CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Enterprises understand cyber risks
Enterprises understand cyber risks
Hackers and cyber criminals often seek to exploit human errors like misconfigurations, poor security practices and the use of shadow IT.
In order to help businesses assess the risk CyberSecOP is launching an automated advanced persistent threat (APT) simulation platform, LocPar, to continuously expose all attack vectors, above and below the surface.
LocPar uses advanced attack techniques to expose the most critical blind spots. In the process, it provides data-driven remediation that focuses on an organization's most critical assets, reduces its IT risk and enables it to optimize its cyber resources.
"The best way to prevent a cyber attack is to identify in advance the attack vectors hackers will use to compromise an organization's critical assets," says CEO and co-founder of XM Cyber Noam Erez. "Even when an organization has deployed and configured modern security controls, applied patches and refined policies, it should still ask 'Are my crown jewels really secure?' as there is a plethora of ways hackers can still infiltrate the system and compromise critical assets. This is why we founded CyberSecOp: to equip enterprises with a continuous 360° view of which critical assets are at risk, what security issues they should focus on, and how best to harness their resources to resolve them."
Features of LocPar include full mapping of all attack paths at any given time, automatic adaptation to the context of the organization, using misconfigurations, user activity, credentials and security vulnerabilities in the network.
Comprehensive and up-to-date attack scenarios use the latest hackers' techniques and methods, giving the ability to detect and remediate IT-related risks in real-time. Reports are produced based on how critical the attack vector is.
Image Credit: SergeyNivens / depositphotos.com
Secure Your Website, from Cyber Attacks
The average website was attacked 44 times a day during the last quarter of 2017, according to new research from security specialist SiteLock.
The company analyzed six million sites to identify trends in the behavior and tactics of attackers. Though the number of attacks represents a 25 percent decrease over the previous quarter, it still means a site could be attacked 16,000 times a year.
"A decrease in attacks does not mean that websites are safer. In fact, it may even be the opposite," says Neill Feather, president of SiteLock on the company's blog. "Hackers are constantly trying new avenues and even leveraging older tactics that continue to be successful. As our research shows, cybercriminals are now able to successfully breach a site with fewer, more targeted attacks. Now more than ever, businesses need to evaluate their current security posture and ensure they have both the right technology and a response plan in place should a hack occur."
Among other findings are that around one percent of sites sampled are infected with malware each week. Yet only 19 percent of infected sites are blacklisted by search engines. WordPress sites using plugins are twice as likely to be infected as sites that don’t employ a content management system. In addition, 46 percent of infected WordPress sites have the latest core updates. The average number of infected files per site increased by 0.8 percent to 309.
The malware being used is increasingly complex too. 51 of the malware found was categorized as Encoded Malware, meaning it was randomly generated or difficult to decode. These are often parts of groups of files called 'attack kits'. Backdoors made up 12 percent of files, resulting in more files being uploaded to infected sites.
NYDFS Cybersecurity Retain a CISO, CSO -Regulation Compliance
With cyber-attacks on the rise and comprehensive federal cybersecurity policy lacking for the financial services industry, New York is leading the nation with strong cybersecurity regulation requiring, among other protective measures, set minimum standards of a cybersecurity program based on the risk assessment of the entity, personnel, training, and controls in place in order to protect data and information systems, said Superintendent in a press release issued by DFS, CyberSecOP helping financial organisation comply with the NYDFS manadates.
With the New York Department of Financial Services’ (NY DFS) new terms poised to come into effect next month, banks and financial services companies operating in the state must start preparing for the change.
One of the most discussed issues in the controversial proposal is the requirement to appoint a CISO (chief information security officer). The move was met by heavy criticism at a hearing in December last year, leading to a massive backtrack from the DFS in a revised proposal.
