CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Cyber Security Developments
Cyber Security Is The Backbone Any Online Businesses – Here Are Some Quick Tips To Keep Yourself Informed About The Latest Threats Surrounding Your Business.
Cyber Security Developments
Within a standard nine to five working day, it’s said that there are almost two million data records lost or stolen. Cybercrime has become something of an epidemic in recent years – and it’s no exaggeration to say that everyone is at risk.
Hackers operate in an increasingly complex way and are happy to target small businesses and individuals, who are most likely to be vulnerable to attack. The nature of the threat changes as technology advances and so the only way to stay safe is to stay up to date.
But that’s easier said than done, right? How do you keep up to date with the latest cybersecurity developments?
Follow The News
When it comes to cyber security, ignorance is not bliss – it’s a recipe for disaster. It’s imperative that you identify and follow a news feed that you can trust. By doing so, you can keep on top of any fresh threats that have emerged, learn lessons from other cyber attacks and pick up the latest tips and advice from influencers and experts in this field.
News from this sector really shouldn’t be seen as the preserve of IT specialists – the scale and nature of the threat suggest that this should be of interest to everyone. There’s a burgeoning band of podcasts available on the subject for people who prefer to digest content in this way too.
Bring Up The ‘Security Question’
If you think that installing an anti-virus program is enough, then you’re mistaken. Don’t just presume that you’re safe because you have this because this is merely the first line of defense to root out attacks. By adopting a safety first mindset you can ensure that the way you handle your data is less risky.
Whether it’s securing your Wi-Fi network at home, managing and updating your passwords on a regular basis or the way you collect, collate and analyze data throughthe point of sale software at work, continually ask yourself ‘is this safe?’ Just as ignorance isn’t bliss, complacency could prove your undoing. Place ‘security’ high on the list of credentials to consider when buying new software or hardware, don’t just go for the cheapest option.
Training
Even the experts are constantly having to refresh their understanding of the threat posed by cyber attacks. It pays to search out training opportunities, especially if you’re a business. You are, after all, only as safe as the people operating your software and systems and you don’t want to put the security of your business in the hands of someone who is unsure about what they are doing. Individuals and businesses alike can find free learning materials on Cybrary to help plug any knowledge gaps they have.
It’s Good To Talk
Cyber attacks are incredibly common – but people don’t often enough talk about their experiences. Perhaps you’re afraid or embarrassed to have been caught out? There’s no need to be. In fact, talking with friends and colleagues could really help you to stay safe. Pass on tips about new apps, good software, neat tips and tricks and any new cyber attack tactics you have come across and you can help to do your own bit to combat the criminals.
By keeping up to speed with security news, refreshing your training, sharing tips and tricks and adopting a safety first attitude you’ll give yourself the best possible chance of staying on top of cyber security developments and, best of all, safe.
Cisco Switches vulnerable to remote hacking
Security researchers at Embedi have disclosed a critical vulnerability in Cisco IOS Software and Cisco IOS XE Software that could allow an unauthenticated, remote attacker to execute arbitrary code, take full control over the vulnerable network equipment and intercept traffic.
The stack-based buffer overflow vulnerability (CVE-2018-0171) resides due to improper validation of packet data in Smart Install Client, a plug-and-play configuration and image-management feature that helps administrators to deploy (client) network switches easily.
Embedi has published technical details and Proof-of-Concept (PoC) code after Cisco today released patch updates to address this remote code execution vulnerability, which has been given a base Common Vulnerability Scoring System (CVSS) score of 9.8 (critical).
Researchers found a total of 8.5 million devices with the vulnerable port open on the Internet, leaving approximately 250,000 unpatched devices open to hackers.
To exploit this vulnerability, an attacker needs to send a crafted Smart Install message to an affected device on TCP port 4786, which is opened by default.
"To be more precise, the buffer overflow takes place in the function smi_ibc_handle_ibd_init_discovery_msg" and "because the size of the data copied to a fixed-size buffer is not checked, the size and data are taken directly from the network packet and are controlled by an attacker," Cisco explain in its advisory.
The vulnerability can also result in a denial-of-service condition (watchdog crash) by triggering indefinite loop on the affected devices.
Researchers demonstrated the vulnerability at a conference in Hong Kong after reporting it to Cisco in May 2017.
Affected Hardware and Software:
The vulnerability was tested on Catalyst 4500 Supervisor Engines, Cisco Catalyst 3850 Series Switches, and Cisco Catalyst 2960 Series Switches devices, as well as all devices that fall into the Smart Install Client type are potentially vulnerable, including:
- Catalyst 4500 Supervisor Engines
- Catalyst 3850 Series
- Catalyst 3750 Series
- Catalyst 3650 Series
- Catalyst 3560 Series
- Catalyst 2960 Series
- Catalyst 2975 Series
- IE 2000
- IE 3000
- IE 3010
- IE 4000
- IE 4010
- IE 5000
- SM-ES2 SKUs
- SM-ES3 SKUs
- NME-16ES-1G-P
- SM-X-ES3 SKUs
Cisco fixed the vulnerability in all of its affected products on 28th March 2018, and Embedi published a blog post detailing the vulnerability on 29th March. So, administrators are highly recommended to install free software updates to address the issue as soon as possible.
Security Specialist
Security Consulting
Many people who sell security products call themselves security consultants and they are part of the security field, but there are also security consultants who don't sell products. These individuals are paid on an hourly or project basis to help clients, usually, corporations, protect their personnel and property. Property security embraces both real estate and tangible equipment as well as other assets like client lists and proprietary technology. Employee and customer theft, as well as piracy, are possible focuses for a security consulting practice. Technical security consultants are knowledgeable about products, such as electronic security systems, including their development and how to apply them. The work may involve system design as well as drafting plans and documents.
Computer Security
While virtually all security consultants employ computer technology in their work, the computer security niche specifically involves protecting computer systems and networks themselves against unauthorized use and abuse. A computer security consultant often specializes in particular operating systems such as UNIX, LINUX or Windows.
