CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
CyberSecOp News and Insight Chronicles
Welcome to CyberSecOp News and Insight Chronicles, your go-to destination for the latest updates, insights, and analysis on the ever-evolving world of cybersecurity.
1. New Cyber Threats on the Horizon
In today's interconnected world, cyber threats continue to evolve alarmingly. Security experts warn of a new breed of malware targeting critical infrastructure, including power grids and transportation systems. Stay informed to stay protected.
2. Rise of Ransomware Attacks
Ransomware attacks are making headlines again, with reports of significant corporations falling victim to sophisticated ransomware campaigns. As businesses increasingly rely on digital infrastructure, the need for robust cybersecurity measures has never been more critical.
3. The Role of AI in Cybersecurity
Artificial intelligence plays an increasingly important role in cybersecurity for defenders and attackers. From AI-driven threat detection to automated hacking techniques, understanding the intersection of AI and cybersecurity is critical to staying ahead of emerging threats.
4. Privacy Concerns in the Age of Big Data
As technology advances, privacy and data security concerns are growing. From social media platforms to smart home devices, individuals and organizations must grapple with the ethical implications of collecting and storing vast amounts of personal data.
5. Cybersecurity Legislation and Policy
Governments worldwide are grappling with regulating cybersecurity in an increasingly digital world. From data protection laws to international agreements on cyber warfare, policymakers face complex challenges in safeguarding the digital realm.
6. The Human Element of Cybersecurity
While technological solutions are essential, the human element of cybersecurity must be considered. From employee training to cultivating a culture of security awareness, organizations must prioritize people alongside technology to mitigate cyber risks effectively.
Stay Informed, Stay Secure
Cybersecurity is a dynamic and ever-changing field; staying informed is the first defense against cyber threats. Join us at CyberSecOp News and Insight as we continue to explore the latest developments, trends, and insights shaping the future of cybersecurity. Remember, knowledge is power; we can build a safer digital world together.
Insights from Verizon's 2024 Data Breach Investigations Report
Understanding today’s hyper-evolving threat landscape is critical for organizations to protect their critical data. Verizon's 2024 Data Breach Investigations Report (DBIR) provides invaluable insights into emerging trends and challenges in cybersecurity, offering actionable recommendations for strengthening defenses.
Key Findings:
Exploitation of Zero-Day Vulnerabilities: The report highlights a significant increase in attacks leveraging zero-day vulnerabilities, such as the MOVEit exploit, which saw a staggering 180% surge in incidents. These vulnerabilities are prime targets for threat actors, particularly in ransomware and extortion schemes.
Rise of Ransomware and Extortion Attacks: Ransomware and extortion attacks continue to proliferate, comprising 32% of all breaches. With cybercriminals refining their tactics for maximum financial gain, organizations face heightened risks of data extortion and disruption.
Human Factor in Breaches: Despite advancements in technology, human error remains a prevalent contributor to breaches, accounting for 68% of incidents. This underscores the importance of cybersecurity awareness training in empowering employees to recognize, report and mitigate potential threats.
Errors Leading to Breaches: The report highlights a concerning increase in breaches resulting from unintended errors, such as misconfigurations and data mismanagement. Strengthening data governance frameworks and adherence to security policies and protocols is crucial to minimizing these avoidable lapses.
Effectiveness of Phishing Awareness: Phishing attacks have become more persistent and focused. Though organizations are making strides in educating employees to identify and report phishing attempts, The rapid response times required to counter phishing threats underscore the need for ongoing awareness training and incident response readiness.
Implications for Cybersecurity Strategy:
Organizations must prioritize proactive cybersecurity measures not only to mitigate their risks and safeguard their assets, they need to know what their loss landscape looks like. Implementing robust password management, Multi-Factor Authentication (MFA), and Privilege Management solutions are examples of proven solutions that can help fortify an organization’s defenses against Cyber-crime.
How CyberSecOp Can Assist:
CyberSecOp offers tailored solutions to address the evolving cybersecurity landscape and mitigate emerging threats. Our portfolio of proven, award winning services empower organizations to be more aware of their threat landscape and prepare themselves with proactive response measures. Additionally, our team of cybersecurity experts provides comprehensive guidance on implementing robust security measures, conducting risk assessments, and ensuring compliance with industry regulations.
By partnering with CyberSecOp, organizations can enhance their cybersecurity posture, mitigate cyber risks, and maintain trust in an increasingly interconnected world.
Strengthening Security: Understanding Password Management, MFA, and Privilege Management
Safeguarding sensitive data requires a comprehensive strategy that encompasses more than traditional security measures. As organizations navigate the persistent threat of credential theft, adopting robust password management, Multi-Factor Authentication (MFA), and Privilege Management solutions is essential.
Password Management: Password management involves implementing policies and tools to regulate password creation, storage, and rotation. These three simple steps enable organizations to enforce strong password policies, securely store credentials, and ensure regular updates, reducing the risk of unauthorized access. Strong password management is crucial as it is the first defense against unauthorized entry into systems and data breaches.
Multi-Factor Authentication (MFA): Multi-Factor Authentication (MFA) provides an additional layer of security by requiring users to provide multiple verification forms before accessing systems or data. MFA significantly mitigates the risk of credential-based attacks, even if passwords are compromised. MFA enhances security by adding an extra barrier that malicious actors must overcome to gain unauthorized access.
Privilege Management: Privilege Management limits access to sensitive data and resources within an organization. It is crucial in maintaining data integrity and protecting critical assets from malicious actors. Only authorized users have the necessary permissions to access specific information or perform certain actions. Privilege Management helps prevent unauthorized access, data breaches, and insider threats by enforcing granular access controls and monitoring user privileges.
Summary:
Enhance Security Posture: Implement robust password management, MFA, and Privilege Management solutions to strengthen your organization's security posture and resiliency against cyber threats.
Regulatory Compliance: Effective password and user privilege management helps organizations comply with industry regulations and data protection laws, such as GDPR and PCI DSS.
Reduced Risk of Data Breaches: These measures significantly reduce the likelihood of data breaches and financial losses associated with cyberattacks by mitigating the risk of unauthorized access and credential theft.
Proactive Monitoring: Continuous monitoring for credential leaks and unauthorized access is essential to promptly detect and mitigate potential risks, safeguard sensitive data, and preserve organizational reputation.
