CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Don't Get Hacked Twice: How Cyber Insurance Might Be Leaving You Exposed
Cybersecurity is a top concern for businesses of all sizes. Data breaches are costly and damaging, and cyber insurance has emerged as a critical tool for mitigating risk. But what if your cyber insurance policy isn't all it's cracked up to be?
While cyber insurance offers valuable protection, hidden clauses and limitations could leave your organization vulnerable in the wake of an attack. Here's why you should be skeptical and take a proactive approach to cyber defense:
Hidden Coverage Gaps:
Not All Breaches Are Created Equal: Many policies exclude specific breach types, such as social engineering attacks or ransomware incidents involving specific extortion tactics. Be sure you understand these exclusions to avoid a nasty surprise after a claim.
Sub-Limits and Coverage Caps: Policies often have sub-limits for specific categories of expenses, like data recovery or notification costs. These sub-limits might not be enough to cover the total cost of a significant breach. Additionally, there might be an overall cap on coverage, leaving you on the hook for substantial financial losses.
Prescriptive Response Requirements:
Slowing Down Your Defense: Some policies mandate specific response protocols following a breach. While intended to minimize damage, these protocols might hinder your ability to take the most effective course of action. Delays in securing your network or notifying affected parties could worsen the situation.
Limited Vendor Choice:
Dictating Your Defense Strategy: Certain policies restrict the vendors you can use for incident response or forensic investigation. This could limit your ability to choose the most qualified or experienced team for your situation.
The Power of Proactive Defense
Don't rely solely on cyber insurance as a safety net. Here's how to take charge of your cybersecurity:
Conduct Regular Risk Assessments: Identify your vulnerabilities and prioritize mitigation efforts.
Invest in Employee Training: Empower your employees to recognize and avoid cyber threats.
Implement Strong Security Measures: Utilize firewalls, data encryption, and multi-factor authentication.
Have a Clear Incident Response Plan: Outline a fast, effective response strategy for cyber incidents.
The Importance of a Trusted Partner
In addition to the proactive measures above, having a trusted partner like CyberSecOp in your corner can make all the difference. CyberSecOp is a comprehensive cybersecurity solution offering:
Digital Forensics and Incident Response: Our team of experts can quickly identify the source of a breach, contain the damage, and begin the recovery process.
Negotiation and Ransomware Payment Team: In the unfortunate event of a ransomware attack, CyberSecOp has a dedicated team to negotiate with attackers and minimize ransom payments. We understand the delicate balance of recovering your data while protecting your organization's reputation.
The Bottom Line
Cyber insurance can be a valuable tool, but it shouldn't be your only line of defense. By understanding your policy's limitations and taking proactive security measures, you can minimize the risk of a cyberattack and ensure a faster, more effective response if one occurs. Remember, an ounce of prevention is worth a pound of cure, especially in the ever-evolving world of cybersecurity.
Partner with CyberSecOp today for a comprehensive cybersecurity strategy that protects your organization before, during, and after an attack.
Risk Mitigate vs. Remediate: Understanding the Key Differences in Risk Management
In risk management, cybersecurity, and compliance, the terms "mitigate" and "remediate" often surface. Though sometimes used interchangeably, they denote distinct approaches to addressing issues. Understanding the differences between mitigation and remediation is crucial for implementing effective strategies. This blog post will clarify these terms and explore their roles in risk management.
What Does It Mean to Mitigate?
Mitigation refers to the actions taken to reduce the severity, seriousness, or harmful effects of a risk or issue. It involves implementing measures to lessen the impact or likelihood of a potential problem. The goal of mitigation is not to eliminate the risk entirely but to make it more manageable and less damaging.
Examples of Mitigation:
Installing Firewalls: In cybersecurity, installing firewalls can mitigate the risk of unauthorized access to a network.
Employee Training: Providing training to employees on best practices for data security can mitigate the risk of data breaches.
Regular Maintenance: Regular maintenance on machinery can mitigate the risk of mechanical failures.
What Does It Mean to Remediate?
Remediation involves the actions taken to correct or fix a problem that has already occurred. It is a reactive approach that focuses on eliminating the issue and restoring the system or environment to its normal state. Remediation aims to resolve the problem at its source and ensure it does not recur.
Examples of Remediation:
Patching Software: After a vulnerability is discovered in software, applying patches to fix the vulnerability is a remediation action.
Data Recovery: Restoring lost data from backups after a data breach or accidental deletion is a form of remediation.
Cleaning Contaminated Sites: In environmental management, cleaning up polluted sites to remove contaminants is remediation.
Key Differences Between Mitigation and Remediation
1. Proactive vs. Reactive:
Mitigation is a proactive approach, aiming to prevent or lessen the impact of potential problems before they occur.
Remediation is a reactive approach, addressing and correcting issues that have already happened.
2. Objective:
Mitigation seeks to reduce risk and make potential issues more manageable.
Remediation seeks to eliminate problems and restore normalcy.
3. Scope:
Mitigation often involves ongoing measures and practices to continuously manage risk.
Remediation involves specific actions taken to resolve a particular issue.
Why Both Are Important
Effective risk management requires both mitigation and remediation strategies. Mitigation helps in minimizing the chances and impact of risks, while remediation ensures that any issues that do arise are swiftly and effectively dealt with. By combining these approaches, organizations can maintain a robust defense against potential threats and ensure rapid recovery from any incidents that occur.
Conclusion
Mitigation and remediation are essential components of risk management, each serving a unique purpose. Mitigation focuses on proactive measures to reduce the likelihood and impact of risks, while remediation addresses issues that have already occurred. By understanding and implementing both strategies, organizations can better protect themselves against threats and ensure a swift recovery when problems arise.
CrowdStrike and Microsoft Outage
On July 19th CrowdStrike deployed a faulty patch/configuration update for its Falcon sensor software. The effected devices were those PC’s and servers running Windows operating systems. The outage, which affected systems worldwide, including Windows virtual machines and the MS Azure platform, began rebooting and/or crashing at approximately 10:48 AM Eastern. (The affected systems also included those running Windows 10 and 11 that were running CrowdStrike Falcon). Machines running macOS and Linux were NOT affected. It was noted in a number of sources that there was a similar issue for devices running Linux in April 2024.
At 9:27 AM Eastern, CrowdStrike deployed updated content. Devices that booted with this later content were not affected.
NATURE OF THE ISSUE:
CrowdStrike’s CEO, George Kurtz, confirmed the issue was due to a faulty kernel configuration level file and NOT the result of a Cyber Attack. Given the AT&T data breach just 10 days ago on July 12th, and the fact that there have been 10 major Cyber Attacks or Data Breaches so far in 2024, it was not surprising for the general public, as well as all of the affected all types and sizes of businesses ranging from airlines to hospitals to federal agencies and retail stores to immediately think that another Cyber Incident was the cause of the ensuing outages caused by the configuration issue. Thankfully this was not a cyber-attack, however, this issue does point out just how vulnerable the organizations we critically reliant on are.