Site Consulting
Whether it's new construction or remodeling, virtually every building and office-be it a high-tech industrial complex, retail franchise, distribution center, self-storage facility, housing development, hotel, resort, casino, parking lot or law firm-is interested in some aspect of site security. Security site consultants evaluate the physical design of such buildings and spaces, determine what security problems a sites poses and recommend countermeasures, such as guards, electronic security with cameras and electric lights, or a combination of methods and policies.
System Design
Security system designers develop specifications and provide architectural or engineering support in the design phase of a security consulting project. System designers may also develop new electronic security tools to be used at a particular location.
Forensic Consulting
Forensic security consultants serve as expert witnesses in trials in which security breaches are at issue, such as with fires, thefts, break-ins, and so on. Forensic consultants may specialize in any of the above fields.
As a security practitioner, you can also develop niches for your work based on the type of clients you work with, such as museums or historical sites, shipyards and airports. Unlike professional investigators, security consultants don't have to be licensed by state agencies. However, there are professional associations you can join and certification programs you can complete, which may help foster a sense of trust with your clients. One of the larger associations, which provides certification.
Specializing is key to marketing a security specialty business because it will help you more easily identify and market to clients who need such services, such as architects and contractors or members of a particular industry, such as software developers or law firms. You'll be soliciting work and attracting clients by making presentations and speeches or networking in organizations where you can showcase your expertise. In addition to your knowledge of security, you must be prepared to develop your speaking skills in order to attract new business.
What Is Network Security?
What Is Network Security? - CyberSecOp
Network security is an organization’s strategy and provisions for ensuring the security of its assets and all network traffic. Network security is manifested in an implementation of security hardware and software. For the purposes of this discussion, the following approach is adopted in an effort to view network security in its entirety.
What Is Network Security?
Policy
The IT Security Policy is the principle document for network security. Its goal is to outline rules for ensuring the security of organizational assets. Employees today often utilize several tools and applications to conduct business productively. Policy-driven from the organization’s culture supports these routines and focuses on safely enabling these tools for employees. Enforcement and auditing procedures for any regulatory compliance to which an organization is subject must be mapped out in the policies, and controls as well.
Types of network security
Access control
Not every user should have access to your network. To keep out potential attackers, you need to recognize each user and each device. Then you can enforce your security policies. You can block noncompliant endpoint devices or give them only limited access. This process is network access control (NAC).
Antivirus and antimalware software
"Malware," short for "malicious software," includes viruses, worms, Trojans, ransomware, and spyware. Sometimes malware will infect a network but lie dormant for days or even weeks. The best antimalware programs not only scan for malware upon entry, but also continuously track files afterward to find anomalies, remove malware, and fix damage.
Application security
Any software you use to run your business needs to be protected, whether your IT staff builds it or whether you buy it. Unfortunately, any application may contain holes, or vulnerabilities, that attackers can use to infiltrate your network. Application security encompasses the hardware, software, and processes you use to close those holes.
Behavioral analytics
To detect abnormal network behavior, you must know what normal behavior looks like. Behavioral analytics tools automatically discern activities that deviate from the norm. Your security team can then better identify indicators of compromise that pose a potential problem and quickly remediate threats.
Data loss prevention
Organizations must make sure that their staff does not send sensitive information outside the network. Data loss prevention, or DLP, technologies can stop people from uploading, forwarding, or even printing critical information in an unsafe manner.
Email security
Email gateways are the number one threat vector for a security breach. Attackers use personal information and social engineering tactics to build sophisticated phishing campaigns to deceive recipients and send them to sites serving up malware. An email security application blocks incoming attacks and controls outbound messages to prevent the loss of sensitive data.
Firewalls
Firewalls put up a barrier between your trusted internal network and untrusted outside networks, such as the Internet. They use a set of defined rules to allow or block traffic. A firewall can be hardware, software, or both. Cisco offers unified threat management(UTM) devices and threat-focused next-generation firewalls.
Intrusion prevention systems
An intrusion prevention system (IPS) scans network traffic to actively block attacks. Next-Generation IPS (NGIPS) appliances do this by correlating huge amounts of global threat intelligence to not only block malicious activity but also track the progression of suspect files and malware across the network to prevent the spread of outbreaks and reinfection.
Mobile device security
Cybercriminals are increasingly targeting mobile devices and apps. Within the next 3 years, 90 percent of IT organizations may support corporate applications on personal mobile devices. Of course, you need to control which devices can access your network. You will also need to configure their connections to keep network traffic private.
Network Segmentation
Software-defined segmentation puts network traffic into different classifications and makes enforcing security policies easier. Ideally, the classifications are based on endpoint identity, not mere IP addresses. You can assign access rights based on role, location, and more so that the right level of access is given to the right people and suspicious devices are contained and remediated.
Security information and event management
SIEM products pull together the information that your security staff needs to identify and respond to threats. These products come in various forms, including physical and virtual appliances and server software.
VPN
A virtual private network encrypts the connection from an endpoint to a network, often over the Internet. Typically, a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Web security
A web security solution will control your staff’s web use, block web-based threats, and deny access to malicious websites. It will protect your web gateway on site or in the cloud. "Web security" also refers to the steps you take to protect your own website.
Wireless security
Wireless networks are not as secure as wired ones. Without stringent security measures, installing a wireless LAN can be like putting Ethernet ports everywhere, including the parking lot. To prevent an exploit from taking hold, you need products specifically designed to protect a wireless network.
Cyber Security, New York Fights Back to Prevent Financial System Take Down
New York is quietly working to prevent a major cyber attack that could bring down the financial system.
As hackers become more sophisticated and cyber attacks more routine, New York is on notice.
With a lack of leadership from the federal government, New York is one of the first states to implement new cyber regulations.
The state is quietly working to prevent a major cyber attack that could bring down Wall Street's financial system.
But even with the strictest cybersecurity regulations in the country, experts warn New York's efforts may still not be enough.
NEW YORK — Five months before the 9/11 attacks, US Secretary of Defense Donald Rumsfeld sent a memo to one of his advisers with an ominous message.
