DDoS Protection, DDoS Prevention
&
Mitigation Services
CyberSecOp DDoS Blocks Block Cyber-Criminals trying to break into your website, We utilize the leading Web Application Firewall on top of our threat intelligence systems, to block know and unknown attacks. DDos, Code injection, Bot Blocker, IP restriction and others.
DDoS Attack Protection & DDoS Mitigation Services
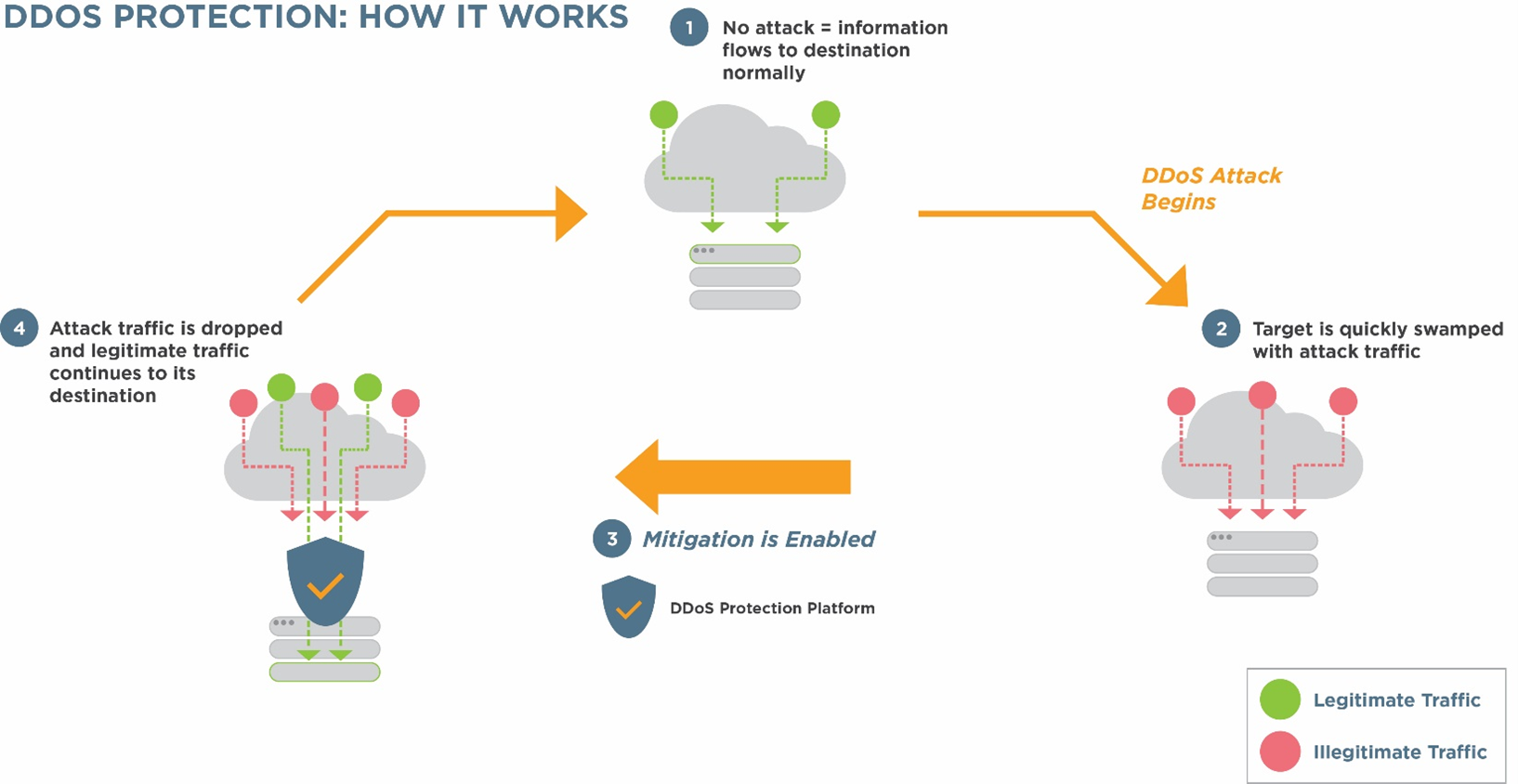
DDoS protection is critical, though DDoS is one of the older cyberthreats, they have become more advanced in recent years. They happen when hackers manage to remotely control computer “bots”, otherwise known as systems that have been taken over with malware. They then direct thousands of these computers to send requests to one target, for example a website or application. This causes a traffic flood and leads servers to crash, preventing genuine visitors from gaining access.
