CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
CrowdStrike Incident: Shifting Boardroom and Government Cybersecurity Strategies
The recent CrowdStrike incident, which was triggered by a problematic update rather than a breach, has become a significant turning point for boardroom executives and government leaders. This incident has exposed vulnerabilities in current cybersecurity strategies and revealed how reliance on a few dominant suppliers can jeopardize national security. As a result, there has been a notable shift in how these leaders approach their cybersecurity measures.
The Vulnerability of Supply Chain Dependencies
The CrowdStrike incident highlighted a crucial vulnerability: many organizations, including government entities and large corporations, depend on the same cybersecurity products. This shared reliance means that an issue with one supplier can have far-reaching effects, potentially disrupting entire sectors or even national security. The problem is not just with the individual products but with the interconnected nature of the supply chain.
A Strategic Shift: Exploring Alternatives
In light of this realization, boardroom and government leaders are reevaluating their cybersecurity strategies. There is a growing emphasis on exploring alternatives to the widely-used products that contributed to the incident. The focus is now on less popular software solutions that offer comparable services with enhanced security features. This strategic shift aims to minimize the risk of widespread disruptions by diversifying the technology landscape and reducing dependency on a few dominant suppliers.
Microsoft’s New Strategy: Enhancing Kernel-Level Protection
In response to the broader concerns highlighted by the CrowdStrike incident, Microsoft is intensifying its focus on kernel-level security. The kernel, being the core component of the operating system, is a critical area that attackers often target. Microsoft's new strategy includes:
Strengthened Kernel Defenses: Implementing advanced measures to protect the kernel from attacks such as rootkits and unauthorized modifications.
Improved System Integrity: Ensuring that the core system remains secure and unaltered to prevent potential exploits.
Advanced Threat Detection: Deploying new technologies that offer better detection and response to kernel-level threats.
By focusing on kernel-level security, Microsoft aims to address the vulnerabilities that have been exposed and enhance the overall resilience of its operating systems.
CyberSecOp’s Role in Diversifying Security Strategies
At CyberSecOp, we have been proactively helping our clients diversify their vendor portfolios over the years. Our approach emphasizes not only identifying alternative solutions but also integrating them into a comprehensive security strategy. This diversification helps mitigate risks associated with over-reliance on a single supplier and ensures that our clients have a robust defense against potential threats.
Moreover, CyberSecOp operates on a diversified supply chain model, aligning with the evolving needs of our clients and the broader market. This model ensures that we can provide a wide range of secure solutions and adapt to changes in the technology landscape effectively.
Opportunities for Smaller Technology Providers
The shift towards exploring alternative solutions is opening up opportunities for smaller, emerging technology providers. As larger organizations and government bodies seek alternatives to mainstream products, they are finding that smaller, innovative companies offer competitive solutions with robust security measures. This shift is leveling the playing field and allowing new players to enter the market, challenging the existing dominance of major tech giants.
Implications for the Technology Market
Increased Market Diversity: The push towards alternative solutions is fostering a more diverse technology market. Smaller companies are now better positioned to compete, offering specialized and secure solutions that might have previously been overlooked.
Enhanced Security: Organizations can improve their overall security posture by integrating a broader range of products and solutions. This diversification helps to mitigate the risk associated with relying on a single supplier.
Growth in Innovation: The entry of smaller players into the market encourages innovation, bringing fresh perspectives and cutting-edge technologies to address cybersecurity challenges.
Reduced Monopoly Power: As organizations and government bodies explore alternative solutions, the dominance of a few major tech firms is being challenged, leading to a more competitive and balanced industry.
Conclusion
The CrowdStrike incident, stemming from a problematic update, has triggered a significant shift in boardroom and government cybersecurity strategies. By moving away from over-reliance on a few suppliers and exploring diverse alternatives, leaders are enhancing their security measures and opening doors for smaller technology providers. Additionally, Microsoft’s new focus on kernel-level protection represents a proactive step toward addressing core vulnerabilities.
At CyberSecOp, our commitment to diversifying vendor portfolios and operating on a diversified supply chain model aligns with these evolving strategies, helping clients navigate these changes and strengthen their security posture. This shift promises to foster a more dynamic and secure technology market, drive growth, and reduce the monopolistic control exerted by larger organizations. Staying informed and adaptable will be crucial for organizations navigating these changes and capitalizing on new opportunities in the cybersecurity sector.
The Rise of VCISO and VCTO: Safeguarding Systems and Ensuring Compliance
Today's digital landscape looms large with cyber threats, and ever changing compliance and regulatory requirements organizations are increasingly turning to Virtual Chief Information Security Officers (VCISOs), Virtual Chief Technology Officers (VCTOs) and related outside counsel to bolster their defenses and ensure compliance. These virtual roles offer specialized expertise and strategic guidance without the overhead costs associated with full-time executive positions. For enterprise organizations, having the ability to engage an independent third party to validate ideas, policies and processes while also providing guidance and support to the technical executive suite is a key differentiator.
Let's explore why organizations are embracing VCISOs and VCTOs and how these professionals are essential in protecting systems and ensuring compliance.
Expertise in Cybersecurity
Cybersecurity threats are evolving at an alarming rate, with sophisticated attacks targeting businesses of all sizes. VCISOs play a crucial role in developing, implementing and validating robust cybersecurity strategies tailored to an organization's unique needs. They bring extensive experience in threat assessment, risk management, incident response, and security best practices. By partnering with a VCISO, organizations gain unbiased access to up-to-date knowledge and proactive measures to mitigate risks.
