CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Fusing People and Technology: Igniting Customer-Centric Transformation and Elevating Cybersecurity Maturity
In the dynamic landscape of modern business, customer-centric transformation stands as the beacon guiding organizations toward sustainable success. Today, we delve into the symbiotic relationship between people and technology, exploring how this fusion fuels customer-centric transformation and fortifies cybersecurity maturity.
Unveiling the Nexus:
Understanding the Dynamics:
At the heart of customer-centric transformation lies the intricate interplay between people and technology. While technology serves as the enabler, it is the human touch that infuses empathy, creativity, and adaptability into transformative endeavors.Unveiling Transformation Catalysts:
Empowered Workforce: Empowering employees with cutting-edge technology and fostering a culture of innovation unleashes their potential to deliver unparalleled customer experiences.
Data-Driven Insights: Leveraging advanced analytics and AI empowers organizations to glean actionable insights from vast troves of data, enabling personalized customer interactions and informed decision-making.
Agile Technologies: Embracing agile technologies equips organizations with the agility to swiftly respond to evolving customer needs and market dynamics, driving continuous innovation and competitive differentiation.
The Cybersecurity Imperative:
Far from being a mere byproduct, cybersecurity plays a pivotal role in fueling customer-centric transformation and fortifying organizational resilience. Here's how:Trust and Confidence: Robust cybersecurity measures instill trust and confidence among customers, fostering long-lasting relationships and brand loyalty.
Data Protection: By safeguarding customer data from cyber threats, organizations uphold their commitment to privacy and compliance, enhancing customer trust and mitigating reputational risks.
Innovation Security: Cybersecurity underpins innovation security, ensuring that customer-centric initiatives remain shielded from cyber threats and vulnerabilities.
Resilience Against Cyber Threats: A cyber-resilient infrastructure fortifies organizations against cyber threats, ensuring uninterrupted customer service delivery and business continuity.
Harnessing the Synergy:
In the realm of customer-centric transformation, the fusion of people and technology emerges as the cornerstone of success. By empowering employees, leveraging data-driven insights, and embracing agile technologies, organizations can deliver unparalleled customer experiences while fortifying their cybersecurity maturity.
As we embark on this transformative journey, let us recognize the indispensable role of cybersecurity in safeguarding customer trust and organizational resilience. By prioritizing cybersecurity measures, organizations can amplify the impact of customer-centric initiatives while fortifying their defenses against cyber threats.
Together, let us harness the transformative power of people and technology to propel our organizations toward customer-centric excellence and cybersecurity resilience.
For further exploration of these transformative insights and tailored cybersecurity solutions, we invite you to connect with our expert cyber teams at CyberSecOp.
Databricks: AI Could Become So Intelligent That It Surpasses Human Intelligence
Databricks is a unified analytics platform that helps businesses accelerate time to insights with data engineering, data science, and machine learning. Databricks is at the front and center of machine learning, and its capabilities are vast.
Some of the key capabilities of Databricks include:
Data engineering: Databricks makes it easy to ingest, clean, and prepare data for analysis. Databricks also provides a variety of tools for data transformation and data modeling.
Data science: Databricks provides a complete environment for data scientists to build, train, and deploy machine learning models. Databricks also provides a variety of tools for data visualization and model evaluation.
Machine learning: Databricks provides a variety of machine learning algorithms and frameworks. Databricks also provides a variety of tools for model deployment and monitoring.
In addition to its core capabilities, Databricks also offers a number of additional features, such as:
Collaboration: Databricks makes it easy for teams to collaborate on data projects. Databricks provides a variety of tools for sharing data, code, and notebooks.
Security: Databricks is built on a secure foundation. Databricks provides a variety of features for data security, such as role-based access control, data encryption, and audit logging.
Governance: Databricks provides a variety of features for data governance, such as data lineage tracking, data quality checks, and data policy enforcement.
Databricks is a powerful platform that can help businesses accelerate time to insights with data engineering, data science, and machine learning. If you are looking for a platform to help you with your data projects, Databricks is a great option.
Here are some additional thoughts on the potential dangers of AI, as raised by Ian Hogarth:
AI could become so intelligent that it surpasses human intelligence. This could lead to a situation where AI is able to make decisions that are better than humans, but which humans do not understand. This could have a profound impact on society, as humans would no longer be in control of their own destiny.