THE FIX:
Should any organizations still be unable to fix their issues, there are a number of organizations, including CyberSecOp, that are able to help you with the relatively direct but painstaking task fix for the ‘outage’.
Affected Machines can be restored by booting into safe-mode or the Windows Recovery Environment and deleting any .sys files beginning with C-00000291- and with timestamp 0409 UTC in the %windir%\System32\drivers\CrowdStrike\ directory.
This process must be done locally on each individual device.
Someone will have to reboot the affected computers individually with manual intervention on each system.
NOTE: Some Azure customers have had success by rebooting the affected virtual machines numerous times (10,12,15 times was not unheard of) while connected to Ethernet.
NOTE: Microsoft has also recommended restoring from back-up from before July 18th.
HOW AND WHY THIS HAPPENED
Though at this time we cannot be 100% certain as to what caused this issue, we can expect that one of the primary culprits was the lack of testing and validation of the configuration update prior to its release. As noted in last week’s posting from CyberSecOp, it is absolutely critical for organizations of all sizes, across all market segments to properly plan and establish policies for their use, deployment and on-going updating of their technology ecosystem. In this case, whether or not CrowdStrike has the proper plans and controls in place to ensure they have screened and tested their upgrades, patches and releases is not in question – what is being questioned, and far more importantly is - have they been followed. Further, are those organizations and their managed services providers; effected by this latest outage properly testing and validating ANY changes to their environments before deploying them in to production environments? Is the CMDB in place?
THE MORAL OF THE STORY …
Organizations must develop, iterate on, and adhere to robust policies and procedures to enhance their change management processes. From a risk management standpoint, organizations should reconsider their operational strategies to ensure that dependency on a single vendor does not impact all of their operations. Diversifying vendors and creating competitive hedges can be crucial in times of disaster. Questions organizations should consider asking their managed services providers include:
Was this a planned update?
What testing was conducted in non-production environments, and what were the results?
What CMDB policies and procedures were overlooked?
Unveiling the Blueprint for Cybersecurity-Infused Transformation Success: Insights for CEOs and Tech Leaders
In the relentless quest for organizational evolution and security resilience, the pursuit of successful transformation stands as a cornerstone. Today, we're thrilled to unveil invaluable insights garnered from a collaborative research endeavor between EY teams and the esteemed University of Oxford’s Saïd Business School. This blog post is meticulously crafted to arm you, esteemed leaders across diverse industries, with actionable strategies to fortify transformational endeavors against cyber threats.
Here's the Essence:
Deconstructing Research Revelations:
Our joint venture uncovered six pivotal levers essential for transformation success. Rooted in human behavior and fortified with cybersecurity principles, these levers possess the transformative potential to amplify success rates by a staggering 2.6 times, culminating in a remarkable 73% success rate (Source EY).Decoding Transformation Levers in the Cyber Era:
Lead: Cultivate collaboration and inclusivity, championing cyber-aware ideas across all organizational tiers.
Inspire: Craft a compelling vision of transformation fortified with cybersecurity principles, igniting innovation and fortifying alignment.
Care: Listen intently and empathetically, prioritizing emotional support and cyber-aware stakeholder engagement.
Empower: Nurture cybersecurity expertise and autonomy within teams, fortifying bottom-up resilience.
Build: Champion human-centric cyber-resilient solutions, aligning tech investments with user-centric needs and security imperatives.
Collaborate: Foster a cyber-resilient culture of open communication and collaboration, fortifying organizational agility and security resilience.
Actionable Cyber Takeaways:
Embrace a cyber-aware mindset to fuel innovation and cybersecurity resilience.
Articulate a compelling cybersecurity-infused transformation narrative to rally collective commitment and fortify cyber defense.
Prioritize active listening and empathetic cyber leadership to foster stakeholder engagement and security buy-in.
Empower teams with cyber expertise and resources to drive cyber-resilient innovation and cyber defense.
Center tech initiatives around user-centric cybersecurity to enhance adoption and fortify organizational security posture.
Foster a cyber-resilient collaborative environment to cultivate agility and fortify organizational security resilience.
Leverage these cyber-infused insights as your compass to navigate the intricate terrain of digital transformation fortified against cyber threats. Together, let's embark on a cyber-resilient transformative journey that propels our organizations to unprecedented heights of cyber-secure success.
For further exploration of these cyber-infused insights and tailored cybersecurity advisory services, we invite you to connect with our expert cyber teams at CyberSecOp.
Why Lesser-Known Software Can Offer Unique Protection Against Hackers
In the realm of cybersecurity, the choice of software can significantly impact an organization's defense against cyber threats. While mainstream software solutions are widely adopted due to their robust features and extensive support, lesser-known software can sometimes provide unique advantages in protecting against hackers. This blog delves into why using lesser-known software can enhance your cybersecurity posture and the potential benefits it offers.
Understanding the Cybersecurity Landscape
The cybersecurity landscape is constantly evolving, with hackers continuously developing new methods to exploit vulnerabilities. Most cyber attacks target widely-used software, as it offers a higher probability of success due to its large user base. As a result, organizations using mainstream software are often more vulnerable to attacks, simply because they are more frequent targets.
Advantages of Lesser-Known Software
Reduced Attack Surface
Lesser-known software typically has a smaller user base, making it a less attractive target for hackers. Cybercriminals tend to focus their efforts on popular software with widespread adoption, where a single exploit can affect many users. By using software that flies under the radar, organizations can reduce their attack surface and lower the likelihood of being targeted.
Obscurity as a Defense
While security through obscurity is not a standalone strategy, it can provide an additional layer of protection when combined with other robust security measures. Lesser-known software is less likely to be on the radar of attackers who are scanning for common vulnerabilities in widely-used applications. This obscurity can make it more challenging for hackers to find and exploit weaknesses.
Unique Architectures and Codebases
Mainstream software often shares similar architectures and codebases, making it easier for hackers to develop exploits that can be reused across multiple platforms. Lesser-known software, on the other hand, may have unique architectures and codebases that require different attack methods. This diversity can slow down attackers and make it more difficult for them to successfully compromise systems.
Niche-Specific Security Features
Lesser-known software is often developed for niche markets with specific security needs. As a result, these solutions may incorporate specialized security features that are not present in more general-purpose software. These niche-specific features can provide enhanced protection tailored to the unique requirements of certain industries or applications.
Agility in Patching and Updates
Smaller software vendors can sometimes be more agile in responding to security vulnerabilities. With a smaller user base and less bureaucracy, they can quickly release patches and updates to address newly discovered vulnerabilities. This rapid response can help organizations stay ahead of emerging threats and reduce the window of exposure to potential attacks.
Considerations When Using Lesser-Known Software
While lesser-known software can offer unique protection advantages, it's important to consider the potential challenges and ensure a balanced approach to cybersecurity:
Thorough Evaluation
Conduct a thorough evaluation of the software's security features, development practices, and vendor reputation. Ensure that the software undergoes regular security audits and follows best practices in secure coding and vulnerability management.
Compatibility and Integration
Ensure that the lesser-known software integrates seamlessly with your existing IT infrastructure and security tools. Compatibility issues can create gaps in your security posture and hinder your ability to effectively manage and monitor your systems.
