CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
3CX DesktopApp Supply Chain Attack: What You Need to Know
After being alerted by several security researchers of an ongoing supply chain attack in its 3CX DesktopApp, 3CX is currently working on a software update. According to the company's CEO, Nick Galea, the malware affects the Windows Electron client for customers running update 7. As an immediate response, the company has advised users to uninstall and reinstall the app, and in the meantime, use its PWA (progressive web application) client instead.
3CX is a Voice Over Internet Protocol (VoIP) IPBX software development company with over 600,000 customers and 12 million users in 190 countries. Its 3CX DesktopApp allows users to make calls, chat, video conference, and check voicemail using their desktop. Some of its customers include BMW, Honda, Ikea, Pepsi, and Toyota.
The ongoing attack was detected by security researchers at Sophos, Crowdstrike, and SentinelOne, who observed malicious activity originating from a trojanized version of the 3CX DesktopApp. Sophos reported that the software is a digitally signed version of the softphone desktop client for Windows and is packaged with a malicious payload. The application has been abused by the threat actor to add an installer that communicates with various command-and-control servers.
According to SentinelOne, the threat actor registered a massive attack infrastructure in February 2022 and is tracking the attack under the name SmoothOperator. Researchers noted that it is a chain attack that takes advantage of the DLL side-loading technique to load a malicious DLL that's designed to retrieve an icon file payload. The trojanized 3CX DesktopApp is the first stage in a multi-stage attack chain that pulls ICO files appended with base64 data from GitHub and ultimately leads to a third-stage infostealer DLL still being analyzed as of the time of writing.
Crowdstrike also found that the malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and hands-on-keyboard activity in a small number of cases. Sophos noted that the DLL side-loading is designed in such a way that users will not realize any difference while using the application. The information stealer can gather system information and sensitive data stored in Google Chrome, Microsoft Edge, Brave, and Mozilla Firefox browsers.
In conclusion, the ongoing supply chain attack on the 3CX DesktopApp has prompted urgent action from the company, with a software update in progress and a recommendation for users to switch to its PWA client in the meantime. Security researchers have detected malicious activity originating from the trojanized version of the app, which has been abused by the threat actor to communicate with command-and-control servers and steal sensitive data. As always, it is important to stay vigilant and take immediate action in response to any security alerts or warnings.
Phishing Attack Prevention: What is Phishing?
What is Phishing?