How CyberSecOp Can Assist: CyberSecOp offers a comprehensive portfolio of services, such as Managed SOC or dark web monitoring services, to help organizations detect compromised credentials and proactively safeguard their data. Additionally, our team of cybersecurity experts provides tailored guidance and support in implementing robust security measures, conducting risk assessments, and ensuring compliance with industry regulations. By partnering with CyberSecOp, organizations can strengthen their defenses against cyber threats, protect sensitive information, and maintain trust with stakeholders in today's interconnected world.
Cybersecurity Defense: Crafting a Successful Vulnerability Management Process Framework
Fortifying your defenses against the evolving threat landscape starts with addressing the gaps within your vulnerability management programs. In this blog, we delve into the intricate process of crafting a successful vulnerability management process framework, highlighting key challenges, strategies, and real-world scenarios.
Understanding the Landscape: The Importance of Process
The cornerstone of effective vulnerability management starts with the process. While technology and skilled professionals are vital components, the absence of well-defined processes can undermine these efforts, leading to inefficiencies and missed opportunities. Establishing clear workflows and transparent priorities is essential to ensuring the success of vulnerability management initiatives.
Challenges and Solutions: Building Robust Processes
Crafting a successful vulnerability management process framework has its challenges. Organizations must navigate various hurdles to establish effective processes, from defining effective workflows to prioritizing risks based on potential impact. Automation, continuous improvement, and adherence to established cybersecurity frameworks are key strategies for overcoming these challenges and building a resilient foundation for vulnerability management.
Real-World Scenario: Learning from Experience
Recently, the CyberSecOp team encountered a client struggling with inconsistent reporting, communication failures, and ineffective remediation plans due to the absence of robust processes in their vulnerability management program. This scenario underscores the critical importance of well-defined processes enabling capable individuals and advanced technology. Organizations can enhance their vulnerability management program and mitigate potential risks by developing clear policies, standard operating procedures, and a continuous improvement framework.
Conclusion: Forging Resilience Through Collaboration
In this dynamic, ever-evolving landscape of cyber-risk security, organizations must embrace a holistic approach to vulnerability management, addressing the challenges within each leg of the three-legged stool: technology, people, and processes. By investing in cohesive, integrated, forward-looking vulnerability management strategies, organizations can safeguard their digital assets and position themselves as leaders in the ongoing battle against cyber adversaries.
Stay Vigilant, Stay Secure
At CyberSecOp, we remain committed to empowering organizations with the knowledge and tools they need to navigate the complexities of the digital landscape securely. Let us forge a resilient foundation that protects your valuable assets and strengthens your cybersecurity posture.
Thank you for your continued trust and partnership. Do you Have questions about email protection, cyber defenses, or business security? Contact us today at 866-973-2677.
Give Your Endpoint Protection Program the Attention It Deserves
We are excited to share insights on the critical importance of endpoint security in today's evolving cyber threat landscape. At CyberSecOp, we recognize that adequate endpoint security is foundational to safeguarding your organization against cyberattacks and data breaches. We explore why your endpoint strategy deserves your undivided attention and provide actionable recommendations to enhance your endpoint protection program.
Understanding the Endpoint Threat Landscape
The endpoint threat landscape continues to evolve, with studies indicating that up to 90% of successful cyberattacks originate at endpoint devices. Regardless of organization size or industry, all entities are susceptible to cyber threats targeting endpoints. With remote workforces being more pervasive than ever before, there are more personal devices, wireless networks, and reliance on being productive outside the office’s four walls, maintaining visibility and managing endpoints has become increasingly challenging.
Navigating the Challenges of a Decentralized Workforce
The rise of remote workforces has expanded the attack surface, making endpoint management more complex. Organizations must contend with the proliferation of personal devices in the workplace and the need to implement effective mobile device management and endpoint policies. Endpoint detection and response (EDR) solutions are crucial in managing decentralized workforces, providing visibility and security across many endpoints.
Addressing Risks from Non-Traditional Devices
The emergence of non-traditional endpoint devices, such as smartwatches and IoT devices, introduces new avenues for cyber exploitation. Organizations must adapt their security strategies to encompass these diverse endpoints and mitigate associated risks effectively.
Optimizing Tool Coverage and Compliance
Legacy antivirus solutions are no longer sufficient to protect against modern cyber threats. Organizations must evaluate their cybersecurity toolsets to ensure comprehensive coverage and avoid redundancy. Furthermore, maintaining regulatory compliance and meeting cyber insurance requirements are paramount for endpoint security programs.
Future-Proofing Your Endpoint Protection Platform
Endpoint security is not just another tool but a foundational aspect of any cybersecurity program. By integrating endpoint security into your overall security stack and considering all defense strategies, organizations can effectively enhance their cyber resilience and mitigate emerging threats.
Concluding Thoughts: Strengthening Your Cyber Defense
Now is the time to prioritize, assess, and elevate your endpoint protection program. With advanced solutions in place, organizations can secure their cyber infrastructure, enhancing their overall cyber resilience.
At CyberSecOp, we are committed to helping organizations navigate the complexities of the modern threat landscape and strengthen their cybersecurity posture. If you want to learn more about how the right endpoint solution can benefit your business, we invite you to contact us for a consultation.
Thank you for your attention. We look forward to partnering with you to enhance your cybersecurity ecosystem defenses.
Why Cybersecurity and Compliance Starts at the Top
In today's digital age, cybersecurity and compliance have become paramount concerns for organizations across industries. As cyber threats evolve and regulatory requirements become increasingly stringent, businesses must adopt a top-down approach to security. At CyberSecOp, we believe that cybersecurity and compliance initiatives must originate from the executive suite and permeate throughout the organization to ensure the adoption and resiliency of the systems in place.
Why Cybersecurity and Compliance Must Start from the Top
Setting the Tone: Leadership sets the tone for organizational culture, including attitudes toward cybersecurity and compliance. When executives prioritize security and compliance, it sends a clear message that these are non-negotiable aspects of the business; the entire organization must be thoughtful and engaged
Resource Allocation: Adequate resources, including budget and personnel, are essential for implementing robust cybersecurity measures and maintaining compliance. Leadership’s commitment ensures resources are appropriately allocated and aligned to the organization’s strategic objectives.
Risk Management: Understanding the potential impact of cyber threats on financial, business operations and reputational levels, leadership can make informed effective decisions to mitigate these risks.
Regulatory Compliance: Many organizations are legally required to comply with industry regulations, governance expectations, and standards. Leadership oversight ensures organizational compliance, avoiding potential legal, financial, and reputational consequences.