Vendor Support
Assess the level of support provided by the software vendor. Reliable support is crucial for timely updates, patch management, and resolving any security issues that may arise.
Comprehensive Security Strategy
While lesser-known software can provide additional protection, it should be part of a comprehensive security strategy. Combine it with other security measures such as firewalls, intrusion detection systems, multi-factor authentication, and employee training to create a robust defense against cyber threats.
Conclusion
In an era where cyber threats are increasingly sophisticated, exploring lesser-known software can offer unique protection advantages. By reducing the attack surface, leveraging obscurity, and benefiting from niche-specific security features, organizations can enhance their cybersecurity posture. However, it's essential to balance the use of lesser-known software with a comprehensive security strategy and ensure thorough evaluation and vendor support.
Contact Us Today
To learn more about how to integrate lesser-known software into your cybersecurity strategy and enhance your protection against cyber threats, contact us at CyberSecOp. Our experts are ready to help you navigate the complexities of cybersecurity and build a robust defense tailored to your organization's needs.
CyberSecOp Chronicles: Insights from CrowdStrike's 2024 Global Threat Report
CyberSecOp Chronicles presents a comprehensive overview of key insights extracted from CrowdStrike's 2024 Global Threat Report. In this report, we delve into six critical trends identified by CrowdStrike, including the persistence of identity-based attacks, the surge in cloud-environment intrusions, and the exploitation of third-party relationships by threat actors. With the addition of 34 new threat actors in 2023, the threat landscape continues to evolve rapidly, necessitating proactive cybersecurity measures. CyberSecOp, leveraging its expertise, has been aiding clients in ransomware remediation and payment processes from the outset. Accelerated network compromises and periphery network targeting further underscore the urgency for robust cybersecurity strategies. Our recommendations aim to equip organizations with actionable insights to fortify their defenses and mitigate emerging cyber threats effectively. Stay informed and secure with CyberSecOp Chronicles.
Highlights from CrowdStrike’s 2024 report
Identity-based and social engineering attacks still take center stage.
Cloud-environment intrusions increased by 75%.
Third-party relationships exploitation make it easier for attackers to hit hundreds of targets.
CrowdStrike added 34 new threat actors in 2023.
Attackers are compromising networks at a faster rate.
Attackers are targeting periphery networks.
CyberSecOp Chronicles presents a comprehensive breakdown of the key insights unveiled in CrowdStrike's 2024 Global Threat Report. This report sheds light on the evolving landscape of cyber threats, providing crucial information for enterprises to fortify their security posture.
Identity-Based Attacks Remain Pervasive
Despite advancements in cybersecurity measures, identity-based attacks remain a prominent threat. Threat actors continue to favor phishing, social engineering, and credential theft tactics. CrowdStrike's report highlights the persistence of attacks like phishing campaigns orchestrated by threat actors such as FANCY BEAR and SCATTERED SPIDER, emphasizing the need for robust security awareness training and multi-factor authentication (MFA) protocols.
Cloud Security Under Siege
The shift to cloud-based infrastructure has not gone unnoticed by cybercriminals. Cloud-environment intrusions saw a staggering 75% increase from 2022 to 2023, with attackers exploiting vulnerabilities for financial gain. Cloud-conscious attacks, where threat actors specifically target cloud environments, have surged by 110%, posing significant challenges for organizations worldwide. CyberSecOp emphasizes the importance of implementing cloud-native security solutions and educating teams on cloud security best practices.
Exploiting Third-Party Relationships
Supply chain attacks have emerged as a favored tactic among threat actors, offering a gateway to compromise multiple targets efficiently. CrowdStrike's findings underscore the prevalence of third-party exploitation, enabling attackers to infiltrate organizations across various sectors. CyberSecOp advocates for heightened vigilance when engaging with third-party vendors and emphasizes the importance of robust vendor risk management frameworks.
Growing Threat Actor Landscape
CrowdStrike's continuous monitoring identified 34 new threat actors in 2023, further expanding the diverse landscape of cyber threats. This influx underscores the dynamic nature of cybersecurity challenges and the need for adaptive security strategies. CyberSecOp, leveraging its expertise, has been assisting clients from the outset with ransomware remediation and ransomware payment, ensuring swift and effective response to such threats.
Accelerated Network Compromises
Attackers are increasingly adept at infiltrating networks and swiftly escalating their activities. The average breakout time for intrusion activities has decreased, with attackers leveraging stolen credentials and trusted relationships to expedite their malicious objectives. CyberSecOp stresses the importance of comprehensive endpoint detection and response (EDR) solutions to detect and mitigate intrusions effectively.
Focus on Periphery Networks
Threat actors are capitalizing on vulnerabilities in network peripheries, targeting devices and systems that may not be adequately monitored. This includes exploiting End of Life products and unmanaged devices, presenting significant challenges for defenders. CyberSecOp emphasizes the criticality of securing all network endpoints and implementing robust patch management practices to mitigate risks effectively.
Recommendations for Mitigating Cybersecurity Risks
In response to the evolving threat landscape outlined in CrowdStrike's report, CyberSecOp provides actionable recommendations for enhancing cybersecurity resilience:
Implement phishing-resistant MFA and extend it to legacy protocols.
Conduct comprehensive user awareness programs to combat social engineering tactics.
Deploy integrated security solutions capable of correlating threats across identity, endpoint, and cloud environments.
Prioritize the adoption of Cloud Native Application Protection Platforms for comprehensive cloud security.
Utilize consolidated security platforms offering complete visibility and threat detection capabilities.
By implementing these proactive measures, organizations can bolster their defenses against emerging cyber threats and safeguard their digital assets effectively.
CyberSecOp Chronicles News delivers timely insights and actionable strategies to navigate the complex cybersecurity landscape. Stay informed, stay secure.
Strengthening Security: Understanding Password Management, MFA, and Privilege Management
Safeguarding sensitive data requires a comprehensive strategy that encompasses more than traditional security measures. As organizations navigate the persistent threat of credential theft, adopting robust password management, Multi-Factor Authentication (MFA), and Privilege Management solutions is essential.
Password Management: Password management involves implementing policies and tools to regulate password creation, storage, and rotation. These three simple steps enable organizations to enforce strong password policies, securely store credentials, and ensure regular updates, reducing the risk of unauthorized access. Strong password management is crucial as it is the first defense against unauthorized entry into systems and data breaches.
Multi-Factor Authentication (MFA): Multi-Factor Authentication (MFA) provides an additional layer of security by requiring users to provide multiple verification forms before accessing systems or data. MFA significantly mitigates the risk of credential-based attacks, even if passwords are compromised. MFA enhances security by adding an extra barrier that malicious actors must overcome to gain unauthorized access.
Privilege Management: Privilege Management limits access to sensitive data and resources within an organization. It is crucial in maintaining data integrity and protecting critical assets from malicious actors. Only authorized users have the necessary permissions to access specific information or perform certain actions. Privilege Management helps prevent unauthorized access, data breaches, and insider threats by enforcing granular access controls and monitoring user privileges.