AI could become so powerful that it could pose a threat to humanity. This could happen if AI is used for malicious purposes, such as developing autonomous weapons or creating surveillance systems that are too powerful to be controlled by humans.
AI could become so ubiquitous that it could become difficult to distinguish between humans and machines. This could lead to a situation where humans are no longer unique or special.
It is important to be aware of the potential dangers of AI, and to take steps to mitigate these risks. One way to do this is to ensure that AI is developed and used in a responsible manner. This means ensuring that AI is aligned with human values, and that it is used for good rather than for evil.
It is also important to remember that AI is a tool, and like any tool, it can be used for good or for evil. It is up to us to decide how AI is used, and to ensure that it is used for the benefit of humanity.
Chat GPT 3 and Chat GPT 4: How They're Helping the World
In the last few years, artificial intelligence has revolutionized the way we interact with technology. One of the most remarkable developments in this field is the creation of advanced chatbots powered by natural language processing (NLP). Among them, Chat GPT 3 and Chat GPT 4 are two of the most popular and powerful NLP models.
Chat GPT 3, released in 2020 by OpenAI, is a third-generation language model that can generate human-like responses to a wide range of prompts, from simple questions to complex essays. Its developers trained it on a massive corpus of text data, including books, articles, and websites, using an unsupervised learning algorithm that allowed it to learn patterns and structures in language without explicit guidance from humans.
Since its release, Chat GPT 3 has been used for a variety of applications, such as chatbots, language translation, content creation, and even coding. Its ability to understand natural language and generate coherent responses has made it a valuable tool for businesses, developers, and researchers alike.
Chat GPT 4, which is currently in development and expected to be released in the near future, promises to take NLP to the next level. According to OpenAI, Chat GPT 4 will be even more powerful and versatile than its predecessor, with the ability to perform tasks that are currently beyond the reach of AI, such as reasoning and common-sense understanding.
The Benefits of Chat GPT 3 and Chat GPT 4
The benefits of Chat GPT 3 and Chat GPT 4 are numerous and far-reaching. Here are a few examples:
Improved Customer Experience: Chatbots powered by Chat GPT 3 and Chat GPT 4 can provide personalized and natural interactions with customers, improving the overall experience and satisfaction.
Language Translation: The ability of Chat GPT 3 and Chat GPT 4 to understand and generate language can be used to create better translation services, improving communication and understanding between people from different cultures and languages.
Content Creation: Chat GPT 3 and Chat GPT 4 can generate high-quality content for a variety of purposes, such as marketing, journalism, and education, saving time and resources for businesses and individuals.
Education: Chat GPT 3 and Chat GPT 4 can be used to create intelligent tutoring systems, helping students learn more effectively and efficiently.
Who is Using Chat GPT?
Many companies and organizations are already using Chat GPT 3 for various applications. Some of the notable examples are:
Microsoft: Microsoft has integrated Chat GPT 3 into its Power Virtual Agents platform, enabling developers to create conversational AI experiences with ease.
OpenAI: OpenAI has developed GPT-3-powered chatbots that can perform various tasks, such as writing emails, generating code, and even composing poetry.
Intel: Intel has used Chat GPT 3 to create an AI-powered chatbot to help customers find the right products and services.
The Future of Chat GPT
As AI technology continues to evolve, the future of Chat GPT looks promising. With the release of Chat GPT 4, we can expect even more advanced and sophisticated NLP models that can perform tasks that were previously thought impossible. In the coming years, we may see the emergence of AI-powered virtual assistants that can understand and respond to our needs naturally and intuitively, revolutionizing the way we interact with technology.
Conclusion
Chat GPT 3 and Chat GPT 4 are two of the most exciting developments in the field of artificial intelligence. Their ability to understand and generate language has opened up a world of possibilities.
Known Cyber Espionage Group and Advanced Persistent Threats (APTs)
The primary purpose of cyber espionage groups and advanced persistent threats (APTs) is to gather sensitive information covertly from target organizations or individuals. This information can include a wide range of data, such as intellectual property, trade secrets, military plans, political intelligence, and more.
APTs are called "advanced" because they use advanced tactics and techniques to infiltrate and compromise target systems. They are called "persistent" because they often maintain a long-term presence on a target's systems to continue gathering information.