Requirements of the CISO
The latest proposal removes any explicit requirement to hire a CISO, which is good news for many smaller or rural financial institutions that don’t currently have one in place. What this means, practically, is that the position is no longer necessarily exclusive. Banks can choose to designate someone to complete the tasks of a CISO while also performing other duties. Alongside this, the proposal does not state that the specific title of ‘CISO’ is required.
So what will the CISO (or CISO by any other name) be asked to do? The role now covers a broader set of responsibilities but in a less detailed manner. The designated person will have to provide an annual report to the board of directors (previously proposed as a biannual report) on the “cybersecurity program and material cybersecurity risks”, according to the proposal. It is now specified that the report must be “in writing” but it no longer needs to be provided to the NY DFS upon request.
The required content of the report will now also be less extensive. The CISO must identify and report only on material cyber risks rather than all cyber risks. This will involve “consider[ing]” those issues “to the extent applicable.” Additionally, the CISO will be able to tailor their focus to the issues appropriate to their organization.
Finding the right candidate
The NY DFS’ revision allowing the CISO to be an employee of the covered entity (i.e. an internal hire), or an affiliate or third-party service provider offers crucial flexibility for smaller financial institutions.
Companies with only a handful of employees – the most vocal in their frustration at the DFS’ initial plans – may look to shuffle their existing staff.
When doing that – or in making a new hire – there are certain things organizations need to look for. The CISO role is not just a tech-specific position, notes John Linkous, RSA Conference’s technology advisor, but they must now be “a trusted advisor to the business as a whole”. He adds:
“One of the most critical capabilities is simply the ability to understand the business much more intimately than his or her predecessors. Business drives the need for technology, and so security must be focused on how data is used within those business functions, across the end-to-end spectrum. Without a solid understanding of what the organization does, and how it makes money, an information security officer is going to have a fundamental disconnect with what’s needed to protect the enterprise.”
Third-party service providers or affiliates
Given the responsibility placed on the CISO, outsourcing the role to a third party can be an appealing proposition.
Going down this route presents its own set of issues, though. As TechTarget reported, third parties are “almost always” involved when it comes cyber breaches – arguing that it is either through a lack of accountability or oversight. While service-level agreements (SLAs) are always advised, the DFS has taken steps to ensure the right measures are in place. In response to the fear that financial services firms would not always have sufficient power to force third parties to accept their preferred provisions, the NY DFS now dictates that all third-party services must be performed under contractual provisions rather than by way of “relevant guidelines for due diligence.”
Source: www.itgovernanceusa.com
Study Reveals 90 Percent of Businesses Will Use Biometric Authentication by 2020
Spiceworks today announced the results of a new survey examining the adoption and security of biometric authentication technology in the workplace. The results show 62 percent of organizations currently use biometric authentication technology, and an additional 24 percent plan to utilize it within the next two years. The findings indicate that although most IT professionals believe biometric authentication is more secure than traditional forms of authentication, such as text-based passwords, PIN numbers, and personal security questions, only 10 percent of respondents believe biometrics are secure enough to be used as the sole form of authentication.
Fingerprint and face scanners are most commonly used in the workplace
Fingerprint and face scanners are the most common types of biometric authentication used on corporate devices and services. The results show 57 percent of organizations are using fingerprint scanning technology, while 14 percent are using face recognition technology. Other biometric methods utilized include hand geometry recognition (5 percent), iris scanning technology (3 percent), voice recognition (2 percent), and palm-vein recognition (2 percent).
When further examining the types of fingerprint scanners organizations are using on company devices and services, the results show Apple Touch ID is the most commonly used at 34 percent, followed by Lenovo Fingerprint Manager (13 percent) and Samsung fingerprint readers (13 percent). Eleven percent of organizations are also using fingerprint scanners from Microsoft and Dell, while 23 percent are using fingerprint scanners from other vendors. Additionally, when examining the specific types of face and iris recognition technologies utilized, the results show 14 percent of organizations are using Apple Face ID, 13 percent are using Microsoft face login via Windows Hello, and 7 percent are using Android Face Unlock.