CyberSecOp DDoS mitigation solution include CDN-based, DDoS scrubbing, and DNS components, depending on each customer's requirements. CyberSecOp protecting DNS services from DDoS attacks incorporates automated rate controls, custom Web Application Firewall (WAF) rules, monitoring tools, traffic profiles and workflows that avoid unnecessary mitigation actions. monitors detect a DDoS attack, support personnel immediately notify customers about it and recommend a mitigation strategy. In addition to monitoring, the company offers on-demand mitigation. Contact our Global Incident Response Hotline: 212-459-0802
CyberSecOp Cap DDoS Attack Protection Benefits
Confidence in security
Keep your visitors safe by defending against the most sophisticated DDoS attacks with 99.99 percent accuracy.
Constant uptime
Ensure zero disruption to your site or user experience in the event of a DDoS attack. DDoS attacks are notorious for taking sites offline for hours at a time—long enough to detract a customer or visitor.
Cost savings
Not only can preventing a DDoS attack save you money, but CyberSecOp DDoS Cap cloud-based DDoS protection eliminates the high costs that come with additional servers and load balancing infrastructure.
Advanced visitor identification
Differentiate human traffic from bot traffic with advanced visitor identification. You can customize your settings and block malicious traffic from entering your site.
Stay informed
Stay updated on the security of your website by viewing your DDoS attack protection results at any time from your CyberSecOp DDoS Cap Dashboard.
Quick and easy setup
Setting up your DDoS protection is easy, and the CyberSecOp DDoS Cap team of experts are available to help 24/7/365.
CyberSecOp DDoS Cap NextGen DDoS Protection Service
CyberSecOp DDoS Cap DDoS runs a global network of servers to ensure 24/7/365 uptime, and visitors to your website will never know that your website is under attack. They will not encounter latency, CAPTCHAs, HTTP errors, or wait messages like other DDoS protection services use. And CyberSecOp DDoS Cap prevents direct-to-IP DDoS attack by hiding the IP of the origin server.
1GB CAP Shield WAF + DDoS
Constant website uptime with state-of-the-art DDoS protection
Sophisticated web application, infrastructure, and DNS protection
Access to advanced visitor identification
Blocks bad bots
Includes traffic statistics and reports
Includes a premium content delivery network to increase website speed
Advanced static and dynamic content caching
Sophisticated threat protection from the OWASP Top 10 cyberthreats
Provides fully secure end-to-end encryption for SSL
Prevents search engine backlisting
Improves SEO
Eliminate comment and form spam
Application layer DDoS Protection Service
Application layer DDoS attacks aim to exhaust the resources of the target and disrupt access to the target’s website or service. Attackers load the bots with a complicated request that taxes the target server as it tries to respond. The request might require database access or large downloads. If the target gets several million of those requests in a short time, it can very quickly get overwhelmed and either slowed to a crawl or locked up completely.
An HTTP Flood attack, for example, is an application layer attack that targets a web server on the target and uses many fast HTTP requests to bring the server down. Think of it as pressing the refresh button in rapid-fire mode on your game controller. That kind of traffic from many thousands of computers at once will quickly drown the webserver.
The nature of today’s DDoS threats
Criminal activity was quite common. However, the number of successful DDoS attacks has been increasing with DDoS as a service. This decrease in DDoS attacks is likely to have resulted from the following:
Police investigations that have resulted in the arrest of criminals across the world
Technical countermeasures that have been successful against DDoS attacks
Other articles and links related to Distributed Network Attacks / DDoS
What is DDoS
In computing, a denial-of-service attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.
Common Denial-of-Service Attacks
There are many different methods for carrying out a DoS attack. The most common method of attack occurs when an attacker floods a network server with traffic. In this type of DoS attack, the attacker sends several requests to the target server, overloading it with traffic. These service requests are illegitimate and have fabricated return addresses, which mislead the server when it tries to authenticate the requestor. As the junk requests are processed constantly, the server is overwhelmed, which causes a DoS condition to legitimate requestors.
In a Smurf Attack, the attacker sends Internet Control Message Protocol broadcast packets to a number of hosts with a spoofed source Internet Protocol (IP) address that belongs to the target machine. The recipients of these spoofed packets will then respond, and the targeted host will be flooded with those responses.
A SYN flood occurs when an attacker sends a request to connect to the target server, but never completes the connection through what is known as a three-way handshake—a method used in a TCP/IP network to create a connection between a local host/client and server. The incomplete handshake leaves the connected port in an occupied status and unavailable for further requests. An attacker will continue to send requests, saturating all open ports, so that legitimate users cannot connect.
Individual networks may be affected by DoS attacks without being directly targeted. If the network’s internet service provider (ISP) or cloud service provider has been targeted and attacked, the network will also experience a loss of service.