INCIDENT RESPONSE PLAN SERVICES
We Detect, Investigate, and provide Incident Response Plans, we keep our eyes on your network's activity and ensure you have the right Incident response plan in place.
Incident Response Plan Services
Incident Response Plan Development
Do you have an Incident Response Plan: Whether or not your organization is prepared, security breaches have become common occurrences; for this, you will need a Data Breach Incident Management team, sometimes the bad guys win, and security measures occasionally fail to prevent an incident. Cyber Security Operations has experts in incident response, data breach Incident Management, forensics, and electronic discovery who can support or supplement your team when suspected unauthorized, illegal, or malicious activities are detected, or you are ready to develop a comprehensive plan, so you are prepared in the event of a breach. Emergency Response Team (ERT) and Breach Incident Response services call us at 212-459-0802.
Incident Response Plan Development
Our team of experts will guide you to build a solid incident response plan around best practices regarding the incident response process and procedures.
An incident response plan is a set of tools and procedures that your security team can use to identify, eliminate, and recover from cybersecurity threats. It is designed to help your team respond quickly and uniformly against any type of external threat.
Incident response plans ensure that responses are as effective as possible. These plans are necessary to minimize damage caused by threats, including data loss, abuse of resources, and the loss of customer trust.
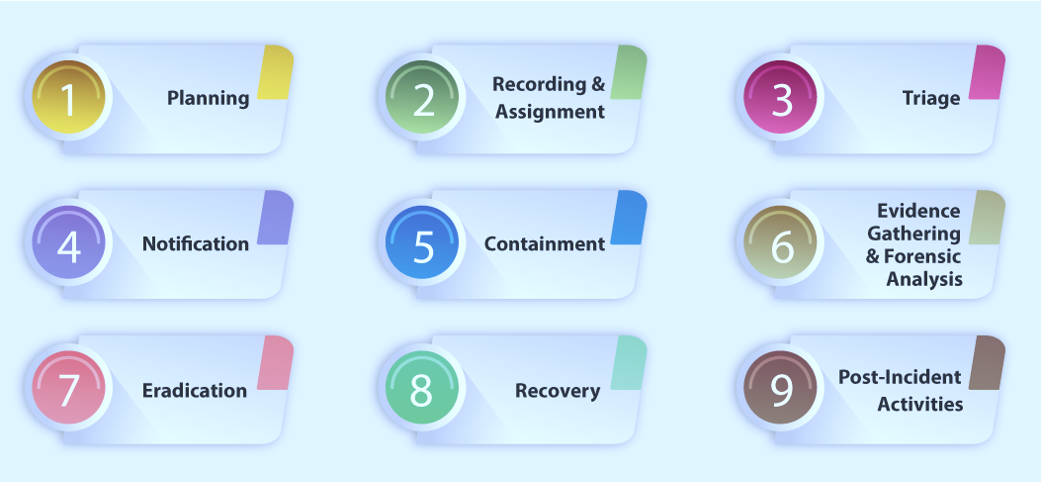
The incident response phases are:
Preparation
Identification
Containment
Eradication
Recovery
Lessons Learned
Incident Response Preparation
Preparation is the first phase of incident response planning and arguably the most crucial in protecting your business and digital assets. During the preparation stage you’ll document, outline, and explain your IR team’s roles and responsibilities, including establishing the underlying security policy which will guide the development of your IR plan.
Identification, Detection and Analysis Response
The detection and analysis phase is where the action begins to happen in our incident response process. In this phase, we will detect the occurrence of an issue and decide whether or not it is an incident so that we can respond to it appropriately. Malware are continuously growing in sophistication and numbers. Over the last decade, remarkable progress has been achieved in anti-malware mechanisms. However, several pressing issues (e.g., unknown malware samples detection) still need to be addressed adequately.
Incident Containment & eradication
The containment, eradication, and recovery phase is where the majority of the work takes place to solve the incident, at least in the short term.
Have artifacts/malware from the attacker been securely removed?
Has the system been hardened, patched, and have updates been applied?
Can the system be re-imaged
incident recovery planning
Getting your business back to normal operations is our first priority. A rapidly restored plan enables your business operations efficiently and effectively recover critical business components. We work with organizations to build a way for you to provide your organization with a world-class disaster recovery program. It’s easier than you think to consolidate your backup and DR solutions. Design and launch a disaster recovery implementation on your own or through one of our trusted service providers.
Disaster recovery orchestration with runbooks
Backup-based replication of production machines
Instant off-site failover to the cloud recovery site
Recovery of the deceased is done with expert efficiency
Lessons Learned
Once the investigation is complete, hold an after-action meeting with all Incident Response Team members and discuss what you’ve learned from the data breach. This is where you will analyze and document everything about the breach. Determine what worked well in your response plan and where there were some holes. Lessons learned from mock and real events will help strengthen your systems against future attacks.
Incident Response Readiness services
Our Incident Response Readiness services include the development of the Incident Response Plan (IRP), Incident Response Team Training, First Responder Training, an Incident Response (IR) Technology Review, a Threat Hunting service, and a Service Level Agreement for Live Incident Response.
Find more information on Incident Response Plan and Incident Management.