Strategic Technology Leadership
Technology, the backbone of modern enterprises, driving innovation, efficiency, and growth also can be our Achilles heal if not properly governed
VCTOs focus on strategic oversight of an organization's technology infrastructure and operations. They ensure technology investments align with business objectives while optimizing performance and scalability while managing the threat landscape. From cloud adoption to digital transformation initiatives, VCTOs offer invaluable insights and guidance to navigate complex technological landscapes.
Cost-Effective Solution
VCISOs and VCTOs offer cost-effective solutions that provide expertise on an as needed and scheduled basis. This allows organizations to access top-tier talent with the flexibility and level of enablement organizations can use to address their needs and priorities.
Compliance and Regulatory Adherence
Compliance has become non-negotiable in an era of stringent data protection regulations such as GDPR, CCPA, and HIPAA. VCISOs and VCTOs are well-versed in regulatory requirements and industry standards, ensuring organizations adhere to relevant laws and guidelines. They validate established governance frameworks, conduct audits, and implement controls to safeguard sensitive data and maintain regulatory compliance. With the benefit of being an independent third party, VCISOs and VCTs are able to provide the oversight and governance auditors require and insurance companies appreciate, further mitigating financial risk and exposure.
Tailored Solutions for Diverse Industries
Whether in finance, healthcare, or manufacturing, these virtual executives collaborate closely with internal teams to align security and technology strategies with organizational goals. It is important to keep in mind that every industry faces unique challenges and changing regulatory landscapes.
Conclusion
Having access to VCISOs and VCTOs is key to enhancing an organizations strategic advantage as the technical and threat landscapes continue to evolve. By leveraging the skills of VCISOs and VCTOs, organizations are better positioned against cyber threats, optimize technology investments, and maintain regulatory integrity, safeguarding their reputation and sustaining long-term success.
CyberSecOp Managed Security with AI offers MDM, DLP, SIEM, and XDR services.
CyberSecOp is a managed security service provider (MSSP) that offers a range of security services, including AI-powered security, Data Loss Prevention (DLP), Security Information and Event Management (SIEM), and Extended Detection and Response (XDR).
AI-powered security is a cutting-edge technology that uses artificial intelligence and machine learning algorithms to detect and prevent security threats in real-time. This technology can analyze vast amounts of data and identify patterns that would be difficult for a human to detect. This allows for faster response times and improved overall security.
DLP is a security solution that helps organizations prevent sensitive data from being leaked or stolen. This is done by monitoring and controlling the flow of data both within the organization and externally. DLP can be used to protect data such as intellectual property, financial information, and personal information.
SIEM is a technology that provides real-time monitoring and analysis of security events across an organization's network. This allows security analysts to identify and respond to potential threats in real-time, helping to minimize the impact of a security breach.
XDR is a newer technology that goes beyond traditional SIEM by integrating multiple security solutions into a single platform. XDR can provide greater visibility and context into security events by correlating data from different sources, allowing for a more comprehensive understanding of potential threats.
Overall, CyberSecOp's security services are designed to provide comprehensive and effective
The Growing Cyber Threat from China: AI is being used by China to develop new cyber weapons
The United States is facing an increasing threat from China in cyberspace. China is becoming more aggressive in its use of cyber attacks and developing new and more sophisticated capabilities. The U.S. government and private sector need to take steps to improve their cyber security in order to protect against these threats.
One of the biggest challenges facing the U.S. is the growing use of artificial intelligence (AI) by China. AI is being used by China to develop new cyber weapons and to automate its cyber attacks. This is making it more difficult for the U.S. to defend against these attacks.
The U.S. government and the private sector need to work together to develop new AI-based cyber defenses. They also need to invest in research and development to stay ahead of China in developing AI-based cyber weapons.
In addition, the U.S. needs to work with its allies to share information about cyber threats and to coordinate responses to these threats. This will help to protect the U.S. and its allies from Chinese cyber-attacks.
The U.S. is facing a serious threat from China in cyberspace. However, the U.S. can take steps to protect itself from these threats by improving its cyber security, developing new AI-based cyber defenses, and working with its allies.
Here are some additional details about the threat from China:
China is believed to be responsible for a number of high-profile cyber-attacks, including the 2017 WannaCry ransomware attack and the 2020 SolarWinds hack.
China is also believed to be developing a number of new cyber weapons, including AI-based weapons that can automate attacks and make them more difficult to defend against.
The U.S. government and private sector have been working to improve their cyber security, but China's growing capabilities pose a serious challenge.
The U.S. and its allies need to continue to work together to share information about cyber threats and to coordinate responses to these threats.
China is believed to be responsible for a number of high-profile cyber-attacks, including the 2017 WannaCry ransomware attack and the 2020 SolarWinds hack.
The WannaCry ransomware attack was a global cyberattack that affected over 200,000 computers in over 150 countries. The attack was carried out using a worm that exploited a vulnerability in the Windows operating system. The worm was able to spread from computer to computer, encrypting files and demanding a ransom payment in Bitcoin.
The SolarWinds hack was a sophisticated cyberattack that targeted the U.S. government and private sector. The attack was carried out by using a malicious update to the SolarWinds Orion software. The update was installed on computers at over 100 organizations, including the U.S. Department of State, the Department of Homeland Security, and the National Security Agency. The attackers were able to use the access they gained to these organizations to steal sensitive data.