Why Happy Employees Ensure a Trusted System
Employee Buy-In: A positive work environment fosters employee buy-in and commitment to cybersecurity best practices. When employees feel valued and supported, they are more likely to adhere to security policies and procedures, reducing the risk of insider threats.
Training and Awareness: Engaged and satisfied employees are receptive to cybersecurity training and awareness initiatives. Regular training sessions empower employees to recognize and respond to security threats, enhancing overall cyber resilience.
Culture of Accountability: A culture of happiness and satisfaction promotes accountability and responsibility at all levels of the organization. Employees' ownership of the organization’s overall cyber health and wellness drives acceptance and acknowledgment of the need to be risk-aware.
Reduced Turnover: It has been proven that a low turnover rate minimizes the risk of insider threats associated with disgruntled or departing employees. A stable workforce contributes to the continuity and consistency of security measures.
Conclusion: Building a Culture of Security and Trust
Cybersecurity and compliance must be ingrained in an organization’s culture from the top down. Leadership’s commitment to resource allocation and risk management are essential to a comprehensive security strategy. Fostering employee happiness and satisfaction are important additives to a culture focused on security, promoting adherence to policies and procedures, and ensuring a trusted system.
At CyberSecOp, we understand the importance of a holistic approach to cybersecurity and compliance. Organizations can develop tailored security solutions and cultivate a culture of security excellence by partnering with us.
Thank you for prioritizing cybersecurity and compliance in your organization. Together, we can build a safer and more resilient digital future.
Understanding the UnitedHealth Data Breach: Lessons Learned and Cybersecurity Imperatives
In recent months, the healthcare industry has been rocked by a significant number of cybersecurity breaches, the most prolific of which was at UnitedHealth Group. This breach sheds light on the critical importance of robust cybersecurity measures in safeguarding sensitive patient data and ensuring the continuity of essential services.
Below we delve into the details of this breach and explore its broader implications for cybersecurity in the healthcare industry as a whole.
The breach at UnitedHealth's tech unit on February 12th was orchestrated by hackers who gained remote access to the network using stolen login credentials. This breach, attributed to the cybercriminal gang AlphV, aka BlackCat, underscored the vulnerabilities inherent in relying solely on passwords for authentication, particularly the absence of multi-factor authentication (MFA). The compromised Change Healthcare Citrix portal, lacking MFA, provided an open gateway for cybercriminals to infiltrate and encrypt the systems, leading to a ransom demand to restore access.
The aftermath of the breach highlighted the significant disruption to American healthcare. Change Healthcare was locked out of the essential systems impacting medical claims processing across the country. UnitedHealth Group has been diligently working with law enforcement agencies and cybersecurity firms, including Google, Microsoft, Cisco, and Amazon, to investigate the breach and secure affected systems.
However, the ransom payment made by UnitedHealth Group underscores the complex ethical and practical considerations surrounding ransomware attacks. While paying the ransom may, or may not truly ensure the decryption of systems and the restoration of services, it also incentivizes cybercriminals to continue their nefarious activities.
In response to the breach, UnitedHealth Group has taken proactive measures to support affected healthcare providers, providing over $6.5 billion in accelerated payments and no-interest, no-fee loans to mitigate the financial impact.
This breach serves as a stark reminder of the urgent need for healthcare organizations to prioritize cybersecurity and implement robust defenses against evolving cyber threats. CyberSecOp continues to provide award winning services, standing ready to assist organizations in mitigating risks, conducting comprehensive risk assessments, and implementing tailored cybersecurity strategies to safeguard sensitive data and ensure the integrity of critical systems.
As the healthcare industry grapples with the fallout of this breach, it is imperative for organizations to learn from these events and strengthen their cybersecurity posture to protect patient privacy and maintain the trust of stakeholders.
Together, we can work towards building a more resilient and secure healthcare ecosystem where patient data remains protected and essential services remain uninterrupted.
Fort Knox Your Data: Why Partner with a Combined MSSP & GRC Powerhouse Like CyberSecOp?
The digital landscape is a battlefield, and your data is the treasure. Cyber threats lurk around every corner, and complex regulations add another layer of complexity but fear not! Partnering with a Managed Security Service Provider (MSSP) and Governance, Risk, and Compliance (GRC) consulting firm like CyberSecOp gives you a one-stop shop for an impenetrable defense system.
Here's why CyberSecOp is your ultimate security and compliance guardian:
Fortress-Level Security: We provide 24/7 threat detection, rapid response, and advanced security solutions to keep your data safe from cyberattacks.
GRC Compliance Navigation: We will guide you through the labyrinth of regulations, ensuring compliance with industry standards and mitigating legal risks at the same time.
Cost-Effective Defense: CyberSecOp offers a combined solution that saves you time, money, and resources eliminating the need for separate security and compliance teams.
Dream Team Expertise: Gain access to a powerful team of cybersecurity veterans and GRC specialists, all working seamlessly to safeguard your organization.
Streamlined Operations: Our integrated approach eliminates silos and ensures all your security and compliance efforts are perfectly coordinated.
Actionable Insights: We go beyond reports by providing actionable insights and recommendations tailored to your specific needs and budget.
Why Choose CyberSecOp?
Comprehensive Security & Compliance Solutions: From managed detection and response to risk assessments and compliance audits and Incident Response Services if needed, we offer a full spectrum of services.
Custom-Fit Approach: We tailor our solutions to your unique industry, size, and regulatory landscape, ensuring a perfect fit.
Proven Track Record of Success: We've helped countless organizations achieve a state of digital resilience and recovery, giving them peace of mind and a competitive edge.
Focus on Measurable Results: We prioritize outcomes that align with your business goals, demonstrating the real value of our partnership.
We utilize one of the most comprehensive GRC software platforms; this ERM is a completed game changer
Don't settle for fragmented solutions.
Partner with CyberSecOp and unlock the power of a unified security and compliance powerhouse. Contact us today for a free consultation and see how we can help you Fort Knox your data!
Thriving in the Digital Age: Mastering Digital Continuity and Cyber Risk Management
In today's dynamic digital landscape, businesses face a constant barrage of challenges. Evolving customer expectations, ever-present cybersecurity threats, and a growing emphasis on sustainability demand a strategic approach and execution. Here's where the concepts of digital continuity and cyber risk management come into play, acting as cornerstones for organizational resilience and success.
This blog post explores why these concepts matter and how businesses can leverage them to navigate the ever-changing digital world.