Cyber espionage groups and APTs are often sponsored by governments or other organizations, and they may target a wide range of sectors, including government, military, finance, and more. The information they gather can be used for various purposes, including military advantage, economic gain, and political leverage.
Here are a few things you will need to know to understand this blog:
Compromise: When a system or network is compromised, an unauthorized party has gained access to it. This could be due to a security vulnerability or a successful cyber attack.
Cyber espionage: Cyber espionage refers to the practice of collecting sensitive information covertly through the use of computer networks and the internet, often for military or political purposes.
Exploit: An exploit is a vulnerability or weakness in a computer system, network, or application that can be exploited by an attacker to gain unauthorized access or perform other malicious actions.
Ransomware: Ransomware is malware that encrypts a victim's files, making them inaccessible until a ransom is paid to the attacker.
Breach: A breach is an incident in which a security system or protocol has been successfully attacked or bypassed.
Phishing: Phishing is a type of cyber attack that involves tricking people into revealing sensitive information, such as login credentials or financial information, by pretending to be a legitimate entity. This is often done through fake emails or websites.
Known Cyber Espionage Group and Advanced Persistent Threats
There are many known cyber espionage groups and advanced persistent threats (APTs) that have been identified by cybersecurity researchers. Some examples include:
APT1 (also known as Comment Crew or Shanghai Group): A Chinese APT that has been active since 2004 and has been linked to several high-profile cyber espionage campaigns.
APT28 (also known as Fancy Bear or Sofacy Group): A Russian APT that has been active since at least 2007 and has been linked to cyber espionage campaigns against governments, military organizations, and other high-value targets.
APT29 (also known as Cozy Bear or The Dukes): Another Russian APT that has been active since at least 2008 and has been linked to cyber espionage campaigns against a wide range of targets, including government agencies, think tanks, and political organizations.
APT3 (also known as Gothic Panda or UPS Team): A Chinese APT that has been active since at least 2010 and has been linked to cyber espionage campaigns against a wide range of targets, including governments, military organizations, and businesses.
APT10 (also known as Stone Panda or MenuPass Group): A Chinese APT that has been active since at least 2010 and has been linked to cyber espionage campaigns against a wide range of targets, including governments, military organizations, and businesses.
Cyber Espionage Group and Advanced Persistent Threats Tools
Cyber espionage groups and advanced persistent threats (APTs) use various tools and techniques to infiltrate and compromise target systems. These can include:
Malware: APTs often use malware to infect and compromise target systems. This can include viruses, trojans, worms, ransomware, and other types of malicious software.
Spearphishing: APTs may use spearphishing attacks to trick target individuals into revealing sensitive information or installing malware. Spearphishing attacks are highly targeted and often involve using fake emails or websites that appear legitimate.
Vulnerabilities: APTs may exploit vulnerabilities in software or systems to gain access to a target's systems. This can include known vulnerabilities that have not been patched, as well as zero-day vulnerabilities (vulnerabilities that are unknown to the vendor and have not yet been patched).
Command and control servers: APTs may use command and control servers to remotely control the malware they have deployed on a target's systems and to exfiltrate stolen data.
Custom tools: APTs may use custom tools developed specifically for their operations. These tools may be designed to evade detection or to perform specific tasks, such as stealing specific types of data or taking control of systems.
How to Protect System Form Cyber Espionage Groups and Advanced Persistent Threats?
Here are a few steps that organizations and individuals can take to protect their systems from cyber espionage groups and advanced persistent threats (APTs):
Keep software and systems up to date: Make sure to apply the latest security updates and patches for all software and systems. This can help to close known vulnerabilities that could be exploited by APTs.
Use antivirus and firewall software: Install and regularly update antivirus and firewall software to help protect against malware and other threats.
Use strong, unique passwords: Use strong, unique passwords for all accounts and do not reuse passwords across different accounts.
Enable two-factor authentication: Use two-factor authentication, which requires a second form of authentication in addition to a password, whenever possible. This can help to protect against attacks that rely on stolen passwords.
Be cautious of emails and links: Be cautious of emails and links, particularly those that come from unknown sources. Do not click on links or download attachments from untrusted sources, as they may contain malware.
Educate employees: Educate employees about the risks of cyber attacks and teach them how to recognize and avoid suspicious emails and other threats.
Conduct regular security assessments: Conduct regular security assessments to identify vulnerabilities and to ensure that security measures are effective.