Phishing is the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about to protect themselves.
Phishing Attack Prevention:
Why are so many companies vulnerable to phishing? Not having the right tools in place and failing to train employees on their role in information security.
Employees possess credentials and overall knowledge that is critical to the success of a breach of the company's security. One of how an intruder obtains this protected information is via phishing. The purpose of phishing is to collect sensitive information to use that information to gain access to otherwise protected data, networks, etc. A phisher's success is contingent upon establishing trust with its victims. We live in a digital age, and gathering information has become much easier as we are well beyond the dumpster diving days.
How do I protect against phishing attacks?
Free Email Protection
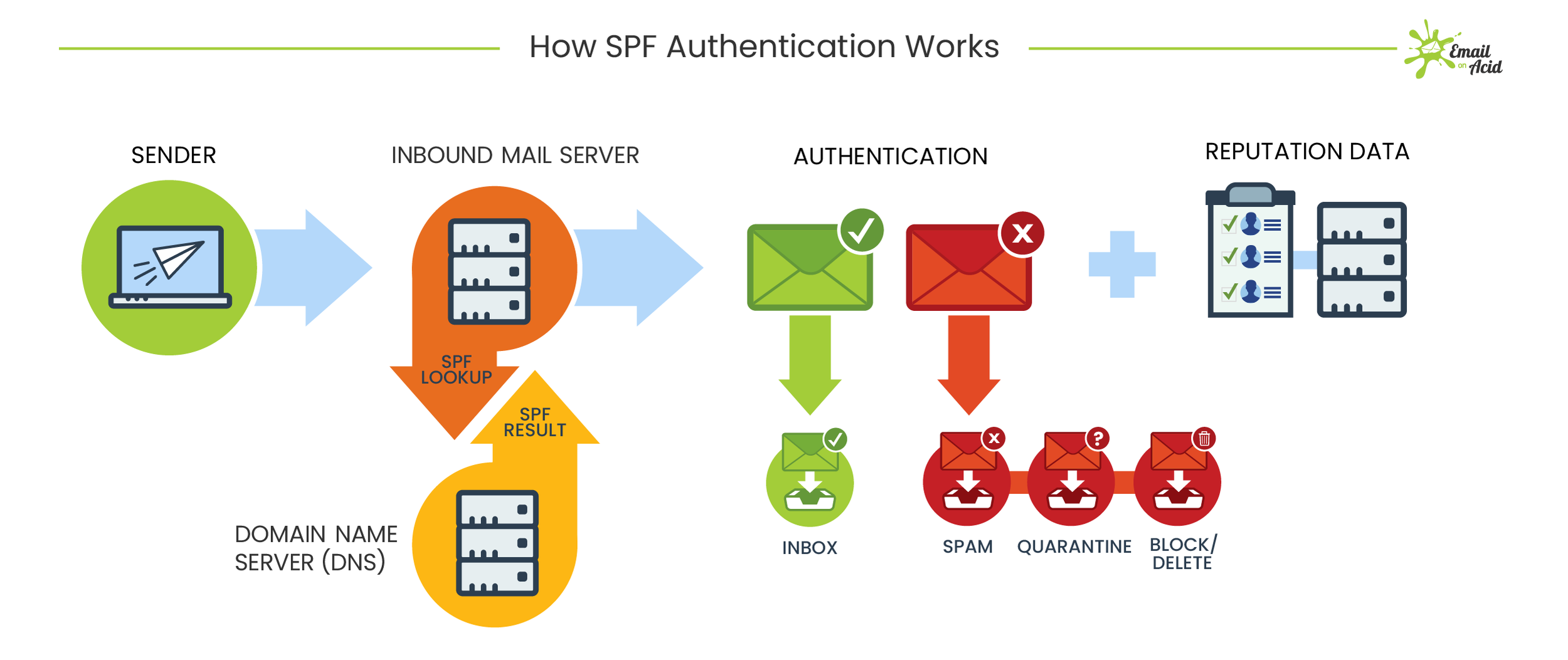
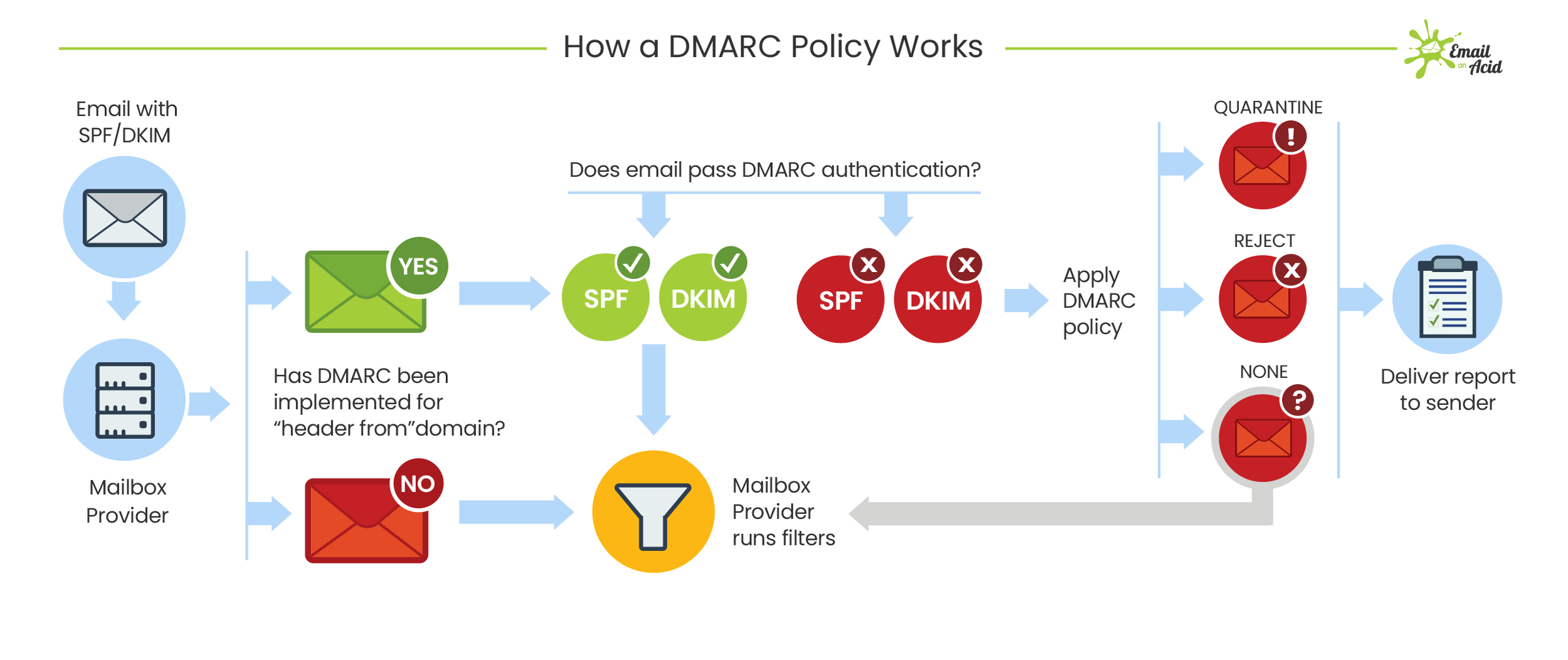
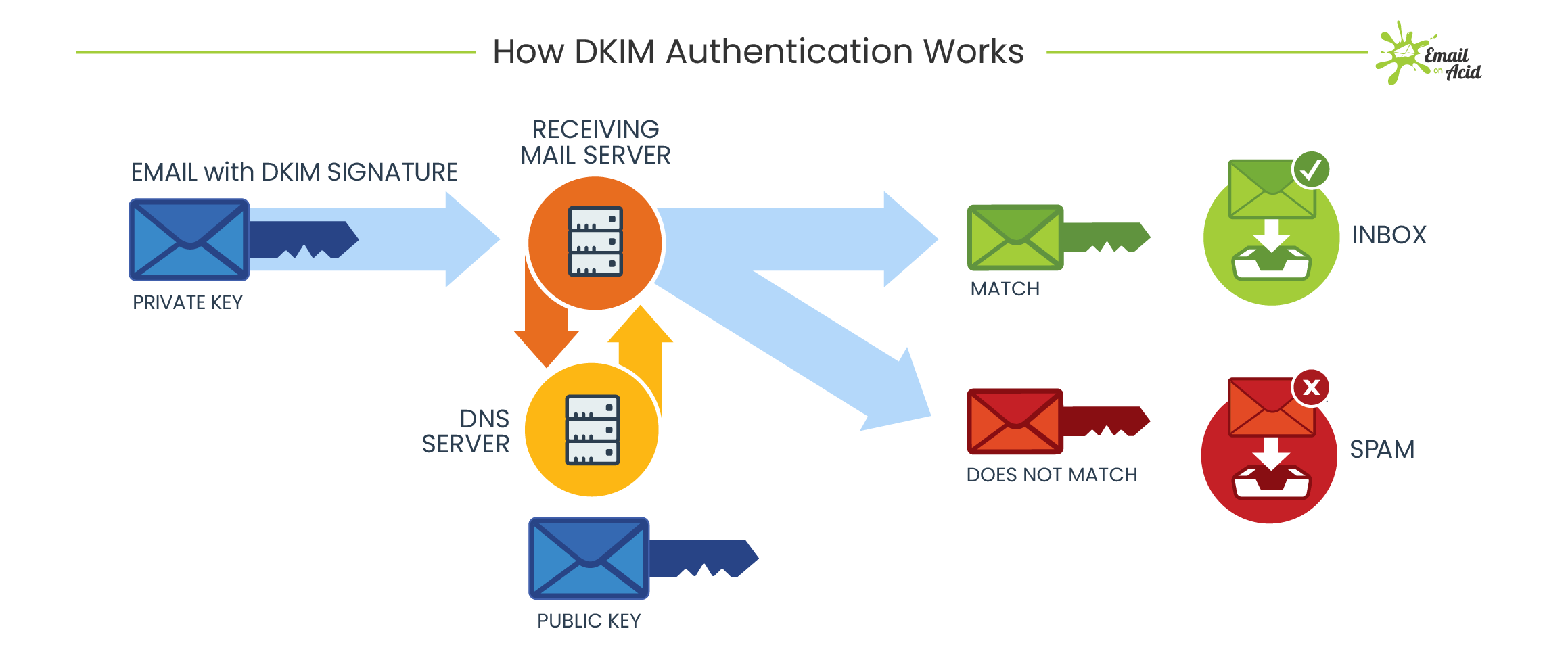
Free protocols that help organizations improve email security; Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM) were developed. SPF cross-checks the sender’s IP address with an approved list of IP addresses, and DKIM uses an encrypted digital signature to protect emails. While these are both individually effective, they have their own set of flaws. DMARC, developed in 2012, is a protocol that uses both SPF and DKIM authentication to secure email and has a mechanism that sends the domain owner a report whenever an email fails DMARC validation.