The Power of Digital Continuity
Digital continuity ensures a seamless flow of digital information, guaranteeing operational efficiency and fostering seamless collaboration. It allows businesses to adapt to technological advancements without disruption, ensuring the consistency, accessibility, and reliability of their digital assets.
Here's how CyberSecOp can help you establish a robust digital continuity plan:
Digital Transformation Assessments: We conduct a thorough evaluation of your existing architecture, systems, processes, and data flows, identifying areas for improvement and pinpointing vulnerabilities.
Business Continuity Planning: Our experts collaborate with you to develop a comprehensive business continuity plan, ensuring minimal disruption in the face of unforeseen events.
Data Management Solutions: We implement robust data management practices to safeguard your critical information and streamline access for authorized users.
Building a Culture of Cyber Resilience
Strengthening cybersecurity measures is crucial for protecting sensitive data and critical infrastructure from cyber threats. Conducting regular risk assessments and fostering a culture of cybersecurity awareness among employees are essential steps.
CyberSecOp offers a suite of services to bolster your organization's cyber defenses:
Managed Security Services: We provide proactive threat detection, rapid incident response, and 24/7 security monitoring to safeguard your systems from cyberattacks.
Penetration Testing: We simulate cyberattacks to identify vulnerabilities in your systems and applications, allowing you to address them before malicious actors exploit them.
Security Awareness Training: Our engaging training programs equip your employees with the knowledge and skills to identify and mitigate cyber threats.
Digital Continuity: A Pillar of Sustainability
Digital continuity aligns with sustainability initiatives by optimizing resource utilization and minimizing waste. By digitizing operations, businesses can reduce their carbon footprint and enhance energy efficiency, contributing to a more sustainable future.
Conclusion
By embracing digital continuity, strengthening cybersecurity practices, and prioritizing sustainability, businesses can navigate the digital landscape with confidence, agility, and a commitment to the environment. Partnering with CyberSecOp empowers you to unlock the full potential of digital technologies while mitigating cyber risks and driving growth alongside a sustainable future.
Ready to thrive in the digital age?
Contact CyberSecOp today to discuss your unique needs and discover how we can help you build a resilient and sustainable future!
Empowering Healthcare E-Commerce: Navigating Cybersecurity Challenges
Empowering Healthcare E-Commerce: Navigating Cybersecurity Challenges with CyberSecOp
Consumer expectations in healthcare are evolving, paving the way for exciting opportunities for healthcare organizations in e-commerce, remote care, and technology based advancements in care. However, with the rise in cyberattacks, it's crucial for regulated health companies venturing into any of these areas to prioritize and harden their cybersecurity measures. Analysts project significant growth in the global healthcare cybersecurity market, estimated to reach around US$58.4 billion by 2030.
To navigate this evolving landscape successfully, healthcare companies must adopt scalable and adaptable e-commerce solutions that prioritize the protection of Protected Health Information (PHI), while also remaining compliant. Choosing the right platforms grounded in security-by-design principles is vital. Integration of cybersecurity measures and auditable compliance across organizational processes is essential, ensuring industrialized security, availability, and global reach.
CyberSecOp offers assistance through cybersecurity solutions focused on Direct to Consumer for Consumer Product security solutions, addressing the evolving consumer needs in healthcare. Trust is paramount, particularly in the healthcare sector, as the industry embraces digital direct-to-consumer (DTC) models. Building trust is essential for long-term success.
Open communication about PHI safeguarding measures builds consumer trust in healthcare ecosystems, fostering engagement and sustainable growth. Establishing long-lasting consumer relationships based on trust is paramount, influencing consumer decisions and promoting brand loyalty.
Modernizing and hardening direct-to-consumer channels in regulated healthcare markets presents significant opportunities, contingent upon effective risk management and trust-building efforts with support from CyberSecOp will build that trust.
As a security consultancy, CyberSecOp provides award winning, industry recognized, expert guidance on cybersecurity strategies tailored specifically for the healthcare industry, ensuring comprehensive protection of PHI and compliance with regulatory requirements.
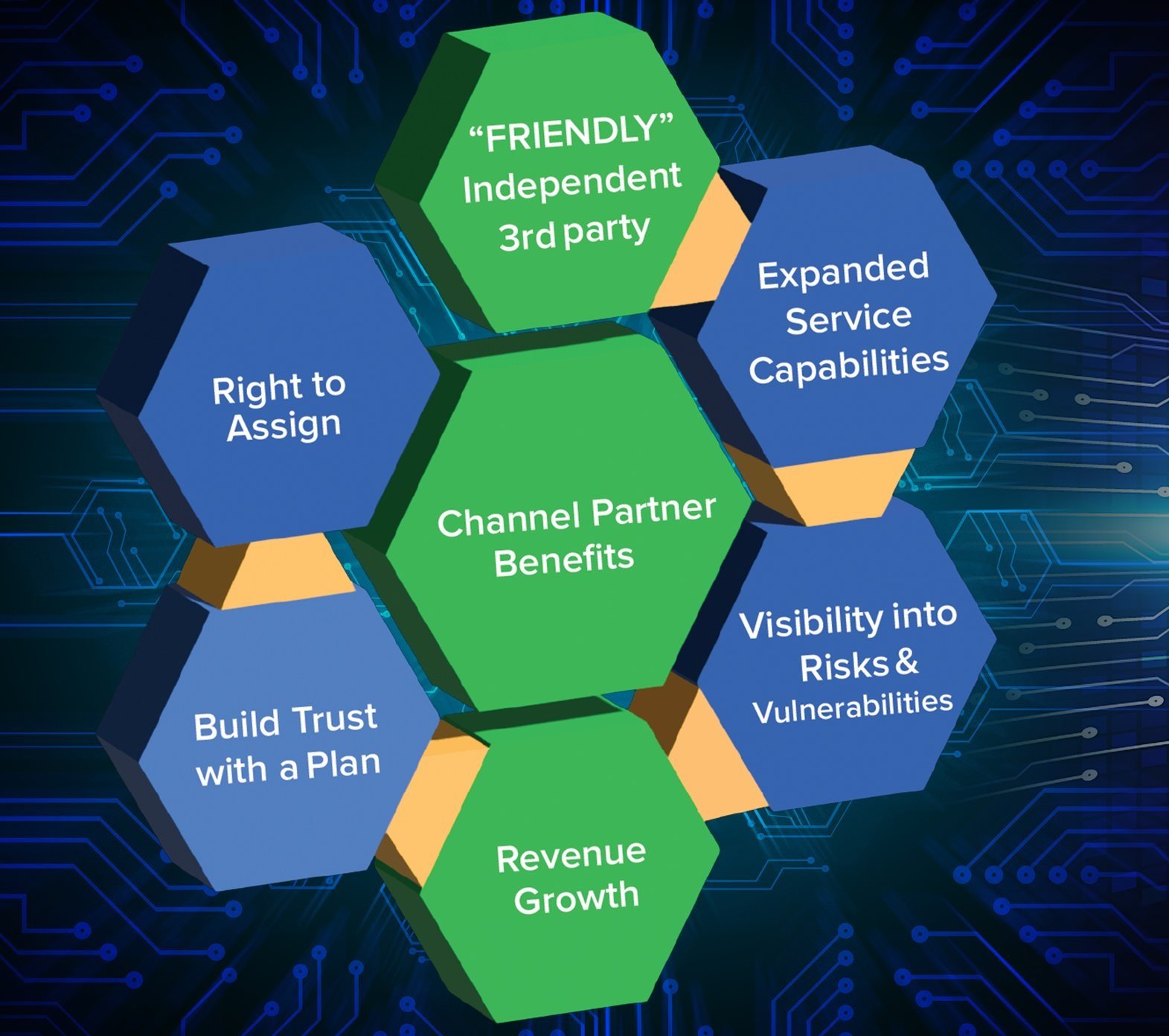
Enhancing Cybersecurity Partnerships: Why MSPs, VARs, and Advisory Firms Should Collaborate with CyberSecOp
As threats continue to evolve and become more sophisticated, it is imperative organizations stay ahead of the curve by implementing and more importantly maintaining a robust cybersecurity posture. This is where strategic partnerships with cybersecurity experts like CyberSecOp can make all the difference.