While 46 percent of organizations utilize biometric authentication on smartphones, 25 percent use it to authentication employees on laptops and 22 percent use it on tablets. Additionally, 17 percent of organizations use biometrics to verify employees on time clock systems, and 11 percent use it on door locks for the server room. Other uses for biometrics in the workplace include technology to authenticate employees on applications with sensitive data, wearables, and email.
A lack of transparency exists around the security of biometrics
Although biometric authentication in the workplace is already commonplace, many IT professionals still don’t trust the technology. More than 50 percent of IT professionals believe biometrics are harder to hack than traditional text-based passwords, but only 23 percent believe biometric authentication will replace traditional text-based passwords in the next two to three years.
IT professionals’ distrust around biometrics is potentially due to a lack of transparency from vendors around the security risks. According to the survey results, 65 percent of IT professionals believe there’s not enough transparency about the vulnerabilities discovered in biometric systems, and 63 percent believe there isn’t enough transparency regarding the privacy of biometric data collected by vendors. In fact, nearly 60 percent of IT professionals said they need more information about where technology vendors store biometric data.
“Many IT professionals aren’t convinced biometrics can serve as a secure and reliable replacement for the standard username and password combo,” said Peter Tsai, senior technology analyst at Spiceworks. “Unless technology vendors can address the security issues and privacy concerns associated with biometrics, the technology will likely be used side-by-side in the workplace with traditional passwords or as a secondary authentication factor for the foreseeable future.”
Compliance Complacency: Are your Compliant
Data is power. It’s a prime commodity for businesses, which in turn means it is constantly under threat. Just try and think back to a week where a data breach or cyber attacks did not hit the headlines, and you’ll struggle. Not only are these threats a growing problem for any organisation, but the issue becomes more paramount when combined with upcoming changes in compliance. The surge of data created by the digital age has called for a change in how organisations store and handle it. The consequences of non-compliance are well-documented by now, whether that’s in the form of a fine, insolvency or even closure.
Surely then it can be assumed that this issue is being taken sufficiently seriously by organisations across all industries? Initial findings from our recent global research[1] suggest otherwise.
Our inaugural The Little Book of IT study found that in the UK, 30 per cent of business respondents who classified their security technology as “fully implemented/integrated,” reported that no security improvements could be made. This bold assumption would infer that over a third of businesses believe their systems are fully prepared to deal with the security challenges facing them, and may explain why a seemingly inadequate 10% of IT budget is being spent on security provisions (which represents only 2.25% growth over the previous year’s expenditure, with next year’s spend set to be marginally even less at 1.86%). Whilst it’s nigh-on impossible to keep pace with cyber criminals, it is none-the-less vital to constantly evaluate the security protocols and tools an organisation has in place. To do otherwise is to risk leaving itself (and anyone connected to its systems) a sitting duck.
Surprisingly, the research also found that remaining secure to cyber threats is only the second highest IT priority, after changing IT infrastructure and cloud adoption. Businesses are either extremely relaxed or perilously unaware of the changing responsibilities and liabilities around compliance. Have we entered a period of compliance complacency? To do so would be unwise, given the upcoming changes in regulation. To add salt into the wound, just over half of respondents (51% stated they had been offered training to regulatory compliance.
It’s not the first time that the complacency label has been banded around when it comes to security (especially when pinning down responsibility) – and the above stats do infer such a laissez faire attitude. That said, a deeper dive into this research unveiled a far more complex situation. On further questioning, security was the number one factor taken into consideration when adopting new technology.
With this in mind it would seem less like complacency, and more confusion – with some areas of the business placing it with greater importance than others. What’s needed then is a more cohesive and integrated security and data integrity strategy. One that embraces all employees, albeit tailored to their specific business roles.
