CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
Ensure Cyber Resilience by Developing Your Cyber Resilience Plan
Cybersecurity risks are common in the digital age, but we should not allow them to limit our business goals. Cybersecurity consulting and security breaches have gradually become critical parts of the IT department. We cannot tackle cyber threats without the expertise of cybersecurity consultants or cybersecurity breach experts.
Whether starting from scratch or looking to improve your existing cybersecurity resources, hiring a qualified cybersecurity consultant or security breach expert is always a good idea first.
Cybersecurity Vulnerabilities, Exploits, and Threats
Cybersecurity vulnerabilities are more likely to occur when old software versions are in use. Cybercriminals may exploit any software bugs they find. They may even write malware to specifically target older applications, which are less secure and easier to hack than their newer counterparts.
If you want to protect your company from cyber attacks, here are a few ways:
Use the latest version of any application that is essential for your business (e.g., antivirus software);
Have an expert conduct regular audits and penetration tests;
Install operating system patches as soon as possible;
Train employees on cybersecurity best practices;
Strengthen network defenses by having an active firewall, two-factor authentication, and strong passwords policies in place;
Let employees know what they can do to keep their devices safe at home and work.
Implement ransomware backup best practices
Cyber Risk Mitigation Solution
When considering an organization's cyber security approach, the initial needle-moving goal should not be to avoid all risks, but instead, the strategy should contemplate how much security and what type of risk level is appropriate for different vulnerabilities.
The vulnerability analysis techniques present an opportunity for organizations to address the weaknesses in their current system and security framework. The flaw-based techniques help in assessing risks, hypothesizing breach points as well as benefits and disadvantages produced as a result of these risks. The damage potential (DP) technique offers this kind of precise information about vulnerable areas within cyber-systems that are commonplace features of computers and mobile devices.
Companies are getting hit by ransomware attacks, but there are things that both companies and employees can do to protect themselves by hiring an organization like CyberSecOp to implement a robust security program.
Security breaches can have disastrous effects as they potentially expose sensitive data to hackers. Companies are advised to plan their security measures in a preventive way and commit to these methods. The response should also be planned in order to restore the state prior to or minimize the damage caused by a security breach effectively.
Governmental agencies are investing in cybersecurity.
Cybersecurity has become a major issue. Governmental agencies are investing in the cybersecurity domain and focusing on security advancements. For example, Cybersecurity Strategy 2020 and expanding U.S. Cyber Task Force under DHS relate to this area of security and address the broad scope of cyber threats to federal networks, systems, or communications infrastructure identify priorities for cyber risk management, ensure persistent attention to counterterrorism with respect to cyberspace policymaking, execution baseline resilience against digital interference, reduce interstate conflict over jurisdictional responsibilities related to cybersecurity matters by improving key information-sharing practices among relevant federal entities in order to promote operational coordination on cybersecurity matters.
Don't Forget the Fundamentals on World Backup Day 2022
March 31st is apparently world backup day! Who knew? In honor of that it seemed like a good time for a quick post extolling the virtues of backups. According to the “WorldBackupDay” website, 21% of people have never taken a backup and 30% of computers are already infected with malware. While these stats are related to individuals and not necessarily businesses the stats sound about right.
Take Backups!
Regardless of whether you are a small business or a global Fortune 500 company, backups are an essential part of your organization's risk management plan. It’s easy to be lulled into complacency. Just the other day I was working with an organization in the mechanical service delivery industry who’s entire “IT Infrastructure” was a single 2017 iMac. They never bothered with any additional machines, backups and other such items because they had been told that Mac’s were “bulletproof” and not susceptible to the common maladies of the humble PC. Unfortunately, their Mac was susceptible to good old fashioned old age and corrupt updates. As a result they found themselves in a position where they had a large proposal for a job due the next day and the only place it existed was on this one broken Mac. Now fortunately for them, we were able to recover the system and restore their data, but what if we hadn’t been able to? It is absolutely critical, regardless of the size of your organization that you have a backup solution in place tailored to your specific needs. Stay tuned for some suggestions on backup providers we love at the end of this article!
Test your Backups!
This might seem like a no-brainer, but in addition to taking backups, it's critically important that you TEST your backups. Having a plan and procedure in place for how to recover your data in the event of a disaster is just as important as taking the backup in the first place! In my last example of the company with a single iMac. What if they had set up icloud and automatically configured their file to sync there. If I had asked the owner of the business if he had the password for the icloud account or even knew what account icloud was associated with, I wonder if he would have known? Having a documented plan that outlines where your backups go, what authentication is used to access them, how frequently they are taken, and how to restore them to a device is critical. If you are a larger organization you probably want to start having conversations about RTO and RPO at this point as well and ensuring your backup solution can meet those goals. (Recovery Time Objective, Recovery Point Objective.) Essentially, how long will it take to recover my data and how much time passes between backups, or put more simply, how much data can I afford to lose? 1 Day’s Worth? 1 Weeks worth? Less? More? Make sure your backup solution can meet your specific needs and goals!
Protect your Backups!
Finally, congrats if you're taking and testing your backups! Are you also protecting your backups? You’re probably thinking, protecting my backups?! What’s this guy going on about now? Consider this, you backup your information every night and test it regularly. You sleep easy at night knowing that you can recover should the worst happen. However, what you don’t know, is that earlier last month one of your employee’s laptops was infected with a virus. This virus replicated across your organization but stayed dormant, collecting information about your company and environment but not taking any malicious actions yet. The threat actor discovers that your backups run nightly and are stored for 4 months on a network share. The virus then deletes all of your backups and begins encrypting your files. When you return to work the next day and find all of your computers and files encrypted, you attempt to recover from backup only to find your backups have been deleted! This is an oversimplification of the process but this is essentially what the bad guys are doing. There are many ways to prevent this sort of attack including storing backups in offline or immutable data stores, encrypting your backups and storing multiple copies of every backup in different locations. At this point you might be thinking “I can simply copy files to an external drive of some sort on a regular basis right?” , but what if something happens to that drive? As the old timer’s say, “two is one and one is none”. The idea is that if you only have one, something could happen to it and then you have none. Have a backup plan for your backup plan!
Conclusion
Now that you’re completely terrified know that there are solutions out there for all of these problems. Proper backup planning is a key component of every organization's Disaster Recovery, Business Continuity and Incident Response Planning. If you are looking for assistance with any of those plans, make sure you give us at CyberSecOp a call, we would love to help you with this.
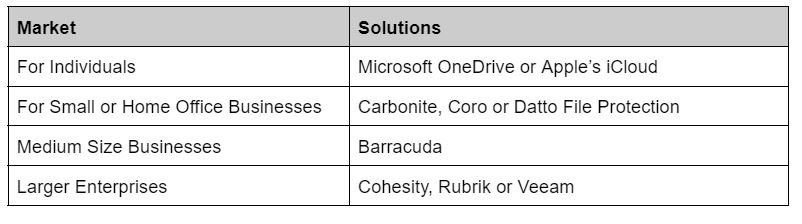
In the meantime if you're looking for somewhere to start with backup’s here are some of our favorites.