CyberSecOp is a cybersecurity consultancy offering a range of services aimed at bolstering cybersecurity posture and compliance management. These include services focused on Risk Management, Vendor Management, Governance, Risk, and Compliance (GRC) Platform, Security Operations Center (SOC) as a Service, Security Testing as a Service, and Virtual Chief Information Security Officer (vCISO) services.
Now more than ever; Managed Service Providers (MSPs), Value-Added Resellers (VARs), and service providers need to align themselves with a third-party cybersecurity firm to help their clients make better, more informed decisions. CyberSecOp has spent years advising teams from IT, Finance, Legal, Board Advisors, and the C-suite of their organization's financial exposures, threat landscape(s), and risk avoidance planning. By partnering with CyberSecOp, these entities can ensure that their organizations their end-users, partners, and vendors are effectively safe from risk with a comprehensive approach designed to mitigate cyber risk falling out of regulatory compliance.
Why partnering with CyberSecOp is beneficial for MSPs, VARs, and external advisory firms such as Legal or Accounting firms?
Peace of Mind: By partnering with CyberSecOp, MSPs, VARs, and advisory firms can offer their clients peace of mind knowing that their cybersecurity needs are in capable hands. This not only strengthens client relationships but also enhances the reputation and credibility of our partners with their clients.
Trusted Independence: As a partner of CyberSecOp, our team has two areas of focus. First As an independent third party, we bring our deep expertise and experience to the table, providing insights and solutions that the majority of MSP’s, VAR’s and Advisory firms are unable to. Second, Independence affords CyberSecop freedom from internal biases or agendas. Our unbiased analysis and recommendation strengthen our partner’s positioning with the end client.
Cybersecurity is a collaborative effort that requires the collective expertise and resources of various stakeholders. MSPs, VARs, and advisory firms have a crucial role to play in helping their clients navigate the complex cybersecurity landscape. By partnering with CyberSecOp, these entities can ensure that their clients, users, partners, and vendors have access to cutting-edge technology solutions and expert guidance to mitigate the cybersecurity risk landscape effectively. Together, we can build a more secure and resilient digital ecosystem for all.
Cybercrime: A Booming Industry Threatening Your Business
If Cybersecurity is not part of your ongoing business planning and forethought, your business will likely become an afterthought.
By incorporating strong, enforceable cybersecurity policies, your organization becomes a defensible harder target. Per a recent MSN article, if cybercrime were a standalone economy, it would be third in line behind the U.S. and China. Cybercrime is on pace to pass $17.5 trillion by 2025.
How is your organization planning for and addressing your Cybersecurity and Governance, Risk & Compliance requirements?
43% of all data breaches involve small and medium-sized businesses.
68% of all cyber-attacks focused on business disruption first and data acquisition second.
72% of cybercrime victims are large businesses (affecting not only their employees and customers but also their partners and suppliers).
Over 75% of targeted cyberattacks start with an email (RoundRobin)
Approximately 84% of all events are caused by humans
Nearly 90% of ransomware attacks are preventable
In 2021 there was an estimated 2.7billion hours of lost production globally due to cybercrime (Norton)
Beyond the Headlines: The True Cost of Cybercrime
The adoption of artificial intelligence (AI) technologies has hyper-accelerated the amount of data being generated. This growth will continue exponentially as newer platforms and tools are developed. As businesses turn to novel insurance models, which by definition are new and do not resemble what we have known or used previously to evaluate the risks related to retaining sensitive data in the current cybersecurity climate. Organizations need to understand their risk profile and the financial reality of the loss of access to their data.
it’s more important than ever to truly understand and plan for the threat landscape and the potential financial implications associated with cyber incidents, data exfiltration, and work stoppages.
The importance of data and an organization's capacity to appropriately protect it will be essential factors in assessing overall risk, influencing investors, insurability, and overall profitability.
What is Regulations Compliance and Cybersecurity Compliance?
Being compliant refers to adhering to specific laws, regulations, standards, or guidelines relevant to a particular industry or field. Compliance ensures that organizations operate within legal boundaries, meet industry standards, and uphold ethical practices. In the context of cybersecurity, compliance involves implementing measures to protect sensitive data, prevent unauthorized access, and mitigate security risks.
In today's digital landscape, cybersecurity compliance is paramount for businesses to safeguard their assets and maintain trust with customers. Failure to comply with cybersecurity regulations can result in severe consequences, including legal penalties, financial losses, and reputational damage.
Cybersecurity services play a crucial role in helping organizations achieve and maintain compliance. These services encompass a range of offerings, including cybersecurity consulting, IT security services, and cybersecurity consulting services. Cybersecurity consultants assist organizations in identifying compliance requirements, assessing their current security posture, and implementing measures to meet regulatory standards.