But here’s the thing: a recent report from phishing specialist Agari states that only 1/3 of the Fortune 500 have configured DMARC.
User education
One way to protect your organization from phishing is user education. Education should involve all employees. High-level executives are often a target. Teach them how to recognize a phishing email and what to do when they receive one. Simulation exercises are also key for assessing how your employees react to a staged phishing attack.
Security technology
No single cybersecurity technology can prevent phishing attacks. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control.
How does phishing work?
Phishing starts with a fraudulent email or other communication that is designed to lure a victim. The message is made to look as though it comes from a trusted sender. If it fools the victim, he or she is coaxed into providing confidential information, often on a scam website. Sometimes malware is also downloaded onto the target’s computer.
What are the dangers of phishing attacks?
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing.
Types of Phishing
Deceptive Phishing. The term "phishing" originally referred to account theft using instant messaging but the most common broadcast method today is a deceptive email message. Messages about the need to verify account information, system failure requiring users to re-enter their information, fictitious account charges, undesirable account changes, new free services requiring quick action, and many other scams are broadcast to a wide group of recipients with the hope that the unwary will respond by clicking a link to or signing onto a bogus site where their confidential information can be collected.
Malware-Based Phishing refers to scams that involve running malicious software on users' PCs. Malware can be introduced as an email attachment, as a downloadable file from a web site, or by exploiting known security vulnerabilities--a particular issue for small and medium businesses (SMBs) who are not always able to keep their software applications up to date.
Keyloggers and Screenloggers are particular varieties of malware that track keyboard input and send relevant information to the hacker via the Internet. They can embed themselves into users' browsers as small utility programs known as helper objects that run automatically when the browser is started as well as into system files as device drivers or screen monitors.
Session Hijacking describes an attack where users' activities are monitored until they sign in to a target account or transaction and establish their bona fide credentials. At that point the malicious software takes over and can undertake unauthorized actions, such as transferring funds, without the user's knowledge.
Web Trojans pop up invisibly when users are attempting to log in. They collect the user's credentials locally and transmit them to the phisher.
Hosts File Poisoning. When a user types a URL to visit a website it must first be translated into an IP address before it's transmitted over the Internet. The majority of SMB users' PCs running a Microsoft Windows operating system first look up these "host names" in their "hosts" file before undertaking a Domain Name System (DNS) lookup. By "poisoning" the hosts file, hackers have a bogus address transmitted,taking the user unwittingly to a fake "look alike" website where their information can be stolen.
System Reconfiguration Attacks modify settings on a user's PC for malicious purposes. For example: URLs in a favorites file might be modified to direct users to look alike websites. For example: a bank website URL may be changed from "bankofabc.com" to "bancofabc.com".
Data Theft. Unsecured PCs often contain subsets of sensitive information stored elsewhere on secured servers. Certainly PCs are used to access such servers and can be more easily compromised. Data theft is a widely used approach to business espionage. By stealing confidential communications, design documents, legal opinions, employee related records, etc., thieves profit from selling to those who may want to embarrass or cause economic damage or to competitors.
DNS-Based Phishing ("Pharming"). Pharming is the term given to hosts file modification or Domain Name System (DNS)-based phishing. With a pharming scheme, hackers tamper with a company's hosts files or domain name system so that requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site. The result: users are unaware that the website where they are entering confidential information is controlled by hackers and is probably not even in the same country as the legitimate website.
Content-Injection Phishing describes the situation where hackers replace part of the content of a legitimate site with false content designed to mislead or misdirect the user into giving up their confidential information to the hacker. For example, hackers may insert malicious code to log user's credentials or an overlay which can secretly collect information and deliver it to the hacker's phishing server.
