CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Don't let a cyber security breach damage your reputation
Cybersecurity breaches have cost many organizations some of their largest clients. While most organizations quickly hire legal experts, public relations teams, and a cyber security firm like CyberSecOp, the reputation damages have already begun. For example, your client may not have access to your services for hours before you realize that your system was affected.
Prime attack time
Attackers are strategic with time selection to minimize their activities being seen by employees. Most attackers operate on weekends or at night, knowing that most organizations’ employees do not access or monitor systems at this time.
When does reputation damage begin?
Reputation issues may begin long before the organization knows about an attacker. Some attackers disclose information on social media so that the organization will act quickly to their demands. Most cybercriminals spend an average of three months on clients’ systems before they act, but by this point, they may have already sold your data on the dark web or to your competitor.
Disclosing sensitive information violates privacy policies and requirements such as CCPA, GDPR, and some states’ and countries’ data protection regulations or requirements. The data disclosed may also include clients and your client’s customer information, putting your clients at risk. They, too, need to report the breach to their customers and provide the necessary protection to protect their customer’s credit and identity.
Reputation damage extends to your client.
At this point, not only is your organization’s reputation is in jeopardy, but also the reputation of your client and your client’s customers. All of these expenditures may be a liability to your organization if the breach is on your side, especially if there is evidence that you didn’t take due care regarding your organization’s security posture.
Conclusion
Defense-in-depth security program
Having a defense-in-depth security program such as those offered by CyberSecOp, cannot only save your business money but can also help you compete against other companies that have not implemented a security program. Most organizations have implemented a vendor management program to mitigate their threat against a third-party risk. A security program that includes third-party risk management is critical to identifying and remediating internal and external threats.
Don't Forget the Fundamentals on World Backup Day 2022
March 31st is apparently world backup day! Who knew? In honor of that it seemed like a good time for a quick post extolling the virtues of backups. According to the “WorldBackupDay” website, 21% of people have never taken a backup and 30% of computers are already infected with malware. While these stats are related to individuals and not necessarily businesses the stats sound about right.
Take Backups!
Regardless of whether you are a small business or a global Fortune 500 company, backups are an essential part of your organization's risk management plan. It’s easy to be lulled into complacency. Just the other day I was working with an organization in the mechanical service delivery industry who’s entire “IT Infrastructure” was a single 2017 iMac. They never bothered with any additional machines, backups and other such items because they had been told that Mac’s were “bulletproof” and not susceptible to the common maladies of the humble PC. Unfortunately, their Mac was susceptible to good old fashioned old age and corrupt updates. As a result they found themselves in a position where they had a large proposal for a job due the next day and the only place it existed was on this one broken Mac. Now fortunately for them, we were able to recover the system and restore their data, but what if we hadn’t been able to? It is absolutely critical, regardless of the size of your organization that you have a backup solution in place tailored to your specific needs. Stay tuned for some suggestions on backup providers we love at the end of this article!
Test your Backups!
This might seem like a no-brainer, but in addition to taking backups, it's critically important that you TEST your backups. Having a plan and procedure in place for how to recover your data in the event of a disaster is just as important as taking the backup in the first place! In my last example of the company with a single iMac. What if they had set up icloud and automatically configured their file to sync there. If I had asked the owner of the business if he had the password for the icloud account or even knew what account icloud was associated with, I wonder if he would have known? Having a documented plan that outlines where your backups go, what authentication is used to access them, how frequently they are taken, and how to restore them to a device is critical. If you are a larger organization you probably want to start having conversations about RTO and RPO at this point as well and ensuring your backup solution can meet those goals. (Recovery Time Objective, Recovery Point Objective.) Essentially, how long will it take to recover my data and how much time passes between backups, or put more simply, how much data can I afford to lose? 1 Day’s Worth? 1 Weeks worth? Less? More? Make sure your backup solution can meet your specific needs and goals!
Protect your Backups!
Finally, congrats if you're taking and testing your backups! Are you also protecting your backups? You’re probably thinking, protecting my backups?! What’s this guy going on about now? Consider this, you backup your information every night and test it regularly. You sleep easy at night knowing that you can recover should the worst happen. However, what you don’t know, is that earlier last month one of your employee’s laptops was infected with a virus. This virus replicated across your organization but stayed dormant, collecting information about your company and environment but not taking any malicious actions yet. The threat actor discovers that your backups run nightly and are stored for 4 months on a network share. The virus then deletes all of your backups and begins encrypting your files. When you return to work the next day and find all of your computers and files encrypted, you attempt to recover from backup only to find your backups have been deleted! This is an oversimplification of the process but this is essentially what the bad guys are doing. There are many ways to prevent this sort of attack including storing backups in offline or immutable data stores, encrypting your backups and storing multiple copies of every backup in different locations. At this point you might be thinking “I can simply copy files to an external drive of some sort on a regular basis right?” , but what if something happens to that drive? As the old timer’s say, “two is one and one is none”. The idea is that if you only have one, something could happen to it and then you have none. Have a backup plan for your backup plan!