China is also believed to be developing a number of new cyber weapons, including AI-based weapons that can automate attacks and make them more difficult to defend against.
AI-based cyber weapons are weapons that use artificial intelligence to automate attacks. These weapons can be used to launch large-scale attacks that would be difficult for humans to carry out. They can also be used to target specific individuals or organizations.
The U.S. government and private sector have been working to improve their cyber security, but China's growing capabilities pose a serious challenge.
The U.S. government and private sector have been working to improve their cyber security in recent years. They have invested in new technologies and training to defend against cyber-attacks. However, China's growing capabilities pose a serious challenge. China is investing heavily in cyber security and is developing new technologies that could be used to launch attacks on the U.S.
The U.S. and its allies need to continue to work together to share information about cyber threats and to coordinate responses to these threats.
The U.S. and its allies need to continue to work together to share information about cyber threats and to coordinate responses to these threats. This will help to protect the U.S. and its allies from Chinese cyber-attacks.
In conclusion,
the U.S. faces a severe threat from China in cyberspace. China is developing new cyber weapons and is using artificial intelligence to automate attacks. The U.S. government and the private sector must work together to improve their cyber security and develop new AI-based cyber defenses. The U.S. also needs to work with its allies to share information about cyber threats and to coordinate responses to these threats.
The U.S. and China are engaged in a cyber arms race, and the U.S. needs to take steps to stay ahead of China. The U.S. must invest in research and development and work with its allies to share information and coordinate responses. The U.S. also needs to educate its citizens about cyber security and how to protect themselves from attacks.
The cyber threat from China is real and severe, but the U.S. can take steps to protect itself. By working together, the U.S. and its allies can deter China from carrying out attacks and protect themselves from those occurring.
Company CISOs and Boards Brace for New SEC Cybersecurity Regulations
The U.S. Securities and Exchange Commission (SEC) is proposing new cybersecurity regulations that would require public companies to report cybersecurity incidents within four business days and to have a board-approved cybersecurity policy in place. The regulations are designed to protect investors from the risks of cybercrime and to hold public companies accountable for their cybersecurity practices.
Company CISOs (chief information security officers) and boards are bracing for the new regulations, which they believe will be costly and burdensome to implement. However, they also recognize that the regulations are necessary to protect companies and their investors from the ever-growing threat of cybercrime.
In this blog post, we will discuss the SEC's proposed cybersecurity regulations and what they mean for company CISOs and boards. We will also provide tips for companies on how to prepare for the regulations.
The SEC's Proposed Cybersecurity Regulations
The SEC's proposed cybersecurity regulations would require public companies to do the following:
Report cybersecurity incidents within four business days. Companies would be required to report any cybersecurity incidents that have a material impact on the company or its investors.
Have a board-approved cybersecurity policy in place. The policy should address the company's cybersecurity risks and how it will manage those risks.
Conduct regular cybersecurity assessments. The assessments should identify and fix vulnerabilities in the company's systems and networks.
Have a plan in place to respond to a cyberattack. The plan should include steps to contain the damage, notify regulators and customers, and restore operations.
The SEC's proposed regulations are based on the Cybersecurity Framework, a voluntary framework developed by the National Institute of Standards and Technology (NIST). The Cybersecurity Framework provides a set of best practices for organizations to follow to improve their cybersecurity posture.
The SEC's proposed regulations are likely to face opposition from some companies, who argue that they are too burdensome and costly. However, the SEC is likely to move forward with the regulations, given the increasing risk of cybercrime.
What the Regulations Mean for Company CISOs and Boards
The SEC's proposed cybersecurity regulations will have a significant impact on company CISOs and boards. CISOs will need to ensure that their companies are in compliance with the regulations, which will require them to implement and maintain a robust cybersecurity program. Boards will need to oversee the company's cybersecurity program and ensure that it is effective.
The regulations will also have a financial impact on companies. Companies will need to invest in cybersecurity controls and staff to comply with the regulations. The costs of compliance will vary depending on the size and complexity of the company.
Tips for Companies on How to Prepare for the Regulations
Companies can take the following steps to prepare for the SEC's proposed cybersecurity regulations:
Assess your cybersecurity risks. The first step is to assess your company's cybersecurity risks. This will help you to determine which areas need the most attention.
Implement appropriate security controls. Once you know your risks, you can implement appropriate security controls to mitigate them. This could include things like firewalls, intrusion detection systems, and data encryption.
Train your employees. Your employees are your first line of defense against cyberattacks. Make sure they are trained on cybersecurity best practices, such as how to identify and avoid phishing scams.
Stay up-to-date on cybersecurity news and trends. The cybersecurity landscape is constantly changing. Make sure you stay up-to-date on the latest news and trends so you can protect your company from new threats.
Conduct regular cybersecurity audits. Regular cybersecurity audits can help you to identify and fix vulnerabilities before they are exploited by attackers.
Implement a cybersecurity awareness program. A cybersecurity awareness program can help your employees to understand the risks of cybercrime and how to protect themselves and the company.
By taking these steps, you can help your company to comply with the SEC's proposed cybersecurity regulations and protect itself from the ever-growing threat of cybercrime.
Defending Against Cybersecurity Threats: Best Practices for Individuals and Organizations
Cybersecurity breaches have become increasingly common in recent years, affecting organizations and individuals alike. According to a report by Risk Based Security, there were over 18,000 publicly disclosed data breaches in the first half of 2021, resulting in the exposure of over 18 billion records. This represents a 47% increase in the number of breaches compared to the same period in 2020.