Man-in-the-Middle Phishing is harder to detect than many other forms of phishing. In these attacks hackers position themselves between the user and the legitimate website or system. They record the information being entered but continue to pass it on so that users' transactions are not affected. Later they can sell or use the information or credentials collected when the user is not active on the system.
Search Engine Phishing occurs when phishers create websites with attractive (often too attractive) sounding offers and have them indexed legitimately with search engines. Users find the sites in the normal course of searching for products or services and are fooled into giving up their information. For example, scammers have set up false banking sites offering lower credit costs or better interest rates than other banks. Victims who use these sites to save or make more from interest charges are encouraged to transfer existing accounts and deceived into giving up their details.
Prevent DDoS attacks across your enterprise
DDoS (Distributed Denial of Service) attacks feature amongst the most dreaded kinds of cyber attacks, for any enterprise today. This is especially because, as the name itself suggests, there it causes a total denial of service; it exhausts all resources of an enterprise network, application or service and consequently it becomes impossible to gain access to the network, application or the service.
In general, a DDoS attack is launched simultaneously from multiple hosts and it would suffice to host the resources, the network and the internet services of enterprises of any size. Many prominent organizations today encounter DDoS attacks on a daily basis. Today DDoS attacks are becoming more frequent and they are increasing in size, at the same time becoming more sophisticated. In this context, it becomes really important that enterprises look for DDoS attack prevention services, in fact the best DDoS attack prevention services, so as to ensure maximum protection for their network and data.
The different kinds of DDoS attacks
Though there are different kinds of DDoS attacks, broadly speaking there are three categories into which all the different kinds of DDoS attacks would fit.
The first category is the volumetric attacks, which include those attacks that aim at overwhelming network infrastructure with bandwidth-consuming traffic or by deploying resource-sapping requests. The next category, the TCP state-exhaustion attacks, refer to the attacks that help hackers abuse the stateful nature of the TCP protocol to exhaust resources in servers, load balancers and firewalls. The third category of DDoS attacks, the application layer attacks, are basically the ones targeting any one aspect of an application or service at Layer 7.
Of the above-mentioned three categories, volumetric attacks are the most common ones; at the same time there are DDoS attacks that combine all these three vectors and such attacks are becoming commonplace today.
DDoS attacks getting sophisticated, complex and easy-to-use
Cybercriminals today are getting cleverer and smarter. They tend to package complex, sophisticated DDoS attack tools into easy-to-use downloadable programs, thereby making it easy even for non-techies to carry out DDoS attacks against organizations.
What are the main drivers behind DDoS attacks? Well, there could be many, ranging from ideology or politics to vandalism and extortion. DDoS is increasingly becoming a weapon of choice for hacktivists as well as terrorists who seek to disrupt operations or resort to extortion. Gamers too use DDoS as a means to gain competitive advantage and win online games.
There are clever cybercriminals who use DDoS as part of their diversionary tactics, intending to distract organizations during APT campaigns that are planned and executed in order to steal data.
How to prevent DDoS attacks
The first thing that needs to be done, to prevent DDoS attacks from happening, is to secure internet-facing devices and services. This helps reduce the number of devices that can be recruited by hackers to participate in DDoS attacks.
Since cybercriminals abuse protocols like NTP, DNS, SSDP, Chargen, SNMP and DVMRP to generate DDoS traffic, it’s advisable that services that use any of these ought to be carefully configured and run on hardened, dedicated servers.
Do repeated tests for security issues and vulnerabilities. One good example is doing penetration tests for detecting web application vulnerabilities.
Ensure that your enterprise implements anti-spoofing filters as covered in IETF Best Common Practices documents BCP 38 and BCP 84. This is because hackers who plan DDoS attacks would generate traffic with spoofed source IP addresses.
Though there are no fool-proof techniques that can prevent DDoS attacks completely, you can ensure maximum protection by ensuring proper configuration of all machines and services. This would ensure that attackers don’t harness publicly available services to carry out DDoS attacks.
It’s to be remembered that it’s difficult to predict or avoid DDoS attacks and also that even an attacker with limited resources can bring down networks or websites. Hence, for any organization, it becomes important that the focus is always on maximum level protection for enterprise networks, devices, websites etc.