be sanctioned or otherwise have a sanctions nexus.
Facilitating ransomware is harmful long term
Not only do ransomware payments fuel future attacks, OFAC explained it also threatens US national security interests given their profit and later ability to advance their cause. Paying ransom to a sanctioned entity or jurisdiction could fund activities in conflict with national interests.
What is Ransomware? Ransomware is a form of malicious software (“malware”) designed to block access to a computer system or data, often by encrypting data or programs on information technology systems to extort ransom payments from victims in exchange for decrypting the information and restoring victims’ access to their systems or data. In some cases, in addition to the attack, cyber actors threaten to publicly disclose victims’ sensitive files. The cyber actors then demand a ransomware payment, usually through digital currency, in exchange for a key to decrypt the files and restore victims’ access to systems or data.
Ransomware Payments with a Sanctions Nexus Threaten U.S. National Security Interests
Facilitating a ransomware payment that is demanded as a result of malicious cyber activities may enable criminals and adversaries with a sanctions nexus to profit and advance their illicit aims. For example, ransomware payments made to sanctioned persons or to comprehensively sanctioned jurisdictions could be used to fund activities adverse to the national security and foreign policy objectives of the United States. Ransomware payments may also embolden cyber actors to engage in future attacks. In addition, paying a ransom to cyber actors does not guarantee that the victim will regain access to its stolen data.
Facilitating Ransomware Payments on Behalf of a Victim May Violate OFAC Regulations
Under the authority of the International Emergency Economic Powers Act (IEEPA) or the Trading with the Enemy Act (TWEA),9 U.S. persons are generally prohibited from engaging in transactions, directly or indirectly, with individuals or entities (“persons”) on OFAC’s Specially Designated Nationals and Blocked Persons List (SDN List), other blocked persons, and those covered by comprehensive country or region embargoes (e.g., Cuba, the Crimea region of Ukraine, Iran, North Korea, and Syria). Additionally, any transaction that causes a violation under IEEPA, including transactions by a non-U.S. person which causes a U.S. person to violate any IEEPA-based sanctions, is also prohibited. U.S. persons, wherever located, are also generally prohibited from facilitating actions of non-U.S. persons, which could not be directly performed by U.S. persons due to U.S. sanctions regulations. OFAC may impose civil penalties for sanctions violations based on strict liability, meaning that a person subject to U.S. jurisdiction may be held civilly liable even if it did not know or have reason to know it was engaging in a transaction with a person that is prohibited under sanctions laws and regulations administered by OFAC.
Victims of Ransomware Attacks Should Contact Relevant Government Agencies OFAC encourages victims and those involved with addressing ransomware attacks to contact OFAC immediately if they believe a request for a ransomware payment may involve a sanctions nexus. Victims should also contact the U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure Protection if an attack involves a U.S. financial institution or may cause significant disruption to a firm’s ability to perform critical financial services.
U.S. Department of the Treasury’s Office of Foreign Assets Control
- Sanctions Compliance and Evaluation Division: ofac_feedback@treasury.gov;
- (202) 622-2490 / (800) 540-6322
- Licensing Division: https://licensing.ofac.treas.gov/; (202) 622-2480
U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure
- Protection (OCCIP)
- OCCIP-Coord@treasury.gov; (202) 622-3000
- Financial Crimes Enforcement Network (FinCEN)FinCEN Regulatory Support Section: frc@fincen.gov 12 See FinCEN Guidance, FIN-2020-A00X, “Advisory on Ransomware and the Use of the Financial System to Facilitate Ransom Payments,” October 1, 2020, for applicable anti-money laundering obligations related to financial institutions in the ransomware context.
Contact Information for Other Relevant U.S. Government Agencies:
Federal Bureau of Investigation Cyber Task Force
U.S. Secret Service Cyber Fraud Task Force
Cybersecurity and Infrastructure Security Agency
Homeland Security Investigations Field Office
Using Linux Won't Save You from Ransomware - Here's Why
"Ransomware attacks are becoming more targeted, sophisticated, and costly, even as the overall frequency of attacks remains consistent." (FBI, 2019)
Since early 2018, there has been a sharp spike in the cleverness, thoroughness, and precision of the security breaches we see in the ransomware landscape. Regardless of attack vector - whether it's from phishing, vishing, or the classic insider threat - once ransomware is on your computer, it's incredibly difficult to restore your files. It takes some serious intervention to stand a chance of recovering your business (or personal) data.