The consequences of a cybersecurity breach can be severe and long-lasting. Breaches can lead to the theft of sensitive data, financial losses, reputational damage, and legal liabilities. For businesses, a cybersecurity breach can result in lost productivity, customer loss, and damage to the company's brand and reputation.
To address the growing threat of cybersecurity breaches, organizations need to take a proactive approach to cybersecurity. This includes implementing robust security measures, regularly monitoring systems for signs of intrusion, and educating employees about safe online practices. Organizations should also have an incident response plan in place to quickly and effectively respond to a breach if one occurs.
Individuals can also take steps to protect themselves from cybersecurity breaches, such as using strong and unique passwords, enabling two-factor authentication, and being cautious of phishing attacks.
Defending against cyber security threats
Defending against cyber security threats is a complex and ongoing process that requires a combination of technical, administrative, and physical measures. Here are some general steps you can take to improve your cyber security posture:
Keep software and systems up-to-date: Regularly update your operating system, applications, and antivirus software to patch vulnerabilities and fix bugs.
Use strong and unique passwords: Use complex passwords and avoid using the same password across multiple accounts. Consider using a password manager to generate and store strong passwords.
Enable two-factor authentication: Enable two-factor authentication (2FA) on all your online accounts, which adds an extra layer of security beyond passwords.
Be cautious of phishing attacks: Be suspicious of emails or messages that ask for personal or financial information or contain suspicious links. Always verify the source before providing any information.
Use a firewall: A firewall can help protect your network by filtering traffic and blocking unauthorized access.
Back up your data regularly: Back up your important data regularly to protect against data loss in case of a security breach or hardware failure.
Limit access to sensitive data: Restrict access to sensitive data to only those who need it and use secure methods to share data.
Educate yourself and others: Stay informed about the latest cyber security threats and educate others, including employees, family members, and friends, about safe online practices.
Remember, cyber security is an ongoing process, and it requires constant attention and vigilance. By implementing these steps, you can help protect yourself and your organization from cyber threats.
In conclusion, cybersecurity breaches are a growing threat that can have severe consequences for both organizations and individuals. By implementing robust security measures and staying vigilant, organizations and individuals can help reduce the risk of a breach and minimize the impact if one occurs.
Mastering Vulnerability Testing: Tips and Techniques for Robust Cybersecurity
Vulnerability testing, also known as vulnerability assessment, is the process of identifying, evaluating, and prioritizing potential security vulnerabilities in a computer system, network, or application. It involves simulating attacks or exploitation attempts to discover weaknesses in the system's defenses.
Vulnerability testing can be done manually or through automated tools, and it may include testing for known software vulnerabilities, configuration issues, and access control vulnerabilities. The goal of vulnerability testing is to identify potential security risks before attackers can exploit them and to provide recommendations for mitigating or eliminating them.
Standard vulnerability testing techniques include vulnerability scanning, penetration testing, and ethical hacking. These tests can help organizations identify weaknesses in their security posture and take appropriate measures to strengthen their defenses and protect sensitive data.
Vulnerability testing is a critical aspect of ensuring the security of computer systems, networks, and applications. As technology advances and cyber threats become more sophisticated, it is essential for organizations to regularly perform vulnerability testing to identify potential security risks and take steps to mitigate them.
Through vulnerability testing, organizations can identify software vulnerabilities, configuration issues, and access control weaknesses that cybercriminals may exploit. By identifying these vulnerabilities, organizations can take appropriate measures to strengthen their security defenses and protect their sensitive data.
Various techniques can be used for vulnerability testing, including automated tools, manual testing, penetration testing, and ethical hacking. Each of these techniques has its advantages and disadvantages, and organizations may use a combination of them to provide comprehensive vulnerability testing.
Determine the scope of the test: Clearly define what will be tested, including the network, systems, applications, and any other assets that could be vulnerable to attack.
Use the right tools: Choose various tools, including vulnerability scanners, penetration testing tools, and web application scanners, to cover all potential vulnerabilities.
Prioritize vulnerabilities: Prioritize vulnerabilities based on the level of risk they pose and their potential impact on the organization.
Perform regular testing: Conduct vulnerability testing regularly after any significant changes or updates to the network, systems, or applications.
Test from internal and external perspectives: Conduct tests from internal and external perspectives to identify vulnerabilities that both internal and external attackers could exploit.
Ensure test results are accurate: Verify and validate test results to ensure they accurately reflect the actual vulnerabilities present in the system.
Address vulnerabilities promptly: Take prompt action to address any vulnerabilities identified during testing, including applying patches, updating configurations, and implementing additional security measures.
Document and communicate results: Document the vulnerability testing results and communicate them to relevant stakeholders, including IT staff, senior management, and external auditors.
In conclusion, vulnerability testing is an essential part of any organization's security program. It helps identify potential security risks before attackers can exploit them and provides recommendations for mitigating or eliminating these risks. By performing regular vulnerability testing, organizations can strengthen their security defenses, protect sensitive data, and reduce the risk of costly security breaches.
Staying on the Offence: SIEM & SOC Benefits
Many businesses these days do not have the resources or the skill set in-house to effectively create, administer and manage a fully operational Security Operations Center. A Security Operations Center (SOC) is a critical component of an organization's overall security strategy. It is a centralized team responsible for detecting, analyzing, and responding to security incidents in real time. In today's rapidly changing threat landscape, having a SOC is more important than ever.