Conclusion
Now that you’re completely terrified know that there are solutions out there for all of these problems. Proper backup planning is a key component of every organization's Disaster Recovery, Business Continuity and Incident Response Planning. If you are looking for assistance with any of those plans, make sure you give us at CyberSecOp a call, we would love to help you with this.
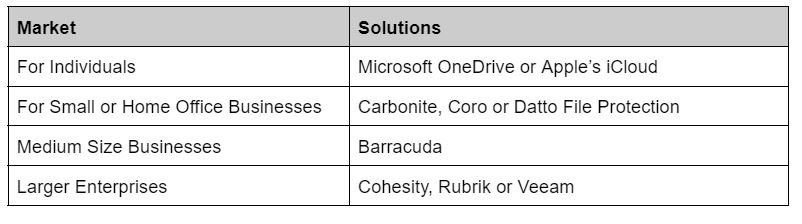
In the meantime if you're looking for somewhere to start with backup’s here are some of our favorites.
Author: Timothy Burger
Chrome and Edge Should Be Updated Due to a Zero-Day Vulnerability
Google and Edge has released an update to remediate a critical zero-day chrome exploit. The zero-day is a weakness in Edge and Chrome's JavaScript engine that can be used by hackers to inject their code into your browser. Google explains for zero-day exploit CVE-2022-1096, first reported to the company by an anonymous tip on March 23. As part of our commitment to continuous support in security monitoring and enhancement we advise all clients to update to Chrome version 99.0.4844.84 and Microsoft Edge 99.0.1150.55 of as soon as possible.
DETAILS AND REMEDY FOR MICROSOFT AND GOOGLE
At this time Microsoft and Google won't provide much more information other than admitting there have already been attacks leveraging this zero-day weakness and keeping some information away from the public as a safety measure, stating that full details on how the exploit worked won't be made public until most users have the fix. Fortunately, this time Microsoft and Google was apparently able to issue a patch before the exploit became widely known.
Normally Chrome updates happen in the background when you close and reopen your computer's browser.
Microsoft issued its own notice and said the issue was fixed in Edge.
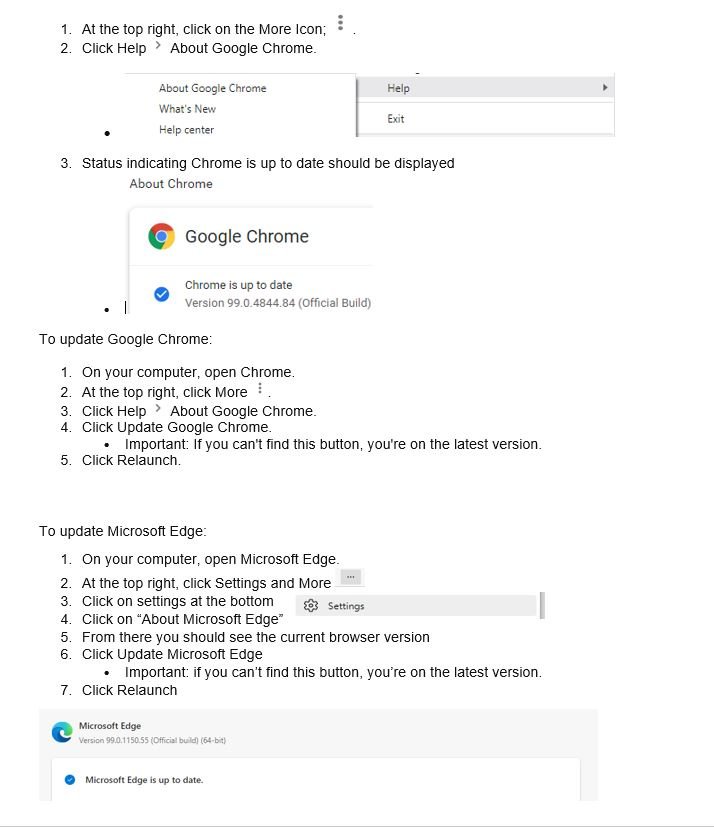
Please follow the steps below to ensure you have the latest version of Chrome.