The easiest solution is to get the appropriate key and decryption tool, and use them together to unlock your files...but typically you only receive those resources in exchange for paying the ransom, and many companies can’t afford the ransom at its original price. By that time, there's a good chance you've taken a catastrophic financial blow. From hospitals, to insurance companies, to banks, there are plenty of highly valuable (and highly vulnerable) assets to be manipulated, and threat actors don’t hesitate to put lives at stake for the benefit of their wallets.
So how can we prevent these breaches? What is the key to staying safe from attackers?
The answer may be simpler than you think.
The three most impactful measures you can take to stay safe are as follows:
★ Quarantine
○ Take your computer off the network or wifi and reset your data by wiping the device entirely back to its factory settings (the way it came when you bought it) the moment you can confirm there has been a breach.
★ Have a backup
○ You can only take the first measure if you either don’t care at all about your data, or you have bothered to back it up so you have an unencrpted copy.
★ Get help negotiating your ransom down
○ If you need to pay the threat actor the ransom money to recover your data, there are many firms that can help you with this - don’t pay the full price of the ransom! Firms that can help with ransom negotiation and essential protections include CyberSecOp, which you can reach by using Our Contact Form.
So what’s so special about the threat of Linux-based malware? A Linux-based ransomware variant has the potential to take down any and every industry. Major cloud providers like AWS (Amazon Web Services), Oracle, and Microsoft base entire workloads on Linux; malware sweeping through those servers could bring down any company that uses a modernized cloud stack to host their sites and data.
And then there are hacktivists - hackers who hack to do activism for their cause (which can vary greatly in scope between organizations). Hacktivists have a history of using their ransomware attacks to make a point - whether it’s political or personal - and to incite fear in other companies or individuals who support the cause represented by the victim. While you might not think this presents a threat to you personally, or even to your business, the truth is that innovations in cyberattacks threaten us all. If the target were to have a Linux-based system, the hacktivist group targeting that individual would be devoted to finding a way to spread ransomware across Linux-based devices. When ransomware is evolved by perpetrators to this degree, we are likely to see major outages across all the cloud providers listed above, and it could cripple any business or personal account that is hosted therein.
To avoid such a catastrophic and monolithic problem, we should learn to govern our systems from a more ecosystem-centric approach, rather than depend on the classic signature-based antivirus alerts that have become standard. You may recognize Norton Antivirus alerts or even operating-system-based protection like Windows Defender presenting to you pop-ups about updating your signatures.
The truth is that we shouldn’t rely on the technical drivers of these updates, the people who hunt down and publish these known virus signatures, to keep us safe. We should be educating our employees, friends, and families, on the essentials of how to stay digitally secured and prevent breaches in the modern threat landscape. This concept is especially important as a mere tweak in the code of a virus and a quick recompilation of that code can cause the hash (or signature) of the virus to change, causing these famous signature-based antivirus softwares to completely miss the threat on your device.
A phenomenal example of how dangerous this variant-based workaround can be is what happened to the Colorado State Department of Transportation (CDOT) in early 2018.
“As CDOT’s Information Security group scrambled to contain the spread and impact of SamSam’s first wave, their efforts were quickly undermined by another variant of the same ransomware strain that was spreading throughout many of the newly sanitized zones of their network.”[1] (Richard Horne for the SANS Institute)
In an interview with the Denver Post, Brandi Simmons, a spokeswoman for the state's Office of Information Technology said, “The variant of SamSam ransomware just keeps changing. The tools we have in place didn't work. It's ahead of our tools.” The tools in question were signature-tracking antivirus software, like what many of us use on our home computers. In the end, Colorado's Office of Information Technology, the Colorado National Guard, and the FBI all had to collaborate to contain this threat, and by the time they had, over 2,000 computers running Windows and McAfee security software had been taken offline.
In conclusion, it seems inevitable that we will see Linux systems fall prey to the same types of ransomware we currently battle; it’s only a matter of time. Make sure you’re safe and you know how to protect your data: maintain a backup of all your files, be ready to quarantine in the event of a breach, and remember not to panic. We are here to help.
Sources:
https://www.sans.org/reading-room/whitepapers/tools/strings-me-linux-ransomware-39870
https://www.darkreading.com/attacks-breaches/second-ransomware-round-hits-colorado-dot/d/d-id/1331197
Authored by Alison Stuart
What is Cyber Security, IT Security, and Data Security?
What is the need for IT security and CyberSecurity?
Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
IT security is a set of cybersecurity strategies that prevents unauthorized access to organizational assets such as computers, networks, and data. It maintains the integrity and confidentiality of sensitive information, blocking the access of sophisticated hackers.
What is Data Security?