Benefits of SOC as a SIEM
Protects against cyber threats: A SOC monitors and analyzes the organization's networks, systems, and applications for signs of cyber threats, such as hacking attempts, malware infections, and phishing attacks. By detecting threats early and taking action to prevent or mitigate them, a SOC helps to protect the organization from harm.
Increases efficiency: By centralizing security operations, a SOC helps organizations to be more efficient in their response to security incidents. The SOC team can respond quickly to incidents without coordinating with multiple departments and can share information and resources more efficiently.
Enhances compliance: Organizations are increasingly required to meet strict security and privacy regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR). A SOC can help organizations to comply with these regulations by monitoring their networks and systems for compliance and ensuring that any necessary changes are made.
Improves incident response: A SOC provides a dedicated team trained to respond to security incidents. This team can quickly contain and resolve incidents, reducing the impact on the organization and its customers.
In conclusion, having a security operations center is essential for organizations looking to protect their assets, reduce the risk of security incidents, and comply with industry regulations. By centralizing security operations, a SOC helps organizations respond to incidents more efficiently and effectively, ultimately reducing the risk of harm. CyberSecOP utilizes a US-based SOC team that is available 24/7/365 to ensure your business is protected by the latest ransom and malware threats out there.
AI the Future of Cyber Security
AI tools can sift through enormous amounts of data to look for patterns and learn about user behavior. This allows for the early detection of hackers before they cause harm.
Companies involved in cyber security are investing money into these technologies to fend off attacks and are starting to reap the rewards. AI-based technologies' capabilities are growing exponentially, enabling businesses to identify more sophisticated cyber threats before they materialize; more companies will likely start using AI tools as their usability increases.
As a result, more complex attacks will be recognized, making AI a crucial tool in the fight against cybercrime.
Artificial intelligence and machine learning are becoming more and more popular among businesses as
Artificial intelligence (AI) functions like a computer program focused on gaining success. Machine learning (ML), on the other hand, is a self-learning tool that evolves as it gains experience. Combining the two can guarantee accuracy and success in the cybersecurity industry.
Traditional Cyber Security
The fundamental problem with traditional cyber security measures is that it cannot keep up with the scale of the threat today. Conventional methods to collect and analyze information lead to an overload of data. It is labor-intensive and, therefore, prone to manual errors. Since they need more visibility into the network, it is also challenging to prepare against a potential threat.
AI in Cyber Security
In comparison, artificial intelligence in cyber security has a higher success in detecting possible threats and defending against them.
1. Network Threat Identification
This is the most basic use case for AI in cyber security today. More than 70% of businesses today are dependent on AI-enabled network security platforms. Furthermore, as enterprises share sensitive data over networks, AI-enabled systems are better equipped to protect the data transmitted or stored.
2. AI Email Monitoring
AI is used today to monitor incoming and outgoing emails to safeguard against cyber threats like phishing. The most probable risks are reported to the security personnel, and appropriate action can be taken. This becomes very important in the finance sector. Here, anomaly detection is used to identify phishing attacks and misdirected emails, prevent data breaches and identify other cyber security threats.
3. AI Endpoint Protection
Traditional anti-virus software can scan files for known viruses. The software cannot safeguard your data without security updates on new viruses. On the other hand, software that uses AI can detect a threat owing to anomaly detection or unusual behavior. Therefore it is better equipped to predict, detect and prevent a cybersecurity threat.
4. AI-based User Behaviour Modeling
In some cyber security attacks, the login id of a person can be manipulated by a complete takeover, without the person's knowledge. The only way to identify and stop this is by identifying a change in the behavior pattern of their activity. With AI technology solutions, such changes can be easily detected and security can then be alerted to investigate the matter further.
Conclusion
Cyber security systems with AI can anticipate a threat and deploy necessary action to prevent an attack. As a result, more and more corporations today are making special allowances in their budgets for upgrading to AI-enabled cyber security systems. As long as companies continue to feed accurate data, the system will swiftly detect any deviation from the baseline.
Cyber Insurance Ransomware
Cybersecurity is more important now than ever, and with more and more businesses around the world being affected by cyberattacks, having adequate cyber insurance has become essential.
Due diligence is a crucial part of getting the right cyber insurance policy. Companies should evaluate their potential risks and vulnerabilities in order to determine if they need a robust policy or if a cheaper, lower-coverage policy can suffice. Knowing what type of policy they need can help them save money while increasing assurance that they are properly covered if an attack occurs.
Companies need to understand that getting the right cyber insurance policy comes at a cost, as premiums tend to increase significantly when coverage increases. However, with proper due diligence, companies can make sure that their policies meet their needs without paying too much for unnecessary coverage.
Cybersecurity companies are recognizing “cyber extortion coverage” or “ransomware cyber insurance” as a critical element in protecting against the increasing ransomware threats and cyber attacks. This type of insurance protects organizations from losses due to such malicious activities, such as data breaches, ransomware threats, and other forms of cyber attacks.
By providing this type of coverage, cybersecurity companies can give their clients greater security and peace of mind. This coverage helps ensure that they won't be responsible financially for payments associated with an attack that results in the loss or theft of sensitive data. It also provides protection against any reputational losses that may arise after such an attack has taken place.