Summary:
Enhance Security Posture: Implement robust password management, MFA, and Privilege Management solutions to strengthen your organization's security posture and resiliency against cyber threats.
Regulatory Compliance: Effective password and user privilege management helps organizations comply with industry regulations and data protection laws, such as GDPR and PCI DSS.
Reduced Risk of Data Breaches: These measures significantly reduce the likelihood of data breaches and financial losses associated with cyberattacks by mitigating the risk of unauthorized access and credential theft.
Proactive Monitoring: Continuous monitoring for credential leaks and unauthorized access is essential to promptly detect and mitigate potential risks, safeguard sensitive data, and preserve organizational reputation.
How CyberSecOp Can Assist: CyberSecOp offers a comprehensive portfolio of services, such as Managed SOC or dark web monitoring services, to help organizations detect compromised credentials and proactively safeguard their data. Additionally, our team of cybersecurity experts provides tailored guidance and support in implementing robust security measures, conducting risk assessments, and ensuring compliance with industry regulations. By partnering with CyberSecOp, organizations can strengthen their defenses against cyber threats, protect sensitive information, and maintain trust with stakeholders in today's interconnected world.
Navigating the Sea of Data Privacy Laws and Cyber Regulations in 2024
Introduction
Fasten your digital seatbelts, because 2024 is shaping up to be a global whirlwind of data privacy and cybersecurity regulations. From five new comprehensive state data privacy laws in the US, including the Utah Consumer Privacy Act (UCPA) taking effect at the end of 2023, to radical new consumer health data privacy laws, businesses worldwide face unprecedented compliance challenges. But fear not, intrepid captains of your digital vessels! A robust security and privacy program can be your life raft in this regulatory storm, no matter where you navigate the digital seas.
The Perfect Storm: New Privacy, Breach Notification, and Cybersecurity Laws (Worldwide)
This year, businesses are facing a global regulatory tsunami:
1. New Privacy Laws: The US isn't alone. Comprehensive data privacy laws are popping up worldwide, with jurisdictions like Brazil, China, California, Australia, and now Utah, Texas, Oregon, Florida, and Montana leading the charge. Each law brings its own unique requirements, making compliance a complex international puzzle.
2. Breach Notification Blitz: Data breaches are a global concern, and governments are responding with stricter notification laws. From the EU's GDPR to India's Personal Data Protection Bill, expect to see tighter deadlines, broader notification requirements, and potential penalties for failing to report breaches promptly.
3. Cybersecurity Mandates on the March: Governments are raising the bar on cybersecurity, imposing new mandates and standards on businesses across industries. From zero trust requirements to software assurance guidelines, staying compliant will require proactive investment in your security posture.
Key US Data Privacy Laws and Health Data Privacy Regulations to Be Aware of in 2024:
Data Privacy Laws:
Utah Consumer Privacy Act (UCPA) - Effective December 31, 2023: Applies to businesses exceeding $25 million in revenue and processing data of 100,000 or more Utah residents. Grants Utah residents rights to access, delete, and opt-out of the sale of their personal data.
Texas Data Privacy and Security Act (TDPSA) - Effective July 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of Texas residents. Grants similar rights to UCPA, with additional restrictions on data deletion and requiring data security measures.
Oregon Consumer Privacy Act (OCPA) - Effective July 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of 100,000 or more Oregon residents. Grants similar rights to UCPA, with emphasis on data minimization and specific requirements for obtaining consumers' consent.
Florida Digital Bill of Rights - Effective July 1, 2024: Establishes principles for data privacy but does not create individual rights or enforcement mechanisms. Requires businesses to disclose data collection practices and implement data security measures.
Montana Consumer Data Privacy Act (MCDPA) - Effective October 1, 2024: Applies to businesses exceeding $25 million in revenue and handling data of 25,000 or more Montana residents. Grants rights to access, correct, and delete personal data, with exemptions for specific sectors.
Health Data Privacy Regulations:
Washington My Health My Data Act: Enacted in May 2023, prohibits the selling of Washingtonians' health data and restricts collection and sharing without consent. Imposes geofencing limitations around sensitive healthcare facilities.
Nevada Consumer Health Privacy Law (SB 370): Effective March 31, 2024, prohibits selling consumer health data without written consent and restricts collection and sharing. Similar geofencing limitations as Washington.
Amended California Consumer Privacy Act (CCPA) Regulations: Taking effect July 1, 2023, expand CCPA's scope to include specific consumer rights regarding their health data.
Colorado Universal Opt-Out Mechanisms: Effective July 1, 2023, requires businesses exceeding $100 million in gross revenue to offer a universal opt-out mechanism for the sale of personal data, including health data.
Connecticut Senate Bill 3: Took effect July 1, 2023, adds "consumer health data" to its data privacy act, requiring opt-in consent for selling and imposing geofencing restrictions around sensitive healthcare facilities.
Navigating the Calm After the Storm with CyberSecOp
2024 has indeed become a tsunami of data privacy and cybersecurity regulations, leaving businesses feeling like they're caught in a riptide. But fear not, weary sailors! Just as a lighthouse guides ships through treacherous waters, a robust security and privacy program can be your beacon of stability in this ever-changing regulatory landscape.
Implementing a comprehensive program isn't just about weathering the storm – it's about thriving in the calmer seas ahead. By prioritizing compliance, you can:
Avoid costly fines and legal action: Proactive measures significantly reduce the risk of non-compliance penalties.
Build trust and loyalty with customers: Demonstrating your commitment to data privacy fosters trust and encourages customer loyalty.
Reduce the likelihood and impact of data breaches: Robust security measures minimize the risk of breaches and mitigate their potential damage.
Gain a competitive edge: Being ahead of the curve on privacy regulations can attract privacy-conscious consumers and partners.
This is where organizations like CyberSecOp come in. We're not just your life raft in the storm – we're your skilled navigators, equipped with the expertise and resources to chart a course towards secure and compliant waters. Here's how we can help:
Conduct thorough security and privacy assessments: Identify vulnerabilities and gaps in your current posture, providing a clear roadmap for improvement.
Develop and implement tailored security and privacy programs: Create solutions that meet your specific needs, industry regulations, and global reach.
Stay ahead of the curve with ongoing monitoring and updates: Our team keeps you informed of evolving regulations and industry best practices.
Respond effectively to data breaches: Minimize the impact of breaches and ensure compliance with reporting requirements.
Offer expert guidance and support throughout your journey: Our team of experienced professionals is here to answer your questions and address your concerns.
Don't wait for the next regulatory wave to hit. Contact CyberSecOp today and let us help you navigate the ever-changing seas of data privacy and cybersecurity with confidence. Together, we can ensure your business sails smoothly towards a successful and secure future.
Russian Cyber Spy Group APT28 Backdoors Cisco Routers via SNMP
Russian-aligned cyber groups are seeking to target Western infrastructure, including Russian cyber spy group APT28 backdoors Cisco routers via SNMP
The UK's National Cyber Security Centre (NCSC) has warned that Russian-aligned cyber groups are seeking to target critical infrastructure in the West. The NCSC said that these groups are motivated more by ideology than by money, and that they pose a potential risk to crucial infrastructure systems in Western countries, especially those that are "poorly protected."