"Cyberwar," read the subject line.
"Please take a look at this article," Rumsfeld wrote, "and tell me what you think I ought to do about it. Thanks."
Attached was a 38-page paper, published seven months prior, analyzing the consequences of society's increasing dependence on the internet.
It was April 30, 2001. Optimistic investors and frenzied tech entrepreneurs were still on a high from the dot-com boom. The World Wide Web was spreading fast.
Once America's enemies got around to fully embracing the internet, the report predicted, it would be weaponized and turned against the homeland.
The internet would be to modern warfare what the airplane was to strategic bombers during World War I.
The paper's three authors — two PhD graduates and the founder of a cyber defense research center — imagined the damage a hostile foreign power could inflict on the US. They warned of enemies infecting computers with malicious code, and launching mass denial of service attacks that could bring down networks critical to the functioning of the American economy.
"[We] are concerned that US leadership, and other decision makers about Internet use, do not fully appreciate the potential consequences of the current situation," the report said. "We have built a network which has no concept whatsoever of national boundaries; in a war, every Internet site is directly on the front line. If we do not change course soon, we will pay a very high price for our lack of foresight."
The US government had a problem on its hands and it seemed a long ways from figuring out how to handle it.
More than 17 years later, that problem seems to have only gotten worse.
Follow the money
Willie Sutton, the notorious Brooklynite who spent his life in and out of prison, once told a reporter he robbed banks because that's where the money is. Computer hackers aren't so different.
In 2016, hackers attacked companies in the financial services sector more than companies in any other industry, according to IBM. Over 200 million financial records were breached that year, a 937% increase from 2015. And that's not including the incidents that were never made public.
As hackers become more sophisticated and cyber attacks more routine, New York is on notice. Home to the most valuable stock exchange on Earth, New York City is the financial capital of the world. When the market moves here, it moves everywhere.
So it was no surprise when in September 2016, Gov. Andrew Cuomo announced that the New York State Department of Financial Services (NYDFS) was gearing up to implement sweeping, first-of-their-kind cybersecurity regulations to protect the state's financial services industry — an unprecedented move no other state or federal agency had taken anywhere in the US.
Cybersecurity in New York's financial industry was previously governed by voluntary frameworks and suggested best practices. But the NYDFS introduced, for the first time, regulations that would be mandatory, including charging firms fines if they didn't comply.
Maria Vullo, the state's top financial regulator, told Business Insider that her No. 1 job is to protect New Yorkers.
"They're buying insurance. They're banking. They're engaging in financial transactions. And in each of those activities, they're providing their social security information, banking information, etc.," she said. "The companies that are obtaining that personal information from New Yorkers must protect it as much as possible because a breach of that information is of great consequence to the average New Yorker."
On March 1, the regulations turn a year old, although some of the rules are not yet in effect and will phase in overtime.
The NYDFS oversees close to 10,000 state-chartered banks, credit unions, insurance companies, mortgage loan servicers, and other financial institutions, in addition to 300,000 insurance licensees.
The combined assets of those organizations exceed $6 trillion, according to the NYDFS — and they're all in constant danger of being hacked.
Banks are vulnerable
In the summer of 2014, an American, two Israelis, and two co-conspirators breached a network server of JPMorgan Chase, the largest US bank.
They got hold of roughly 83 million customers' personal information, including names, addresses, phone numbers, and email addresses.
The hackers didn't steal any money from personal bank accounts, but that wasn't the point.
They wanted access to a massive trove of emails that they could use for a larger, separate money scam. In just three years, that operation netted the hackers more than $100 million.
The JPMorgan hack wasn't the end game. It was a piece of the puzzle.
The attack began with the simple theft of a JPMorgan employee's login credentials, which were located on a server that required just one password.
Most servers with sensitive information like a person's banking data require what's called multi-factor, or two-factor authentication.
But JPMorgan's security team had lapsed and failed to upgrade the server to include the dual password scheme, The New York Times reported at the time.
The attack, the breach, and the reputational damage that followed could have been avoided with tighter security. Instead, the hack went down as one of the largest thefts of customer data in US history.
"Banks are especially vulnerable," Matthew Waxman, a professor at Columbia Law School and co-chair of the Cybersecurity Center at the Columbia Data Science Institute, told Business Insider. "Disruption to the information systems on which banks rely could have shockwaves throughout the financial system, undermining public confidence in banking or knocking off line the ability to engage in commercial transactions."
That's the kind of catastrophic damage that worried the authors cited in Defense Secretary Rumsfeld's 2001 memo.
They weren't only concerned about stolen email addresses and social security numbers. They were worried about the fallout from such activity.
Banking works because consumers trust the system. But what if people lose trust?
Waiting until a catastrophe
News of impending cybersecurity regulations in New York in the fall of 2016 was both welcomed and shunned.
Some companies saw it as a chance to improve their own security standards while others complained of government overreach. Some were relieved to find they wouldn't have to make any adjustments to the way they operated. Others were overwhelmed by the heavy lifting they would have to do to comply.
How a company views the regulations depends in large part on its size. Bigger institutions with more cybersecurity professionals and more resources at their disposal tend to already have in place much of what the regulations require. Many smaller companies, which tend to be under-staffed and under-resourced, have a lot more work to do to catch up.
Jenny Cheng/Business Insider
The only additional thing Berkshire Bank has to do is sign off on its annual compliance form, which it sends to NYDFS to prove that it's doing everything it's supposed to be doing.
"We actually have to do nothing [new] from a compliance standpoint," the company's chief risk officer Gregory Lindenmuth told Business Insider.
While several cybersecurity consultants told Business Insider they acknowledge the NYDFS rules as a positive step in the right direction, they also point to a new law in Europe as a leading example of the role government has to play in protecting individuals' privacy rights and ensuring that companies secure consumers' personal information.
In 2016, the European parliament passed a law called the General Data Protection Regulation (GDPR) — landmark legislation that imposes millions of euros in fines on companies that do not adequately protect their customers' data.