Remediation Efforts
On your computer, open Chrome.
Author: Tanvir Ahmed
ADVISORY: Reports of possible digital breach
ADVISORY: Reports of possible digital breach
Okta investigating reports of possible digital breach
Lapsus$, a cyber extortion gang, has announced that they have breached Microsoft and Okta.
The gang has leaked torrents containing source code for Bing, Bing Maps, and Microsoft Cortana, as well as a screenshot of an internal Microsoft Azure DevOps account. They also claim to have had “Superuser/Admin” access to Okta’s systems for two months, and said its focus was “only on Okta customers.”
Both Microsoft and OKTA have started an investigation to confirm or disprove they’ve been breached.
Recommended Actions:
These attacks are a striking reminder of the supply chain’s cyber risks - Real risks brought to organizations by use of softwares and systems like OKTA, Microsoft, as well as many others.
Please work with your vCISO or Risk Manager to ensure the proper Vendor Security controls and processes are in place as well as other vital security controls that will drastically reduce the possibility of these dangerous hacks spilling into your network and systems.
Author: Michael Sardari
CISA's 'Shields Up' Alert Highlights Foreign Cyberthreats
Cyberwarfare is the battlefield of today. Increased geopolitical tensions stemming from Russia's unprovoked attack on Ukraine has led to CISA (the Cybersecurity & Infrastructure Security Agency) issuing a "Shields Up" bulletin. Every organization must be prepared to respond to disruptive cyber activity, especially those in critical infrastructure fields.
Here are some tips to help you keep your organization safe in these trying times.
Reduce the likelihood of a damaging cyber intrusion
Use MFA or Multi-Factor-Authentication everywhere.
Ensure all Systems are patched and up to date.
Consider increasing patch frequency if not already real-time.
Take steps to quickly detect a potential intrusion
Run, update and monitor a strong Endpoint Protection Program.
Consider increasing Spam and Phishing filter sensitivity.
Disable any non-essential ports and protocols, specifically through external gateways.
Ensure that the organization is prepared to respond if an intrusion occurs
Review your incident response plan and ensure it is up to date and all parties are clear on their roles.
Maximize your organization's resilience to a destructive cyber incident
Ensure that you are taking regular backups and that your backups are encrypted and immutable.
Test your backup and recovery procedures.
Communicate with your users, the best and strongest defense is a well-educated and well-prepared workforce.
If you are a CyberSecOp customer today in either our vCISO or vSOC program your risk manager will be reaching out shortly to ensure this guidance is being implemented to the extent possible within your organization.
If you are not currently enrolled in one of our plans and need assistance assessing your posture and capabilities, please feel free to reach out.
What is a Zero Trust Security Architecture?
What is Zero Trust Security?
Zero Trust Security, also referred to as Zero Trust Networks or Zero Trust Architecture, is a security concept with one basic principle: don’t automatically trust anything to access your data, whether it’s connecting from outside your organization or within. Implementing Zero Trust involves various technologies, policies, and processes that help you better respond to the sophisticated approaches cybercriminals are using to gain access to sensitive data.
CyberSecOp’s Zero Trust Security service offers a comprehensive solution to secure all access to your applications and environment from any user, device, and location. Zero trust is a security model based on maintaining strict access controls.
With the recent and very public surge of cyber incidents affecting businesses and critical infrastructure, you may have heard the phrase ‘Zero Trust’ regarding cyber security and protecting business assets. So what is Zero Trust? Put Zero Trust is a model of thought that centers around never trusting any device, application, or person, regardless of whether they are attempting to connect from inside or outside the network. This methodology is gaining more and more traction as cloud application usage increases and the permanent shift to remote work is further implemented.
Zero trust is a strategy where everything (People, Data, Sessions, Devices, Applications) is treated as suspicious regardless of whether it's inside or outside the network. Essentially it is a ‘default deny’ posture, even for users within the organization. Instead of ‘Trust, verify the organization ‘Never Trusts, Always Verify.’ This is not accomplished by one tool but rather by policy, procedure, and means. Zero trust also focuses on Least Privilege- a Methodology that states no user should have more rights and permissions than what is needed to perform their work.
Zero Trust focuses on 5 pillars
1. Device Trust
2. User Trust
3. Transport and Session Trust
4. Application Trust
5. Data Trust
CyberSecOp can transform your business into a Zero Trust model by focusing on the tools, policy, and procedures to protect these five pillars and substantially decrease the odds of a successful breach.