Cybersecurity companies like CyberSecOp offer comprehensive solutions to assist organizations in navigating the complexities of cybersecurity compliance. Here's how CyberSecOp can help:
Regulatory Expertise: CyberSecOp consultants possess in-depth knowledge of cybersecurity regulations and standards relevant to various industries. They can help organizations interpret complex compliance requirements and develop tailored strategies to address specific regulatory mandates.
Risk Assessments: CyberSecOp conducts thorough risk assessments to identify potential security vulnerabilities and compliance gaps within an organization's infrastructure. By assessing risks proactively, organizations can prioritize remediation efforts and minimize the likelihood of compliance violations.
Policy Development: CyberSecOp assists organizations in developing and implementing robust cybersecurity policies and procedures aligned with regulatory requirements. These policies cover areas such as data protection, access control, incident response, and employee training, ensuring comprehensive compliance coverage.
Technical Solutions: CyberSecOp offers a range of technical solutions to enhance cybersecurity and facilitate compliance. This includes implementing encryption technologies, access controls, intrusion detection systems, and security monitoring tools to protect sensitive data and prevent unauthorized access.
Training and Awareness: CyberSecOp provides cybersecurity training and awareness programs to educate employees about compliance requirements, security best practices, and the importance of maintaining a secure digital environment. By fostering a culture of cybersecurity awareness, organizations can empower employees to contribute to compliance efforts effectively.
Continuous Monitoring and Compliance Audits: CyberSecOp conducts regular security assessments and compliance audits to ensure ongoing adherence to regulatory standards. By monitoring systems and processes continuously, organizations can identify and address compliance issues promptly, reducing the risk of regulatory penalties and data breaches.
In summary, CyberSecOp plays a vital role in helping organizations navigate the complexities of cybersecurity compliance. By offering regulatory expertise, conducting risk assessments, developing policies and procedures, implementing technical solutions, providing training and awareness, and conducting continuous monitoring and audits, CyberSecOp assists organizations in achieving and maintaining compliance with confidence. With CyberSecOp's support, organizations can enhance their security posture, mitigate risks, and demonstrate a commitment to protecting sensitive data and maintaining compliance with applicable regulations.
Safeguarding Business Operations: The Importance of Privileged Access Management Risk Assessment
In today's digital age, businesses heavily depend on digital systems, applications, and online platforms for their day-to-day operations. However, alongside this reliance on technology comes the ever-growing risk of unauthorized access to sensitive accounts and data. Particularly vulnerable are companies with privileged access to critical systems and applications, making them prime targets for cyber threats aimed at exploiting human vulnerabilities within organizations.
Recent headlines have shed light on the alarming sophistication of cybercriminals, with reports of ransom scams employing AI-generated deepfakes to manipulate individuals into surrendering substantial sums of money. Such incidents underscore the evolving tactics of cyber attackers and their readiness to exploit technological advancements for financial gain.
The impact of cybercrime on businesses cannot be overstated. According to recent statistics, in 2022 alone, the FBI received over 900,000 cybercrime complaints, resulting in staggering losses amounting to $5.3 billion. From phishing scams to ransomware attacks, cybercriminals employ a diverse array of tactics, leveraging AI-powered technologies to breach security measures and wreak havoc on organizations' digital infrastructure.
In light of these escalating threats, it is imperative for businesses to remain vigilant and proactively safeguard their digital assets. One crucial step towards bolstering cybersecurity defenses is the implementation of Privileged Access Management (PAM) risk assessments.
By conducting thorough PAM risk assessments, organizations can identify potential security gaps and vulnerabilities associated with privileged access to critical systems and applications. This process involves several key steps:
Step 1: Identify privileged users and assets
Begin by identifying all individuals, including employees, contractors, and third-party vendors, who possess privileged access to critical systems and applications. Simultaneously, pinpoint the assets these users can access, such as servers, databases, and essential applications.
Step 2: Determine the level of access
Next, ascertain the extent of access granted to each privileged user. This entails delineating the specific privileges conferred upon them, such as administrative or superuser access. Moreover, evaluate existing policies and procedures governing access to critical assets.
Step 3: Assess the risks
Conduct a comprehensive assessment of the risks associated with privileged access. Identify potential threats and vulnerabilities, including unauthorized access attempts, data breaches, and insider threats. Assess the potential impact of these risks on the organization's operations, reputation, and financial standing.
Step 4: Implement controls
Implement robust controls to mitigate identified risks effectively. This may involve deploying role-based access controls, enforcing the principle of least privilege, and establishing robust monitoring and auditing mechanisms to detect and prevent unauthorized access.
Step 5: Review and update regularly
Regularly review and update the PAM risk assessment to ensure its continued effectiveness. Adapt the assessment to reflect changes in the organization's PAM policies, procedures, and the evolving threat landscape.
By adhering to these steps, businesses can fortify their cybersecurity posture and mitigate the risks associated with privileged access. Ultimately, prioritizing cybersecurity and staying abreast of emerging threats is paramount in safeguarding sensitive accounts and ensuring uninterrupted business operations amidst the ever-present specter of cyber threats.
Defense Department Releases Companion CMMC Public Comment
Defense Department Releases Companion Video for CMMC Public Comment Period
Feb. 15, 2024 | By C. Todd Lopez, DOD News
In a bid to demystify the intricacies and significance of the recently published proposed rule for its Cybersecurity Maturity Model Certification (CMMC) program, the Defense Department has unveiled an informative video resource.
Tailored to enlighten members of the defense industrial base and other stakeholders, the video elucidates the nuances of the proposed rule for the CMMC program. Its primary objective is to assist stakeholders in comprehending the intricacies of the program and to facilitate their preparation of comments and feedback for the upcoming review process, shaping the finalization of the CMMC program proposed rule.
A 60-day public comment period on the proposed rule commenced on Dec. 26, 2023, and will conclude on Feb. 26 at 11:59 p.m. The feedback received during this period will be meticulously reviewed and will play a pivotal role in informing the final rule.
At its core, the Cybersecurity Maturity Model Certification program serves as a mechanism for the Defense Department to ascertain the preparedness of defense contractors, regardless of size, in managing controlled unclassified information and federal contract information in compliance with federal regulations.
Central to the program's execution are the authorized CMMC "third-party assessment organizations" (C3PAOs), tasked with conducting CMMC Level 2 certification assessments for interested companies. The Department will oversee CMMC Level 3 assessments.
