CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
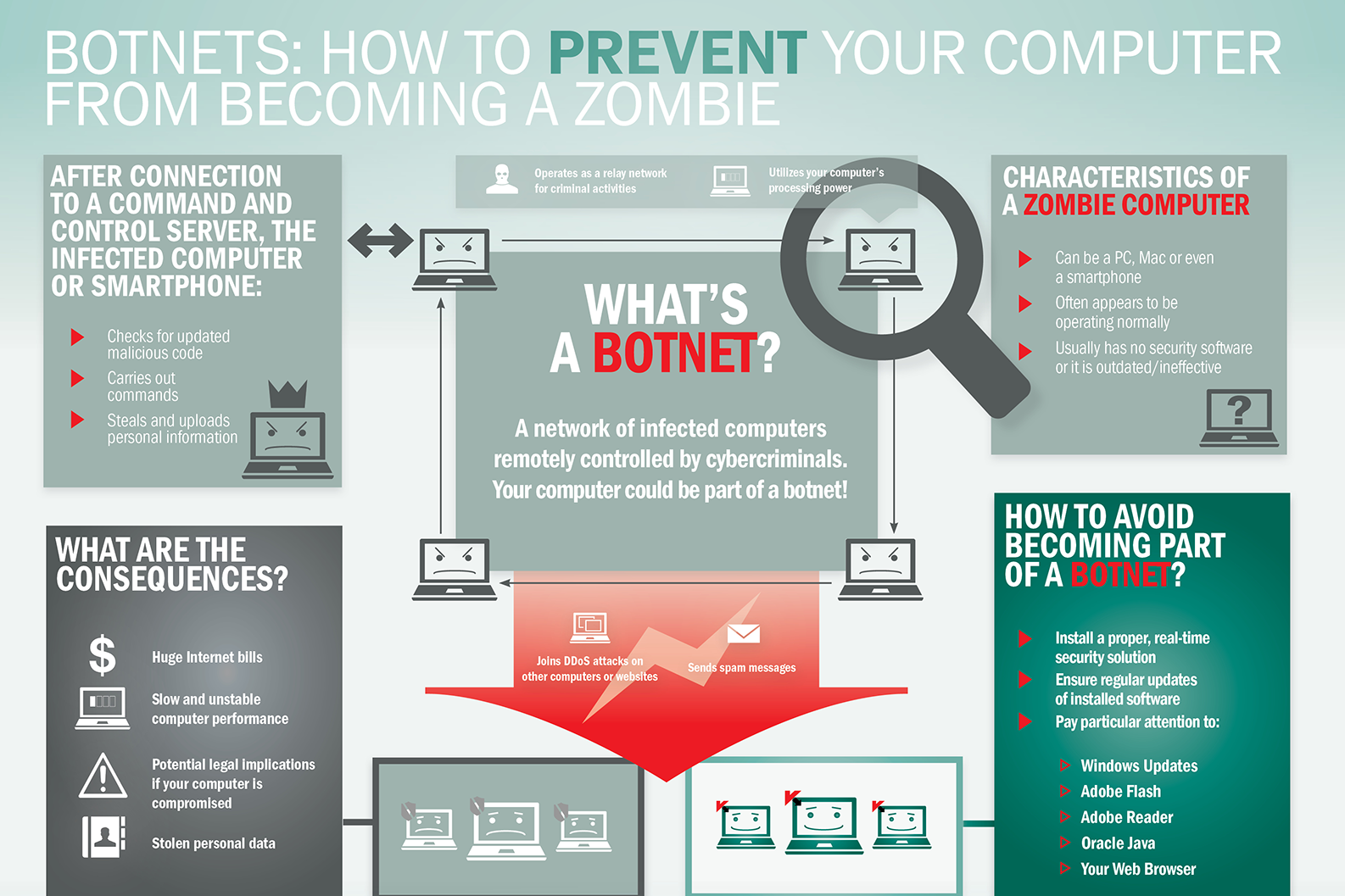
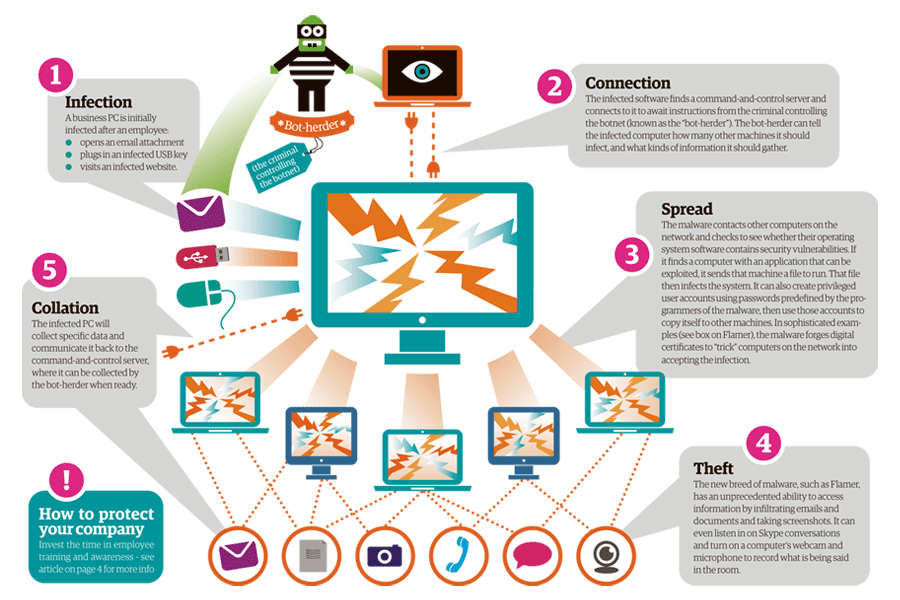
What is Botnet - Cybercriminals #1 Weapon
The word Botnet is formed from the words ‘robot’ and ‘network’. Cybercriminals use special Trojan viruses to breach the security of several users’ computers, take control of each computer and organise all of the infected machines into a network of ‘bots’ that the criminal can remotely manage.