Whereas the NYDFS regulations cover just one industry in one US state, the GDPR affects companies in all industries across all 28 member states of the European Union. Companies that do not report a data breach or fail to comply with the law more generally could be fined up to €20 million or 4% of its global revenue.
Matthew Waxman, the Columbia professor, says it's not surprising that the implementation of such a law remains far-fetched in the US.
"It's sometimes very difficult to get the government to take action against certain threats until a catastrophe takes place," Waxman said. "But that could change very suddenly if the banking system were knocked offline or another very major disruption to everyday life affected the lives and security of citizens on a massive scale."
But are the deterrents strong enough?
Data protection advocates calling for stricter cybersecurity regulations in the US are generally happy about the NYDFS rules.
For the first time, a state government is taking seriously the protection of consumer data, they say. It's giving companies in the financial sector an ultimatum: protect New Yorkers or face punishment.
"My big criticism of the regulations is there's no clear consequence for non-compliance," Thomas Boyden, the president of GRA Quantum and a cybersecurity expert who helps companies defend against cyber attacks, told Business Insider. "If companies don't feel like there's going to be any consequence for any action on their part, companies aren't going to take [the regulations] seriously."
In fact, for many companies, Boyden thinks "that's the default position."
Vullo, the head of the NYDFS, said she has the ability to fine companies that are not complying and is willing to exercise that authority, although how much that cost may be would depend case-by-case.
"I don't want this to be a punitive atmosphere, but obviously if institutions are not taking this seriously, then there will be consequences," she said. "But it's not the objective."
If anything, the objective is to make it clear that cyber threats are real and that New Yorkers and the companies that maintain their personal information are facing higher risks of attack.
Cybersecurity affects everyone, and Vullo said she hopes the regulations will help companies prioritize it.
"Everyone is part of our cybersecurity team," Theresa Pratt, the chief information security officer at Market Street Trust, a private trust company in New York, told Business Insider. "It doesn't matter what myself or my colleagues do from a technical perspective. If I have one user who clicks a bad link or answers a phisher's question over the phone, it's all for naught."
New York leading the way
The new rules have far-reaching implications beyond New York. A business in the state that has a parent company based in Germany, for example, still has to comply with the regulations.
This leaves some organizations in the precarious position of having to either restructure company-wide cybersecurity practices or build an entirely new and unique security apparatus that is specific to its New York offices.
"I do think that because of the scope of some of these regulations, they're kind of blurring the lines between countries and continents. I think we're going to see more and more of this," GreyCastle Security CEO Reg Harnish told Business Insider. The New York-based consulting firm is helping companies comply with the new regulations.
In the absence of leadership from the federal government on certain issues related to cybersecurity and data protection, states like New York are beginning to fill the void. Several cybersecurity experts told Business Insider that the NYDFS regulations could become a model for other industries or even policies at the national level.
Last year, at least 42 states introduced more than 240 bills or resolutions related to various cybersecurity issues, according to the National Conference of State Legislatures. And since the NYDFS rules took effect, financial regulators in Colorado and Vermont have followed New York's lead with cybersecurity regulations of their own.
Indeed, cyber experts have come a long way in better understanding the threats we face since Rumsfeld's dire cyberwar memo in 2001. But 17 years on, the former secretary of defense's concerns still seem as relevant as ever.
Perhaps the memo was a prescient warning — a warning that fell on deaf ears, but is not too late to address.
GDPR European Union General Data Protection Regulation
The European Union General Data Protection Regulation will go into effect on May 25, and healthcare organizations who treat patients from any of the 28 EU nations will need to familiarize themselves with the law to ensure compliance.
GDPR requires companies to gain affirmative consent for any data collected from people who reside in the EU. And organizations that violate the law could face fines up to four percent of their global annual revenue or 20 million euros -- whichever fine is higher.
While U.S. organizations must remain HIPAA-compliant, GDPR rules could be a game-changer for those who care for EU patients. Providers will need to consider data flows, cross-border data transfer, privacy and security monitoring, to ensure their policies are compliant with the law.
Tougher than HIPAA
GDPR is much more stringent than HIPAA, as it broadens the definition of personal data and covers any information associated with an “identified or identifiable natural person,” including computer IP addresses, photos, credit card data and the like.
The law also mandates organizations process data requests from EU patients much more quickly than with U.S. standards. And providers will also need clear permission to even use EU resident information.
Because of HIPAA, GDPR is nothing new for U.S. healthcare organizations, explained Kristen Johns, partner at Waller, a national healthcare law firm.
“But it will be a real shock for people who aren’t aware of the kind of data they hold and what they share with other vendors,” said Johns. “But for healthcare, it shouldn’t be a shock or learning curve.”
To Johns, there’s a fundamental difference between GDPR and HIPAA, as the EU law is based on personal rights, while HIPAA is focused more on the data itself and who can share it and what can be done with it.
Right to erasure and consent
One of the biggest challenges for U.S. provides will likely be the GDPR “right to be forgotten” or sometimes known as the right to erasure. One of the cornerstones of the law is to strengthen individual rights, meaning organizations must honor all patient requests to erase personal data.
It also places limits on how long data can be stored, covering all data not considered valuable to scientific research under GDPR definition. Organizations must implement technology capable of totally and completely erasing personal data upon request.
For the U.S., where it’s common to store patient data indefinitely, this will be a major change.
Notice of consent is the other area U.S. providers must fully understand, explained Johns. Providers should draft consent forms that outline what’s collected and make sure that they give a clear place for patients to opt in or out of data sharing or collection.
“Securing disclosure: It boils down to consent, something beyond what exists now in most cases,” Johns said. “You have to show that you have that chance to opt in and out easily. And consent has to be in clear, plain language. Currently, not all these healthcare consents are.”
Roughly translated, GDPR mandates the elimination of fine print, often overlooked by patients, which can contain loopholes in privacy policies. The idea is that organizations will need to simplify consent language so that it’s easy for patients to understand.