Data security means protecting digital data, such as those in a database, from destructive tampering and unauthorized access. Hardware based security or assisted computer security offers an alternative to software-only computer security.
Common examples of:
- Data encryption
- Tokenization
- Key management
- Data loss prevention
- Data classification
- Data accees management
What is the need for network security?
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware. Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect.
What is Internet security
Internet security involves the protection of information that is sent and received in browsers, as well as network security involving web-based applications. These protections are designed to monitor incoming internet traffic for malware as well as unwanted traffic. This protection may come in the form of firewalls, antimalware, and antispyware.
What is Critical infrastructure security:
Critical infrastructure security consists of the cyber-physical systems that modern societies rely on.
Common examples of critical infrastructure:
- Electricity grid
- Water purification
- Traffic lights
- Shopping centers
- Hospitals
What is Application security:
You should choose application security as one of the several must-have security measures adopted to protect your systems. Application security uses software and hardware methods to tackle external threats that can arise in the development stage of an application.
Applications are much more accessible over networks, causing the adoption of security measures during the development phase to be an imperative phase of the project.
Types of application security:
- Software development
- Application testing
- Code review
- Vunerablity and penetration testing
What is Network security:
Network security ensures that internal networks are secure by protecting the infrastructure and inhibiting access to it.
Common examples of network security implementation:
- Extra logins
- New passwords
- Application security
- Antivirus programs
- Antispyware software
- Encryption
- Firewalls
- Monitored internet access
Types of cyber threats:
The threats countered by cyber-security are three-fold:
Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption.
Cyber-attack often involves politically motivated information gathering.
Cyberterrorism is intended to undermine electronic systems to cause panic or fear.
So, how do malicious actors gain control of computer systems? Here are some common methods used to threaten cyber-security:
Malware
Malware means malicious software. One of the most common cyber threats, malware is software that a cybercriminal or hacker has created to disrupt or damage a legitimate user’s computer. Often spread via an unsolicited email attachment or legitimate-looking download, malware may be used by cybercriminals to make money or in politically motivated cyber-attacks.
There are a number of different types of malware, including:
Virus: A self-replicating program that attaches itself to clean file and spreads throughout a computer system, infecting files with malicious code.
Trojans: A type of malware that is disguised as legitimate software. Cybercriminals trick users into uploading Trojans onto their computer where they cause damage or collect data.
Spyware: A program that secretly records what a user does, so that cybercriminals can make use of this information. For example, spyware could capture credit card details.
Ransomware: Malware which locks down a user’s files and data, with the threat of erasing it unless a ransom is paid.
Adware: Advertising software which can be used to spread malware.
Botnets:Networks of malware infected computers which cybercriminals use to perform tasks online without the user’s permission.
SQL injection
An SQL (structured language query) injection is a type of cyber-attack used to take control of and steal data from a database. Cybercriminals exploit vulnerabilities in data-driven applications to insert malicious code into a databased via a malicious SQL statement. This gives them access to the sensitive information contained in the database.
Phishing
Phishing is when cybercriminals target victims with emails that appear to be from a legitimate company asking for sensitive information. Phishing attacks are often used to dupe people into handing over credit card data and other personal information.
Man-in-the-middle attack
A man-in-the-middle attack is a type of cyber threat where a cybercriminal intercepts communication between two individuals in order to steal data. For example, on an unsecure WiFi network, an attacker could intercept data being passed from the victim’s device and the network.
Denial-of-service attack
A denial-of-service attack is where cybercriminals prevent a computer system from fulfilling legitimate requests by overwhelming the networks and servers with traffic. This renders the system unusable, preventing an organization from carrying out vital functions.
8 Cyber Security Best Practices for Business
- Conduct Phishing Simulations
- Implement Risk Management Governance Approach
- Secure Remotely Working and Travelling Employees
- Plan for mobile devices
- Create a Cybersecurity Awareness Training Program
- Monitor User and File Activity
- Enforce password best practices
- Enforce the Use of Password Managers, SSOs, and MFAs
- Audit Privileged Access
- Implement Data Loss Prevention
- Update Software and Systems
- Implement and monitor EDR, MDR, and SIEM
- Regularly back up all data, and offsite backup
CyberSecOp cybersecurity solution provide pace of mind when it comes to privacy and security. Ensuring data security in the cloud or onpfremisies , compliant and protected by best-in-class security: your data, and the tools you use to harness it, can truly empower your business.
Vishing Awareness
Vishing
Spoofing a legitimate phone number, voice phishing scammers lead people to believe the call is legitimate
What is Vishing?