Are you worried about cyber espionage?
CyberSecOp managed services help organizations by providing the expertise and resources; we are a specialized cybersecurity provider for organizations that may not have the in-house expertise or resources to manage their cybersecurity effectively.
Some common types of managed services in the context of APTs and cyber espionage may include:
Threat intelligence and monitoring: Offer real-time monitoring for APTs and other threats, as well as analysis of threat intelligence data.
Vulnerability management: Offer services to help organizations identify and address vulnerabilities in their systems and applications.
Security incident response: Offer support to organizations in responding to security incidents, including providing guidance on how to contain and mitigate the effects of an attack.
Security testing and assessment: Providers may offer services to help organizations assess the effectiveness of their current security measures and identify areas for improvement.
CyberSecOp use MITRE ATT&CK to help organizations better understand the tactics, techniques, and procedures used by attackers and design more effective defenses against them. We also use it in relation to incident response, allowing organizations to quickly identify what stage of an attack they are dealing with and take appropriate action.
Using MITRE ATT&CK to provide services, it helps your clients improve their cybersecurity posture and defend against cyber attacks. This could involve providing guidance on how to implement controls to mitigate specific attack techniques, conducting assessments to identify vulnerabilities and areas for improvement, or providing incident response support.
Don't Forget the Fundamentals on World Backup Day 2022
March 31st is apparently world backup day! Who knew? In honor of that it seemed like a good time for a quick post extolling the virtues of backups. According to the “WorldBackupDay” website, 21% of people have never taken a backup and 30% of computers are already infected with malware. While these stats are related to individuals and not necessarily businesses the stats sound about right.
Take Backups!
Regardless of whether you are a small business or a global Fortune 500 company, backups are an essential part of your organization's risk management plan. It’s easy to be lulled into complacency. Just the other day I was working with an organization in the mechanical service delivery industry who’s entire “IT Infrastructure” was a single 2017 iMac. They never bothered with any additional machines, backups and other such items because they had been told that Mac’s were “bulletproof” and not susceptible to the common maladies of the humble PC. Unfortunately, their Mac was susceptible to good old fashioned old age and corrupt updates. As a result they found themselves in a position where they had a large proposal for a job due the next day and the only place it existed was on this one broken Mac. Now fortunately for them, we were able to recover the system and restore their data, but what if we hadn’t been able to? It is absolutely critical, regardless of the size of your organization that you have a backup solution in place tailored to your specific needs. Stay tuned for some suggestions on backup providers we love at the end of this article!
Test your Backups!
This might seem like a no-brainer, but in addition to taking backups, it's critically important that you TEST your backups. Having a plan and procedure in place for how to recover your data in the event of a disaster is just as important as taking the backup in the first place! In my last example of the company with a single iMac. What if they had set up icloud and automatically configured their file to sync there. If I had asked the owner of the business if he had the password for the icloud account or even knew what account icloud was associated with, I wonder if he would have known? Having a documented plan that outlines where your backups go, what authentication is used to access them, how frequently they are taken, and how to restore them to a device is critical. If you are a larger organization you probably want to start having conversations about RTO and RPO at this point as well and ensuring your backup solution can meet those goals. (Recovery Time Objective, Recovery Point Objective.) Essentially, how long will it take to recover my data and how much time passes between backups, or put more simply, how much data can I afford to lose? 1 Day’s Worth? 1 Weeks worth? Less? More? Make sure your backup solution can meet your specific needs and goals!
Protect your Backups!
Finally, congrats if you're taking and testing your backups! Are you also protecting your backups? You’re probably thinking, protecting my backups?! What’s this guy going on about now? Consider this, you backup your information every night and test it regularly. You sleep easy at night knowing that you can recover should the worst happen. However, what you don’t know, is that earlier last month one of your employee’s laptops was infected with a virus. This virus replicated across your organization but stayed dormant, collecting information about your company and environment but not taking any malicious actions yet. The threat actor discovers that your backups run nightly and are stored for 4 months on a network share. The virus then deletes all of your backups and begins encrypting your files. When you return to work the next day and find all of your computers and files encrypted, you attempt to recover from backup only to find your backups have been deleted! This is an oversimplification of the process but this is essentially what the bad guys are doing. There are many ways to prevent this sort of attack including storing backups in offline or immutable data stores, encrypting your backups and storing multiple copies of every backup in different locations. At this point you might be thinking “I can simply copy files to an external drive of some sort on a regular basis right?” , but what if something happens to that drive? As the old timer’s say, “two is one and one is none”. The idea is that if you only have one, something could happen to it and then you have none. Have a backup plan for your backup plan!