Tighter security
GDPR also cracks down on security requirements to ensure patient data is protected. This includes implementing pseudonymization and redundancy, along with routine pen testing and intrusion detection measures. Further, much like with HIPAA, organizations will need a continuous process to evaluate its security measures.
But one GDPR mandate that some healthcare organizations still haven’t gotten right is the need for encryption. Providers must lockdown all patient data -- if they haven’t already.
And one final security measure that is vastly different than HIPAA is that organizations will only have 72 hours to inform EU patients of a breach. HIPAA gives providers 60-days from the time of discovery.
“In reality, GDPR article is about data protection by design and by default,” said Johns. “It gives all identities that could be a data processor … a chance to look at their IT infrastructure and see where they can improve to comply with GDPR.”
There are plenty of lists online to determine how entities can be compliant with the data structure of each entity, and how it applies to internal audits, explained Johns. But for healthcare, “the big thing is the internal audit: looking to make sure they have the ability to access information quickly in a compliant way with GDPR and HIPAA.”
Enterprises understand cyber risks
Enterprises understand cyber risks
Hackers and cyber criminals often seek to exploit human errors like misconfigurations, poor security practices and the use of shadow IT.
In order to help businesses assess the risk CyberSecOP is launching an automated advanced persistent threat (APT) simulation platform, LocPar, to continuously expose all attack vectors, above and below the surface.
LocPar uses advanced attack techniques to expose the most critical blind spots. In the process, it provides data-driven remediation that focuses on an organization's most critical assets, reduces its IT risk and enables it to optimize its cyber resources.
"The best way to prevent a cyber attack is to identify in advance the attack vectors hackers will use to compromise an organization's critical assets," says CEO and co-founder of XM Cyber Noam Erez. "Even when an organization has deployed and configured modern security controls, applied patches and refined policies, it should still ask 'Are my crown jewels really secure?' as there is a plethora of ways hackers can still infiltrate the system and compromise critical assets. This is why we founded CyberSecOp: to equip enterprises with a continuous 360° view of which critical assets are at risk, what security issues they should focus on, and how best to harness their resources to resolve them."
Features of LocPar include full mapping of all attack paths at any given time, automatic adaptation to the context of the organization, using misconfigurations, user activity, credentials and security vulnerabilities in the network.
Comprehensive and up-to-date attack scenarios use the latest hackers' techniques and methods, giving the ability to detect and remediate IT-related risks in real-time. Reports are produced based on how critical the attack vector is.
Image Credit: SergeyNivens / depositphotos.com
Secure Your Website, from Cyber Attacks
The average website was attacked 44 times a day during the last quarter of 2017, according to new research from security specialist SiteLock.
The company analyzed six million sites to identify trends in the behavior and tactics of attackers. Though the number of attacks represents a 25 percent decrease over the previous quarter, it still means a site could be attacked 16,000 times a year.
"A decrease in attacks does not mean that websites are safer. In fact, it may even be the opposite," says Neill Feather, president of SiteLock on the company's blog. "Hackers are constantly trying new avenues and even leveraging older tactics that continue to be successful. As our research shows, cybercriminals are now able to successfully breach a site with fewer, more targeted attacks. Now more than ever, businesses need to evaluate their current security posture and ensure they have both the right technology and a response plan in place should a hack occur."
Among other findings are that around one percent of sites sampled are infected with malware each week. Yet only 19 percent of infected sites are blacklisted by search engines. WordPress sites using plugins are twice as likely to be infected as sites that don’t employ a content management system. In addition, 46 percent of infected WordPress sites have the latest core updates. The average number of infected files per site increased by 0.8 percent to 309.
The malware being used is increasingly complex too. 51 of the malware found was categorized as Encoded Malware, meaning it was randomly generated or difficult to decode. These are often parts of groups of files called 'attack kits'. Backdoors made up 12 percent of files, resulting in more files being uploaded to infected sites.
NYDFS Cybersecurity Retain a CISO, CSO -Regulation Compliance
With cyber-attacks on the rise and comprehensive federal cybersecurity policy lacking for the financial services industry, New York is leading the nation with strong cybersecurity regulation requiring, among other protective measures, set minimum standards of a cybersecurity program based on the risk assessment of the entity, personnel, training, and controls in place in order to protect data and information systems, said Superintendent in a press release issued by DFS, CyberSecOP helping financial organisation comply with the NYDFS manadates.
With the New York Department of Financial Services’ (NY DFS) new terms poised to come into effect next month, banks and financial services companies operating in the state must start preparing for the change.
One of the most discussed issues in the controversial proposal is the requirement to appoint a CISO (chief information security officer). The move was met by heavy criticism at a hearing in December last year, leading to a massive backtrack from the DFS in a revised proposal.
Requirements of the CISO
The latest proposal removes any explicit requirement to hire a CISO, which is good news for many smaller or rural financial institutions that don’t currently have one in place. What this means, practically, is that the position is no longer necessarily exclusive. Banks can choose to designate someone to complete the tasks of a CISO while also performing other duties. Alongside this, the proposal does not state that the specific title of ‘CISO’ is required.
So what will the CISO (or CISO by any other name) be asked to do? The role now covers a broader set of responsibilities but in a less detailed manner. The designated person will have to provide an annual report to the board of directors (previously proposed as a biannual report) on the “cybersecurity program and material cybersecurity risks”, according to the proposal. It is now specified that the report must be “in writing” but it no longer needs to be provided to the NY DFS upon request.
The required content of the report will now also be less extensive. The CISO must identify and report only on material cyber risks rather than all cyber risks. This will involve “consider[ing]” those issues “to the extent applicable.” Additionally, the CISO will be able to tailor their focus to the issues appropriate to their organization.
Finding the right candidate
The NY DFS’ revision allowing the CISO to be an employee of the covered entity (i.e. an internal hire), or an affiliate or third-party service provider offers crucial flexibility for smaller financial institutions.
Companies with only a handful of employees – the most vocal in their frustration at the DFS’ initial plans – may look to shuffle their existing staff.