We’ve all heard the countless stories on phishing and how much of a threat is it in today’s information security landscape. Social engineering to solicit confidential information via email is a threat that all of us have been made aware of. Extensive efforts have been made to not only reduce the influx of phishing emails, but also to raise awareness so that users have the know-how to assess and respond to the threat when a malicious email hits their inbox.
In response, threat actors have turned to a newer form of exploitation: Vishing. Vishing is a form of criminal phone fraud that uses social engineering over the phone or SMS to gain confidential information. Here are some examples
Fake call from “Help Desk” asking for credentials
Unsolicited calls for credit and loans
Calls from a fake client asking about an invoice
Vishing is becoming an increasingly favored tool attackers use, due to the Covid-19 pandemic. With the shift to work-from-home environments, corporate VPNS, and elimination of in-person verification, threat actors are shifting their tactics to exploit this widespread weakness.
How do I protect my firm against Vishing?
Security awareness is the best line of defense against this type of attack, so be sure to incorporate vishing education into your information security awareness program. Policies and procedures should be established and communicated to ensure that employees can verify identity when the helpdesk or anyone else from the company calls and asks after proprietary topical information. It is imperative that information security managers instill a sense of suspicion for any caller asking for said information.
Enabling MFA for any system that has access to confidential information, network or system is non-negotiable; that second factor of authentication can halt many types of attacks. When you enable MFA you avoid the use of SMS as a means of authentication as SMS is easily manipulated and exploited.
Lastly, always apply least privilege so that in the event an account is compromised, there will be minimal damage.
AUTHOR: CARLOS NETO
Information Security Officer
Pandemic & Post Pandemic Cyber Security Remote Workforce
The current pandemic gives cloud computing a push forward; our clients are taking advantage of CyberSecOp Alliance resilient cloud-based digital infrastructure for businesses of every size to protect their data. We have noticed 58% growth in our Cloud services, securing and protecting data while working remotely is one of the top concerns for most of our clients.
During the crisis, cyberattacks have increased worldwide, including against critical healthcare institutions, which have been the target of ransomware attacks. Private-sector data reveals a 350% surge in phishing websites since the start of the pandemic.
Our security professionals prepare for a new level of untrusted network activity and cyber attacks as remote working is expected to continue. What are the questions you should be asking, and what controls need to be in place?
Pandemic & Post Pandemic Cyber Security
While we are still very much on this transformation journey, we are working on the mindset of our clients to be prepared for quicker response to a crisis like COVID-19, by doing this we will increase business continuity and build-in security for all remote working processes. Removing legacy systems, introducing more automation, better identity and access management for remote systems, secure build for remote devices, extended security services such as Managed Detection and Response (MDR), IPS/IDS, Advanced Endpoint Protection, Application Firewall, DNS Filtering, Automated Virus Containment, and Filer Reputation Detection this will provide an additional layers of security for remote workforce, please see below for other recommendations.
Telecommuting is the only way of working for many
1. Adoption of virtual desktop will finally see an upswing:
With tele-working likely to become the norm, virtual desktops could become the security baseline for IT teams to enforce data management standards. Virtual desktops emulate a computer system so that IT can control access as such adding input/output devices as well as software and applications. This could become an important control point when remote workers are operating outside the safety of a corporate network.
To meet the stringent criteria of regulatory and corporate compliance regarding data security, many companies will see the adoption of virtual desktops as the go-to solution.
2. We will notice surge in adoption of decentralized cyber security:
Traditional cyber security controls dictate a centralized approach where data is consolidated from different sources to perform analysis and investigation. With swift digitization, security controls will shift to data sources, similar to the trend witnessed in IoT. We could start seeing a new wave of anti-virus, data loss protection, digital rights management and endpoint-based firewalls and other security controls gaining traction.
With millions of employees working from home, hackers’ focus has shifted from enterprise to remote working individuals. To handle the menace that exists in cyberspace, decentralized cyber security will rise where greater emphasis will be placed on data sources such as actual remote employees themselves.
3. Rise in bio metric way of authentication:
User access controls have largely revolved around one or two-factor authentication. These methods rely on “something you know (username)” and “something you have (password)” and given hackers’ interest in employees as the weak link to start a technical exploit, we will see cyber attacks directed towards individuals.
This means identity protection will be of priority and the best defense should focus on building authentication systems which focus on “who you are.” This would require advanced bio metric solutions such as fingerprint/thumbprint/hand print, retina, iris, voice, and facial recognition technologies.
With bio metrics, hackers’ attempt at impersonating you just got a lot harder than trying to break into passwords.