The changing cyber landscape has an impact upon, and requires responsibility from, everyone in the business: from the CEO through to freelance staff and not just the IT department. Security is just one aspect of a business’ IT strategy and teams still have to ensure both the day-to-day running of IT environments whilst still implementing the initiatives which it is hoped will help deliver enhanced business outcomes.
As The Little Book of IT study revealed, the issues and challenges of doing so are numerous. Whether it’s budget constraints impacting security in some way (48%) modernising legacy systems (65%), both are stealing time and focus from innovation. Meanwhile cloud adoption (52%), business analytics (37%) and digitalisation 35% exert great pressure – whether positive or negative – meaning the modern-day IT department has rather a lot to contend with.
In the same way that no man is an Island, no organisation or IT department should be either. With all the challenges facing them is it any wonder that security and compliance is treated as a mutable priority? That said, regardless of the pressures ITDMs face, it doesn’t change security’s importance to the entire business – especially in the era of Digital Transformation and ever imaginative cyber-attacks.
With so many moving parts and layers within any business – let alone myriad dependencies and demand within and without the organisation – getting a handle on existing and emerging threats can seem insurmountable. There are so many routes towards ensuring the security of environments, networks and applications. There’s the human element too – staff, contractors, suppliers – all of whom can help or hinder compliance, security and operational integrity.
So…If resources are stretched. If immutable compliance deadlines loom. If there’s a skills gap.
Working with an expert partner can help. Not only can this augment scarce or stretched resources, it means businesses have an army of knowledge to hand – ideally one capable of delivering robustness, resilience, integrity, availability as well as compliance and security. And across technologies on both sides of the hybrid IT divide. Capable of communicating just as effectively in the board room as the data room… To staff as well as suppliers… To brains wired for business as much as those wired for technology.
A partner to help you identify, negotiate and overcome the ever changing and emerging threat-scape all companies face. Be that compliance or otherwise.
CISO and VCISO for New York Department of Financial Services - NYDFS
Department of Financial Services’ (NY DFS) new terms poised as gone into effect, banks and financial services companies operating in the state should have already implemented a security program, however, if you are not there yet we can help, don't get hit by fines.
One of the most discussed issues in the controversial proposal is the requirement to appoint a CISO (chief information security officer). The move was met by heavy criticism at a hearing in December last year, as we previously reported, leading to a massive backtrack from the DFS in a revised proposal.
Requirements of the CISO
The latest proposal removes any explicit requirement to hire a CISO, which is good news for many smaller or rural financial institutions that don’t currently have one in place. What this means, practically, is that the position is no longer necessarily exclusive. Banks can choose to designate someone to complete the tasks of a CISO while also performing other duties. Alongside this, the proposal does not state that the specific title of ‘CISO’ is required.
So what will the CISO (or CISO by any other name) be asked to do? The role now covers a broader set of responsibilities but in a less detailed manner. The designated person will have to provide an annual report to the board of directors (previously proposed as a biannual report) on the “cybersecurity program and material cybersecurity risks”, according to the proposal. It is now specified that the report must be “in writing” but it no longer needs to be provided to the NY DFS upon request.
The required content of the report will now also be less extensive. The CISO must identify and report only on material cyber risks rather than all cyber risks. This will involve “consider[ing]” those issues “to the extent applicable.” Additionally, the CISO will be able to tailor their focus to the issues appropriate to their organization.
Finding the right candidate
The NY DFS’ revision allowing the CISO to be an employee of the covered entity (i.e. an internal hire), or an affiliate or third-party service provider offers crucial flexibility for smaller financial institutions.
Companies with only a handful of employees – the most vocal in their frustration at the DFS’ initial plans – may look to shuffle their existing staff.
When doing that – or in making a new hire – there are certain things organizations need to look for. The CISO role is not just a tech-specific position, notes John Linkous, RSA Conference’s technology advisor, but they must now be “a trusted advisor to the business as a whole”. He adds:
“One of the most critical capabilities is simply the ability to understand the business much more intimately than his or her predecessors. Business drives the need for technology, and so security must be focused on how data is used within those business functions, across the end-to-end spectrum. Without a solid understanding of what the organization does, and how it makes money, an information security officer is going to have a fundamental disconnect with what’s needed to protect the enterprise.”