When doing that – or in making a new hire – there are certain things organizations need to look for. The CISO role is not just a tech-specific position, notes John Linkous, RSA Conference’s technology advisor, but they must now be “a trusted advisor to the business as a whole”. He adds:
“One of the most critical capabilities is simply the ability to understand the business much more intimately than his or her predecessors. Business drives the need for technology, and so security must be focused on how data is used within those business functions, across the end-to-end spectrum. Without a solid understanding of what the organization does, and how it makes money, an information security officer is going to have a fundamental disconnect with what’s needed to protect the enterprise.”
Third-party service providers or affiliates
Given the responsibility placed on the CISO, outsourcing the role to a third party can be an appealing proposition.
Going down this route presents its own set of issues, though. As TechTarget reported, third parties are “almost always” involved when it comes cyber breaches – arguing that it is either through a lack of accountability or oversight. While service-level agreements (SLAs) are always advised, the DFS has taken steps to ensure the right measures are in place. In response to the fear that financial services firms would not always have sufficient power to force third parties to accept their preferred provisions, the NY DFS now dictates that all third-party services must be performed under contractual provisions rather than by way of “relevant guidelines for due diligence.”
Source: www.itgovernanceusa.com
Study Reveals 90 Percent of Businesses Will Use Biometric Authentication by 2020
Spiceworks today announced the results of a new survey examining the adoption and security of biometric authentication technology in the workplace. The results show 62 percent of organizations currently use biometric authentication technology, and an additional 24 percent plan to utilize it within the next two years. The findings indicate that although most IT professionals believe biometric authentication is more secure than traditional forms of authentication, such as text-based passwords, PIN numbers, and personal security questions, only 10 percent of respondents believe biometrics are secure enough to be used as the sole form of authentication.
Fingerprint and face scanners are most commonly used in the workplace
Fingerprint and face scanners are the most common types of biometric authentication used on corporate devices and services. The results show 57 percent of organizations are using fingerprint scanning technology, while 14 percent are using face recognition technology. Other biometric methods utilized include hand geometry recognition (5 percent), iris scanning technology (3 percent), voice recognition (2 percent), and palm-vein recognition (2 percent).
When further examining the types of fingerprint scanners organizations are using on company devices and services, the results show Apple Touch ID is the most commonly used at 34 percent, followed by Lenovo Fingerprint Manager (13 percent) and Samsung fingerprint readers (13 percent). Eleven percent of organizations are also using fingerprint scanners from Microsoft and Dell, while 23 percent are using fingerprint scanners from other vendors. Additionally, when examining the specific types of face and iris recognition technologies utilized, the results show 14 percent of organizations are using Apple Face ID, 13 percent are using Microsoft face login via Windows Hello, and 7 percent are using Android Face Unlock.
While 46 percent of organizations utilize biometric authentication on smartphones, 25 percent use it to authentication employees on laptops and 22 percent use it on tablets. Additionally, 17 percent of organizations use biometrics to verify employees on time clock systems, and 11 percent use it on door locks for the server room. Other uses for biometrics in the workplace include technology to authenticate employees on applications with sensitive data, wearables, and email.
A lack of transparency exists around the security of biometrics
Although biometric authentication in the workplace is already commonplace, many IT professionals still don’t trust the technology. More than 50 percent of IT professionals believe biometrics are harder to hack than traditional text-based passwords, but only 23 percent believe biometric authentication will replace traditional text-based passwords in the next two to three years.
IT professionals’ distrust around biometrics is potentially due to a lack of transparency from vendors around the security risks. According to the survey results, 65 percent of IT professionals believe there’s not enough transparency about the vulnerabilities discovered in biometric systems, and 63 percent believe there isn’t enough transparency regarding the privacy of biometric data collected by vendors. In fact, nearly 60 percent of IT professionals said they need more information about where technology vendors store biometric data.
“Many IT professionals aren’t convinced biometrics can serve as a secure and reliable replacement for the standard username and password combo,” said Peter Tsai, senior technology analyst at Spiceworks. “Unless technology vendors can address the security issues and privacy concerns associated with biometrics, the technology will likely be used side-by-side in the workplace with traditional passwords or as a secondary authentication factor for the foreseeable future.”
Compliance Complacency: Are your Compliant
Data is power. It’s a prime commodity for businesses, which in turn means it is constantly under threat. Just try and think back to a week where a data breach or cyber attacks did not hit the headlines, and you’ll struggle. Not only are these threats a growing problem for any organisation, but the issue becomes more paramount when combined with upcoming changes in compliance. The surge of data created by the digital age has called for a change in how organisations store and handle it. The consequences of non-compliance are well-documented by now, whether that’s in the form of a fine, insolvency or even closure.
Surely then it can be assumed that this issue is being taken sufficiently seriously by organisations across all industries? Initial findings from our recent global research[1] suggest otherwise.
Our inaugural The Little Book of IT study found that in the UK, 30 per cent of business respondents who classified their security technology as “fully implemented/integrated,” reported that no security improvements could be made. This bold assumption would infer that over a third of businesses believe their systems are fully prepared to deal with the security challenges facing them, and may explain why a seemingly inadequate 10% of IT budget is being spent on security provisions (which represents only 2.25% growth over the previous year’s expenditure, with next year’s spend set to be marginally even less at 1.86%). Whilst it’s nigh-on impossible to keep pace with cyber criminals, it is none-the-less vital to constantly evaluate the security protocols and tools an organisation has in place. To do otherwise is to risk leaving itself (and anyone connected to its systems) a sitting duck.
Surprisingly, the research also found that remaining secure to cyber threats is only the second highest IT priority, after changing IT infrastructure and cloud adoption. Businesses are either extremely relaxed or perilously unaware of the changing responsibilities and liabilities around compliance. Have we entered a period of compliance complacency? To do so would be unwise, given the upcoming changes in regulation. To add salt into the wound, just over half of respondents (51% stated they had been offered training to regulatory compliance.
It’s not the first time that the complacency label has been banded around when it comes to security (especially when pinning down responsibility) – and the above stats do infer such a laissez faire attitude. That said, a deeper dive into this research unveiled a far more complex situation. On further questioning, security was the number one factor taken into consideration when adopting new technology.