New processes will govern our way of work
1. Global privacy regulation and policies will require a re-look:
The current state of privacy regulations is designed around the enterprise network and building the proverbial wall to keep sensitive data out of prying eyes. With remote working concepts taking center stage, re-evaluation of these policies is needed to address the new cyber threats.
From a risk management perspective, global privacy policies will need to encapsulate standard operating procedures regarding BYOD, GDPR, NYDFS, CCPA, SHIELD Act compliance and state privacy laws.
Governance around companies and employees’ social media profiles would also have to be included as these platforms are frequently trolled by hackers as they carry out reconnaissance before launching a cyber attack.
2. Cloud will become more important than ever before:
The shift to cloud services offers employees, customers, suppliers, and everyone else across the ecosystem a seamless and frictionless access to data and applications. Remote access by various users would compound security challenges and presents many new potential attack vectors.
In the post-pandemic world, IT resources would shift towards data, particularly keeping data secure across cloud platforms.
3. Containerization technology will be extended beyond enterprise network to include endpoints:
IT architectures will extend containerization and zoning concepts to include not just systems, but also people, roles, and the level of sensitive data they possess. Containerization, thus, will be extended beyond enterprise networks to include endpoints such as remote worker machines and mobile devices.
This will facilitate cyber security teams to apply varied access controls and demarcate data storage to minimize risk of cyber intrusion and data breach.
Source: Cybersecurity Ventures
What is Cybersecurity Maturity Model Certification (CMMC)
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard intended for implementing cybersecurity across DoD contractors.
The CMMC has been in development for a number of years, but the first details on the framework were released in January 2020. The framework makes use of a “maturity” model, in which audits will be conducted by third-party assessors. Firms will be assigned a “level” that represents the cybersecurity protections, or maturity level they have demonstrated.
Breach Report and predicted loss by 2024
A recent study predicted that business losses due to cybercrime will exceed $4.5 trillion by 2024. The threat to the Defense Industrial Base (DIB)--the network of more than 300,000 businesses, organizations, and universities that research, engineer, develop, acquire, design, produce, deliver, sustain, and operate military weapons systems--is especially alarming due to current cyber warfare activities by cybercriminals and state-sponsored actors.
Security is a foundational component of acquisition
The Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S) recognizes that security is a foundational component of acquisition and that some contractors are trading security to benefit cost, schedule, and performance. It's estimated that the DoD supply chain consists of more than 300,000 businesses and organizations, all of which are targets. Most of these organizations are small to mid-size businesses, which are the most vulnerable to cyber-attacks. Based on over 100 Data Breach Investigation's CyberSecOp recognized that organizations between 100 -300 employees are prime victims for cyber criminals because of lack of security controls.
CMMC Model Structure
The goal of CMMC is to provide a framework for the improvement of cybersecurity in DIB sector organizations. CMMC currently defines 17 domains of technical capability, each with five levels of certification (L1 through L5) and specific practices. The DoD will require an organization to have CMMC Level 3 certification before it can receive Controlled Unclassified Information (CUI) in any domain.
CMMC Domains
CMMC Leveled Practices
The majority of the practices (110 of 171) originate from the safeguarding requirements and security requirements specified in FAR Clause 52.204-21 and DFARS Clause 252.204-7012. The practices fall into five levels:
Level 1 represents basic cyber hygiene, and focuses on the protection of federal contract information (FCI). It consists of practices that correspond only to the basic safeguarding requirements specified in 48 CFR 52.204-21 ("Basic Safeguarding of Covered Contractor Information Systems").
Level 2 is a transitional step in cybersecurity maturity progression to protect CUI. Level 2 consists of a subset of the security requirements specified in NIST SP 800-171, as well as practices from other standards and references.
Level 3 focuses on the protection of CUI. It encompasses all of the security requirements specified in NIST SP 800‑171, as well as additional practices from other standards and references.
At Level 4, the model begins to focus more on the proactive activities an organization can take to protect, detect, and respond to threats. These practices enhance the organization's ability to address and adapt to the changing tactics, techniques, and procedures (TTPs) used by advanced persistent threats (APT)s.
Level 5 focuses on the protection of CUI from APTs. The practices increase the depth and sophistication of cybersecurity capabilities.
CMMC Cyber Compliance Services
DOD has made the effort to simplify CMMC, but it is surely still complicated. CMMC is based on several other standards, including DFARS, CERT RMM, 800-171, AU ACSC Essential Eight, UK NCSC Cyber Essentials, ISO 27001, CIS Critical Security Controls, and the NIST Cyber Security Framework. Utilizing all the above information security standards make it very challenging for most DOD contractors to copy with CMMC. Get compliant with CyberSecOp CMMC Assessment, Security Program & Advisory Services.
