Cyber Security Breach Investigation Services
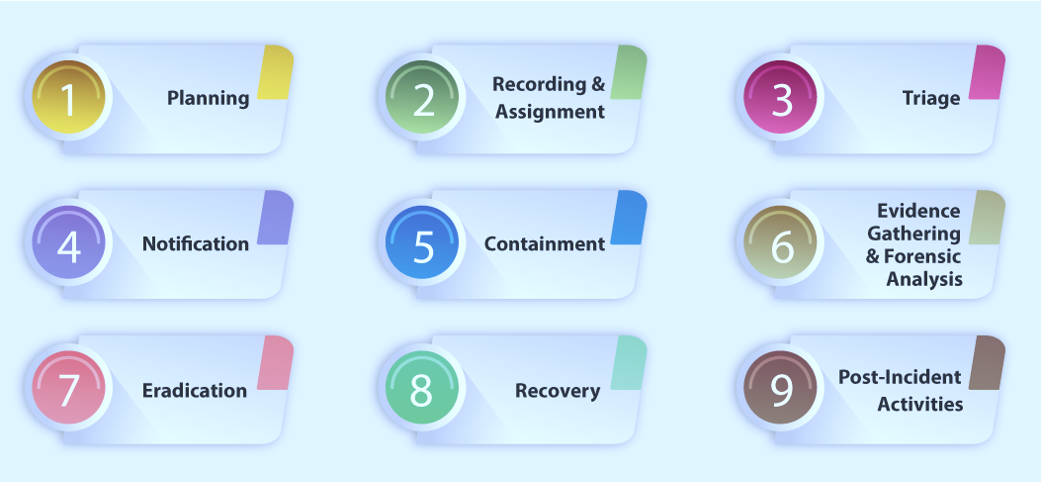
During a breach, it's important to move quickly to contain the threat and minimize the impact by getting to the root cause. However, overlooking evident procedures can limit your ability to help legal or governmental authorities pursue the threat actor. Our digital forensics professionals will work closely with your company’s crisis communications team to provide the public and customers with up-to-date information about any private information that may have been compromised, and information on the steps being taken to help protect customers against future breaches.
Our Forensics and cybersecurity services:
Computer Forensics Investigators
Our Computer Forensics Investigator’s first step is to clearly determine the purpose and objective of the investigation in a free consultation. We will work with you to identify where your data is located. We will document the legal chain of custody of the media and we will make a bit by bit copy and preserve the original. The computer forensic analysis will examine and extract the data that can be viewed by the operating system, as well as data that is invisible to the operating system including deleted data that has not been overwritten.
Forensics Investigator Legal Evidence
Our Computer Forensics Investigator also addresses the legal issues associated with electronic evidence, such as relevant case law, how to navigate the discovery process, protection of privilege, and in general, working with attorneys and other professionals.
CyberSecOp is experienced in providing counsel with clear and usable information, whether it relates to the creation date of a specific file or the provenance of gigabytes of recovered deleted emails.
Our in-house team has testified as experts in state and Federal courts, and have advised on issues including metadata, the recovery of deleted data, and the significance of operating system logs and forensic artifacts
Digital Forensics Services and Malware Analysis
Our IT Security team will thoroughly investigate the incident while keeping you informed of all results. Computer forensic investigation can be performed during Incident Response Handling or independently, depending on your needs. Our experts leverage elite cyber threat intelligence to investigate the breach, determine its likely cause, report progress to appropriate parties as required by PCI Security Standards Council, and help you contain and eradicate the threat from your environment as quickly as possible.