With this in mind it would seem less like complacency, and more confusion – with some areas of the business placing it with greater importance than others. What’s needed then is a more cohesive and integrated security and data integrity strategy. One that embraces all employees, albeit tailored to their specific business roles.
The changing cyber landscape has an impact upon, and requires responsibility from, everyone in the business: from the CEO through to freelance staff and not just the IT department. Security is just one aspect of a business’ IT strategy and teams still have to ensure both the day-to-day running of IT environments whilst still implementing the initiatives which it is hoped will help deliver enhanced business outcomes.
As The Little Book of IT study revealed, the issues and challenges of doing so are numerous. Whether it’s budget constraints impacting security in some way (48%) modernising legacy systems (65%), both are stealing time and focus from innovation. Meanwhile cloud adoption (52%), business analytics (37%) and digitalisation 35% exert great pressure – whether positive or negative – meaning the modern-day IT department has rather a lot to contend with.
In the same way that no man is an Island, no organisation or IT department should be either. With all the challenges facing them is it any wonder that security and compliance is treated as a mutable priority? That said, regardless of the pressures ITDMs face, it doesn’t change security’s importance to the entire business – especially in the era of Digital Transformation and ever imaginative cyber-attacks.
With so many moving parts and layers within any business – let alone myriad dependencies and demand within and without the organisation – getting a handle on existing and emerging threats can seem insurmountable. There are so many routes towards ensuring the security of environments, networks and applications. There’s the human element too – staff, contractors, suppliers – all of whom can help or hinder compliance, security and operational integrity.
So…If resources are stretched. If immutable compliance deadlines loom. If there’s a skills gap.
Working with an expert partner can help. Not only can this augment scarce or stretched resources, it means businesses have an army of knowledge to hand – ideally one capable of delivering robustness, resilience, integrity, availability as well as compliance and security. And across technologies on both sides of the hybrid IT divide. Capable of communicating just as effectively in the board room as the data room… To staff as well as suppliers… To brains wired for business as much as those wired for technology.
A partner to help you identify, negotiate and overcome the ever changing and emerging threat-scape all companies face. Be that compliance or otherwise.
CISO and VCISO for New York Department of Financial Services - NYDFS
Department of Financial Services’ (NY DFS) new terms poised as gone into effect, banks and financial services companies operating in the state should have already implemented a security program, however, if you are not there yet we can help, don't get hit by fines.
One of the most discussed issues in the controversial proposal is the requirement to appoint a CISO (chief information security officer). The move was met by heavy criticism at a hearing in December last year, as we previously reported, leading to a massive backtrack from the DFS in a revised proposal.
Requirements of the CISO
The latest proposal removes any explicit requirement to hire a CISO, which is good news for many smaller or rural financial institutions that don’t currently have one in place. What this means, practically, is that the position is no longer necessarily exclusive. Banks can choose to designate someone to complete the tasks of a CISO while also performing other duties. Alongside this, the proposal does not state that the specific title of ‘CISO’ is required.
So what will the CISO (or CISO by any other name) be asked to do? The role now covers a broader set of responsibilities but in a less detailed manner. The designated person will have to provide an annual report to the board of directors (previously proposed as a biannual report) on the “cybersecurity program and material cybersecurity risks”, according to the proposal. It is now specified that the report must be “in writing” but it no longer needs to be provided to the NY DFS upon request.
The required content of the report will now also be less extensive. The CISO must identify and report only on material cyber risks rather than all cyber risks. This will involve “consider[ing]” those issues “to the extent applicable.” Additionally, the CISO will be able to tailor their focus to the issues appropriate to their organization.
Finding the right candidate
The NY DFS’ revision allowing the CISO to be an employee of the covered entity (i.e. an internal hire), or an affiliate or third-party service provider offers crucial flexibility for smaller financial institutions.
Companies with only a handful of employees – the most vocal in their frustration at the DFS’ initial plans – may look to shuffle their existing staff.
When doing that – or in making a new hire – there are certain things organizations need to look for. The CISO role is not just a tech-specific position, notes John Linkous, RSA Conference’s technology advisor, but they must now be “a trusted advisor to the business as a whole”. He adds:
“One of the most critical capabilities is simply the ability to understand the business much more intimately than his or her predecessors. Business drives the need for technology, and so security must be focused on how data is used within those business functions, across the end-to-end spectrum. Without a solid understanding of what the organization does, and how it makes money, an information security officer is going to have a fundamental disconnect with what’s needed to protect the enterprise.”
Third-party service providers or affiliates
Given the responsibility placed on the CISO, outsourcing the role to a third party can be an appealing proposition.
Going down this route presents its own set of issues, though. As TechTarget reported, third parties are “almost always” involved when it comes to cyber breaches – arguing that it is either through a lack of accountability or oversight. While service-level agreements (SLAs) are always advised, the DFS has taken steps to ensure the right measures are in place. In response to the fear that financial services firms would not always have sufficient power to force third parties to accept their preferred provisions, the NY DFS now dictates that all third-party services must be performed under contractual provisions rather than by way of “relevant guidelines for due diligence.”