Author: Kaushik Reddy
New Remote Attack on Workforce Asks For Consent
A newer type of attack that is gaining momentum on the WFH revolution is Consent Phishing, which seeks the user’s permission as opposed to password.
With today’s widespread use of cloud applications like Webex, Zoom, and Box for increased productivity, the average person has no doubt ran across an application that asks for consent. Attackers have leveraged this familiarity to create malicious applications that request permission for access to sensitive data. Once the user has granted the application access it’s Game Over.
How it works
While each attack method varies, it usually comes down to the following steps:
Threat actor registers a malicious app with an OAuth 2.0 provider, such as Azure Active Directory, AWS, or Google Cloud
The app is configured in an inconspicuous way that makes it seem legitimate
The threat actor gets a link to pop up for the user which may be done through conventional email-based phishing, by compromising a non-malicious website
The victim clicks the link and is shown the familiar-looking consent prompt asking them to allow the application permission to sensitive data
Once the user clicks accept, they have granted the application permissions to access sensitive data
The malicious application receives an authorization code, which it then redeems for an access token, and potentially a refresh token
The access token is used to make API calls on behalf of the user
How to protect against this type of attack
Advanced endpoint protection
User awareness, if the application consent prompt contains misspelling or grammar errors, those are telltale signs that it may be malicious
Configure your organization to only allow applications that are published and verified
Configure policies to whitelist only certain apps for use
Author: Carlos Neto
Home Routers Major Weakness in Work from Home Revolution
‘Prepping’ for Work from Home
For the past few years employees and employers alike extolled the virtues of working from home (‘WFH’). We’ve heard the stories of how it leads to a happier and more productive employee, less overhead for the employer, and just more flexibility overall. Most people knew a shift would come eventually – kind of like the shift to IPV6- but it stalled and stalled. Then the pandemic happened and WFH had been thrust upon us with such force that businesses were, and still are, scrambling to get the pieces in place for an effective remote staff.
It is no longer a secret that WFH is here to stay. Many businesses including Fujitsu and Twitter have just gone ahead and implemented WFH ‘forever’. With this change come challenges. One of those is the security of routers in the millions upon millions of homes that now serve as working offices. According to a study by Germany’s Fraunhofer Institute for Communication, vendors have failed to fix hundreds of vulnerabilities in their consumer-grade routers, leaving hundreds of thousands of users exposed to a wide range of attacks. "Nearly all were found to have security flaws, some of them very severe," the Fraunhofer Institute said in a press release. "The problems range from missing security updates to easily decrypted, hard-coded passwords, and known vulnerabilities that should have been patched long ago."
Advice on next steps
So what should we do? The first step is to know the make and model of your router. Research it for any known vulnerabilities, as there may be some cases where the device is so insecure that even patching it still leaves it vulnerable. Once you’ve decided if it is worth keeping the device make sure that it automatically installed firmware updates. If not you may need to manually update it. A task that is well worth the effort. Another task is to make sure that the administrator password for the router has been changed from the default admin password. Many routers now have unique default passwords for their routers- but there are still plenty out there that don’t.
WFH Users should use complex passwords on their routers including:
· Uppercase and Lowercase
· Numbers and Symbols
· At least 8 characters long
You should also use the strongest Wi-Fi encryption your router supports. WPA3 (Wi-Fi Protected Access Version 3) is best.
You may have children working, playing, and streaming while you are home. Ensure they use their own devices and do not surf on your work devices.
Router configuration and device hardening are just one of the many layers of security that businesses need to adapt and expand to their remote workforce. We here at CyberSecOp would not be surprised if, sooner rather than later, companies begin purchasing, installing, and administering home routers to ensure a secure endpoint to endpoint networking. Until then remain vigilant and patch patch patch!
Author: Carlos Neto
Cybersecurity Risks in a Pandemic: What you need to know
The COVID-19 pandemic has alerted many organizations to gaps in their information security infrastructure heretofore unrealized. Most of these deficiencies have been revealed as a direct outcome of the shift from a workforce-in-place physical environment centered around a fixed and determinable worksite location to a distributed, unstructured environment where most employees and individuals are working remotely.
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations.
The lack of a centralized workspace raises a multiplicity of information security concerns, including but not limited to the following:
1. Does the company have an established Work-From-Home (WFH) information security policy, and if not, how is remote worker security managed?
2. Are employees adequately trained to work remotely, and do they have the appropriate tools at their disposal to ensure the preservation of the security environment?