Ransomware & cyber extortion cyber insurance
Ransomware cyber insurance, also known as cyber extortion coverage, can protect organizations and their customers from the financial losses associated with a malicious attack. Cyber security companies offer this coverage under their cyber liability policies, typically included with a sublimit to help cover medical expenses related to those affected by the attack. Such policies allow companies to respond quickly and effectively to a ransomware attack, limiting the downtime and damage caused. By providing this protection, cyber security companies can ensure that businesses have a back-up option in case of malicious attacks or other unforeseen disasters.
What is Cyber Insurance?
Cyber insurance offers an additional layer of security for businesses against the ever-growing risk of a ransomware attack. Ransomware is a type of malicious software designed to block access to critical data on your computer system until a ransom is paid. By purchasing cyber insurance, companies can minimize the financial impact if they are hit by such an attack, as the policy reimburses victims for any losses incurred as a result of the incident. Cyber insurance also offers security consulting services such as malware removal and web application testing that can help reduce the risk of being targeted in the first place. Companies looking to protect themselves from ransomware should consider investing in cyber insurance to ensure their critical systems are protected against these kinds of threats.
Cyber Insurance& ransomware Protections
Cyber insurance is increasingly becoming an integral part of a company's cybersecurity policy in the face of fast-growing cybercrime threats like ransomware. Ransomware attacks can cause significant financial loss and affect companies' operations in many ways. Cyber insurance acts as a safeguard against such malicious programs and financially mitigates any losses related to the attack and helps companies get back on track without too much disruption. Companies must ensure that they have cyber insurance policies in place to protect themselves from ransomware attacks which have the potential to wreak havoc on any system.
Cyber insurance provides protection against ransomware. Cyber insurance works by providing coverage for financial losses and other damages caused by a hacker, malware or ransomware attack. Cyber insurance policies often cover losses related to data privacy and security, reputation damage, business interruption, and legal expenses. This type of coverage is increasingly becoming more critical as companies are increasingly exposed to cyber-attacks like ransomware. Ransomware is malicious software that locks down computers and networks, preventing users from accessing their own data until a certain amount of money is paid in return for the unlock code. With cyber insurance in place, organizations can ensure that their operations are protected from the financial costs associated with these malicious attacks.
Cyber insurance protects you by transferring loss
Cyber criminals are on the rise, and companies need to do whatever they can to combat attacks from ransomware, malware and phishing attempts. Cyber security companies offer organizations a comprehensive solution for cyber extortion coverage that helps protect against costly losses associated with successful infiltrations. Cyber extortion coverage can be included within a cyber liability policy as a sublimit or it can be secured separately, depending on your company’s risk exposure profile. With this coverage in place, businesses can rest assured that their cyber risk is adequately covered and their reputation is protected.
Cyber insurance Due diligence to ensure adequate protection
With the increasing threat of cyber fraud, companies must perform some due diligence to ensure they have adequate protection. Cyber insurance policies protect businesses from any financial losses caused by cyber-attacks. However, without proper due diligence, companies may end up paying higher premiums or getting policies that do not cover all aspects of the risk.
Therefore, to reduce costs and get the right coverage, companies need to perform thorough research and find insurance providers who offer reasonable terms and conditions with their cyber insurance policies. Companies must also consider factors like premiums, deductibles, limits, and exclusions before purchasing a policy.
By doing so they will be able to get the most suitable coverage for their business at an affordable price.
Cyber insurance due diligence is a key process for any business when evaluating the cost and level of protection offered by their cyber insurance policy. As cyber risks continue to evolve, companies must always be aware of the increasing cost and premiums associated with their current policy and evaluate whether it is enough to keep up with the latest malicious threats.
In order to ensure the most effective protection, companies should conduct due diligence on their cyber insurance policies. This not only involves understanding how claims will be handled in different scenarios, but also considering the cost of increased coverage and extra premium costs that might be necessary. By understanding their risk profile and protecting themselves adequately, businesses can ensure they are equipped if they are ever faced with a malicious attack.
Cyber insurance premiums will continue to increase
Cyber attacks are rising yearly, with more businesses falling victim to cyber- Attacks resulting in security breaches and financial losses. As a result, more companies are now investing in cyber insurance policies to protect their data and minimize damages. However, this increased demand of cyber insurance policies has led to an increase in policy premiums, making it costlier for businesses to obtain the coverage they need. In this article, we will discuss why cyber insurance premiums continue to rise and suggest potential solutions for companies looking for coverage.
Cyber insurance must be included in your risk management strategy
Cyber insurance has become an essential part of any business's risk management strategy. As cyber-attacks become more frequent and destructive, enterprises are turning to cyber insurance providers to protect themselves from costly damages. But as the amount of claims for cyber-attacks increases, so does the increase in premium costs to cover those losses. This article will explore the reasons why we can expect to see a continuous increase in cyber insurance premiums over time.
Cyber insurance policies are becoming increasingly popular as more and more companies are seeing the benefit of having a policy in place to protect their business from cyber-attacks. As more companies realize the impact of cyber security breaches, the demand for cyber insurance is likely to increase, driving up premiums.
As prices increase, so too does the importance of having a comprehensive cyber insurance policy that covers all the possible loopholes that can occur during an attack. With this in mind, businesses are wise to explore their options when selecting their providers and to ensure they get the best coverage available for their needs. By exploring these options and understanding what is covered under different policies, firms can make an informed decision about which provider offers them the most protection at a competitive premium cost.