ZERO TRUST SERVICES & ZERO TRUST PLATFORM
OVERVIEW: MANAGED SECURITY - MDR SERVICES - MANAGED COMPLIANCE
With Zero Trust network access for your private apps and systems, you no longer have to choose between user experience and security. CyberSecOp Managed Zero Trust services were built with a new approach that directly creates zero trust connections between the users and the applications to solve this unique challenge. As a scalable, cloud-native platform, it enables digital transformation by securely connecting users, devices, and applications anywhere without relying on network-wide access. This platform is delivered by five key architecture attributes unique to the CyberSecOp Managed Zero Trust services. Together, they enable organizations to provide strong security and a great user experience to their employees and customers.
ZERO TRUST SECURITY SOLUTION & SERVICES
When all employees have the same access privileges, the network is vulnerable. VPNs may provide adequate security for on-premise resources, but only Zero Trust solutions offer the user-based access rules required for proper cloud security.
Our Zero Trust solutions and services utilize multi-layered cybersecurity protection to transform your business with cybersecurity orchestration, automation, cybersecurity consulting, cloud, and managed security services. We implement a comprehensive approach to secure and protect businesses from cyber threats. Our cybersecurity services cover all the following areas needed for a zero-trust secure environment: Cybersecurity Program Strategy, Risk Management, Risk Assessment, Threat Intelligence, Incident Response, Advanced Malware & Ransomware Protection, Perimeter Security, Application Assessment, & Security Monitoring Services. We know where you are and how to protect your organization with a cybersecurity gap analysis to identify a more precise road map and a more robust cybersecurity program.
Zero Trust Cybersecurity Benefits and More
Zero trust networks, of course, extend beyond security. They are also inherently agile, a vital benefit for an increasingly remote workforce. As massive remote crews put unprecedented strain on cloud resources, the more stability and resilience you can build into your architecture, the better. Rather than backhauling remote data to a static data center, zero trust applications connect directly into your network from outside the perimeter, which helps free up bandwidth for DevOps and access business-critical cloud services.
ADOPT OUR ZERO TRUST SECURITY MODEL DEFENSE APPROACH
AUTOMATED PKI LIFECYCLE MANAGEMENT ZERO TRUST
The automated PKI lifecycle management platform enables Zero Trust by utilizing Public Key Infrastructure (PKI) certificates and key pairs, strengthening digital identities, and securing the connections between entities beyond the firewalled network architecture. In this age of digital transformation, the Zero Trust model increases the need for a consolidated, automated, and modern approach to PKI.
SECURE INTERNET GATEWAY
Control desktop, laptop, and mobile device access to malicious and inappropriate websites.
SECURE WEB GATEWAY
Protect against every kind of threat and ensure strict compliance with policies without slowing down your users.
ANTI SPAM & EMAIL GATEWAY
Secure Email Gateway protects organizations and employees from spear-phishing, malware, spam, and zero-day attacks. To ensure zero trust by removing spam and malicious email traffic before it enters your network to ensure zero trust.
ADVANCED ENDPOINT PROTECTION
Secure all your servers, desktops, laptops, and mobile devices from known and unknown malware–without requiring signatures or updates.
WEB APPLICATION FIREWALL
Powerful, real-time edge protection for
web apps and websites providing advanced
filtering, security, and intrusion protection.
SIMPLIFY COMPLIANCE REPORTING
Meet compliance requirements with no extra work. CyberSecOp Consultants have you covered, delivering streamlined reports of system access across the organization and zero trust technologies.
CYBER SECURITY OPERATIONS CENTER
Your always-on certified cybersecurity professionals team provides 24/7/365 surveillance and remediation services to ensure zero trust.
DATA LOSS PREVENTION
Monitor and control the movement of sensitive and confidential data across the network. Implement a ‘zero-trust’ data loss prevention (DLP) strategy utilizing activity, system-access, schedule, and content-based rules to ensure zero trust.
SINGLE SIGN-ON
A secure cloud single sign-on solution that IT, security, and users will love. Single sign-on solutions can quickly connect to and sync from identity stores including AD, LDAP, HR systems, and other third-party identity providers to ensure zero trust.
MULTI-FACTOR AUTHENTICATION
Secure, intelligent access to delight your workforce and customers. Secure your accounts and apps with a robust multi-factor authentication solution to keep the right people in and the wrong people out. Protect all your resources, including customer-facing and enterprise apps that store your most sensitive data to ensure zero trust.