3. How does the organization manage mobile device and laptop security, including encryption?
4. Control and testing of the commercial VPN?
5. Does the organization maintain a comprehensive data loss protection policy?
6. How, if at all does the organization address data loss protection?
7. Does the organization have a breach response plan for mobile and remote WFH employees?
At CyberSecOp, we can help your organization address these, as well as other concerns related not only to the current operating environment but also pertaining to any and all operating challenges you may face as part of your ongoing operations. Our skilled team of information security professionals can provide a comprehensive assessment of your information security framework and suggest remediation and complementary additions to your existing framework, as the case may be.
There are several things to consider if and when the time comes for firms to return to the office. CyberSecOp recommends:
Third-Party network risk assessment
Operational Responses to Security Incidents
Work from Home Security
Virtual Meeting Applications
Updates and Patches
A full virus scan on workstations returning to the office
Full Windows/Mac updates
Review Wi-Fi connections on returning devices: Some people may come back and still connect to Optimum Wi-Fi (This can be very risky)
Delete any accounts not for company use
Provisioning devices employees may have bought in haste (Hardening AV adding to the domain)
Mobile device management strategy for new mobiles, or devices that employees are using more
Pandemic Policy, Cybersecurity Policy Wireless policy
It is important for organizations to foresee possible consequences transitioning from working remotely to returning to the office. CyberSecOp can help facilitate this transition.
AUTHOR: Michael Young
Achieve an Effective Security Awareness Program
For any company, especially technology-oriented ones, being aware about the cyberthreat landscape is critical. There is often the mindset that most cyberattacks can be warded off by procuring and implementing the latest security technologies, and relying on consultants and internal resources to police implementation.
While this passive strategy may yield a certain level of effectiveness, it also takes a high level of active, participatory security awareness on part of both employees and management in order to 100% fortify the lines of defense around the business or corporation.
STEPS TO ACHIEVE AN EFFECTIVE SECURITY AWARENESS PROGRAM
1. The Major Orienting Components – A comprehensive, participatory information security awareness program should have as its three foundational pillars the principles of confidentiality, integrity, and availability. While the first two terms speak for themselves, the third is often misapprehended. Here, it refers to the organization maintaining a comprehensive system of controls over information security such that employees can be assured of having access to all information necessary to perform their roles without risk of breach.
2. The Protection of Corporate Resources - “Corporate resources” does not just refer to digital assets — it also refers to physical assets, such as paper documents. A security awareness checklist should include the proper usage of document-shredding machines and how the shredded documents should be disposed of.
3. Protection of Corporate Facilities - Employees should be trained not only in how to look for suspicious behavior from the outside, but from the inside as well. This will ensure against unauthorized personnel gaining access to the premises for purposes of mounting internal attacks against the information infrastructure.
4. The Formal Security Awareness Training Program – The corporation should maintain a comprehensive security awareness training program and all employees, irrespective of position with the organization and/or function, should regularly participate.
5. Determining Levels of Responsibility and Segregation of Duties – All employees involved in the day to day management of security over the corporation’s digital and physical information assets should have their roles clearly defined and responsibilities enumerated and documented in a comprehensive ‘R & R’ policy.
CyberSecOp Security Awareness Courses specializes in helping employees understand the mechanisms of spam, phishing, spear-phishing, malware, and social engineering and are able to apply this knowledge in their day-to-day job. Our Security Awareness training solutions effect meaningful, sustainable changes in any workforce. With CyberSecOp Security Awareness Training, employees are not just aware of the dangers presented by an ever-changing threat landscape: they’re empowered to protect your organization from them.
AUTHOR: RICH FIORE
Comodo and CyberSecOp Announce Strategic Partnership
Comodo and CyberSecOp Announce Strategic Partnership
after Award-Winning MSSP Dropped Leading Competitor
Clifton, NJ – June 30, 2020 – Comodo and CyberSecOp today announced their strategic partnership. CyberSecOp, an award-winning, independent security consulting firm providing a range of information security consulting services, has partnered with Comodo to expand its security services offering for its customers. Comodo displaced a leading competitor.
“We focus on the customer experience—delivering what our customers want when they want it. That is our commitment and we take it seriously” said Jeffrey Walker, Chief Information Security Officer at CyberSecOp. “We needed to expand our security operations to fit the growing demand from our customers. Once we saw Comodo's complete SOC as a platform (SOCaaP) offering for MSSP partners and its ingenious auto containment technology, we knew they were the right partner for us. Occasionally, we have a partnership that our firm can't survive without, and we are confident that this is the relationship we are building with Comodo.”