Conclusion
Now that you’re completely terrified know that there are solutions out there for all of these problems. Proper backup planning is a key component of every organization's Disaster Recovery, Business Continuity and Incident Response Planning. If you are looking for assistance with any of those plans, make sure you give us at CyberSecOp a call, we would love to help you with this.
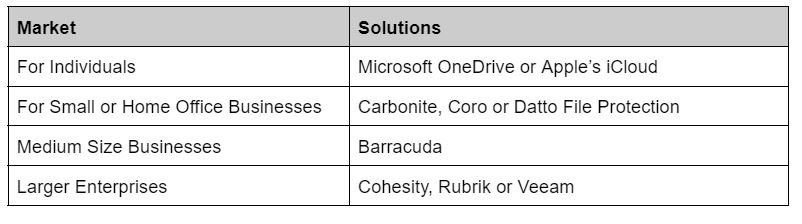
In the meantime if you're looking for somewhere to start with backup’s here are some of our favorites.
Author: Timothy Burger
Penetration Testing and its Benefits
Understanding your vulnerabilities through vulnerability and penetration testing can play an essential role in your firm’s security. We recommend the steps below to sideline these threats:
Discover if your systems are prepared for a cyber-attack
A security expert or ethical hacker will launch a simulated attack using external and internal attacks on your servers, web apps, wireless networks, intranets, network devices, mobile devices, and any other entry point.
Reporting with findings on vulnerabilities in your systems
Once the simulation is complete, the security team will present reports of their findings and recommend the next steps for securing your systems. Since there are several potential entry points into your plans, the team will attempt to exploit those vulnerabilities.
Know where your weaknesses lie and patch up those vulnerabilities before they can be exploited
Conduct an IT penetration testing to identify gaps in your security system, problems with your IT security policy, and vulnerabilities in your firewall and or antivirus. You will obtain a report with all the problematic access points in your system and suggestions for hardware and software improvements. The test will help you determine if you may need to upgrade your Firm’s security.
Internal vulnerabilities
Whether a disgruntled employee or accidental, internal vulnerabilities can be a window for malicious actors to exploit.
Not all Ethical Hackers are created equally
Be sure to hire the most seasoned experts in the field. Your ethical hacker will attempt to exploit the vulnerabilities as a real hacker would – but the effectiveness of the penetration test will ultimately depend on the amount of experience the engineer has.
Once is not enough
As we know, hackers have been becoming increasingly bold with their techniques to infiltrate the most sophisticated systems yet, as proven in the Sunburst Hack; therefore, CyberSecOp recommends testing your systems quarterly and keeping up with systems patches and updates.
CyberSecOp offers:
CyberSecOp has security experts with a combined experience of 40 years. Ask about our pen test sample report.
CyberSecOp is an ISO 27001 Certified Cyber Security Consulting Firm
CyberSecOp is proud ISO 27001 Certified Organization
The team at CyberSecOp is ISO/IEC 27001:2013 (ISO 27001) certified.
International Organization for Standardization (ISO) is an internationally recognized standard that ensures that firms such as CyberSecOp, meet best practices for information security management systems and vigorous risk-based framework approach.
We are committed to following a high-quality and consistent security management system. A-lign, an independent, third-party auditor, found CyberSecOp to have technical controls in place and formalized IT Security policies and procedures. A-lign is an ISO / IEC 27001 certification body accredited by the ANSI-ASQ National Accreditation Board (ANAB) to perform ISMS 27001 certifications. Therefore, through ISO 27001, we have developed and implemented processes and procedures in order to provide requirements for establishing, implementing, maintaining, and continually improving an information security management system. The entire certification leads us to the appropriate requirements for an Information Security Management System (ISMS) in our company — a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management processes.
Achieving the ISO 27001 certification is the result of a great amount of effort, dedication, and involvement from every member of the CyberSecOp team. We are constantly challenging ourselves to improve our service and provide the highest security and privacy standards to meet or exceed the needs and expectations of our customers.
Author: Carlos Neto
Information Security Officer