Enterprise Risk Management vs. Traditional RM
Enterprise Risk Management (ERM) introduces effective risk management (RM) by attacking the issues differently to assess and remediate risks that affect the business. It takes a more robust approach than traditional Risk Management.
Traditional Risk: Business unit leaders, directors, and managers were responsible and accountable for risks in their respective departments. An example is the CFO, or Comptroller is responsible for risks relating to business cash flow and finance. This approach is very siloed. Having some type of Risk management is better than not having it, but this approach does have its shortcomings:
Unidentified risks that don’t fit nicely within a silo. Risks can be anywhere, and sometimes they do not necessarily align with the organizational chart resulting in unidentified risks.
Some risks may span multiple business units. If one leader identifies the risk the business may not understand its true impact and likelihood if it spans multiple departments. An example of this would be a privacy law that affects Spain for example. If the compliance officer ranks this as very low risk because there is no business/consumers or data from Spain residents. However, down the hall in another c-suite office, there are ongoing talks about a possible partnership with a platform in that same country.
Silo risk owners may address a risk in their domain but not understand that the mitigations of their risk can affect another department. A classic example is an IT change that mitigates some technical risks but impacts usability for other departments. This leads to frustration, confusion and ‘shadow IT’
Traditional risk typically focused on internal risks. ERM focuses on external factors as well
Holistic Top-Down Enterprise Risk Management
Enterprise Risk Management attempts to fill these gaps by incorporating a holistic, all-hands-on-deck approach to risk management. EMR is a top-down approach that starts from a strategic approach that trickles down to the operational level (Beasley, 2016).
ERM begins with an understanding of what the organization is trying to achieve short and long term. Identifying all assets (people, technology, data, solutions, networks) ranking those assets, identifying risks and then ultimately remediation and monitoring. It is key to understand that top management and key staff are involved in this process, not just a department leader.
Identify all risks. Whereas with traditional risk management, risks that fall out of a department can be missed, EMR focuses on strategy, compliance, operations, and tactics to attempt to address all risks (internal and external).
The output of EMR should be a risk register that clearly identifies the enterprise's top risks that identify:
Risk identification number
Owner, responsible, and accountable parties
Risk description
Risk Remediation
Risk milestones
Key Risk Indicators
EMR takes a more holistic approach to risk management and incorporates all levels of the business (strategy, tactical, operational). EMR focuses on internal and external risks. EMR is a cycle and not a project; the focus is always on understanding the business's top threats, their remediations if they are being implemented, and how effective those mitigations are. This approach is the next step in the evolutionary process of risk management and provides one of the most impactful and thorough methods for risk management.
Written by:
Carlos Neto 1/9/2023
References:
Beasley , M. (2016). What is enterprise risk management? - North Carolina State University. NC State . Retrieved January 10, 2023, from https://erm.ncsu.edu/az/erm/i/chan/library/What_is_Enterprise_Risk_Management.pdf
Protecting Against Ransomware: Zero Trust Security
Zero trust isn't a silver bullet for ransomware, but if implemented well, it can help create a much more robust security defense.
Did you know only 26% of companies have a specific incident response plan for ransomware? With ransomware attacks constantly on the rise, your organization needs to be prepared and take every possible precaution.
Reduce your organization’s risk with CyberSecOp Zero Trust Program. With the help of a single-source platform for your compliance program, you can protect against vulnerabilities while reducing incident response time by as much as 60%.
Ransomware victims paid more than $600 million to cybercriminals in 2021. According to blockchain analysis firm, Chainalysis, more than $600 million in cryptocurrency could be tied to ransomware payments in 2021, with the Conti ransomware gang accounting for nearly one-third of those payments.
HOW CAN CYBERSECOP HELP YOUR ORGANIZATION BE CYBER READY?
CyberSecOp provides cyber risk and advisory programs that identify security gaps and build strategies using Zero Trust or other security frameworks. The zero-trust model is an effective defense mechanism for preventing ransomware. Adoption of zero-trust architecture, the modern alternative to perimeter-based security, is one of the most effective ways to prevent ransomware attacks.
Don't Forget the Fundamentals on World Backup Day 2022
March 31st is apparently world backup day! Who knew? In honor of that it seemed like a good time for a quick post extolling the virtues of backups. According to the “WorldBackupDay” website, 21% of people have never taken a backup and 30% of computers are already infected with malware. While these stats are related to individuals and not necessarily businesses the stats sound about right.
Take Backups!
Regardless of whether you are a small business or a global Fortune 500 company, backups are an essential part of your organization's risk management plan. It’s easy to be lulled into complacency. Just the other day I was working with an organization in the mechanical service delivery industry who’s entire “IT Infrastructure” was a single 2017 iMac. They never bothered with any additional machines, backups and other such items because they had been told that Mac’s were “bulletproof” and not susceptible to the common maladies of the humble PC. Unfortunately, their Mac was susceptible to good old fashioned old age and corrupt updates. As a result they found themselves in a position where they had a large proposal for a job due the next day and the only place it existed was on this one broken Mac. Now fortunately for them, we were able to recover the system and restore their data, but what if we hadn’t been able to? It is absolutely critical, regardless of the size of your organization that you have a backup solution in place tailored to your specific needs. Stay tuned for some suggestions on backup providers we love at the end of this article!
Test your Backups!