Although the Department does not remunerate C3PAOs, it does establish the requirements governing their operations. Gurpreet Bhatia, the DOD Chief Information Officer's principal director for cybersecurity, underscores the program's significance in safeguarding crucial DOD information from adversarial incursions.
Bhatia emphasizes that the CMMC program is pivotal in bolstering defense contractors' compliance with cybersecurity regulations while enabling the DOD to monitor compliance status effectively.
He underscores the Department's unwavering commitment to implementing the CMMC Program, underscoring its pivotal role in fortifying the protection of DOD's sensitive information. Bhatia urges stakeholders to seize the opportunity to provide feedback on the proposed CMMC rule, underscoring the importance of collaborative efforts in enhancing cybersecurity and safeguarding DOD information assets.
Understanding the Global Ransomware Landscape: A Closer Look at Recent Incidents and Cybersecurity Initiatives
In recent years, state institutions worldwide have increasingly fallen victim to ransomware attacks orchestrated by sophisticated cybercriminal gangs. These nefarious actors employ various tactics, such as encrypting or stealing sensitive data, to extort hefty ransoms from their targets. The primary victims include councils, hospitals, schools, and universities, entities often known for their inadequate cybersecurity measures and urgent operational needs.
The British Library Incident: A Wake-Up Call
One significant incident that highlights the severity of the ransomware threat is the attack on the British Library. Despite the UK government's longstanding policy against paying ransoms, the library became a target, resulting in significant disruptions to its operations. The attackers, after stealing 600GB of data, resorted to dumping it on the dark web when their ransom demands were not met. Moreover, they inflicted irreversible damage by destroying critical infrastructure, making recovery efforts challenging for the institution.
Global Response to Ransomware: Challenges and Innovations
While efforts to combat ransomware globally have intensified, challenges persist, particularly in light of geopolitical developments. The full-scale invasion of Ukraine by Russia disrupted international cooperation on cybersecurity, as Russia withdrew from collaborative efforts. This setback forced law enforcement agencies to explore alternative strategies, including "hack back" operations, to combat ransomware gangs.
US Government's Cybersecurity Funding Boost
In the United States, President Joe Biden has proposed a significant increase in cybersecurity funding as part of his fiscal year 2025 spending plan. This proposal includes additional funding for the Cybersecurity and Infrastructure Security Agency (CISA) and allocations to enhance cybersecurity across various government departments. While the proposal faces political hurdles, it underscores the administration's commitment to bolstering national cybersecurity measures.
Microsoft's Patch Rollout: Addressing Critical Vulnerabilities
Amid the escalating ransomware threat, technology companies like Microsoft play a crucial role in mitigating risks. Recently, Microsoft issued patches for numerous security vulnerabilities affecting its Windows ecosystem, including critical flaws in HyperV and Open Management Infrastructure (OMI). Urging users to prioritize these fixes, Microsoft remains vigilant in addressing potential avenues for remote code execution and denial-of-service attacks.
Conclusion
As ransomware attacks continue to pose significant threats to state institutions and businesses worldwide, collaboration among governments, law enforcement agencies, and technology companies remains imperative. Heightened cybersecurity measures, coupled with proactive initiatives to deter ransomware attacks, are essential in safeguarding critical infrastructure and protecting sensitive data from malicious actors.
Deep Dive: Unconventional Strategies for Fortressing Your Security Posture
In today's ever-escalating cyberwarfare, building an impenetrable security fortress requires venturing beyond the standard firewalls and antivirus shields. Let's delve into unconventional strategies that can bolster your defenses and surprise even the most cunning attackers.
Think Unthinkable, Act Unpredictable:
Embrace the Underdogs: While familiar names dominate the software landscape, consider migrating sensitive operations to lesser-known applications. Their smaller attack surfaces make them less predictable targets, potentially throwing attackers off guard. But beware, thorough vetting and security assessments are crucial before diving in.
Friend or Foe? The Internal Keylogger Conundrum: This ethically sensitive but potentially powerful tool can monitor employee activity but with great caution. Ensure strict regulations and employee privacy are upheld. Remember, prioritize prevention through comprehensive training and access control before resorting to monitoring.
Zero Trust: Your Network, Your Rules: Ditch the outdated "trust but verify" approach and embrace "never trust, always verify" with Zero Trust methodology. Segment your network, enforce multi-factor authentication for every access attempt, and implement least-privilege access, granting escalation only when absolutely necessary. Remember, trust is earned, not assumed.
Beyond Your Walls: Securing the Extended Ecosystem:
Vendor Risk Management: Don't Let the Backdoor Swing Open: Third-party vendors are often the weakest link in the security chain. Conduct thorough attack surface assessments and due diligence checks on every vendor. Prioritize those with demonstrably robust security postures and minimal dark web exposure. Remember, your security is only as strong as your weakest link.
Move Security Beyond Marketing Hype: Don't fall victim to "security theater," where vendors showcase impressive-sounding features without the substance. Demand transparency and evidence of effectiveness. Request detailed security audits and penetration testing reports to see their defenses in action. Remember, security is not a show, it's a shield.
Remember:
There's No Silver Bullet: These strategies are complementary tools, not magic solutions. Integrate them with traditional security practices and a risk-based approach for maximum impact.
Context is King: What works for one organization might not be suitable for another. Tailor your approach based on your specific industry, risk profile, and resources.
Eternal Vigilance is the Price of Liberty: The threat landscape is a living, evolving beast. Stay updated on new vulnerabilities, adapt your strategies accordingly, and conduct regular security assessments to identify and address emerging threats. Remember, security is a continuous journey, not a one-time destination.
By embracing these unconventional ideas, adapting them to your unique context, and maintaining a proactive approach, you can build a security posture that not only deters attackers but leaves them bewildered and frustrated. Remember, the best defense is an unexpected one. Let's start thinking outside the box and outsmart the adversaries before they even have a chance.
Navigating the Sea of Data Privacy Laws and Cyber Regulations in 2024
Introduction
Fasten your digital seatbelts, because 2024 is shaping up to be a global whirlwind of data privacy and cybersecurity regulations. From five new comprehensive state data privacy laws in the US, including the Utah Consumer Privacy Act (UCPA) taking effect at the end of 2023, to radical new consumer health data privacy laws, businesses worldwide face unprecedented compliance challenges. But fear not, intrepid captains of your digital vessels! A robust security and privacy program can be your life raft in this regulatory storm, no matter where you navigate the digital seas.