The NCSC said that the groups often focus on denial-of-service attacks, defacing websites and spreading misinformation. However, some of the groups have stated a desire to achieve a more disruptive and destructive impact against Western critical national infrastructure, including in the UK.
Without outside assistance, it is unlikely that the groups "have the capability to deliberately cause a destructive, rather than disruptive, impact in the short term." However, the NCSC warns that the groups may become more effective over time, and that organizations "act now to manage the risk against successful future attacks."
The NCSC has issued a number of recommendations to organizations to help them protect themselves from these threats. These include:
Keeping software up to date
Using strong passwords and multi-factor authentication
Implementing a robust incident response plan
Raising awareness of cyber security threats among employees
The NCSC also encourages organizations to report any suspicious activity to the NCSC or their local law enforcement agency.
The NCSC's warning comes as the UK and its allies continue to impose sanctions on Russia in response to its invasion of Ukraine. The NCSC said that the sanctions are likely to further motivate Russian-aligned cyber groups to target Western infrastructure.
The NCSC's warning is a reminder that cyber security is a top priority for organizations of all sizes. By taking steps to protect themselves from cyber threats, organizations can help to mitigate the risk of disruption and damage.
In addition to the NCSC's warning, it has also been reported that Russian cyber spy group APT28 has been backdooring Cisco routers via SNMP. APT28, also known as Fancy Bear or Sednit, is a Russian state-sponsored hacking group that has been linked to a number of high-profile cyberattacks, including the 2016 Democratic National Committee email hack.
The backdoor in Cisco routers is believed to have been used by APT28 to gain access to networks and steal sensitive data. The backdoor was discovered by researchers at Cisco Talos, who have released a report on the vulnerability.
The vulnerability is a remote code execution (RCE) vulnerability that affects Cisco IOS 15.2 and earlier versions. The vulnerability can be exploited by an attacker who can send a specially crafted packet to a vulnerable router.
Cisco has released a patch for the vulnerability. Organizations that are using Cisco IOS 15.2 or earlier versions should apply the patch as soon as possible.
The discovery of the backdoor in Cisco routers is a reminder that cyber threats are constantly evolving. Organizations need to be aware of the latest threats and take steps to protect themselves.
This vulnerability is one of several SNMP flaws that Cisco patched on June 29, 2017. Its exploitation requires an attacker to be able to access the vulnerable SNMP OID. For this, they first need to know the SNMP read-only credential, but these are not always hard to find.
Here are some tips for protecting your Cisco routers from this vulnerability:
Keep your software up to date. Cisco has released a patch for this vulnerability. Organizations that are using Cisco IOS 15.2 or earlier versions should apply the patch as soon as possible.
Use strong passwords and multi-factor authentication. Make sure that your SNMP credentials are strong and that you are using multi-factor authentication.
Implement a robust incident response plan. Have a plan in place in case your network is compromised. This plan should include steps for containing the breach, notifying affected parties, and recovering from the attack.
Raise awareness of cyber security threats among employees. Make sure that your employees are aware of the latest cyber threats and how to protect themselves.
In conclusion, the discovery of the backdoor in Cisco routers is a reminder that cyber threats are constantly evolving. Organizations need to be aware of the latest threats and take steps to protect themselves. By taking steps to protect yourself from cyber threats, you can help to mitigate the risk of disruption and damage.
Company CISOs and Boards Brace for New SEC Cybersecurity Regulations
The U.S. Securities and Exchange Commission (SEC) is proposing new cybersecurity regulations that would require public companies to report cybersecurity incidents within four business days and to have a board-approved cybersecurity policy in place. The regulations are designed to protect investors from the risks of cybercrime and to hold public companies accountable for their cybersecurity practices.
Company CISOs (chief information security officers) and boards are bracing for the new regulations, which they believe will be costly and burdensome to implement. However, they also recognize that the regulations are necessary to protect companies and their investors from the ever-growing threat of cybercrime.
In this blog post, we will discuss the SEC's proposed cybersecurity regulations and what they mean for company CISOs and boards. We will also provide tips for companies on how to prepare for the regulations.
The SEC's Proposed Cybersecurity Regulations
The SEC's proposed cybersecurity regulations would require public companies to do the following:
Report cybersecurity incidents within four business days. Companies would be required to report any cybersecurity incidents that have a material impact on the company or its investors.
Have a board-approved cybersecurity policy in place. The policy should address the company's cybersecurity risks and how it will manage those risks.
Conduct regular cybersecurity assessments. The assessments should identify and fix vulnerabilities in the company's systems and networks.
Have a plan in place to respond to a cyberattack. The plan should include steps to contain the damage, notify regulators and customers, and restore operations.
The SEC's proposed regulations are based on the Cybersecurity Framework, a voluntary framework developed by the National Institute of Standards and Technology (NIST). The Cybersecurity Framework provides a set of best practices for organizations to follow to improve their cybersecurity posture.
The SEC's proposed regulations are likely to face opposition from some companies, who argue that they are too burdensome and costly. However, the SEC is likely to move forward with the regulations, given the increasing risk of cybercrime.
What the Regulations Mean for Company CISOs and Boards
The SEC's proposed cybersecurity regulations will have a significant impact on company CISOs and boards. CISOs will need to ensure that their companies are in compliance with the regulations, which will require them to implement and maintain a robust cybersecurity program. Boards will need to oversee the company's cybersecurity program and ensure that it is effective.
The regulations will also have a financial impact on companies. Companies will need to invest in cybersecurity controls and staff to comply with the regulations. The costs of compliance will vary depending on the size and complexity of the company.
Tips for Companies on How to Prepare for the Regulations
Companies can take the following steps to prepare for the SEC's proposed cybersecurity regulations:
Assess your cybersecurity risks. The first step is to assess your company's cybersecurity risks. This will help you to determine which areas need the most attention.
Implement appropriate security controls. Once you know your risks, you can implement appropriate security controls to mitigate them. This could include things like firewalls, intrusion detection systems, and data encryption.
Train your employees. Your employees are your first line of defense against cyberattacks. Make sure they are trained on cybersecurity best practices, such as how to identify and avoid phishing scams.
Stay up-to-date on cybersecurity news and trends. The cybersecurity landscape is constantly changing. Make sure you stay up-to-date on the latest news and trends so you can protect your company from new threats.
Conduct regular cybersecurity audits. Regular cybersecurity audits can help you to identify and fix vulnerabilities before they are exploited by attackers.
Implement a cybersecurity awareness program. A cybersecurity awareness program can help your employees to understand the risks of cybercrime and how to protect themselves and the company.
By taking these steps, you can help your company to comply with the SEC's proposed cybersecurity regulations and protect itself from the ever-growing threat of cybercrime.