CyberSecOp chose Comodo because it’s the world’s only complete, next-gen SOC-as-a platform offering — which includes people, process, and technology. The patent-pending auto containment technology is the world’s only active breach protection that renders ransomware, malware or cyber-attacks useless. In addition, the platform saves MSSP partners time and money, without zero capital outlay.
“Our partners and the channel are in our DNA. Comodo is a partner-centric company and our goal is to make sure our MSSP partners and their clients are secure and happy,” said Alan Knepfer, President and Chief Revenue Officer at Comodo. “We are proud that such a respected MSSP has selected us. Our partners expect the best from us, and this allows us both to take our high standards to the next level.”
About CyberSecOp
CyberSecOp cybersecurity consulting services was founded by two information security professionals, and a managed services IT firm. They recognized the need for cyber security consulting services for small and medium-sized companies, and that small and medium businesses need to be secured with an information cyber security program. We provide Managed Security Services, Cyber Security Consulting, Security Consulting VISO Services, and Security Staffing.
Mission: To redefine customer business equity with best-of-breed transformation, technology, and talent.
Vision: Empower our customers to focus on core business competence through innovative and competitive IT and secure business process outsourcing.
About Comodo Security Solutions, Inc.
Comodo delivers next generation cybersecurity solutions to protect businesses, schools, and government organizations in today’s risk-filled business environment. Headquartered in Clifton NJ, Comodo’s global development team and threat intelligence laboratories deliver innovative, category-leading, solutions for a company’s endpoints, network boundary, and internal network security.
Thousands of companies and organizations rely on Comodo’s technology to authenticate, validate, and secure their most precious asset—information—and to combat constant cyberattacks and threats like ransomware from wreaking havoc on a global scale.
www.comodo.com
sales@comodo.com
+1 888 551 1531
What Is Ransomware?
Ransomware is a type of malicious software that is designed to block access to a computer system or its data until a sum of money is paid. Ransomware attacks typically involve encrypting the victim's data and demanding a ransom from the victim to restore access to the data upon payment. Ransomware attacks can be extremely disruptive and costly for individuals and organizations, as they may result in the loss of important data and interruption of business operations.
There are several ways that ransomware can be delivered, including through email attachments, malicious websites, and vulnerable software. It is important to protect yourself and your organization from ransomware by regularly updating your software and operating systems, using strong passwords and two-factor authentication, and being cautious when opening emails or downloading attachments from unknown sources. If you do fall victim to a ransomware attack, it is important not to pay the ransom and to seek out professional help to restore your system and data.
Ransomware attacks can have significant impacts on businesses.
Ransomware attacks can have significant impacts on businesses, including financial losses, reputational damage, and disruption of operations. According to a 2021 report by the cybersecurity firm Emsisoft, the average ransom demand for a ransomware attack on a business in 2021 was $233,817, with the highest ransom demand being $50 million. The report also found that the number of ransomware attacks on businesses increased by 89% in 2021 compared to the previous year.
In addition to the direct financial costs of ransomware attacks, businesses may also incur indirect costs such as loss of productivity, damage to customer relationships, and legal fees. Ransomware attacks can also lead to reputational damage, as customers and stakeholders may lose trust in the affected business if their data is compromised or if the business is unable to provide its products or services due to the attack.
It is important for businesses to implement strong cybersecurity measures to protect themselves from ransomware attacks, as the costs of such attacks can be significant. This may include regularly updating software and operating systems, using strong passwords and two-factor authentication, and implementing backup and recovery systems to minimize the impact of a successful attack.
ransomware prevention technology
There are several technologies that can be used to prevent ransomware attacks and protect against the damage they can cause. Some of these technologies include:
Antivirus software: Antivirus software can identify and block ransomware before it is able to infect a system.
Firewalls: Firewalls can block incoming connections from known malicious sources, including those used to deliver ransomware.
Email filtering: Email filters can block or quarantine email messages that contain malicious attachments or links, which can prevent ransomware from being delivered through email.
Web filtering: Web filters can block access to malicious websites, which can prevent ransomware from being downloaded from these sites.
Network segmentation: Network segmentation can help to isolate different parts of a network from one another, which can limit the spread of ransomware within an organization.
Backup and recovery systems: Regularly backing up data and implementing recovery systems can help businesses to minimize the impact of a ransomware attack by allowing them to restore their systems and data from a known good state.
It is important to note that no single technology can provide complete protection against ransomware attacks. It is recommended to use a combination of technologies and to regularly update and maintain them to ensure the best possible protection against ransomware.