The Perfect Storm: New Privacy, Breach Notification, and Cybersecurity Laws (Worldwide)
This year, businesses are facing a global regulatory tsunami:
1. New Privacy Laws: The US isn't alone. Comprehensive data privacy laws are popping up worldwide, with jurisdictions like Brazil, China, California, Australia, and now Utah, Texas, Oregon, Florida, and Montana leading the charge. Each law brings its own unique requirements, making compliance a complex international puzzle.
2. Breach Notification Blitz: Data breaches are a global concern, and governments are responding with stricter notification laws. From the EU's GDPR to India's Personal Data Protection Bill, expect to see tighter deadlines, broader notification requirements, and potential penalties for failing to report breaches promptly.
3. Cybersecurity Mandates on the March: Governments are raising the bar on cybersecurity, imposing new mandates and standards on businesses across industries. From zero trust requirements to software assurance guidelines, staying compliant will require proactive investment in your security posture.
Key US Data Privacy Laws and Health Data Privacy Regulations to Be Aware of in 2024:
Data Privacy Laws:
Utah Consumer Privacy Act (UCPA) - Effective December 31, 2023: Applies to businesses exceeding $25 million in revenue and processing data of 100,000 or more Utah residents. Grants Utah residents rights to access, delete, and opt-out of the sale of their personal data.
Texas Data Privacy and Security Act (TDPSA) - Effective July 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of Texas residents. Grants similar rights to UCPA, with additional restrictions on data deletion and requiring data security measures.
Oregon Consumer Privacy Act (OCPA) - Effective July 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of 100,000 or more Oregon residents. Grants similar rights to UCPA, with emphasis on data minimization and specific requirements for obtaining consumers' consent.
Florida Digital Bill of Rights - Effective July 1, 2024: Establishes principles for data privacy but does not create individual rights or enforcement mechanisms. Requires businesses to disclose data collection practices and implement data security measures.
Montana Consumer Data Privacy Act (MCDPA) - Effective October 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of 25,000 or more Montana residents. Grants rights to access, correct, and delete personal data, with exemptions for specific sectors.
Health Data Privacy Regulations:
Washington My Health My Data Act: Enacted in May 2023, prohibits the selling of Washingtonians' health data and restricts collection and sharing without consent. Imposes geofencing limitations around sensitive healthcare facilities.
Nevada Consumer Health Privacy Law (SB 370): Effective March 31, 2024, prohibits selling consumer health data without written consent and restricts collection and sharing. Similar geofencing limitations as Washington.
Amended California Consumer Privacy Act (CCPA) Regulations: Taking effect July 1, 2023, expand CCPA's scope to include specific consumer rights regarding their health data.
Colorado Universal Opt-Out Mechanisms: Effective July 1, 2023, requires businesses exceeding $100 million in gross revenue to offer a universal opt-out mechanism for the sale of personal data, including health data.
Connecticut Senate Bill 3: Took effect July 1, 2023, adds "consumer health data" to its data privacy act, requiring opt-in consent for selling and imposing geofencing restrictions around sensitive healthcare facilities.
Navigating the Calm After the Storm with CyberSecOp
2024 has indeed become a tsunami of data privacy and cybersecurity regulations, leaving businesses feeling like they're caught in a riptide. But fear not, weary sailors! Just as a lighthouse guides ships through treacherous waters, a robust security and privacy program can be your beacon of stability in this ever-changing regulatory landscape.
Implementing a comprehensive program isn't just about weathering the storm – it's about thriving in the calmer seas ahead. By prioritizing compliance, you can:
Avoid costly fines and legal action: Proactive measures significantly reduce the risk of non-compliance penalties.
Build trust and loyalty with customers: Demonstrating your commitment to data privacy fosters trust and encourages customer loyalty.
Reduce the likelihood and impact of data breaches: Robust security measures minimize the risk of breaches and mitigate their potential damage.
Gain a competitive edge: Being ahead of the curve on privacy regulations can attract privacy-conscious consumers and partners.
This is where organizations like CyberSecOp come in. We're not just your life raft in the storm – we're your skilled navigators, equipped with the expertise and resources to chart a course towards secure and compliant waters. Here's how we can help:
Conduct thorough security and privacy assessments: Identify vulnerabilities and gaps in your current posture, providing a clear roadmap for improvement.
Develop and implement tailored security and privacy programs: Create solutions that meet your specific needs, industry regulations, and global reach.
Stay ahead of the curve with ongoing monitoring and updates: Our team keeps you informed of evolving regulations and industry best practices.
Respond effectively to data breaches: Minimize the impact of breaches and ensure compliance with reporting requirements.
Offer expert guidance and support throughout your journey: Our team of experienced professionals is here to answer your questions and address your concerns.
Don't wait for the next regulatory wave to hit. Contact CyberSecOp today and let us help you navigate the ever-changing seas of data privacy and cybersecurity with confidence. Together, we can ensure your business sails smoothly towards a successful and secure future.
What you need to know about IT Company and IT Security Company
CyberSecOp: Your Trusted IT Company and IT Security Company Partner
CyberSecOp is a leading IT security company that provides a comprehensive range of services to help businesses of all sizes protect their data and systems from cyber threats. We offer a wide range of services, including:
Security assessments and penetration testing
Incident response and Remediation
Managed security services
Compliance consulting
Security awareness training
Our expertise:
Our team of experienced security professionals deeply understands the latest cyber threats and how to mitigate them. We are committed to providing our clients with the highest level of security services, and we are always up-to-date on the latest security trends.
Our clients:
We work with a wide range of clients, from small businesses to large enterprises. We understand that each client has different security needs, and we tailor our services accordingly.
Contact us:
To learn more about our services, please contact us today. We would be happy to answer any questions you have and help you protect your organization from cyber threats.
Additional details:
Founded in 2010, CyberSecOp has quickly become a leading IT security company.
The company has been recognized by Gartner as a "Cool Vendor" in the security industry.
CyberSecOp's IT consultants typically have a salary range of $100,000 to $150,000 per year.
The company is ranked number 2 on Gartner's list of top IT security companies.
Here are some of the benefits of working with CyberSecOp:
You will work with a team of experienced and knowledgeable security professionals.
You will have access to the latest security technologies and solutions.
You will be able to tailor your security services to your specific needs.
You will be confident that your data and systems are protected from cyber threats.