Third-party service providers or affiliates
Given the responsibility placed on the CISO, outsourcing the role to a third party can be an appealing proposition.
Going down this route presents its own set of issues, though. As TechTarget reported, third parties are “almost always” involved when it comes to cyber breaches – arguing that it is either through a lack of accountability or oversight. While service-level agreements (SLAs) are always advised, the DFS has taken steps to ensure the right measures are in place. In response to the fear that financial services firms would not always have sufficient power to force third parties to accept their preferred provisions, the NY DFS now dictates that all third-party services must be performed under contractual provisions rather than by way of “relevant guidelines for due diligence.”
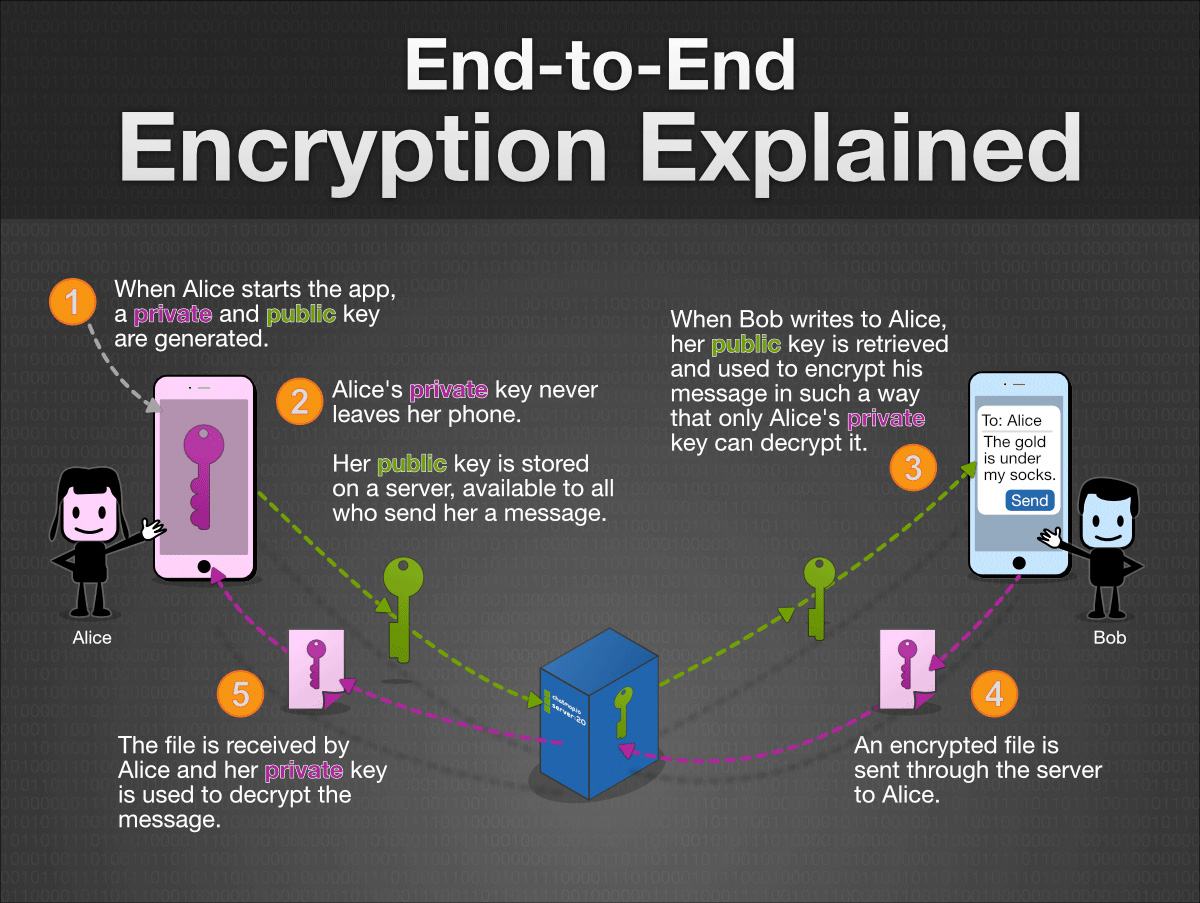
How End to End Encryption Works
2018, the digital era of the Internet, IOT and web technologies, the use of Encryption has become a mandatory part of our daily internet lifestyle. In this digital era peoples are doing business and banking transactions, shopping, communicating and sharing media on social media, reading online news and podcasts, etc. if the encryption is not present there to secure these stuff, everything could be turned into dark and hackers can get the superlative advantage from it.
