How End to End Encryption Works
2018, the digital era of the Internet, IOT and web technologies, the use of Encryption has become a mandatory part of our daily internet lifestyle. In this digital era peoples are doing business and banking transactions, shopping, communicating and sharing media on social media, reading online news and podcasts, etc. if the encryption is not present there to secure these stuff, everything could be turned into dark and hackers can get the superlative advantage from it.
Before talking about the End-to-End encryption, first, understand the term Encryption.
One can explain encryption in a multiple way, I am going to explain in simple terms.
Encryption: A security mechanism that uses complex hashing algorithms which protects the communication and information transmitting through one user (device) to another user(device). Hence, information exchanges like sharing personal details, financial details, and other confidential details over the internet could be secured with the help of this encryption mechanism.
Encryption mechanism ensures the information being exchanged over the internet is only accessible by the end users, no other person, attackers or robots may access it.
Plain Text vs Cipher Text
In Encryption mechanism, the information which is not encrypted is called as Plaintext and the encrypted information is called as ciphertext.
Encryption is characterized two main categories of Symmetric Key Encryption and Asymmetric Key Encryption.
Symmetric Key Encryption
For example, if a user(sender) tries to send hello message to another user (receiver), the message is being passed through the complex algorithm and encrypted using a key. now if the receiver wants to access this message the same key will be required to decrypt the message. This process of encryption and decryption with the same key is called as symmetric key encryption.
In symmetric key encryption, as the same key is being used for encryption and decryption of a message, the key will be known for both parties. Hence, if the key will be stolen or compromised, the whole security mechanism could be interrupted, and information may be compromised. So, in most cased Symmetric Key Encryption is not being used.
Asymmetric Key Encryption
In Asymmetric Key Encryption technology, two different keys are used for encryption and decryption process as the public key and private key. If the message is encrypted using the public, it will only be encrypted using its relevant private key of that public key and vice versa.
The public key remains known and the private key remains unknown.
The asymmetric key encryption is considered as the strongest security mechanism and being used worldwide for the encryption of information.
It is widely used as SSL Certificate encryption, which turns the website into HTTPS and delivers the safes web experience to users.
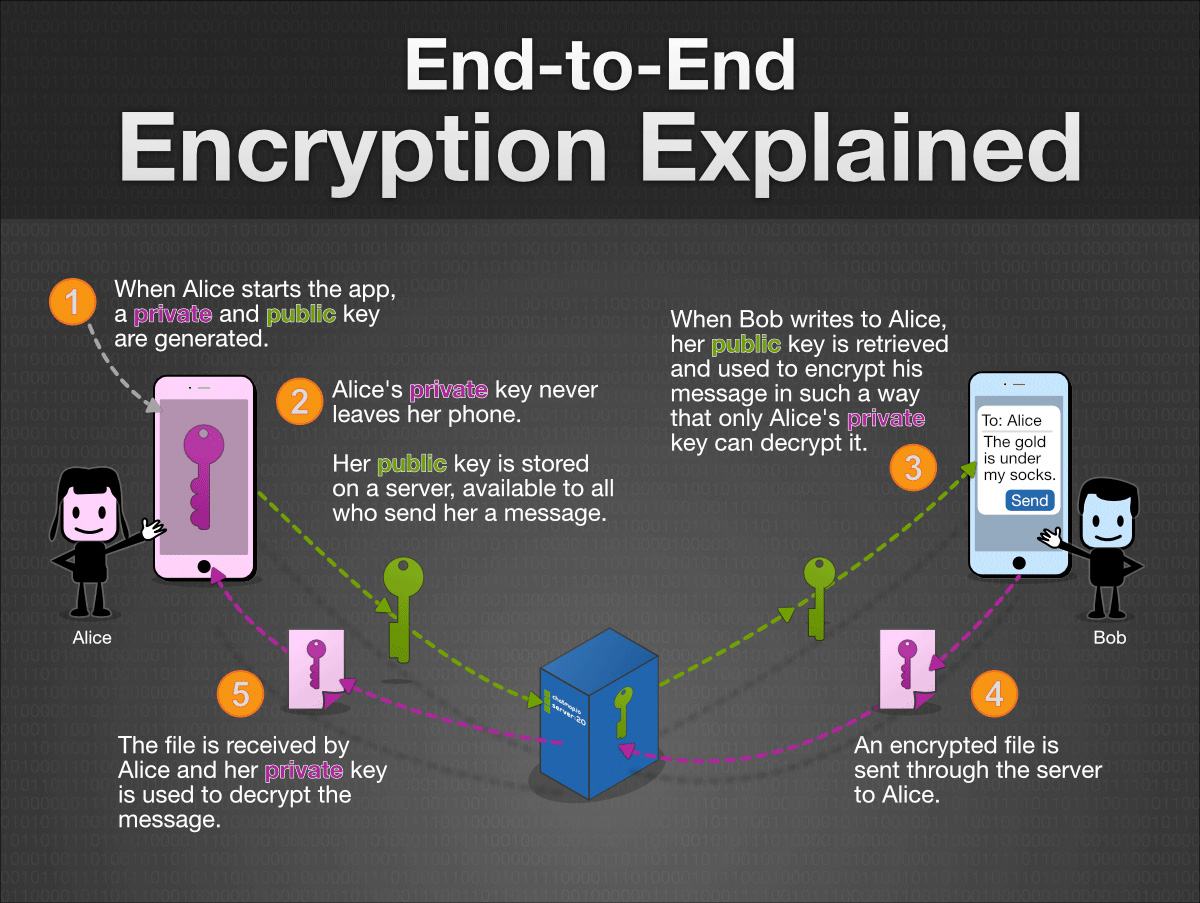
Let’s talk about End-to-End Encryption
Asymmetric Key Encryption is known is End-to-End Encryption. Here, the encryption will only be held over the end networks.
If a user is sending a message to another user, the messing will be transmitted through the secured channel. This message will be only encrypted at the end user’s device. It will not be tamper or changed in between.
For example, Social messaging app WhatsApp is using end-to-end encryption. Hence, the message will be readable by the end user only and it will not be interrupted by any attackers or cyber criminals.
Whether it’s a file exchange, media transfer, VOIP voice or video calls, End-to-End encryption can protect everything from theft.
Implementing End-to-End Encryption.
SSL Certificate encryption is End-to-End encryption where the information being exchanged over the internet will not be decrypted or tampered by any other person.
Here, the website admin needs to get an SSL Certificate from a trusted SSL Certificate Authority, once they issue the SSL, the admin needs to install it on the server.
Now the website URL will be turned into HTTPS which assured the business/website is legitimate and the information is protected using the End-to-End Encryption technology.
Today thousands of Banking websites, E-commerce Businesses, Social Media, Social Messaging Apps, Healthcare, Government and University departments are using the End-to-End encryption provided by SSL Certificate.
End to End Encryption
Important Reads