Botnet Prevention- What is Botnet
How Botnets can impact you
Often, the cybercriminal will seek to infect and control thousands, tens of thousands or even millions of computers – so that the cybercriminal can act as the master of a large ‘zombie network’ – or ‘bot-network’ – that is capable of delivering a Distributed Denial of Service (DDoS) attack, a large-scale spam campaign or other types of cyberattack.
In some cases, cybercriminals will establish a large network of zombie machines and then sell access to the zombie network to other criminals – either on a rental basis or as an outright sale. Spammers may rent or buy a network in order to operate a large-scale spam campaign.
How to prevent your computer becoming part of a Botnet
Installing effective anti-malware software will help to protect your computer against Trojans and other threats.
Cyber Security Developments
Cyber Security Is The Backbone Any Online Businesses – Here Are Some Quick Tips To Keep Yourself Informed About The Latest Threats Surrounding Your Business.
Cyber Security Developments
Within a standard nine to five working day, it’s said that there are almost two million data records lost or stolen. Cybercrime has become something of an epidemic in recent years – and it’s no exaggeration to say that everyone is at risk.
Hackers operate in an increasingly complex way and are happy to target small businesses and individuals, who are most likely to be vulnerable to attack. The nature of the threat changes as technology advances and so the only way to stay safe is to stay up to date.
But that’s easier said than done, right? How do you keep up to date with the latest cybersecurity developments?
Follow The News
When it comes to cyber security, ignorance is not bliss – it’s a recipe for disaster. It’s imperative that you identify and follow a news feed that you can trust. By doing so, you can keep on top of any fresh threats that have emerged, learn lessons from other cyber attacks and pick up the latest tips and advice from influencers and experts in this field.
News from this sector really shouldn’t be seen as the preserve of IT specialists – the scale and nature of the threat suggest that this should be of interest to everyone. There’s a burgeoning band of podcasts available on the subject for people who prefer to digest content in this way too.
Bring Up The ‘Security Question’
If you think that installing an anti-virus program is enough, then you’re mistaken. Don’t just presume that you’re safe because you have this because this is merely the first line of defense to root out attacks. By adopting a safety first mindset you can ensure that the way you handle your data is less risky.
Whether it’s securing your Wi-Fi network at home, managing and updating your passwords on a regular basis or the way you collect, collate and analyze data throughthe point of sale software at work, continually ask yourself ‘is this safe?’ Just as ignorance isn’t bliss, complacency could prove your undoing. Place ‘security’ high on the list of credentials to consider when buying new software or hardware, don’t just go for the cheapest option.
Training
Even the experts are constantly having to refresh their understanding of the threat posed by cyber attacks. It pays to search out training opportunities, especially if you’re a business. You are, after all, only as safe as the people operating your software and systems and you don’t want to put the security of your business in the hands of someone who is unsure about what they are doing. Individuals and businesses alike can find free learning materials on Cybrary to help plug any knowledge gaps they have.
It’s Good To Talk
Cyber attacks are incredibly common – but people don’t often enough talk about their experiences. Perhaps you’re afraid or embarrassed to have been caught out? There’s no need to be. In fact, talking with friends and colleagues could really help you to stay safe. Pass on tips about new apps, good software, neat tips and tricks and any new cyber attack tactics you have come across and you can help to do your own bit to combat the criminals.
By keeping up to speed with security news, refreshing your training, sharing tips and tricks and adopting a safety first attitude you’ll give yourself the best possible chance of staying on top of cyber security developments and, best of all, safe.
Secure Your Website, from Cyber Attacks
The average website was attacked 44 times a day during the last quarter of 2017, according to new research from security specialist SiteLock.
The company analyzed six million sites to identify trends in the behavior and tactics of attackers. Though the number of attacks represents a 25 percent decrease over the previous quarter, it still means a site could be attacked 16,000 times a year.
"A decrease in attacks does not mean that websites are safer. In fact, it may even be the opposite," says Neill Feather, president of SiteLock on the company's blog. "Hackers are constantly trying new avenues and even leveraging older tactics that continue to be successful. As our research shows, cybercriminals are now able to successfully breach a site with fewer, more targeted attacks. Now more than ever, businesses need to evaluate their current security posture and ensure they have both the right technology and a response plan in place should a hack occur."
Among other findings are that around one percent of sites sampled are infected with malware each week. Yet only 19 percent of infected sites are blacklisted by search engines. WordPress sites using plugins are twice as likely to be infected as sites that don’t employ a content management system. In addition, 46 percent of infected WordPress sites have the latest core updates. The average number of infected files per site increased by 0.8 percent to 309.
The malware being used is increasingly complex too. 51 of the malware found was categorized as Encoded Malware, meaning it was randomly generated or difficult to decode. These are often parts of groups of files called 'attack kits'. Backdoors made up 12 percent of files, resulting in more files being uploaded to infected sites.