Before talking about the End-to-End encryption, first, understand the term Encryption.
One can explain encryption in a multiple way, I am going to explain in simple terms.
Encryption: A security mechanism that uses complex hashing algorithms which protects the communication and information transmitting through one user (device) to another user(device). Hence, information exchanges like sharing personal details, financial details, and other confidential details over the internet could be secured with the help of this encryption mechanism.
Encryption mechanism ensures the information being exchanged over the internet is only accessible by the end users, no other person, attackers or robots may access it.
Plain Text vs Cipher Text
In Encryption mechanism, the information which is not encrypted is called as Plaintext and the encrypted information is called as ciphertext.
Encryption is characterized two main categories of Symmetric Key Encryption and Asymmetric Key Encryption.
Symmetric Key Encryption
For example, if a user(sender) tries to send hello message to another user (receiver), the message is being passed through the complex algorithm and encrypted using a key. now if the receiver wants to access this message the same key will be required to decrypt the message. This process of encryption and decryption with the same key is called as symmetric key encryption.
In symmetric key encryption, as the same key is being used for encryption and decryption of a message, the key will be known for both parties. Hence, if the key will be stolen or compromised, the whole security mechanism could be interrupted, and information may be compromised. So, in most cased Symmetric Key Encryption is not being used.
Asymmetric Key Encryption
In Asymmetric Key Encryption technology, two different keys are used for encryption and decryption process as the public key and private key. If the message is encrypted using the public, it will only be encrypted using its relevant private key of that public key and vice versa.
The public key remains known and the private key remains unknown.
The asymmetric key encryption is considered as the strongest security mechanism and being used worldwide for the encryption of information.
It is widely used as SSL Certificate encryption, which turns the website into HTTPS and delivers the safes web experience to users.
Let’s talk about End-to-End Encryption
Asymmetric Key Encryption is known is End-to-End Encryption. Here, the encryption will only be held over the end networks.
If a user is sending a message to another user, the messing will be transmitted through the secured channel. This message will be only encrypted at the end user’s device. It will not be tamper or changed in between.
For example, Social messaging app WhatsApp is using end-to-end encryption. Hence, the message will be readable by the end user only and it will not be interrupted by any attackers or cyber criminals.
Whether it’s a file exchange, media transfer, VOIP voice or video calls, End-to-End encryption can protect everything from theft.
Implementing End-to-End Encryption.
SSL Certificate encryption is End-to-End encryption where the information being exchanged over the internet will not be decrypted or tampered by any other person.
Here, the website admin needs to get an SSL Certificate from a trusted SSL Certificate Authority, once they issue the SSL, the admin needs to install it on the server.
Now the website URL will be turned into HTTPS which assured the business/website is legitimate and the information is protected using the End-to-End Encryption technology.
Today thousands of Banking websites, E-commerce Businesses, Social Media, Social Messaging Apps, Healthcare, Government and University departments are using the End-to-End encryption provided by SSL Certificate.
End to End Encryption
Important Reads