SECURITY INCIDENT EVENT MANAGEMENT
We are providing actionable intelligence leveraging current events and data. Our SIEM collects logs and circumstances of the network traffic and web assets, security devices, operating systems, applications, and databases and reviews the vulnerabilities using artificial intelligence to process to ensure zero trust.
REMOTE MONITORING AND MANAGEMENT
Remote Monitoring and Management (RMM) is remote monitoring software that allows you to remotely monitor and manage endpoints, computers, mobile devices, and networks from a centralized console to ensure zero trust.
MANAGED CYBERSECURITY SERVICES
CyberSecOp is a cybersecurity service provider offering a range of solutions related to protecting computer systems within an organization. Cybersecurity is a constantly evolving industry created in response to hacking, viruses, and other personal and business data threats. CyberSecOp-managed cybersecurity services will provide your business with expertise in the three stages of business cybersecurity protection services: assessment, security program implementation, and governance. We implement external and internal cybersecurity solutions with advanced IT security software and hardware solutions. CyberSecOp provides several cybersecurity tools to ensure end-to-end cybersecurity protection. We also offer IT outsourcing services to address your company’s information technology needs.
End to End Cybersecurity Services
We offer cybersecurity and strategic advisory consulting, incident response, design, and deployment services. We will implement a security program strategy to align information security policy, security controls, and plan with business goals.
LEADING MANAGED CYBERSECURITY SERVICE PROVIDER
CyberSecOp is a leader in managed cybersecurity services. Our cybersecurity team will implement a secure framework and constantly monitor and protect your business from cyber threats. Our cybersecurity experts integrate business context intelligence, threat data, and cybersecurity insights to protect your assets and data. The risk scene develops with rising rates; it takes more oversight with cybersecurity services to effectively ensure your organization is secure from cyber threats. Our team will work with your firm to identify any risks or threats it may face. We will deliver recommendations highlighting security flaws in your environment and the immediate steps to these issues.
CYBERSECURITY AS A SERVICE (CSAAS)
CyberSecOp offers proactive Cybersecurity as a Service (CSaaS) to mitigate cyber risk. Every business needs defense in-depth, includincludessecurity solutions and cybersecurity experts who can deploy and monitor them.
Transform and strengthen your cybersecurity to become proactive, effective and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cybersecurity Services can help?
Home Routers Major Weakness in Work from Home Revolution
‘Prepping’ for Work from Home
For the past few years employees and employers alike extolled the virtues of working from home (‘WFH’). We’ve heard the stories of how it leads to a happier and more productive employee, less overhead for the employer, and just more flexibility overall. Most people knew a shift would come eventually – kind of like the shift to IPV6- but it stalled and stalled. Then the pandemic happened and WFH had been thrust upon us with such force that businesses were, and still are, scrambling to get the pieces in place for an effective remote staff.
It is no longer a secret that WFH is here to stay. Many businesses including Fujitsu and Twitter have just gone ahead and implemented WFH ‘forever’. With this change come challenges. One of those is the security of routers in the millions upon millions of homes that now serve as working offices. According to a study by Germany’s Fraunhofer Institute for Communication, vendors have failed to fix hundreds of vulnerabilities in their consumer-grade routers, leaving hundreds of thousands of users exposed to a wide range of attacks. "Nearly all were found to have security flaws, some of them very severe," the Fraunhofer Institute said in a press release. "The problems range from missing security updates to easily decrypted, hard-coded passwords, and known vulnerabilities that should have been patched long ago."
Advice on next steps
So what should we do? The first step is to know the make and model of your router. Research it for any known vulnerabilities, as there may be some cases where the device is so insecure that even patching it still leaves it vulnerable. Once you’ve decided if it is worth keeping the device make sure that it automatically installed firmware updates. If not you may need to manually update it. A task that is well worth the effort. Another task is to make sure that the administrator password for the router has been changed from the default admin password. Many routers now have unique default passwords for their routers- but there are still plenty out there that don’t.
WFH Users should use complex passwords on their routers including:
· Uppercase and Lowercase
· Numbers and Symbols
· At least 8 characters long
You should also use the strongest Wi-Fi encryption your router supports. WPA3 (Wi-Fi Protected Access Version 3) is best.
You may have children working, playing, and streaming while you are home. Ensure they use their own devices and do not surf on your work devices.
Router configuration and device hardening are just one of the many layers of security that businesses need to adapt and expand to their remote workforce. We here at CyberSecOp would not be surprised if, sooner rather than later, companies begin purchasing, installing, and administering home routers to ensure a secure endpoint to endpoint networking. Until then remain vigilant and patch patch patch!