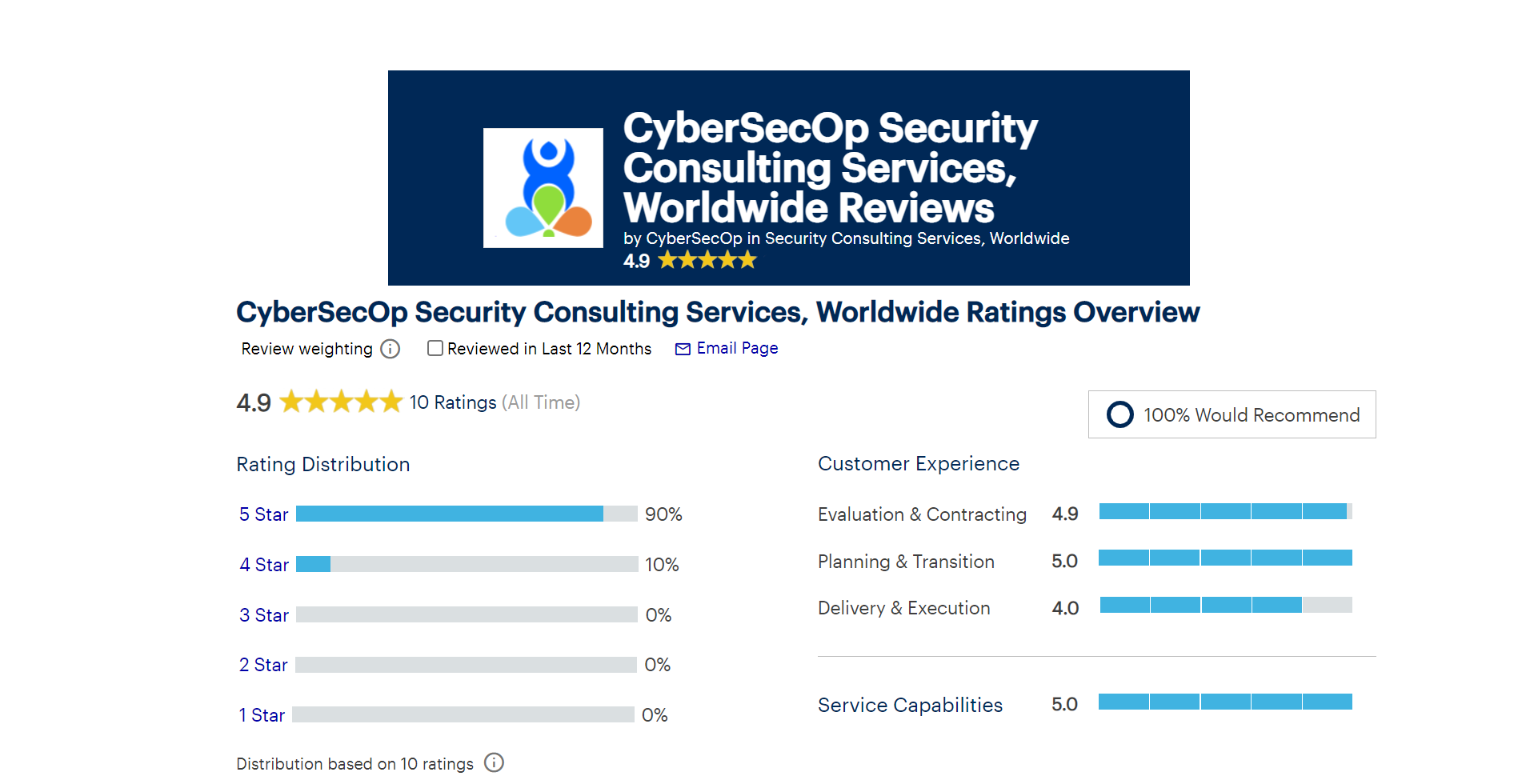
Gartner Recognizes CyberSecOp - Ranked 2nd for Security Consulting Worldwide.
CyberSecOp receives the highest overall score on Gartner Peer Insights for Security Consulting Services, Worldwide in 2022.
June 8, 2022 - CyberSecOp today announced that its Security Consulting Services received a 4.9 out of 5 overall rating from Gartner Peer Insights, placing CyberSecOp in the top two on Gartner’s Security Consulting Services Worldwide category.
"Peer reviews are extremely valuable for evaluating any purchase decision," said Josh Bauer, Executive Director at Loxo Oncology/Lilly. “CyberSecOp appears to actively and continuously listen to us as a customer to ensure they deliver innovative solutions and a valuable user experience."
“CyberSecOp is honored to receive our current ranking status and client feedback, and we will continue to prioritize customer satisfaction across the board." Vincent LaRocca, CEO & Co-Founder.
2022 Gartner Peer Insight
Gartner Peer Insights is the firm's platform for rating and reviewing enterprise technology solutions by end-user professionals for end-user professionals. Through user-contributed reviews from people who have actually used the services, the rating system combines expert opinions and peer insights. Peer Insights User Reviews offers a suite of interactive features for technology buyers, including the ability to customize evaluation criteria to create a quadrant view tailored to the user's goals and priorities. The platform employs rigorous methodologies, processes, and quality standards to deliver unbiased research and authentic peer reviews.
What is Gartner’s research?
Gartner research: Trusted insight for executives and their teams
Gartner research, which includes in-depth proprietary studies, peer and industry best practices, trend analysis, and quantitative modeling, enables us to offer innovative approaches that can help you drive stronger, more sustainable business performance.
Gartner research is unique, thanks to:
Independence and objectivity
Our independence as a research firm enables our experts to provide unbiased advice you can trust.
Actionable insights
Gartner’s research is unbiased, containing vital takeaways and recommendations for impactful next steps.
Proprietary methodologies
Our research practices and procedures distill large volumes of data into clear, precise recommendations.
CEO Letter - Cyber Security Operations Consulting (CyberSecOp)
Vinny La Rocca
Chief Executive Officer
We believe the foundation of our success is grounded in our vision to uplift enterprise security while ensuring confidentiality, integrity, and availability beyond best practices. That purpose is a virtuous circle. We create long-term value by empowering our people to deliver for our customers and communities. CyberSecOp helps organizations with security consulting, incident response and ransomware negotiation, payment, and recovery.
Our vital role to the community can be found in our mission statement. Our mission is to make the world a better place by defending and protecting our clients and partners from the theft of sensitive data through rapid incident response, cyber security programs, threat hunting, and the deployment of protective measures.
Sustainability and Growth
Our sustainability is rooted in our vision and mission statement. We believe this is an integral part of our growth and the reason we can keep our promises to our clients and partners.
Growth - Expectations for 2022 are higher than 2021, a year with 85% growth. Cyber risks currently rank as one of the top global threats to businesses and custodians of data, along with an ever-increasing number of data privacy and protection laws. These factors, combined with CyberSecOp’s ability to respond both proactively and reactively, put the company in a very favorable position.
Partnerships - CyberSecOp continues to develop, encourage and align an increasing number of strategic partnerships, allowing our teams to continually improve upon our Service Level Agreements (SLA’s) and expand our portfolio and breadth of services.