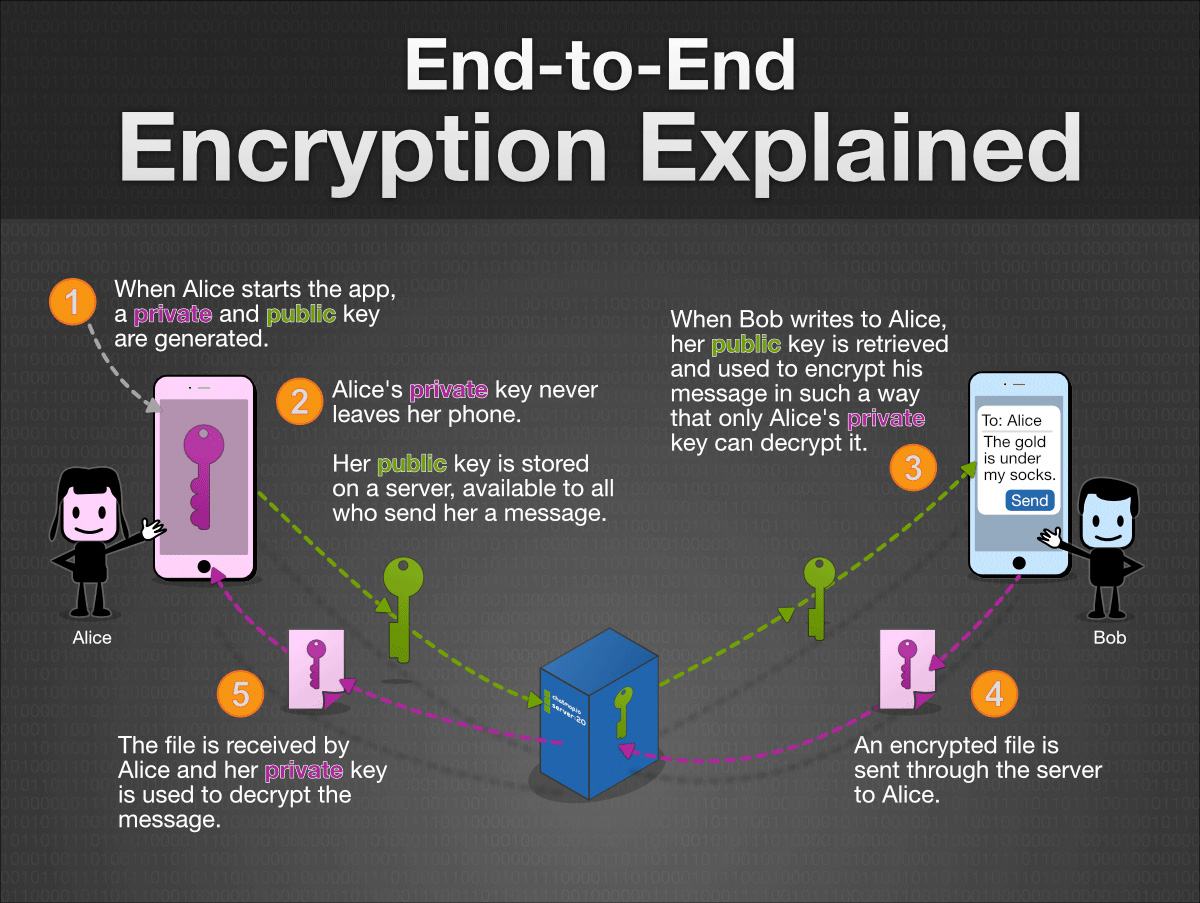
How End to End Encryption Works
2018, the digital era of the Internet, IOT and web technologies, the use of Encryption has become a mandatory part of our daily internet lifestyle. In this digital era peoples are doing business and banking transactions, shopping, communicating and sharing media on social media, reading online news and podcasts, etc. if the encryption is not present there to secure these stuff, everything could be turned into dark and hackers can get the superlative advantage from it.
Before talking about the End-to-End encryption, first, understand the term Encryption.
One can explain encryption in a multiple way, I am going to explain in simple terms.
Encryption: A security mechanism that uses complex hashing algorithms which protects the communication and information transmitting through one user (device) to another user(device). Hence, information exchanges like sharing personal details, financial details, and other confidential details over the internet could be secured with the help of this encryption mechanism.
Encryption mechanism ensures the information being exchanged over the internet is only accessible by the end users, no other person, attackers or robots may access it.
Plain Text vs Cipher Text
In Encryption mechanism, the information which is not encrypted is called as Plaintext and the encrypted information is called as ciphertext.
Encryption is characterized two main categories of Symmetric Key Encryption and Asymmetric Key Encryption.
Symmetric Key Encryption
For example, if a user(sender) tries to send hello message to another user (receiver), the message is being passed through the complex algorithm and encrypted using a key. now if the receiver wants to access this message the same key will be required to decrypt the message. This process of encryption and decryption with the same key is called as symmetric key encryption.
In symmetric key encryption, as the same key is being used for encryption and decryption of a message, the key will be known for both parties. Hence, if the key will be stolen or compromised, the whole security mechanism could be interrupted, and information may be compromised. So, in most cased Symmetric Key Encryption is not being used.
Asymmetric Key Encryption
In Asymmetric Key Encryption technology, two different keys are used for encryption and decryption process as the public key and private key. If the message is encrypted using the public, it will only be encrypted using its relevant private key of that public key and vice versa.
The public key remains known and the private key remains unknown.
The asymmetric key encryption is considered as the strongest security mechanism and being used worldwide for the encryption of information.
It is widely used as SSL Certificate encryption, which turns the website into HTTPS and delivers the safes web experience to users.
Let’s talk about End-to-End Encryption
Asymmetric Key Encryption is known is End-to-End Encryption. Here, the encryption will only be held over the end networks.
If a user is sending a message to another user, the messing will be transmitted through the secured channel. This message will be only encrypted at the end user’s device. It will not be tamper or changed in between.
For example, Social messaging app WhatsApp is using end-to-end encryption. Hence, the message will be readable by the end user only and it will not be interrupted by any attackers or cyber criminals.
Whether it’s a file exchange, media transfer, VOIP voice or video calls, End-to-End encryption can protect everything from theft.
Implementing End-to-End Encryption.
SSL Certificate encryption is End-to-End encryption where the information being exchanged over the internet will not be decrypted or tampered by any other person.
Here, the website admin needs to get an SSL Certificate from a trusted SSL Certificate Authority, once they issue the SSL, the admin needs to install it on the server.
Now the website URL will be turned into HTTPS which assured the business/website is legitimate and the information is protected using the End-to-End Encryption technology.
Today thousands of Banking websites, E-commerce Businesses, Social Media, Social Messaging Apps, Healthcare, Government and University departments are using the End-to-End encryption provided by SSL Certificate.
End to End Encryption
Important Reads