This might seem like a no-brainer, but in addition to taking backups, it's critically important that you TEST your backups. Having a plan and procedure in place for how to recover your data in the event of a disaster is just as important as taking the backup in the first place! In my last example of the company with a single iMac. What if they had set up icloud and automatically configured their file to sync there. If I had asked the owner of the business if he had the password for the icloud account or even knew what account icloud was associated with, I wonder if he would have known? Having a documented plan that outlines where your backups go, what authentication is used to access them, how frequently they are taken, and how to restore them to a device is critical. If you are a larger organization you probably want to start having conversations about RTO and RPO at this point as well and ensuring your backup solution can meet those goals. (Recovery Time Objective, Recovery Point Objective.) Essentially, how long will it take to recover my data and how much time passes between backups, or put more simply, how much data can I afford to lose? 1 Day’s Worth? 1 Weeks worth? Less? More? Make sure your backup solution can meet your specific needs and goals!
Protect your Backups!
Finally, congrats if you're taking and testing your backups! Are you also protecting your backups? You’re probably thinking, protecting my backups?! What’s this guy going on about now? Consider this, you backup your information every night and test it regularly. You sleep easy at night knowing that you can recover should the worst happen. However, what you don’t know, is that earlier last month one of your employee’s laptops was infected with a virus. This virus replicated across your organization but stayed dormant, collecting information about your company and environment but not taking any malicious actions yet. The threat actor discovers that your backups run nightly and are stored for 4 months on a network share. The virus then deletes all of your backups and begins encrypting your files. When you return to work the next day and find all of your computers and files encrypted, you attempt to recover from backup only to find your backups have been deleted! This is an oversimplification of the process but this is essentially what the bad guys are doing. There are many ways to prevent this sort of attack including storing backups in offline or immutable data stores, encrypting your backups and storing multiple copies of every backup in different locations. At this point you might be thinking “I can simply copy files to an external drive of some sort on a regular basis right?” , but what if something happens to that drive? As the old timer’s say, “two is one and one is none”. The idea is that if you only have one, something could happen to it and then you have none. Have a backup plan for your backup plan!
Conclusion
Now that you’re completely terrified know that there are solutions out there for all of these problems. Proper backup planning is a key component of every organization's Disaster Recovery, Business Continuity and Incident Response Planning. If you are looking for assistance with any of those plans, make sure you give us at CyberSecOp a call, we would love to help you with this.
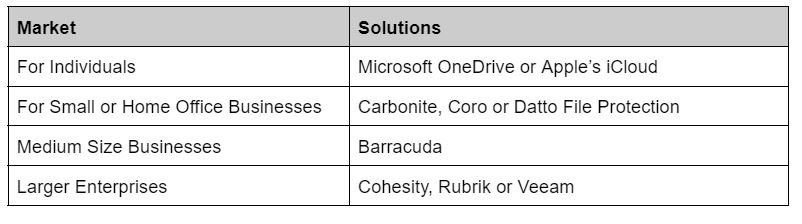
In the meantime if you're looking for somewhere to start with backup’s here are some of our favorites.
Author: Timothy Burger
ADVISORY: Reports of possible digital breach
ADVISORY: Reports of possible digital breach
Okta investigating reports of possible digital breach
Lapsus$, a cyber extortion gang, has announced that they have breached Microsoft and Okta.
The gang has leaked torrents containing source code for Bing, Bing Maps, and Microsoft Cortana, as well as a screenshot of an internal Microsoft Azure DevOps account. They also claim to have had “Superuser/Admin” access to Okta’s systems for two months, and said its focus was “only on Okta customers.”
Both Microsoft and OKTA have started an investigation to confirm or disprove they’ve been breached.
Recommended Actions:
These attacks are a striking reminder of the supply chain’s cyber risks - Real risks brought to organizations by use of softwares and systems like OKTA, Microsoft, as well as many others.
Please work with your vCISO or Risk Manager to ensure the proper Vendor Security controls and processes are in place as well as other vital security controls that will drastically reduce the possibility of these dangerous hacks spilling into your network and systems.
Author: Michael Sardari
CISA's 'Shields Up' Alert Highlights Foreign Cyberthreats
Cyberwarfare is the battlefield of today. Increased geopolitical tensions stemming from Russia's unprovoked attack on Ukraine has led to CISA (the Cybersecurity & Infrastructure Security Agency) issuing a "Shields Up" bulletin. Every organization must be prepared to respond to disruptive cyber activity, especially those in critical infrastructure fields.
Here are some tips to help you keep your organization safe in these trying times.
Reduce the likelihood of a damaging cyber intrusion
Use MFA or Multi-Factor-Authentication everywhere.
Ensure all Systems are patched and up to date.
Consider increasing patch frequency if not already real-time.
Take steps to quickly detect a potential intrusion
Run, update and monitor a strong Endpoint Protection Program.
Consider increasing Spam and Phishing filter sensitivity.
Disable any non-essential ports and protocols, specifically through external gateways.
Ensure that the organization is prepared to respond if an intrusion occurs
Review your incident response plan and ensure it is up to date and all parties are clear on their roles.
Maximize your organization's resilience to a destructive cyber incident
Ensure that you are taking regular backups and that your backups are encrypted and immutable.
Test your backup and recovery procedures.
Communicate with your users, the best and strongest defense is a well-educated and well-prepared workforce.
If you are a CyberSecOp customer today in either our vCISO or vSOC program your risk manager will be reaching out shortly to ensure this guidance is being implemented to the extent possible within your organization.
If you are not currently enrolled in one of our plans and need assistance assessing your posture and capabilities, please feel free to reach out.