Culture - CyberSecOp has built a culture of people passionate about Cybersecurity and Professional Services. Uniting around a common goal brings our team together and ensures everyone is working to assist our clients with Cyber Security and compliance. We are a diverse workforce with an open and collaborative culture. Our goal is to be a leading security consulting company by empowering our employees to provide top-quality services measured against best-in-class industry benchmarks.
Customer Success - Customer satisfaction and success continue to be CyberSecOp’s highest priority, measured by retention and the increase in recurring services. Our success is a direct result of the success of our clients.
Our commitment to our mission, staff, clients and partners will continue to fuel our fast growth, creating long-term value for all stakeholders.
Ransomware Protection with Zero Trust Security
Zero Trust Security Architecture: Why is the Zero Trust Security Model important?
Endpoints represent the most significant attack surface, according to IDC, with over 70% of breaches originating on the endpoint. Organizations have a diverse mix of endpoints connected to their network, whether laptops, mobile endpoints, servers, firewall, wireless hotspots, or IoT devices. Zero-trust architecture works to ensure that users, devices and network traffic are all verified and subjected to least-privilege rules when accessing trusted resources. This way, compromised assets are limited in their scope and an attacker is prevented from moving laterally across the network.
With the rise of remote endpoints and high-profile ransomware attacks, businesses face more cybersecurity threats than ever before. Traditional network security models which assume users and computing devices within the “trusted” network environment are free from compromise and cannot secure organizations. Businesses are also now recognizing that attacks are more sophisticated and that internal networks are no longer more trustworthy than what lies outside the firewall. CyberSecOp and the security community recognized that Zero-trust security is the ultimate protection against ransomware.
Zero Trust Security Optimization
Zero Trust Network (ZTN) concept follows the mantra of never trust, always verify. Through this approach, organizations can reduce their open attack surface and adopt enhanced security capabilities beyond traditional defenses. Zero Trust enables organizations to reduce risk of their cloud and container deployments while also improving governance and compliance. Organizations can gain insight into users and devices while identifying threats and maintaining control across a network.
Traditional – manual configurations and attribute assignment, static security policies, least-function established at provisioning, proprietary and inflexible policy enforcement, manual incident response, and mitigation capability.
Advanced – some cross-solution coordination, centralized visibility, centralized identity control, policy enforcement based on cross-solution inputs and outputs, some incident response to pre-defined mitigations, some least-privilege changes based on posture assessments.
Optimal – fully automated assigning of attributes to assets and resources, dynamic policies based on automated/observed triggers, assets have dynamic least-privilege access (within thresholds), alignment with open standards for cross pillar interoperability, centralized visibility with retention for historical review
10 Ransomware Prevention Best Practices
Below are 10 best practices to help security professionals improve endpoint management:
CyberSecOp Managed Zero Trust security services were built with a new approach that creates zero-trust connections between the users and applications directly to solve this unique challenge. As a scalable, cloud-native platform, it enables digital transformation by securely connecting users,
devices, and applications anywhere, without relying on network-wide access. This platform is delivered by five key architecture attributes, unique to the CyberSecOp Managed Zero Trust Security services that together enable organizations to provide strong security and a great user experience to their employees and customers.
Multi-Factor Authentication (MFA) is is an electronic authentication method in which a computer user is granted access to a website or application only after successfully presenting two or more pieces of evidence to an authentication.
Email Security is critical because 74% of organizations in the United States experienced a successful phishing attack. Implementing email security gateway, DMARC, SPF, DKIM, stronger encryption, and MFA can reduce email compromise by over 98%.
CyberSecOp endpoint management solution that supports application isolation and containment technology is a form of zero-trust endpoint security. Instead of detecting or reacting to threats, it enforces controls that block and restrain harmful actions to prevent compromise. Application containment is used to block harmful file and memory actions on other apps on the endpoint. Application isolation is used to prevent other endpoint processes from altering or stealing from an isolated app or resources. This can prevent ransomware from being deployed on devices.
CyberSecOp endpoint management solution support Protective DNS Service (PDNS) refers to a service that provides Domain Name Service (DNS) protection (also known as DNS filtering) by blacklisting dangerous sites and filtering out unwanted content. It can also help to detect & prevent malware that uses DNS such as URL in phishing emails and hiding tunnels to communicate attackers' command and control servers.
CyberSecOp endpoint management solution supports bandwidth throttling so that remote endpoints can be continuously patched and secured rather than having to periodically send IT resources to remote locations. Our solution delivers patch management over the internet without requiring corporate network access. This ensures that internet-facing systems are patched in a proactive, timely manner rather than IT having to wait for these devices to visit the corporate network before they can be scanned and remediated.
CyberSecOp endpoint management reduces administrative overhead of endpoint management solutions to accommodate tight budgets and future growth. Our solutions support many endpoints using a single management system.
Consolidate endpoint management tools. Use a single tool to patch systems across Windows, Mac and variations of Unix operating systems to simplify administration, minimize the number of open network ports, and reduce the number of active agents on endpoints.
Validate that the endpoint management solution provides accurate, real-time endpoint data and reports. End users make changes to endpoints all the time and information that is hours or days old may not reflect a current attack surface.
CyberSecOp endpoint management allows administrators to apply patches that address the highest levels of risk first based on current endpoint status. This gives the biggest impact from remediation efforts.
Make sure the endpoint management solution enforces regulatory and corporate compliance policies on all endpoints constantly to avoid unintended drift and introduction of new vulnerabilities.
To conclude
Ransomware protection needs to go beyond detecting and blocking an initial malware infection at the email perimeter. Malware can enter your organization by other means, and cyber attacks often use the web channel to contact command and control servers and download the encryption keys necessary to complete the cyber attack.
What is a Zero Trust Security Architecture?
What is Zero Trust Security?
Zero Trust Security, also referred to as Zero Trust Networks or Zero Trust Architecture, is a security concept with one basic principle: don’t automatically trust anything to access your data, whether it’s connecting from outside your organization or within. Implementing Zero Trust involves various technologies, policies, and processes that help you better respond to the sophisticated approaches cybercriminals are using to gain access to sensitive data.
CyberSecOp’s Zero Trust Security service offers a comprehensive solution to secure all access to your applications and environment from any user, device, and location. Zero trust is a security model based on maintaining strict access controls.
With the recent and very public surge of cyber incidents affecting businesses and critical infrastructure, you may have heard the phrase ‘Zero Trust’ regarding cyber security and protecting business assets. So what is Zero Trust? Put Zero Trust is a model of thought that centers around never trusting any device, application, or person, regardless of whether they are attempting to connect from inside or outside the network. This methodology is gaining more and more traction as cloud application usage increases and the permanent shift to remote work is further implemented.
Zero trust is a strategy where everything (People, Data, Sessions, Devices, Applications) is treated as suspicious regardless of whether it's inside or outside the network. Essentially it is a ‘default deny’ posture, even for users within the organization. Instead of ‘Trust, verify the organization ‘Never Trusts, Always Verify.’ This is not accomplished by one tool but rather by policy, procedure, and means. Zero trust also focuses on Least Privilege- a Methodology that states no user should have more rights and permissions than what is needed to perform their work.
Zero Trust focuses on 5 pillars
1. Device Trust
2. User Trust
3. Transport and Session Trust
4. Application Trust
5. Data Trust
CyberSecOp can transform your business into a Zero Trust model by focusing on the tools, policy, and procedures to protect these five pillars and substantially decrease the odds of a successful breach.
ZERO TRUST SERVICES & ZERO TRUST PLATFORM
OVERVIEW: MANAGED SECURITY - MDR SERVICES - MANAGED COMPLIANCE
With Zero Trust network access for your private apps and systems, you no longer have to choose between user experience and security. CyberSecOp Managed Zero Trust services were built with a new approach that directly creates zero trust connections between the users and the applications to solve this unique challenge. As a scalable, cloud-native platform, it enables digital transformation by securely connecting users, devices, and applications anywhere without relying on network-wide access. This platform is delivered by five key architecture attributes unique to the CyberSecOp Managed Zero Trust services. Together, they enable organizations to provide strong security and a great user experience to their employees and customers.
ZERO TRUST SECURITY SOLUTION & SERVICES
When all employees have the same access privileges, the network is vulnerable. VPNs may provide adequate security for on-premise resources, but only Zero Trust solutions offer the user-based access rules required for proper cloud security.
Our Zero Trust solutions and services utilize multi-layered cybersecurity protection to transform your business with cybersecurity orchestration, automation, cybersecurity consulting, cloud, and managed security services. We implement a comprehensive approach to secure and protect businesses from cyber threats. Our cybersecurity services cover all the following areas needed for a zero-trust secure environment: Cybersecurity Program Strategy, Risk Management, Risk Assessment, Threat Intelligence, Incident Response, Advanced Malware & Ransomware Protection, Perimeter Security, Application Assessment, & Security Monitoring Services. We know where you are and how to protect your organization with a cybersecurity gap analysis to identify a more precise road map and a more robust cybersecurity program.
Zero Trust Cybersecurity Benefits and More
Zero trust networks, of course, extend beyond security. They are also inherently agile, a vital benefit for an increasingly remote workforce. As massive remote crews put unprecedented strain on cloud resources, the more stability and resilience you can build into your architecture, the better. Rather than backhauling remote data to a static data center, zero trust applications connect directly into your network from outside the perimeter, which helps free up bandwidth for DevOps and access business-critical cloud services.
ADOPT OUR ZERO TRUST SECURITY MODEL DEFENSE APPROACH
AUTOMATED PKI LIFECYCLE MANAGEMENT ZERO TRUST
The automated PKI lifecycle management platform enables Zero Trust by utilizing Public Key Infrastructure (PKI) certificates and key pairs, strengthening digital identities, and securing the connections between entities beyond the firewalled network architecture. In this age of digital transformation, the Zero Trust model increases the need for a consolidated, automated, and modern approach to PKI.
SECURE INTERNET GATEWAY
Control desktop, laptop, and mobile device access to malicious and inappropriate websites.
SECURE WEB GATEWAY
Protect against every kind of threat and ensure strict compliance with policies without slowing down your users.
ANTI SPAM & EMAIL GATEWAY
Secure Email Gateway protects organizations and employees from spear-phishing, malware, spam, and zero-day attacks. To ensure zero trust by removing spam and malicious email traffic before it enters your network to ensure zero trust.
ADVANCED ENDPOINT PROTECTION
Secure all your servers, desktops, laptops, and mobile devices from known and unknown malware–without requiring signatures or updates.
WEB APPLICATION FIREWALL
Powerful, real-time edge protection for
web apps and websites providing advanced
filtering, security, and intrusion protection.
SIMPLIFY COMPLIANCE REPORTING
Meet compliance requirements with no extra work. CyberSecOp Consultants have you covered, delivering streamlined reports of system access across the organization and zero trust technologies.
CYBER SECURITY OPERATIONS CENTER
Your always-on certified cybersecurity professionals team provides 24/7/365 surveillance and remediation services to ensure zero trust.
DATA LOSS PREVENTION
Monitor and control the movement of sensitive and confidential data across the network. Implement a ‘zero-trust’ data loss prevention (DLP) strategy utilizing activity, system-access, schedule, and content-based rules to ensure zero trust.
SINGLE SIGN-ON
A secure cloud single sign-on solution that IT, security, and users will love. Single sign-on solutions can quickly connect to and sync from identity stores including AD, LDAP, HR systems, and other third-party identity providers to ensure zero trust.
MULTI-FACTOR AUTHENTICATION
Secure, intelligent access to delight your workforce and customers. Secure your accounts and apps with a robust multi-factor authentication solution to keep the right people in and the wrong people out. Protect all your resources, including customer-facing and enterprise apps that store your most sensitive data to ensure zero trust.
SECURITY INCIDENT EVENT MANAGEMENT
We are providing actionable intelligence leveraging current events and data. Our SIEM collects logs and circumstances of the network traffic and web assets, security devices, operating systems, applications, and databases and reviews the vulnerabilities using artificial intelligence to process to ensure zero trust.
REMOTE MONITORING AND MANAGEMENT
Remote Monitoring and Management (RMM) is remote monitoring software that allows you to remotely monitor and manage endpoints, computers, mobile devices, and networks from a centralized console to ensure zero trust.
MANAGED CYBERSECURITY SERVICES
CyberSecOp is a cybersecurity service provider offering a range of solutions related to protecting computer systems within an organization. Cybersecurity is a constantly evolving industry created in response to hacking, viruses, and other personal and business data threats. CyberSecOp-managed cybersecurity services will provide your business with expertise in the three stages of business cybersecurity protection services: assessment, security program implementation, and governance. We implement external and internal cybersecurity solutions with advanced IT security software and hardware solutions. CyberSecOp provides several cybersecurity tools to ensure end-to-end cybersecurity protection. We also offer IT outsourcing services to address your company’s information technology needs.
End to End Cybersecurity Services
We offer cybersecurity and strategic advisory consulting, incident response, design, and deployment services. We will implement a security program strategy to align information security policy, security controls, and plan with business goals.
LEADING MANAGED CYBERSECURITY SERVICE PROVIDER
CyberSecOp is a leader in managed cybersecurity services. Our cybersecurity team will implement a secure framework and constantly monitor and protect your business from cyber threats. Our cybersecurity experts integrate business context intelligence, threat data, and cybersecurity insights to protect your assets and data. The risk scene develops with rising rates; it takes more oversight with cybersecurity services to effectively ensure your organization is secure from cyber threats. Our team will work with your firm to identify any risks or threats it may face. We will deliver recommendations highlighting security flaws in your environment and the immediate steps to these issues.
CYBERSECURITY AS A SERVICE (CSAAS)
CyberSecOp offers proactive Cybersecurity as a Service (CSaaS) to mitigate cyber risk. Every business needs defense in-depth, includincludessecurity solutions and cybersecurity experts who can deploy and monitor them.
Transform and strengthen your cybersecurity to become proactive, effective and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cybersecurity Services can help?